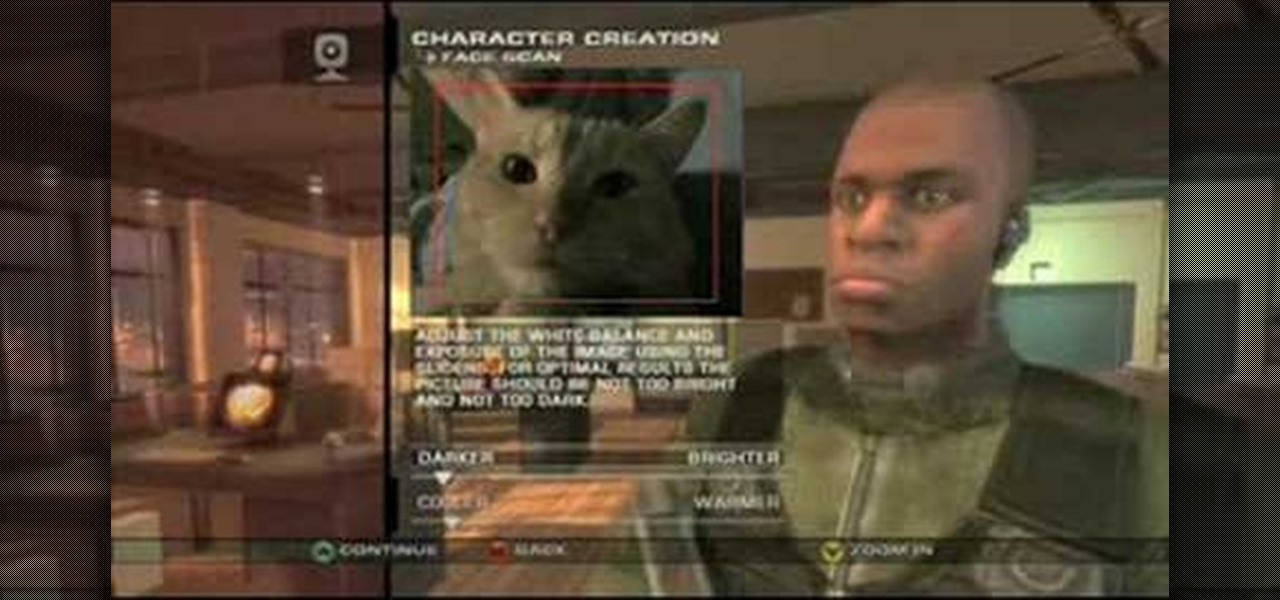
This process requires XBox2 live with vision camera. We are going to create a character. First, you go to multiplayer mode, options and then choose character creation. If you haven't created a character, you will start from scratch here. If you have created a character previously, you will make some adjustments to the character for this presentation. Now, go to player information and then service record. As the program already has a character, we are going to change the appearance of the char...
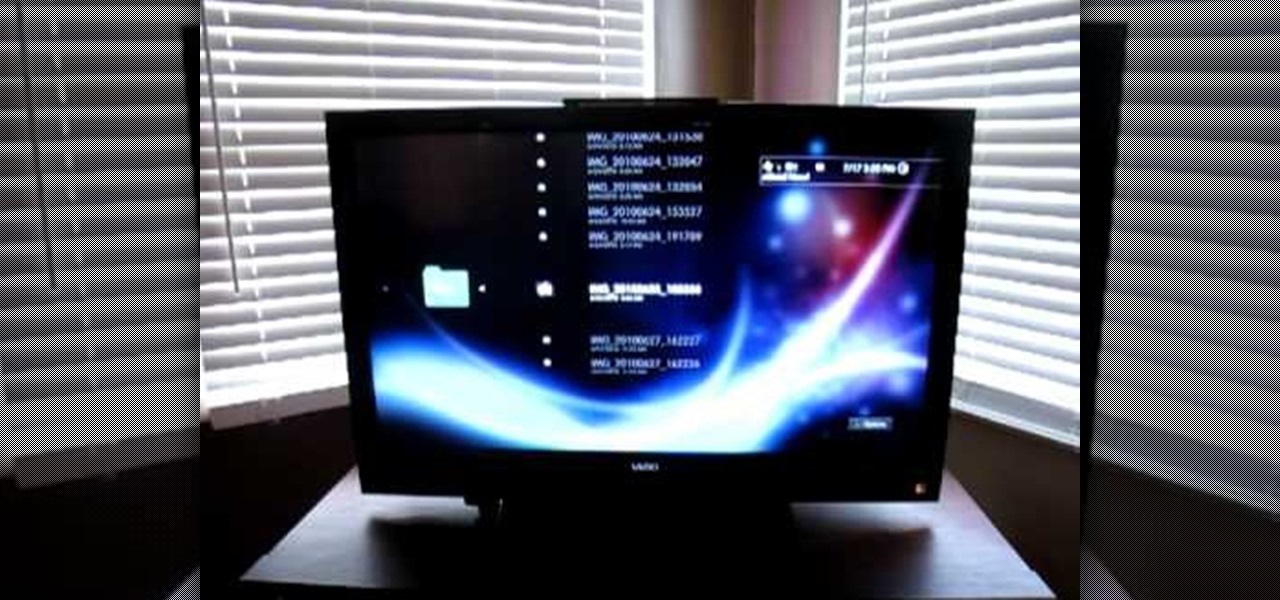
Okay, just because the new Verizon Wireless Droid X comes with an HDMI-out port doesn't mean you're limited to just that. Motorola has made it possible for you to play video, music, and pictures to your television without any wires at all. With the Droid X's DLNA media sharing application, you can easily stream to an PS3 or Xbox, send pics to your PC, and stream videos to your TV. Check out this video walkthrough to learn how to use the DLNA services to connect your Droid X to the PlayStation 3!
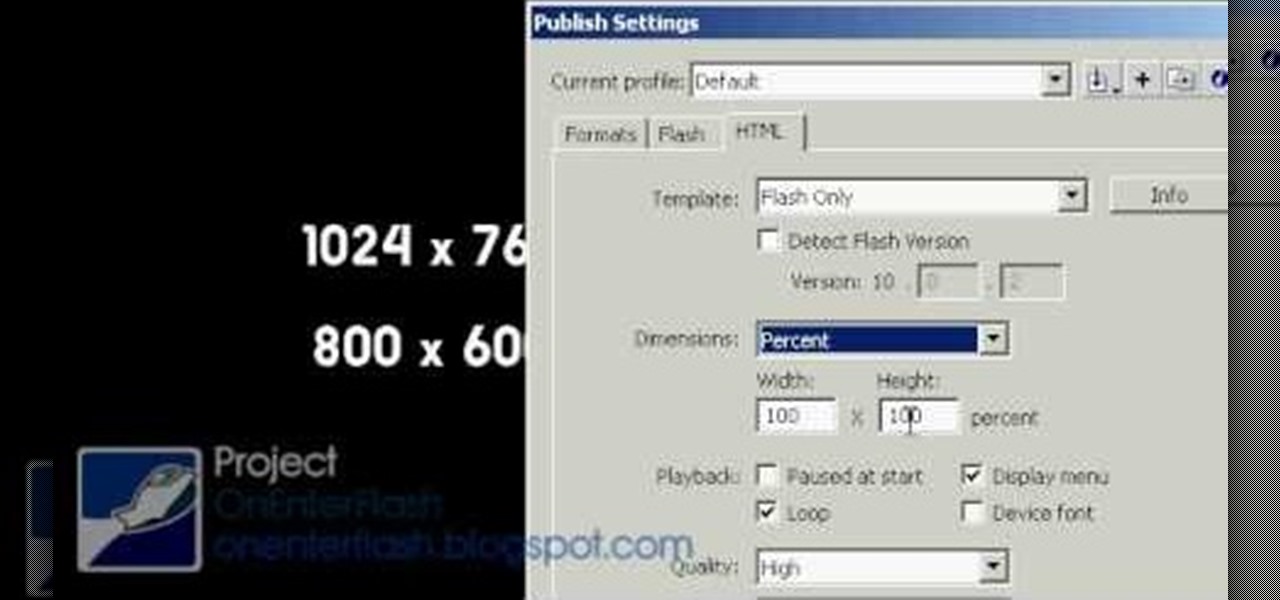
Creating a website from scratch is one of the most productive and most challenging things that you can do on a computer, whether the site promotes your own services and interests or you're being paid to make it for someone else. This nine-part video will walk you through the entire process of making a website using Flash CS4. It is very complete, and if you have the patience to watch all nine parts you should be well on your way to creating a really cool, high-traffic site.

So, you've just got yourself an Apple iPad, but it already needs fixed, or you want to check the innards out for yourself, you're going to have to know how to open that sucker up. This video tutorial will show you how to do just that.
Check out this informative video tutorial from Apple on how to organize your Mail in Mac OS X's Mail. See how to sort messages with rules, create smart mailboxes, and comlpletely organize your mail. Mac OS X. It's what makes a Mac a Mac.
Check out this informative video tutorial from Apple on how to use the basics of Mac OS X Mail. See how to set up mail with your email accounts, compose messages, add attachments, view attachments with Quick Look, and search through Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to use Mac OS X Mail to its fullest. See how to filter out junk mail, use data detectors, and view RSS feeds in Mail. Mac OS X. It's what makes a Mac a Mac.

Check out this informative video tutorial from Apple on how to add a blog to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a photo album in iWeb '09.

Check out this informative video tutorial from Apple on how to add a movie to your website in iWeb '09.

Check out this informative video tutorial from Apple on how to add a countdown clock in iWeb '09.

Microsoft ASP.NET is a free technology that allows programmers to create dynamic web applications. ASP.NET can be used to create anything from small, personal websites through to large, enterprise-class web applications. All you need to get started with ASP.NET is the free .NET Framework and the free Visual Web Developer. In this tutorial, you'll learn how to call your first web service in .NET. In just few minutes you'll be up and running with your own web service in .NET framework in ASP. F...

A good party guest should live by this motto: Ask not what the party can do for you, but what can you do for the party!

Welcome to Green Power Science! In this video tutorial, you'll learn how to make a HHO hydrogen generator. This is a very simple hydrogen generator. Watch the end, for there are some cool ignitions. These is a great way to get cheap alternative power sources.

It's no secret that Apple and Spotify haven't exactly gotten along in the past, but things are looking better than ever in iOS 14.5.

A successful startup needs more than a good idea. To get your startup off the ground, you need to know how to make a plan, fund it, and market it. Trying to learn how to do all of that on your own is impractical and unnecessary.

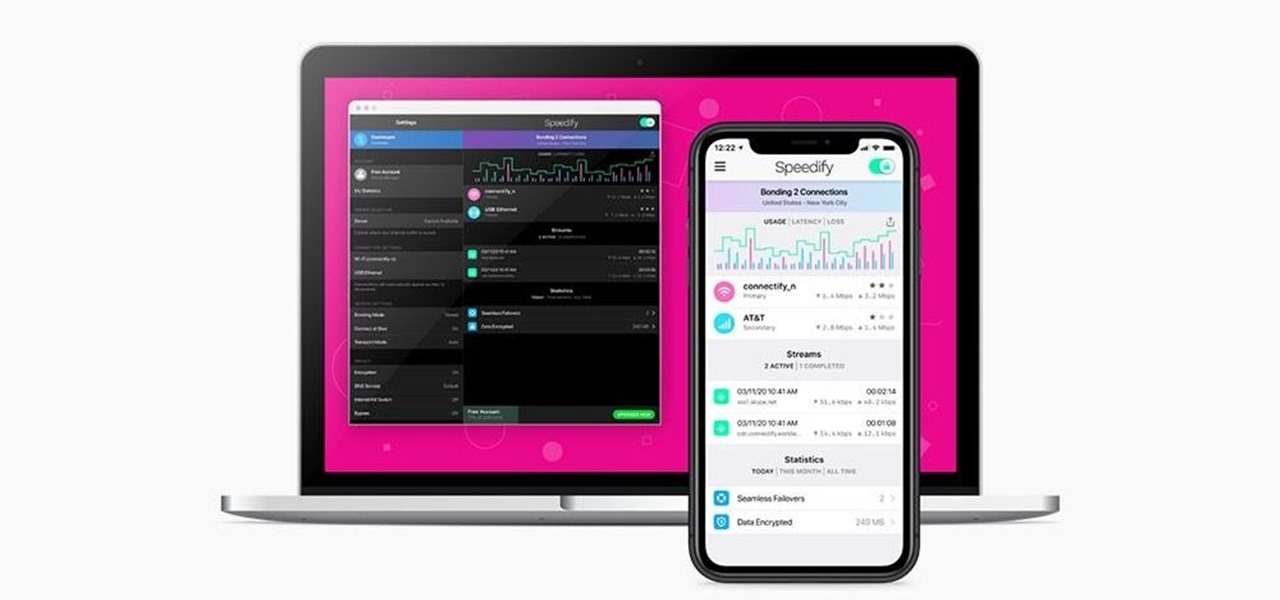
Using a virtual private network (VPN) is one of the safest ways to ensure your identity and data remain secure. Choosing one from the hundreds of services that now exist is another story. How do you tell which VPN truly provides the best protection at a great price?

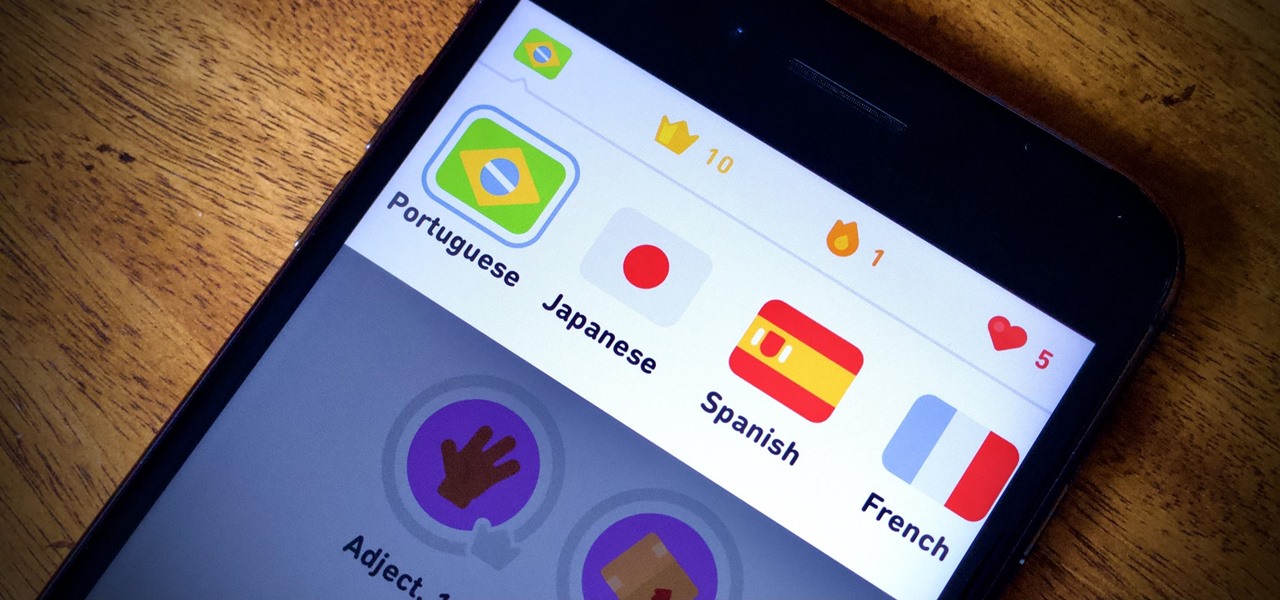
There's only so much Netflix and TikTok a person can take in quarantine before they've had enough. We've only just started our stay-at-home lifestyle, but already TV and movies are getting old. The COVID-19 lockdown doesn't just have to be a mindless watch party, so why not take the time to learn a new language?

Hey, you, still stuck at home? Cheer up, today is the first day of spring. Yes, really. And since you're probably locked in on TV, we're guessing you need a break from some of the less than sunshiney news reports rolling in. Well, no worries, because there's actually some good news to report.

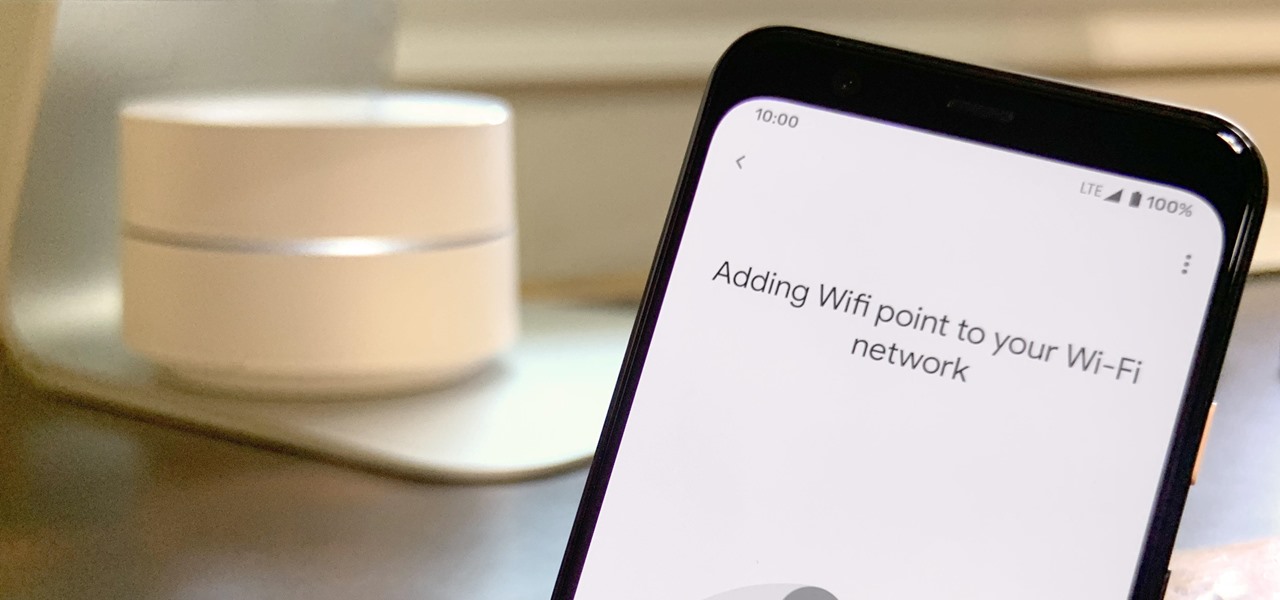
Google is known for merging older products into a new one's ecosystem for ease of use. The transition can take time, and that's the case with the old Google Wifi system now that Nest Wifi is out. Google is working on phasing out the dedicated Google Wifi app in favor of using the Google Home app for all your IoT needs.

Nearly every connection to the internet is dependent on the Domain Name System. DNS, as it's more commonly called, translates domain names like gadgethacks.com into IP addresses, which is what network devices use to route data. The problem with DNS servers is that they don't have your privacy in mind.

You may have recently seen a plethora of Instagram users, including celebrities and politicians, sharing a screenshot declaring that the platform will implement a new "rule" where it would own and could use your photos and videos however it wishes. The screenshots are part of an internet hoax, one that's been around in one way or another since 2012, but what can Instagram actually do with your media?

Smartphones are now indispensable when traveling. Domestic and overseas travel alike require food, navigation, translation, and so much more to make work or vacation successful. Gone are the days of lugging multiple tourist books around with you everywhere you go — you need to let your smartphone handle the dirty work.

News+ is Apple's new digital subscription service for written media that costs $9.99 per month. There is a free trial offered for one month, but you'll start getting charged the monthly fee as soon as your 30 days are up. While it's not very obvious, there is a way to cancel the auto-renewal right before you get charged.

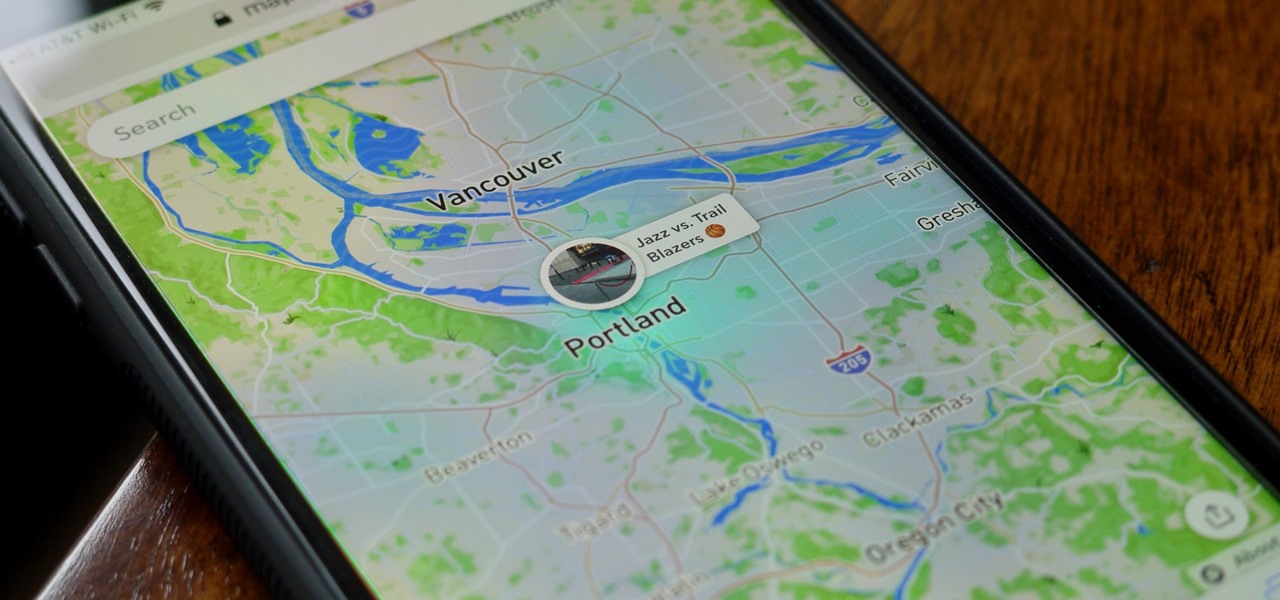
In about 27% of all car crashes, someone was using their cell phone. You may think texting is the big problem here, but many fail to realize that even the smallest smartphone interaction could spell disaster. Thankfully, Google Maps has rolled out an overdue feature that'll help ensure a safer drive.

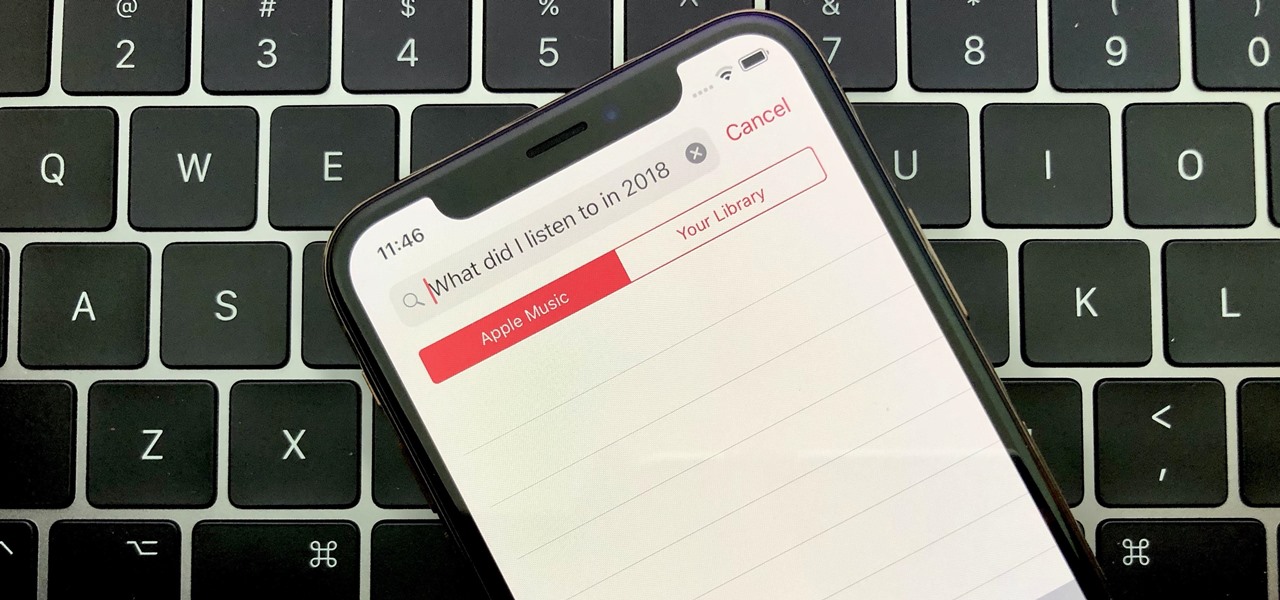
Around the end of each year, Spotify offers a year-in-review service so its users can see what they listened to the past year and share their listening histories in fun infographics. Apple Music does not have such a feature, unfortunately, but there is a way to curb that FOMO feeling this holiday season by downloading your listening history not just for 2018, but for the entire lifespan of your account.

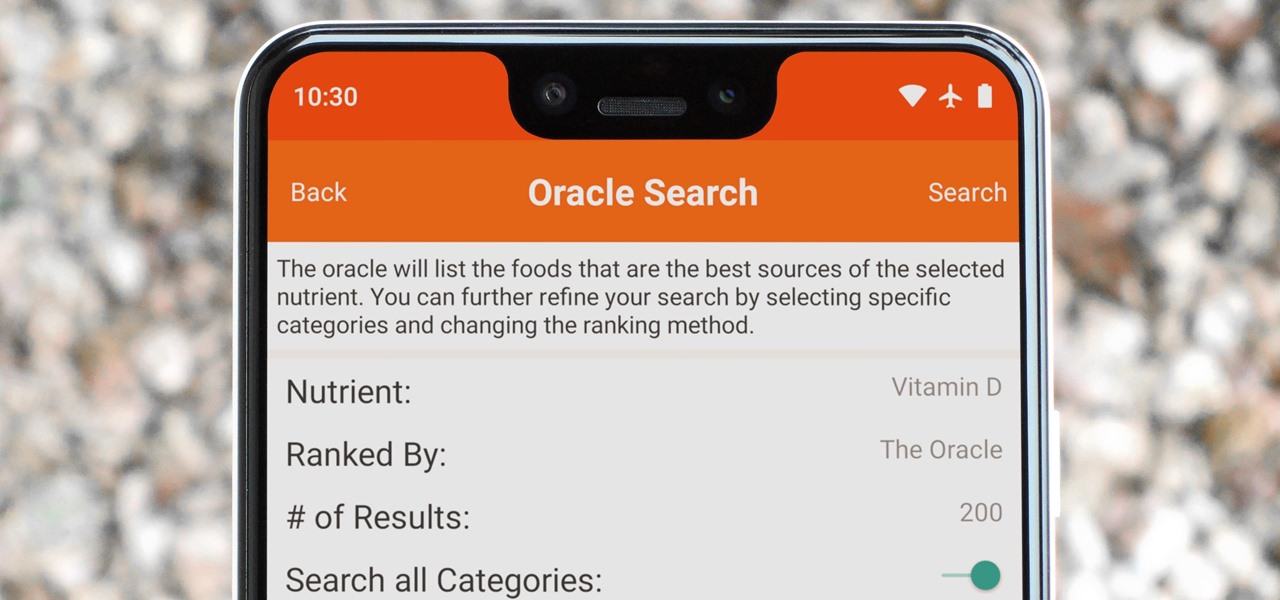
Micronutrients are essential to our health. Unfortunately, many of us aren't getting enough of each nutrient from our diets. It isn't that the food we're eating is bad, but rather we are not eating enough of the right food to get our recommended daily allowance. But with the help of a micronutrient tracker, we can change this.

MoviePass was once the best subscription service on the market for getting cheap movie tickets. For the price and the number of films you could see and save money on, it was unbeatable, but recent changes to the service have made it less enticing. While it still works well for some users, others may have to rely on other options. Personally, I'm leaning toward the latter.

Now that its first developer conference is in the rearview mirror, Magic Leap continues to nurture its content development community, this time with an assist from strategic investor and retail partner AT&T.

Hundreds of Windows 10, macOS, and Linux vulnerabilities are disclosed every single week, many of which elude mainstream attention. Most users aren't even aware that newly found exploits and vulnerabilities exist, nor that CVEs can be located by anyone in just a few clicks from a selection of websites online.

A week after the L.E.A.P. Conference, our cup of Magic Leap news continues to floweth over, with the company's content chief giving us some insight into the company's strategy, and Twilio sharing what its virtual chat app looks like.

Having an efficient workflow is an integral part of any craft, but it's especially important when it comes to probing apps for vulnerabilities. While Metasploit is considered the de facto standard when it comes to exploitation, it also contains modules for other activities, such as scanning. Case in point, WMAP, a web application scanner available for use from within the Metasploit framework.

Transferring hundreds of screenshots, webcam recordings, keystroke logs, and audio recordings between your VPS and a local Kali machine can be tricky. Services like Dropbox don't always have the best privacy policies and suffer data breaches just like any other website. To mitigate these risks, we'll use a secure, open source, and decentralized alternative.

After two dramatic Conference Finals, the dust has settled to reveal ... the Golden State Warriors and the Cleveland Cavaliers. Well, at least the Irving-less Celtics and Rockets (short of Chris Paul for Games 6 and 7) gave it their all. With these teams battling for the fourth straight time, people want to know if the Cavs can even up the score at 2-2.

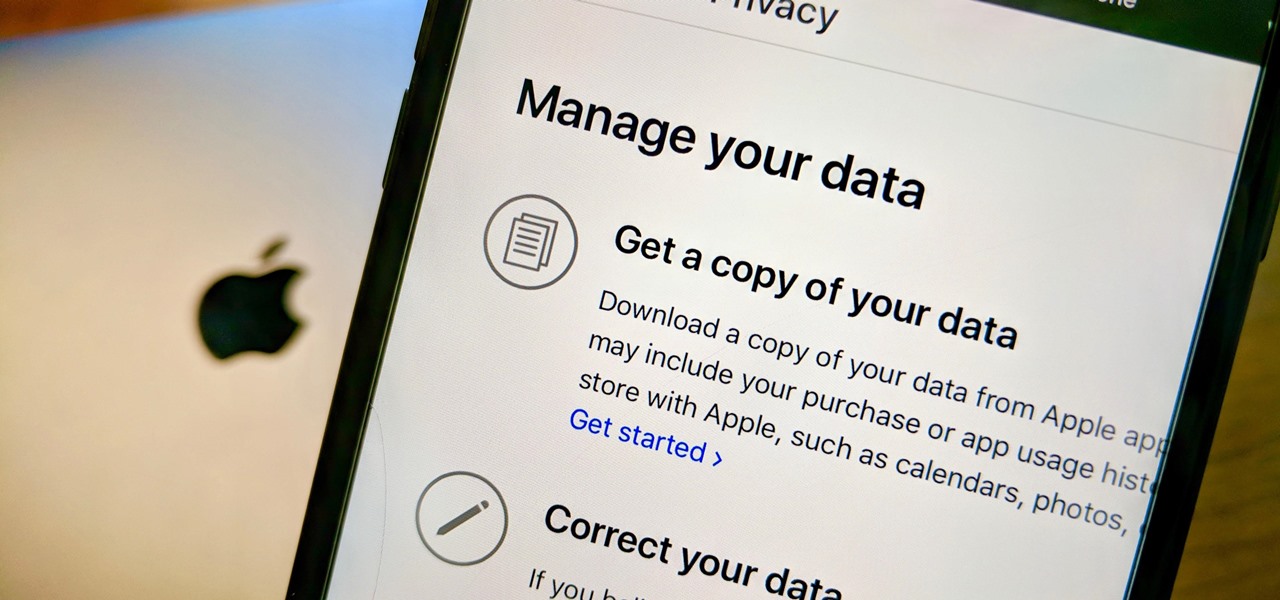
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Smartphones are like high tech buckets that collect our personal information through constant use. This has some obvious benefits, like getting a more personalized experience with our devices. On the other hand, this data is a tempting target for bad actors looking to make a buck at the expense of your privacy.

While it's easy enough to make yourself invisible on Snap Map, nothing is quite as private as not having a Snapchat account at all. Whether you're concerned about your privacy or you simply never signed up for the social media platform, Snapchat's web-based map is an easy way to check in on what's happening in your area and beyond.

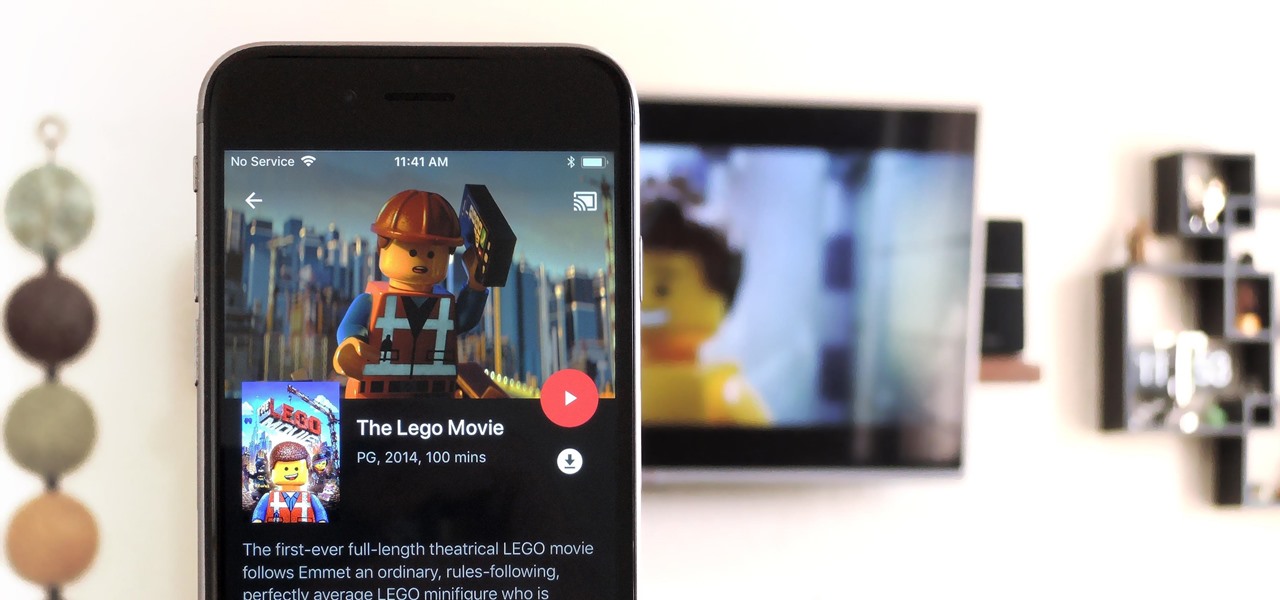
Google announced a partnership with Movies Anywhere that allows you to connect your iTunes, Amazon, and Vudu movie library with Google Play Movies. In other words, movies you purchase from any of these online retailers will be available for playback in the Google Play Movies app after a little setup.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

When hacking into a network during a penetration test, it can sometimes be useful to create your own wireless AP simply by plugging a Pi into an available Ethernet port. With this setup, you have your own backdoor wireless connection to the network in a matter of seconds. Creating an AP is also helpful while traveling, or needing to share a connection with a group of people.