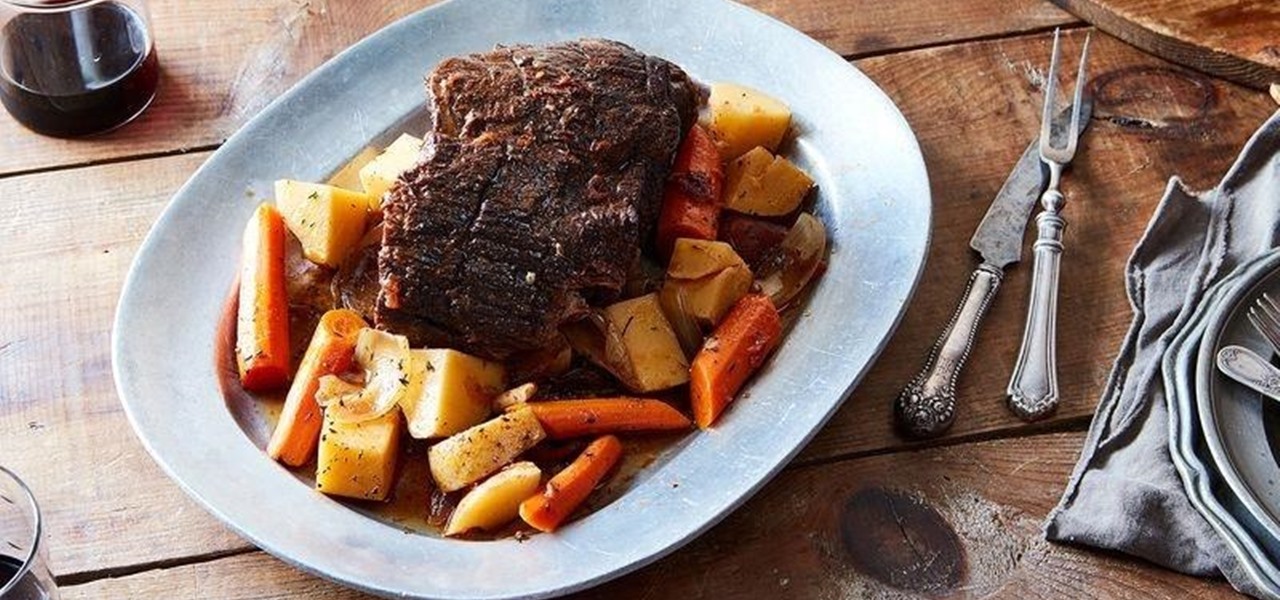We've been hearing some interesting rumors in the last few days that are stirring up all kinds of speculation about the potential upcoming consumer release of the HoloLens. However, MSPoweruser has speculated a bit further past the consumer HoloLens release to a possible HoloLens 2 as soon as Q3 2017.

Microsoft and Unity have been working closely to make sure that HoloLens and Windows Holographic are supported closely with the popular game engine. Unity released a special HoloLens Technical Preview version earlier this year based off of Unity 5.4, but the update today of the main Unity app, version 5.5, has all those Holographic enhancements built right in.

In recent years, wave after wave of technological advancement has led us down roads that are beginning to look more and more like science fiction stories. In their efforts to bring us from science fiction to science fact, Microsoft Research showed us a new communication medium called Holoportation earlier this year—and now they have found a way to make this highly complex holographic system far more mobile.

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

In recent weeks, Unity has made a few great leaps forward for HoloLens development. These new features will increase iteration speed inside Unity and quickly increase the output of applications in the mixed reality space. Of these new features, let's take some time to talk about Holographic Emulation and why this will do so much for the development community.

Every recipe on the face of this planet (okay, maybe a slight exaggeration there) ends with the same six words:

Ah, ginger. From stir fry to smoothies, ginger is a reliably sharp and refreshing flavor that adds zing to everything it touches. It may be a pain in the ass to remove the skin from ginger (or not), but the zest it brings to food is well worth the trouble. Don't Miss: How to Brew Your Own Ginger Beer Like a Boss

Out of all of the "odd couple" food pairings you could imagine, this has got to be one of the outright weirdest.

Fall is here, and it's time for warm, filling meals... that don't involve a lot of effort, because it is getting cold outside and you spent a full day at work wishing you were on the couch with a blanket over your head, dammit.

This is a Q&A video with the question asking if glaze putty can be applied over primer or not. In this short Q&A video I am going to answer this question.

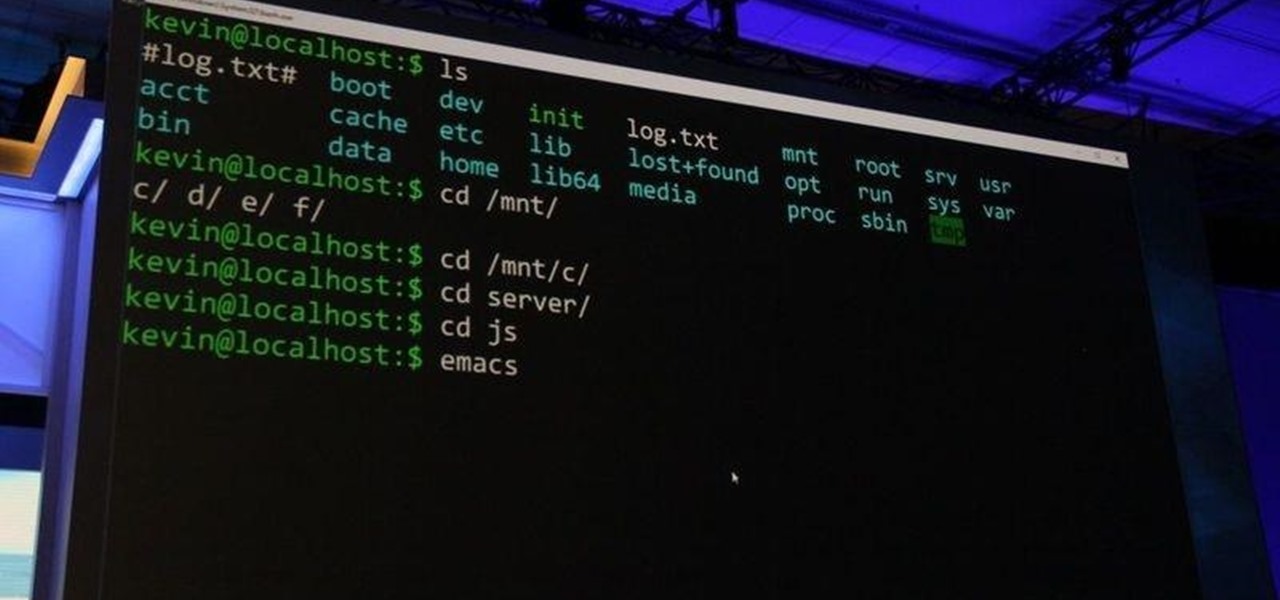
As most of you know, I am a strong advocate for using Linux for hacking. In fact, I would go so far as to say that you cannot be a hacker without knowing Linux well. I laid out various reasons for this in my "Why Every Hacker Should Know & Use Linux" article, and I even have a lengthy, continuing series on Linux Basics to help those new to Linux master it.
Hello guys I am ROMEO 64 (sounds weird I guess but who cares. :D).. Alright....Ever wondered what happens when you login to your Facebook account?

It seemed appropriate that we announce the winner of the first White Hat Award for Technical Excellence on the Academy Awards weekend. This is, in essence, our "Oscar" here at Null Byte. Remember, this contest began on January 4th, 2016 and just recently closed on February 15th. In this contest, I was looking for:

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need

We all know them, and many of us despize them. And some might support them, regardless many have different opinions.

If you're running iOS 10 or lower, there is no built-in way to make a screen recording on an iPad, iPhone, or iPod touch directly from the device, but that doesn't mean there isn't a way to record your screen at all.

A trip to any grocery store's produce section will quickly reveal that bananas are often picked from the tree well before their prime—which is necessary for them to arrive at our local store without going bad. In fact, bananas are refrigerated en route to our supermarkets in order to stave off the ripening process... which makes sense, since they travel quite the distance (from the Tropics around South America or Africa to our proverbial doorstep).

to stay secure, you dont just need Tor, and a VPN. You need good browsing habits. What are Browsing Habits You Ask?

Hello, my fellow hackers. My name is cl0ck. I am a senior majoring in Computer Engineering with an emphasis is Security. I have been lurking the site for a while now reading and learning from the great minds that reside here. I, too, have some knowledge that I would like to share with all of you. This post actually comes from a personal problem I faced and had to find a solution for. Without further ado, here it is:

Hello there, reader! If you've clicked on this How-to then it means you are interested in learning some C programming or just generally curious about what this page has to offer. And so I welcome you warmly to the first of many C tutorials!

You want to become anonymous, and dont want your IP to be logged on websites? Well read along here. Continuing This Series:

I found this article a while back and I found it underneath a bunch of junk. Anyway, it's a article on 9 notorious hacker including Walter O'Brien (You know the T.V. show Scorpion? Well that's him). Not to mention the weird names:

Hello everyone Today I will show a different way to exploit a windows machine with a reverse https payload..."wait...why https? Isn't tcp good anymore?"
Hello! My name is An0nex. I am an ethical hacker who wants to share the art of hacking with all of you guys!

Windows has always been pretty customizable, and there are a ton of ways to change up the way your PC looks—though, it hasn't always been easy. In the past, changing anything other than wallpapers, titlebars, and fonts involved long hours of switching out system files with modified versions and changing icons to no end, but that's not the case with SkinPacks.

Hello, fellow grey hat hackers and aspiring coders. I'm back again with another python tutorial. Just that this one is gonna be a lot cooler ;-). We gonna make an encryption program, that well you know encrypts all the files on your pendrive or hdd or whatever you want....Also lots of thanks to DrapsTV. They have helped me a lot with Python and making awesome programs. The video is here:

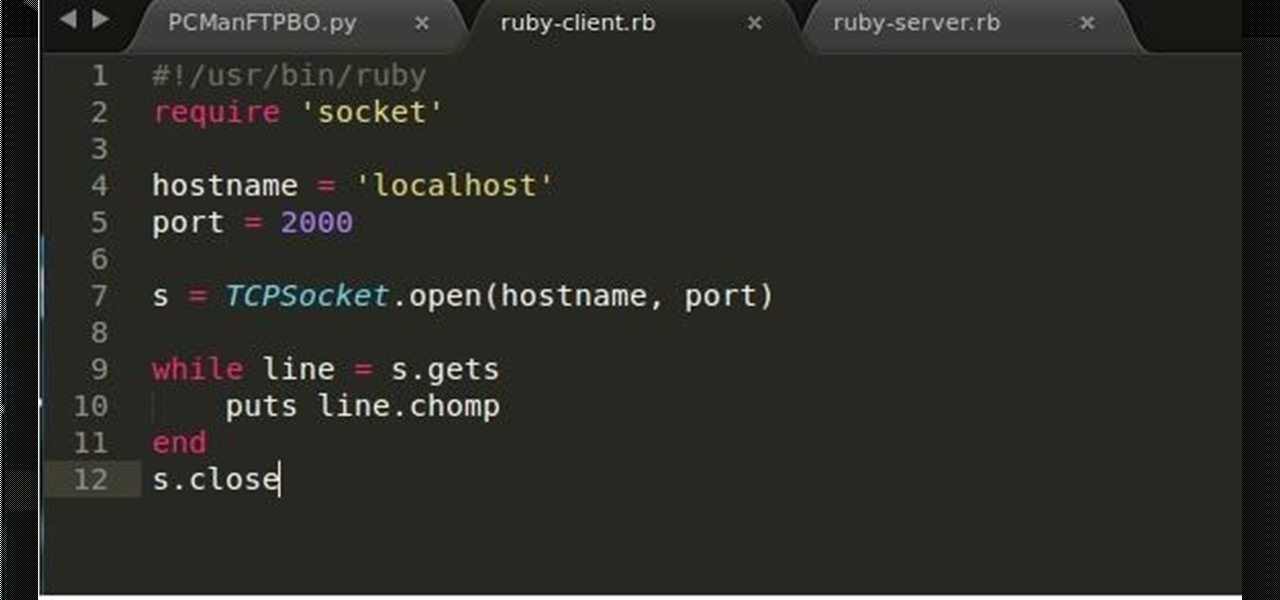
Ruby is a dynamic, general-purpose programming language created by Yukihiro "Matz" Matsumoto in Japan around the mid-90's. It has many uses but with it's flexibility, it makes a great language to write exploits in. In fact, the entire Metasploit Framework is written in Ruby! The sole purpose of this series is to teach hackers the basics of Ruby, along with some more advanced concepts that are important in hacking.

Recently, I've been learning Ruby as a second scripting language. But one topic I never covered with the many lessons online were sockets. So I did some research and came up with a very simple client/server connection that sends a string over the socket.

MagicTree is often the go-to tool for data collection and reporting for many pentesters. It organizes data in nodes in a tree-structure which is very efficient at managing host and network data. Reports can be completely customized to meet the user's needs. Also, MagicTree allows you to import XML data and has XSLT transforms for Nessus, Nmap, OpenVas, Burp, Nikto. MagicTree comes pre-installed in Kali.

This tutorial is for people who want to try different types of hacks in an environment that is the same for everyone so it will help people to ask questions and learn. This series assumes you know how to run a VM and network them together. This series also assumes that the services running on the Metasploitable machine are needed to be running.

Welcome back, my hacking friends. We use our smartphones every day, for business, socialization, and leisure. The number of iPhone users is increasing in dozens of millions every year, with a whopping 63.2 million users in 2014 alone. That's a lot of users.
Hello and Welcome back to another How-To on the Xbox Community Ambassadors World! In this How-To, I am going to tell you and kinda show you how to deal with or avoid angry Xbox Customers.

Before I start this tutorial, no, this is not that "Effective. Power." text that is going around. With that being said, let's talk about this attack.

As crazy as it sounds, there are times when bottles of wine go unfinished. I love a glass or three of vino, but am often guilty of not finishing the bottle. Sometimes I don't have the time to finish it, and other times I like it so much that I open bottle number two and can't finish that.

Hi all, Pro Hackers/Crackers, Let's see how we can use batch for our own Protection instead of exploiting someone with it.

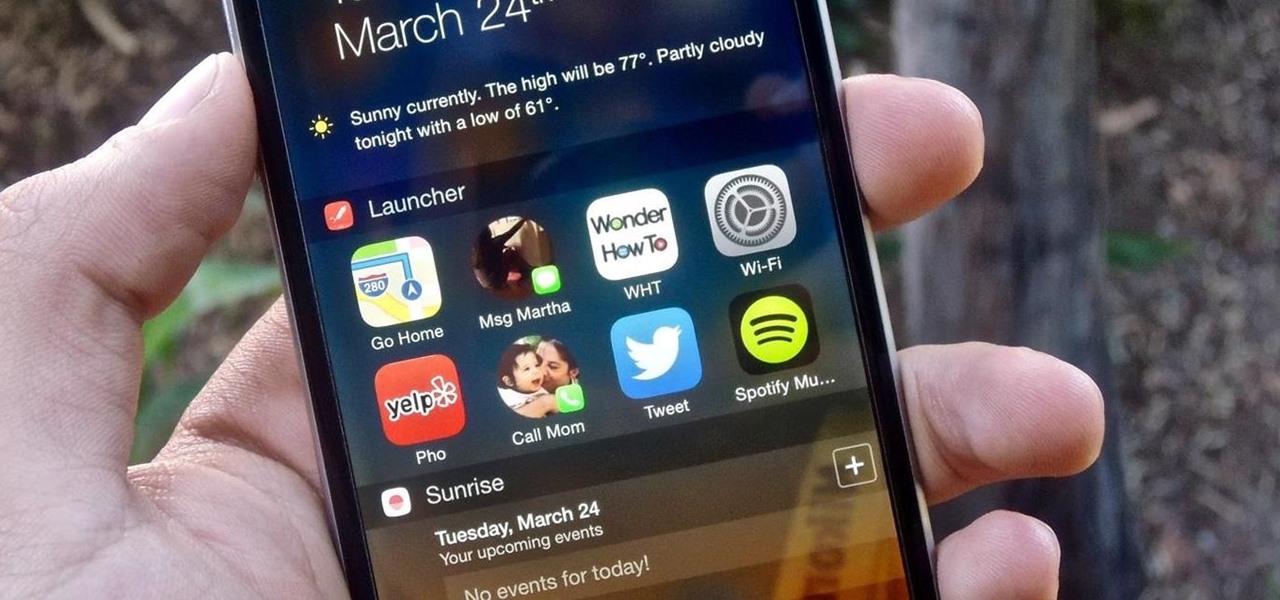
An app called Launcher was released for iOS 8 last September that let users open any installed app directly from a widget in the Notification Center pull-down. For some reason, Apple didn't take too kindly to this and banned Launcher from the iOS App Store just a few days after its release.

After you have registered to this site,sign in then to start missions. Basic Missions

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

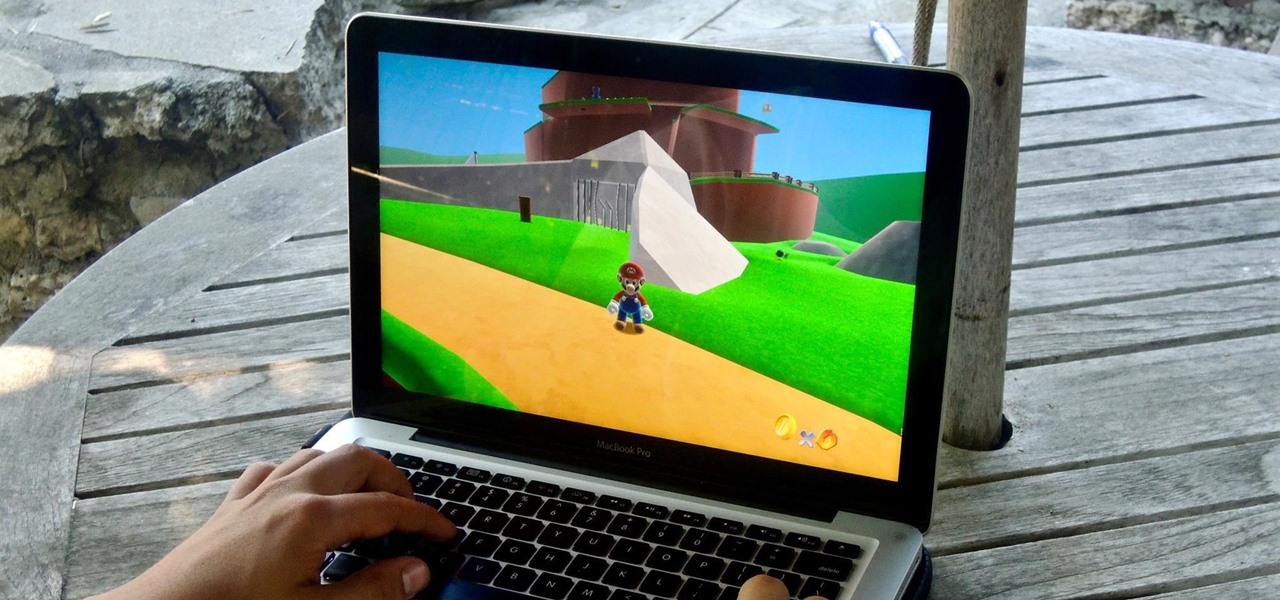
Yup, you read that right. As of now, you can actually play the first level of one of the most popular video games of all time—Super Mario 64—directly in your web browser.