
Gameday! Bring on the best and most evil pranks. Humiliate those closest to you. This devastatingly simple office prank requires nothing out of the ordinary to perform. In fact, you could probably execute this right now, without getting up from your chair.

Yes--- they're really producing a documentary on making chocolate milk. This is very simple, but the home brew commentary is the allure. Really, we just like the girl giggling.

The "wood-chopper" isn't just for lumberjacks. You can get the full woodsman workout yourself, without the axe! Men's Health shows you how to do the wood-chopper exercise, and when you power through this move, your upper and lower body, along with your core muscles, are working to the max.

Doing this workout from Men's Health will increase flexbility and strength in your rotator cuffs. Make sure to execute technical precision to avoid injury.
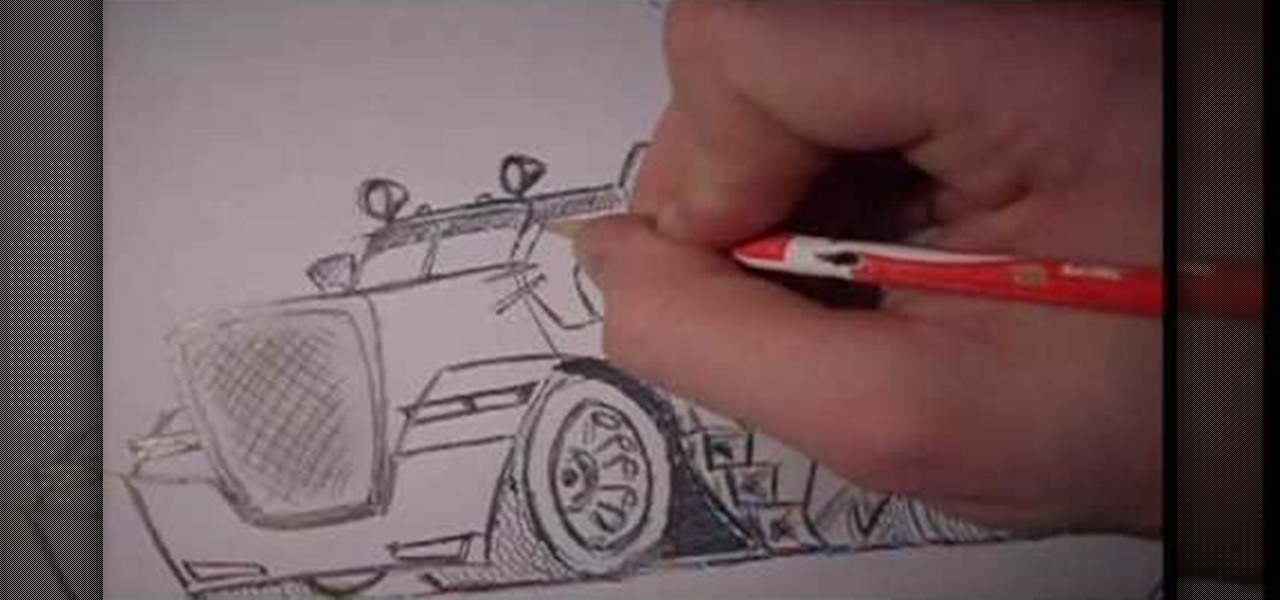
This video demonstrates how to draw a caricature of a truck. Begin with a rectangular shape that is slightly bigger at the top and has rounded corners. This will be the grill. Create an inside border. Below the grill, draw a front bumper. At the top corner of the grill draw a rectangle that is divided into two halves and shade the top section of each half. This is the windshield. Draw hatch marks in the center section of the grill. Above either side of the bumper add narrow divided rectangles...

With an inconspicuous Android phone and USB flash drive, an attacker can compromise a Windows 10 computer in less than 15 seconds. Once a root shell has been established, long-term persistence to the backdoor can be configured with just two simple commands — all while bypassing antivirus software and Windows Defender.

When you have an infection, a doctor prescribes antibiotics to make the bacteria that causes it disappear. Sounds like a good idea, but the disappearance of microorganisms that have inhabited humans for millennia could be driving rising numbers of serious illness and debilitating conditions.

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

This simple video crocheting tutorial shows how to execute a triple or treble crochet stitch. Learn how to crochet this stitch very useful for Japanese amigurumi projects or any other shaped crochet project. Crochet a triple or treble crochet stitch.

Who says Vegas is only good for gambling? This is a level-by-level walkthrough (on realistic difficulty) of Rainbow Six: Vegas for the PS3, XBox 360, and PC. A helpful voiceover commentary is included.

Learn to play golf like Tiger Woods in this rather effusive recreation of a memorable shot in Championship Golf History. In this Great Shots video from GolfLink, golfing professional Joe DeBock from Torrey Pines golf course in La Jolla California demonstrates the chip-in on the 17th at the 2008 Open, on the actual golf course where Tiger did it. This instructional video is accompanied by verbose commentary on the historical event, the famed golfer, and the course itself.

Kung fu is an ancient Chinese martial art that combines technique, balance and power into an effective fighting style. Learn several beginning kung fu combinations with tips from a professional kung fu instructor in this free martial arts video series.

This match involves a queen sacrifice to promote, along with a queen/king checkmate. See how it's done, and listen to a great commentary to learn from.

Rich Dad, Poor Dad author presents commentary on how money can manipulate or be manipulated. Make money work for you.

You can get strong ripped abs by letting your inner child loose! By combining playground exercises and cardio you can have washboard abs that you are proud of. This video shows how to properly execute playground type exercises such as pull-ups to strengthen your arms and push ups to work your arms, back and chest. Follow along to find other quick and easy exercises that you can incorporate into your every day life to get the body you've always desired!

Knowing how to properly set up your mounts for cheerleading will help you execute your stunts safer and better. Learn how to do some stunt mounts in this video tutorial.

The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

The line dance is a dance with repeated sequence of steps in which a group of people dance in one or more lines, all facing the same direction, and executing the steps at the same time. Line dancing's popularity grew out of the 1970's, when the country-western dance continued to explore and develop this form of dancing.

Learn how to practice quick decision making (pass or shoot) when on the high post and establish good basketball game rhythm. Videos two through four cover when and how to execute each option: jump shot, seal the post (pass the ball down to the player at the low post), and swing the ball (after setting the pick and sealing the post).

XSS stands for cross-site scripting, which is a form of web-based exploitation that uses client-side vulnerabilities in a web page to execute malicious JavaScript codes. JavaScript is referred to as "cross-site" because it usually involves an external website containing the malicious code. That code is most commonly used to steal cookies with a website that the attacker created and hosted on another server. The cookies can then be used to escalate privileges and gain root access to someone's ...

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Command injection is a technique used by hackers to execute system commands on a server, usually via a web application or some kind of GUI. This can happen when an application provides some sort of functionality to the user involving the use of system commands. When the input is not properly sanitized, commands not originally intended to be run are allowed to be executed.

Sex makes the world go 'round, and when it does, so does gonorrhea. Finally some good news on the growing menace of drug-resistant gonorrhea — a large, long-term study shows a vaccine may work in reducing the incidence of an increasingly dangerous infection.

Welcome back to control structures, part two featuring the three types of loops. Here we go! What Is a Loop?

If you forgot about April Fool's Day, you're going to have to get creative if you want to pull off some not-so-predictable pranks last minute. To help you with that, in this video you'll learn how to set up and execute 5 of the best last-minute April Fool's Day pranks. April 1st will still be a fun day for you, your friends, and family... just watch!

Ah, Halloween—the funnest, but scariest day of the year. You don't just dress up and go door to door asking for candy—it's the best day to pull off scary/spooky pranks.

Aikido has countless wrist grab forms and techniques for any method of martial arts self defense someone might need to call upon. Learn many of these tips from an Aikido expert in this free video clip series.

For all of you PS3 owners who got addicted to the wonderful puzzle platformer LittleBigPlanet, your hopes and dreams have finally been realized— LittleBigPlanet 2 is now out! Originally set to be released in November of last year, Media Molecule's LBP2 was in stores last Tuesday, January 18th.

kicks since they require greater balance and strength than basic kicks. Learn kung fu jump kicks in this free video series on kung fu training.

A certified strength and conditioning specialist, demonstrates the fat burn circuit with the Powertec Workbench Multisystem. He talks about maintaining muscle, gaining muscle, and losing fat with the right set of workouts. In this workout, you will need to use a circuit which involves moving from one exercise to another and doing everything in the same order several times in a row.

30 Japanese schoolchildren, leg-to-leg. And they're good. Really good. What was I doing at that age, in the neon-lit elementary school gymnasium? Square dancing. Sweaty-palmed square dancing.

Video walkthrough of the Uncle Vlad mission i nGrand Theft Auto 4, in which Niko executes Vlad for all of his treachery. Beat the Uncle Vlad mission in GTA IV.

Don't butcher another interview. This video offers you an 8 step process towards executing a successful interview and winning that desired job! Perform effectively in a job interview.

Compromised uTorrent clients can be abused to download a malicious torrent file. The malicious file is designed to embed a persistent backdoor and execute when Windows 10 reboots, granting the attacker remote access to the operating system at will.

Well-regarded men from the history of the United States tend to grace the country's currency, but what if equally deserving women were honored in the same fashion?

Backdooring a powered-off MacBook is easy when a few minutes of physical access is allowed. That attack works well if the hacker also shares a Wi-Fi network with the victim, but this time, I'll show how to remotely establish a connection to the backdoored MacBook as it moves between different Wi-Fi networks.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

In our previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when an MS Word document is opened. Because Microsoft built DDE into all of its Office products as a way to transfer data one time or continuously between applications, we can do the same thing in Excel to create a spreadsheet that runs malicious code when opened. The best part is, it will do so without requiring macros to be enabled.
Hello everyone! This is my first attempt at a tutorial here. There are a couple great assembly tutorials here, and I wanted to toss my coin in the fountain.







































