Welcome back, my hacker novitiates! There are many ways to hack databases, and most of these techniques require SQL injection (SQLi), which is a way of sending SQL commands back to the database from a web form or other input. In this tutorial, we will use SQL injection to get access to the underlying server. So instead of getting access to the database and its data, we will use the database as an intermediary to gain access to the underlying server.

I'm sure that many of us have heard of that nasty Shellshock vulnerability, but not very many people know how to exploit it. Try these few tricks on vulnerable websites!
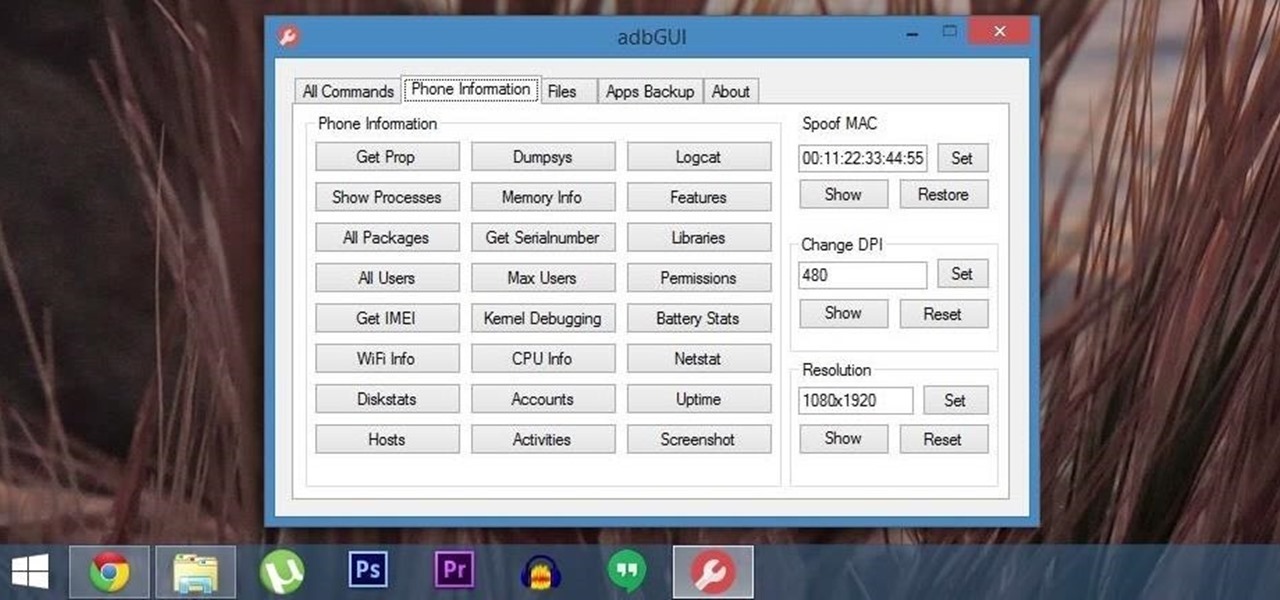
Android Debug Bridge (or ADB for short) serves as a remote terminal interface for executing shell commands on any Android device. Put simply, ADB lets you send commands from your computer to your phone or tablet, some of which would require root access if they were performed on the Android side of the connection.

If you've ever attempted to report a bug to a developer, no doubt you've heard the response, "Get a logcat." This is infinitely important to a developer because of the fact that a logcat captures a full report of every command that was recently executed on your Android device, and it allows them to see exactly where something went wrong.

Personally, I think Velveeta is pretty gross. Nothing about its texture, flavor, or color resembles real cheese. But your taste in cheese isn't the important part—what matters is having something good to eat while you watch the game.

Once when I was a kid, my dad used a glue trap to catch a mouse in our basement. The result was so awful for the mouse that my mom and I made him promise to never use that kind of trap again. Call me a softy, but I'm a firm believer that you don't have to kill pests to get rid of them.

When it comes to our smartphones and tablets, we're always on the lookout for ways to beat the oh so common rapid battery depletion problem that affects practically every mobile device. We'll do anything and everything to keep our battery life at an optimum, from turning off certain features (Wi-Fi and Bluetooth) to removing widgets and applications that use an exorbitant amount of CPU. One of the most popular and efficient ways of saving battery is to lower the screen brightness. Usually, we...

Well, maybe not a real invisibility cloak—sorry Harry Potter fans—but a team of scientists at MIT's SMART Centre are on their way to producing materials that mimic actual invisibility.

Yao Lu: Sustainability Visualized Yao Lu has created a thoughtful and timely series inspired by traditional Chinese paintings entitled New Landscapes in which mounds of garbage covered in green protective nets are assembled and reworked by a computer to create images of rural mountain landscapes shrouded in the mist.

Kung fu is an ancient Chinese martial art that involves using powerful punching techniques. Learn several punching combinations from a professional kung fu instructor in this free video series.

Aikido has countless wrist grab forms and techniques for any method of martial arts self defense someone might need to call upon. Learn many of these tips from an Aikido expert in this free video clip series.

Comic-Con International: San Diego, better known to you and I as "San Diego Comic-Con", is coming very soon; and if you're like me and live far, far away from San Diego (sigh), Twitter is now offering a helpful alternative to keep you in the loop at this year's event.

I've had a thing against bananas ever since Mario Kart; not only do I believe it's the worst weapon in the game, but it's also a very funny-looking food. Nevertheless, bananas are a great source of potassium, and I can't overlook that.

There are very, very few things better than a solid Hobbit songI mean, I was almost brought to tears when Pippin busted out this one in The Lord of the Rings: Return of the King.

These days, when people say "gaming", you think of Xbox 360 and PlayStation 3. Even the Wii. How could you not, with games like Black Ops, Gran Turismo 5 and Wii Sports in every retail store known to man? But if you're the type of gamer who sits in front of the computer screen playing MMORPG, MMORTS and sandbox games, then gaming has an entirely different meaning. If you don't know what those mean, then you've probably never heard of games like World of WarCraft, StarCraft II and more importa...

Every day of the week, WonderHowTo curators are hard at work, scouring the web for the greatest and most inspiring how-to videos. Every Friday, we'll highlight our favorite finds.Make a fireball you can hold in your hands.

World Cup For Free: No TV, No Cable, No Subscriptions Necessary!!! Stuck in the office during an important match? Here's a quick guide on How To Watch World Cup for Free, Live, Streaming Online in the US....

The Costume All you gotta do is dress up like a fly, go to a zip line place (i know they got'em in California).

This is a helpful soccer video because it gives you tactics from both sides of play. Taken from a training routine from the Spanish Football Federation, the video improves your team's ability to retain possession of the ball while also breaking down offense moves in terms of what defense can do to prevent them.

Election day is less than two weeks away and the political rhetoric is at an all time high. From the constant political commercials to the endless cable news coverage, it's hard to escape the noise. And nothing is worse than your social media sanctuaries being invaded by some clown's personal political insights.

WonderHowTo is game on. Note for the devoted gamers with a code of ethics: spoiler alert. This cheat exemplifies the argument that video games are modern social commentary. Just when you thought this game was only about shooting hookers and scoring drugs. This odd Easter Egg gets to the heart of Liberty City, literally.

Without admin privileges, installing additional software, or modifying the Windows 10 firewall, an attacker can alter a router and perform a variety of exploits. It's accomplished by forwarding requests from Kali through a backdoored Windows computer to the router gateway with simple SSH tunnels.

UnrealIRCd is an open-source IRC server that has been around since 1999 and is perhaps the most widely used one today. Version 3.2.8.1 was vulnerable to remote code execution due to a backdoor in the software. Today, we will be exploiting the vulnerability with Metasploit, examining the underlying code to understand it, and creating our own version of the exploit in Python.

Microsoft.com is one of the most extensive domains on the internet with thousands of registered subdomains. Windows 10 will ping these subdomains hundreds of times an hour, making it challenging to firewall and monitor all of the requests made by the operating system. An attacker can use these subdomains to serve payloads to evade network firewalls.

The newest version of macOS has arrived. While everyone's mind is being blown by Mojave's groundbreaking new Dark Mode, we'll be taking advantage of its insecure file permissions to establish a persistent backdoor with a self-destructing payload that leaves little evidence for forensics.

It is often said that the best hackers remain unknown, and the greatest attacks are left undiscovered, but it's hard for an up-and-coming penetration tester or white hat to learn anything unless one of those factors is actually known or discovered. But the end goal here in our SQL injection lessons is to make that statement as true as possible for us when performing our hacks.

It turns out that coming up groundbreaking technology and raising billions may actually be the easy part for Magic Leap, as a new report has revealed yet another legal entanglement at the Florida-based company.

In one of my previous articles, I discussed ShinoBot, a remote administration tool that makes itself obvious. The goal is to see if the user could detect a remote administration tool or RAT on their system. In this article, I'll be demonstrating the use of Pupy, an actual RAT, on a target Ubuntu 16.04 server.

Usually, when I see a video that is captioned "wait for it," I'm quick to dismiss what could possibly come at the end of the clip. In this case, however, I was totally wrong and the final result was definitely worth the wait.

Sup? Today, we'll be learning about for loops in Java: What they are, how they work, and how to create them.

Welcome to a tutorial on crypting technology. In this article, we will be discussing types of crypters, how they work and why they work. After defining these, we will then make our own basic crypter using the function I gave to you as a task to complete by yourself in the previous tutorial.

In this article I will show you how to obtain victim's credentials without cracking any hashes. There are a couple of ways to perform this task (for example dumping the SAM file and cracking the NTLM hashes), but here I will explain how to do it using PowerShell and a bit of social engineering. We are going to create a fake login popup.

Your English teacher is a creep. The way he looks at your girlfriend, the way he always spends ages with the girls in the class going over their work but not the boys, just the way he is.

Now that we have control over a victim's browser, we need to use some attacks to maintain the connection, or even better: upload a shell.

OTW's great Tutorial Hack Like a Pro: How to Save the World from Nuclear Annihilation gives me the inspiration to try this on Win7 sp1.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

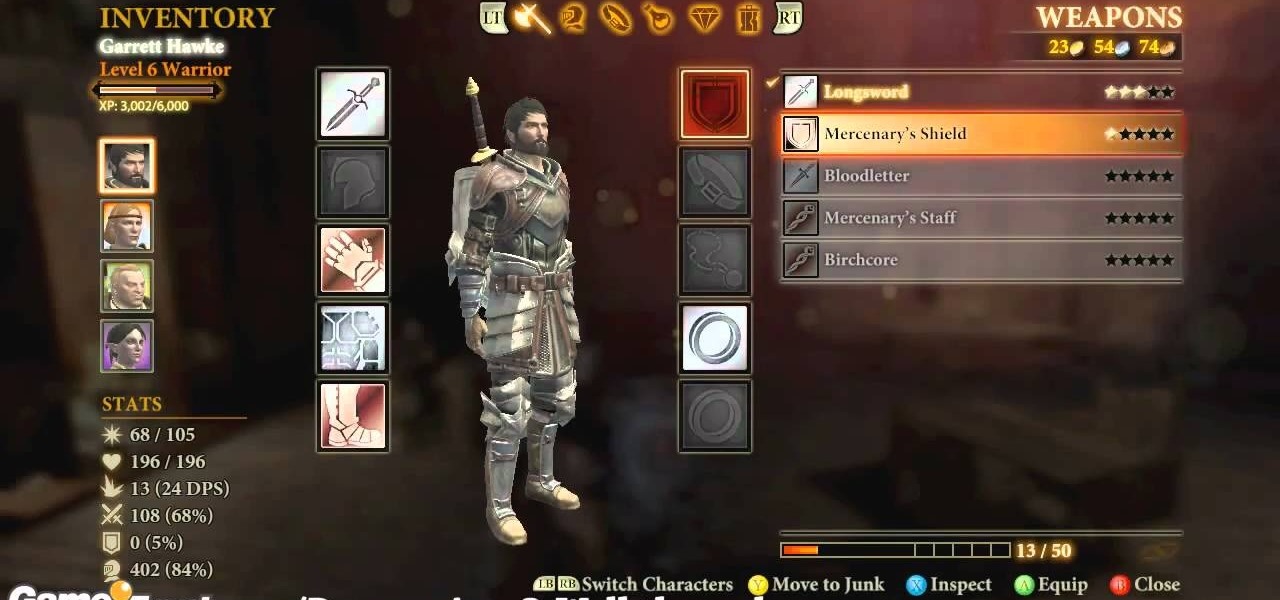
Dragon Age 2 seems to have more awesome and easy-to-execute exploitable glitches than any game in a long time. It almost seem deliberate, which would be a really awesome move on Bioware's part. This video will teach you how to use a really simple inventory glitch to max out any character's armor stat at 100% in less than a minute. You will be almost indestructible, and you can stop whenever you want if you just want a more reasonable boost.

To get the Guerilla Tactics achievement / trophy in Bulletstorm, you must execute 25 skillshots in a single Echoes map. Skillshots are the most fun part Bulletstorm. This video will give you a handy step-by-step guide to getting the achievement in Collapsed Building.

First, you will need a gallon of milk that's about a quarter full. It's best if you empty out the contents, but make sure to save it though because you will be needing it later.

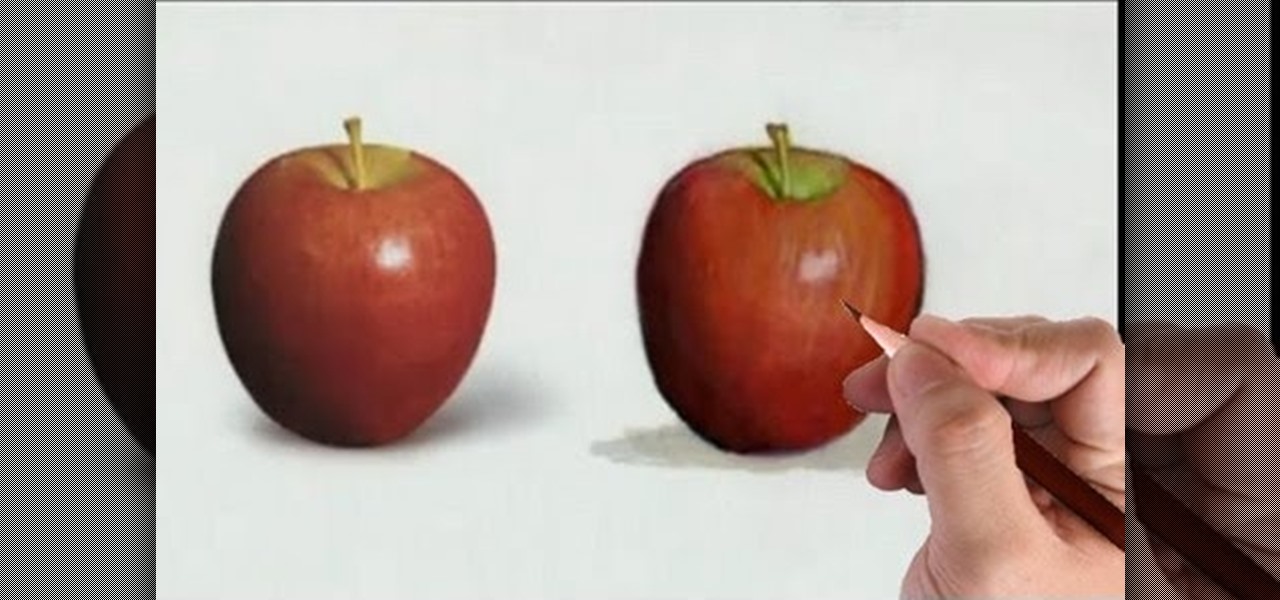
Watch this fine art video tutorial to learn how to illustrate with markers and colored pencils. "This video shows my process for making an illustration (non tradigital). I use illustration markers (usually prismacolor) and color pencils (usually prisma once again) and a wax blending stick. I make my illustrations in two steps: