This fall, DC Comics fans will be treated to an augmented reality experience promoting the Justice League movie. Likewise, history buffs will be able to enjoy their own augmented reality content by way of the Terra Cotta Warriors exhibit at The Franklin Institute in Philadelphia, Pennsylvania and an in-store promotion featuring famous convicts from 19 Crimes wines.

Rising on the world stage, dengue fever is transmitted by mosquitoes — and apparently air travel too.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

If you know that ticks spread Lyme disease, you may already know you might also catch a bunch of other infections from them. One of the lesser-known diseases spread by ticks is infection with the bacterium Anaplasma phagocytophilium, called anaplasmosis.

As summer heats up, new maps from the Centers for Disease Control and Prevention (CDC) gives us our best guess at where Zika-carrying mosquitoes could be hanging out this year in the US.

The possibility of severe tickborne illness is increasing as an aggressive tick from the American southeast moves up the Atlantic Coast.

Fighting fire with fire, scientists are harnessing the adaptability of helpful microbes to challenge the adaptability of deadly microbes. What are we talking about? Hunting with phages — viruses that attack and kill bacteria.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Colorado State University scientists have developed new tech that quickly identifies the presence of Zika virus in mosquito populations — and in human body fluid.

Every Tuesday, Next Reality will give readers a rundown of the augmented and mixed reality news briefs from the preceding week that we didn't cover already. This way, you'll never miss anything of importance in the Next Reality landscape, and will always know what's going on with new augmented and mixed reality tech and applications.

General Motors Co. (GM) is set to expand their fleet of driverless cars in San Francisco, Detroit, and Scottsdale, according to documents filed by the company.

For regions that experienced a boom in mouse populations last year, scientists say 2017 could see a surge in cases of Lyme disease.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

True innovation tends to come from the places we least expect as developers. The Microsoft HoloLens is still a very new product, and some of the other headsets are still just ideas, so the rules for mixed reality are not set in stone. That means all the real problems to be solved are yet to come.

If you're a sushi lover but not an expert sushi maker, you can still enjoy the flavors of sushi rolls at home with these deconstructed sushi dishes.

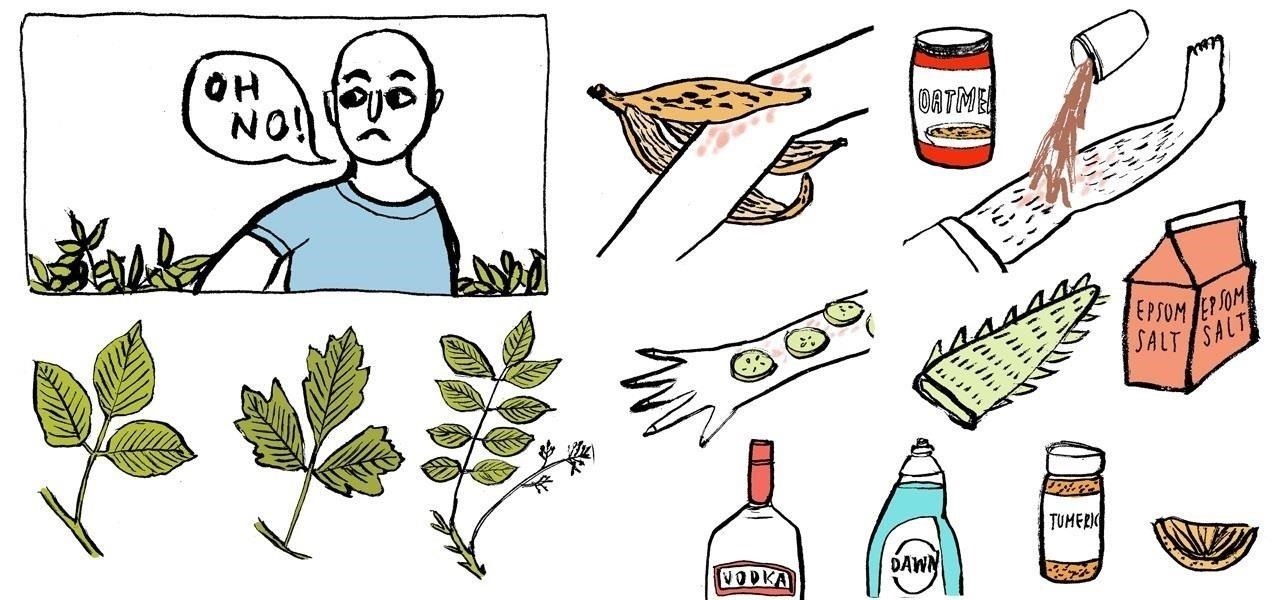
Poison ivy, poison oak, and the lesser known skin irritator, poison sumac, can all cause a conundrum in the search of itch relief: to scratch or not to scratch. Fortunately, there are a number of home remedies one can try to help alleviate the itch(ing), with many like coffee, a banana, baking soda, or mouthwash likely already in-house for most.

Perhaps the most important decoration of the holiday season is the Christmas tree. It's where all of the magic happens. If you're not into real Christmas trees, there's always some festive alternatives, but for those of us who can't live without a natural Christmas tree, choosing the right one for the right price can be an impossible task.

Create funky beats in the same program used by Dr. Dre and Kanye West. Learn how to use Logic Pro 8 software to make music in this free music production tool from a professional audio engineer.

Your sensitive personal data should be strongly protected, and it's never more vulnerable than when you are online. The internet connection is a prime avenue of exposure, and email is one of the least secure forms of communication. Fortunately, there is an easy solution to both of those problems.

File permissions can get tricky on Linux and can be a valuable avenue of attack during privilege escalation if things aren't configured correctly. SUID binaries can often be an easy path to root, but sifting through all of the defaults can be a massive waste of time. Luckily, there's a simple script that can sort things out for us.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

If you're a regular reader of Next Reality, you're more likely to spread the joy of augmented reality than most others. But it can be difficult to introduce newbies into the AR fold if you don't give them exactly the right starting point in terms ease-of-use and affordability. But fear not, oh gift-giving AR pioneer, we're here to help!

What's in a sneeze? Quite a lot—dirt, mucus, and infectious germs—it seems. And sneezing the right way can reduce the germs you share with neighbors.

Create beats with the music program Dr. Dre and Kanye West use to write songs! Learn how to make beats with the Logic Pro 8 Ultrabeat drum machine in this free music production tool tutorial from a professional audio engineer.

If we were to assign a theme for the 2019 edition of the Next Reality 30 (NR30), it might be something along the lines of, "What have you done for me lately?"

Create your own mix with the music software program used by Dr. Dre and Kanye West! Learn how to use Logic Pro 8 plug-ins to make music in this free music production tool from a professional audio engineer.

The remake of the Warner Bros. classic animation meets live-action movie Space Jam, this time starring LeBron James instead of Michael Jordan, hits theaters today.

The COVID-19 pandemic forced many businesses into remote work models, whether they were ready or not, making Zoom a household (or home office) name for its video conferencing service.

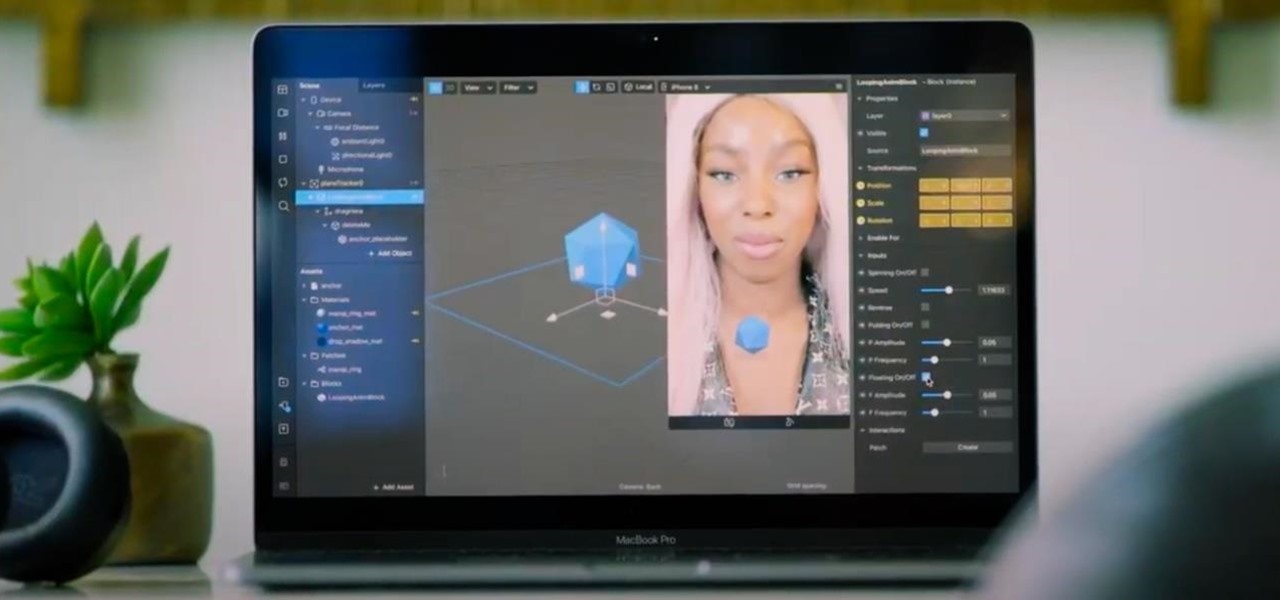
As Apple, Google, Snap, and Facebook wrestle for positioning to lure developers and creators to build augmented reality experiences for their respective tools, Facebook is looking at a learning approach for its Spark AR platform.

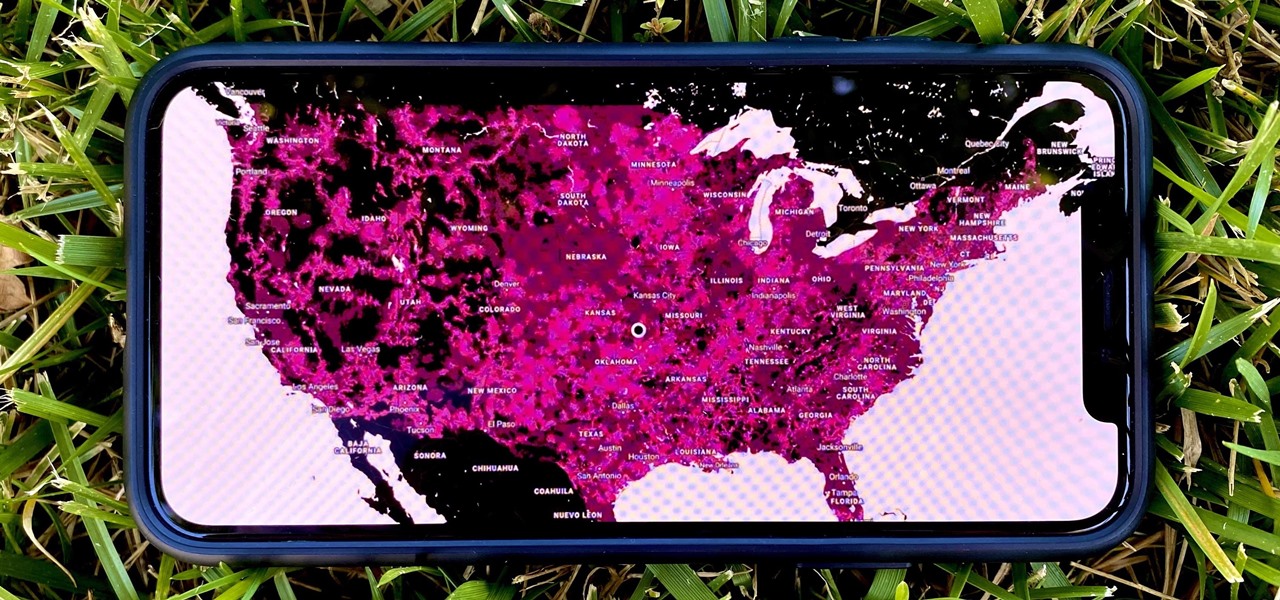
In 2009, 4G LTE networks rolled out in Stockholm and Oslo, replacing 3G as a better upgrade to the mobile data technology that gives us the broadband speeds we have on our mobile devices. Over a decade later, and we have the latest, next-generation wireless network technology among us, 5G, but can you even use it?

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

With the whirlwind of noise surrounding the COVID-19 virus sweeping the nation, it's not hard to default to panic mode. One of the best ways to avoid panicking, however, is to follow trusted sources of information and avoid all of the opinions and trolls that don't reflect reality.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

Most companies have services like employee login portals, internal-only subdomains, and test servers they would prefer to keep private. Red teams and white hat hackers can find these obscure and often vulnerable services using a tool designed to help protect users from fraudulent certificates.