
How To: Make a Simple UDP_Flooder in C pt2
Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.


Alright so last time I gave you a homework assignment. This week we're gonna look at my version of the UDP-Flooder.

Welcome back, my budding hackers! Metasploit, one of my favorite hacking/pentesting tools, has so many capabilities that even after my many tutorials on it, I have only scratched the surface of it capabilities. For instance, it can be used with Nexpose for vulnerability scanning, with Nmap for port scanning, and with its numerous auxiliary modules, nearly unlimited other hacking related capabilities.

Welcome back, everyone. In the previous part of this rapid-fire miniseries, we built the victim portion of the shell. Today, we'll be building the attacker portion. This script will initialize interaction with the victim portion of the shell, send commands, and receive the output.

In my last tutorial, I talked about creating a virus inside of a Word Document in the scenario of a mass-mailer attack. In this post, however, I'm going to be covering creating a fake image or screenshot with a meterpreter backdoor hidden inside to be used in a similar scenario. Step 1: Creating the Virus

INTRODUCTION Hello dear null_byters here we go again with our third part of this serie.

If you're a U.S. expat living, traveling, or studying abroad, or just someone who typically uses virtual private networks (VPNs) in order to access the North American video libraries of services like Hulu or Netflix, you were probably surprised to see that these video streaming services don't work on your Chromecast or Chromecast 2.

Hello all, this is my first submission to null byte! I noticed something a little strange, particularly that whenever Meterpreter is discussed, it is virtually always in the context of Windows. Granted, the Windows Meterpreter is more powerful than the version that can run on OS X (it has several more commands/options), but I think it is still worth noting how to do it. I've even seen some people mistakenly say that Meterpreter can only be run on Windows, which is not true. Meterpreter can ea...

So, we all probably know that when you run a trojan made by Metasploit, nothing will appear to happen. This is a sign for me to immediately check my Task Manager, but for an unsuspecting victim, it will just seem like a broken file. It is likely that they will delete this "broken file" once they see that it "doesn't work." In order to prevent this, we need to disguise the trojan.

Welcome back, my budding hackers!

Welcome back, my hacker novitiates! In previous guides, we have used one of the most powerful hacking platforms on the planet, Metasploit, to perform numerous hacks. They ranged from exploiting Windows XP and Windows 7/8 vulnerabilities, to installing a keylogger and turning on a webcam remotely. We have even been able to save the world from nuclear annihilation, see if our girlfriend is cheating, spy on suspicious neighbors, evade antivirus detection, and more.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my greenhorn hackers! I recently began a series on scripting and have received such positive feedback that I'm going to keep this series going. As I've said before, to graduate from the script kiddie to the pro hacker, you'll need to have some scripting skills. The better you are at scripting, the more advanced your hacking. Ultimately, we are leading up to developing the skills to build your own zero day exploits.

Ever since the FBI took down the Silk Road and Dread Pirate Roberts last month, many questions have been raised about whether Tor still provides anonymity or not, and if it's now broken. I'll try to address that question here today succinctly from multiple angles, keeping it as simple and plain-language as possible. The Closing of Silk Road

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!
This session is about page view sharing. Click collaborate, send collaborate live. It works with Acrobat. It opens a live chat session. Log in with Adobe ID. You can invite others to collaborate. Click to select name, attach a file and send an email. File can be saved on Acrobat. Access can be restricted to those who are invited. Collaborate live panel opens. You can open the invitees computer. Invitee needs to sign in. You have the ability to chat. Start page sharing. Pages are synchronized....

1. Describes how to setup a VPN connection on Windows XP. 2. Goto Start-> Control Panel-> Network connections.
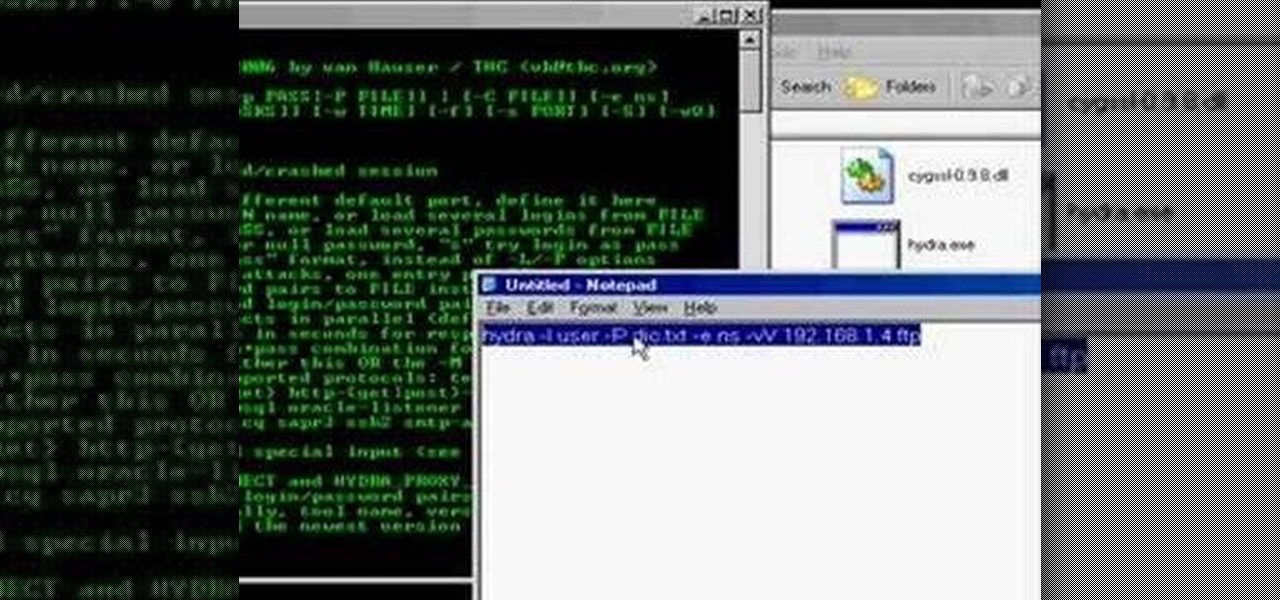
This is a how-to –video on using hydra 5.4 to crack FTP passwords. This video is intended for educational purpose only. It reveals the basics of hacking a FTP server using dictionary search technique. Here are the steps involved.

In this how to video, you will learn how to speed up your Azureus Vuze program. First, open up Azureus Vuze. Next, go to advanced, option, and click preferences. Select preferences and change the port to a number between 49152 to 65535. Once it is changed, go to transfer and make sure that these are set to zero. Once that is done, open your web browser and type in your default gateway. To find this out, go to system preferences, network, and router. Next, enter your user name and password to ...
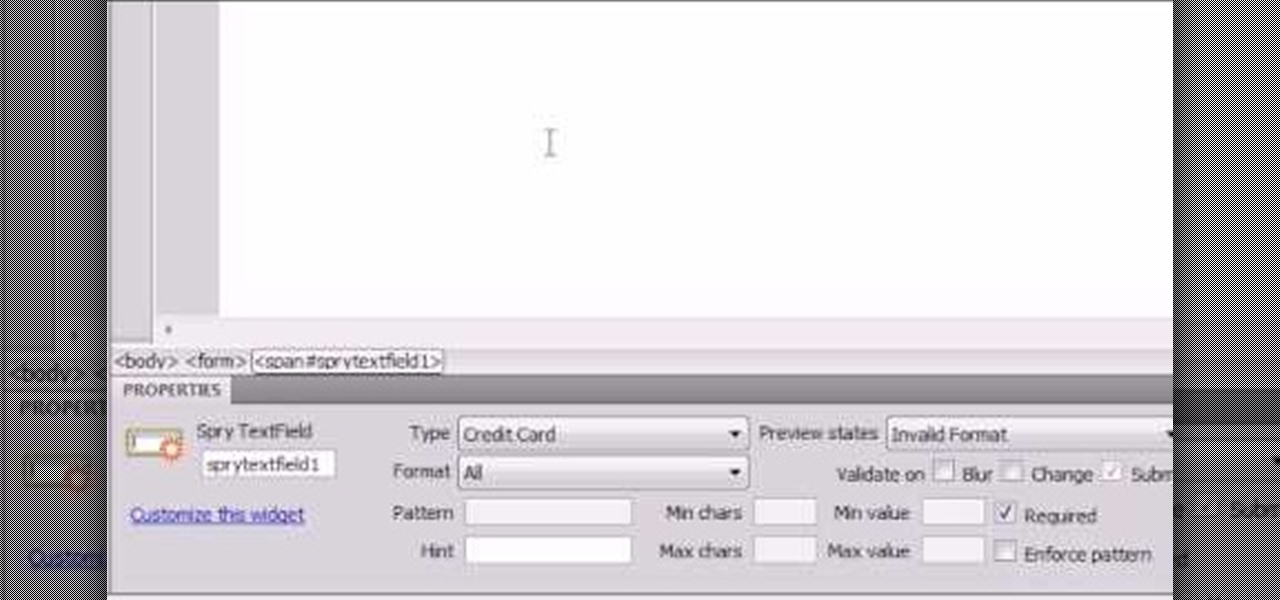
Here the New Boston shows you some tips about using the Spry Validation Text Field. To begin you will go to the Spry Validation Text Field, on Dreamweaver CS4. Looking at the bottom of the page notice the various options that are available for Properties. You find drop-down boxes for Type, Pattern, Minimum or Maximum values, Required, Enforce pattern, Format, Validate on, Blur or Change and Preview States. You can see the types of text available for validating by left mouse clicking the Type ...

HighQuality Tutorials demonstrates how to change your iPod Touch alpine default password. Changing the default password is useful when using your iPod Touch in a public setting to make it less vulnerable to hacking. To change the default password, first open up your internet connection and search for Putty. Download the Putty program. Open and run the Putty program. Your host name will be your IP address for your iPod Touch. Select port 22 and SSH and open up the program. Log in as root and c...
This video tutorial from noxad presents how to backup and burn games for Nintendo Wii game console.To setup game transfer from computer to your console you'll need any type of SD memory card. In this tutorial it's Lexor 1 GB SD card.Insert SD card into your computer card reader. Autoplay window will open, asking what action you want to perform. Select Open folder to view files.You can open SD card manually from My Computer window. (Start button-Computer).Make sure your SD card has folder name...
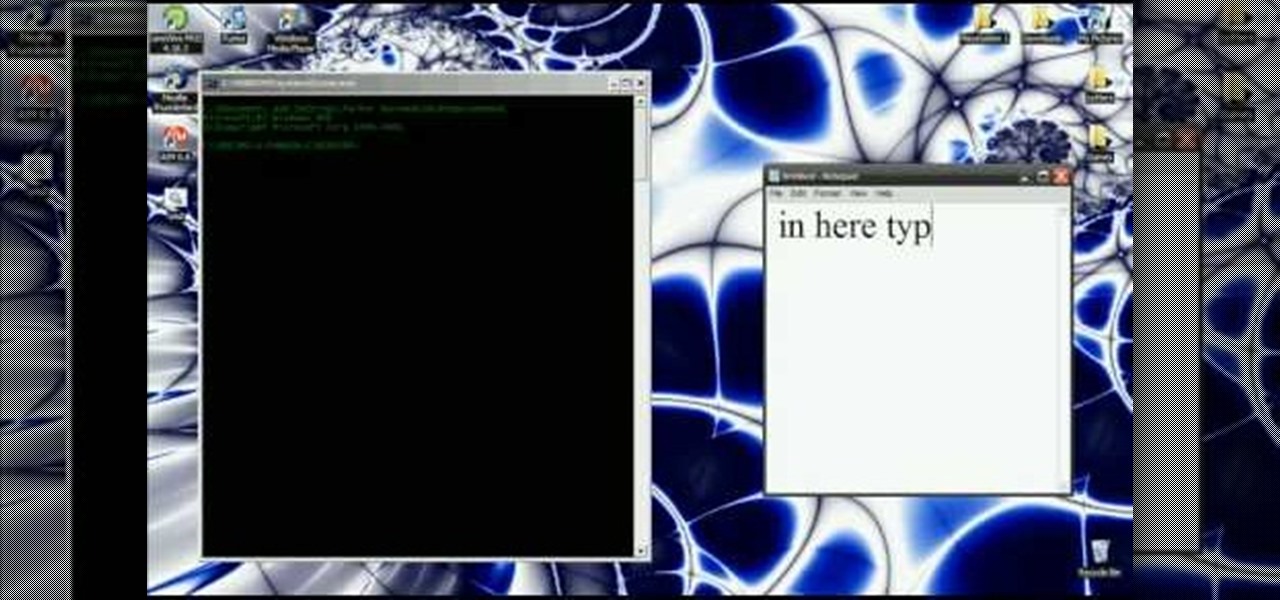
In this video you will learn how to get past website blocks on your school network. Some school computers have command prompts blocked. If this is the case then you will want to open a notepad. In the notepad type command, then save as something school related, making sure the file name ends with .bat. Do not save it on the desktop, but rather in a folder deeper on the unit. Once you've saved it, make sure no one is looking, then open the file. It will bring up a blank black window. In the bl...
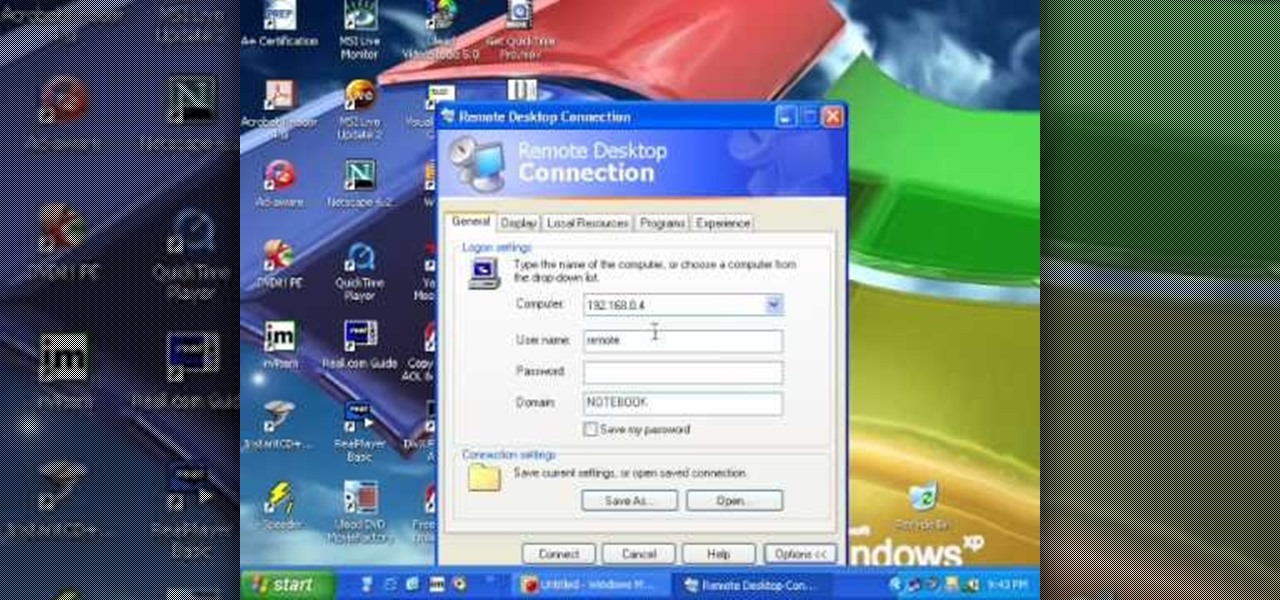
This video from Michael presents how to establish a Remote Desktop connection in Windows XP Professional.This type of connection allows you to access your computer via Internet from any place and manage files, local resources, or perform any other remote activity.To establish Remote Desktop connection click Start button, right click My Computer, from the opened menu select Properties. System Properties window will open. Choose Remote tab. Check Remote Desktop - Allow users to remotely connect...
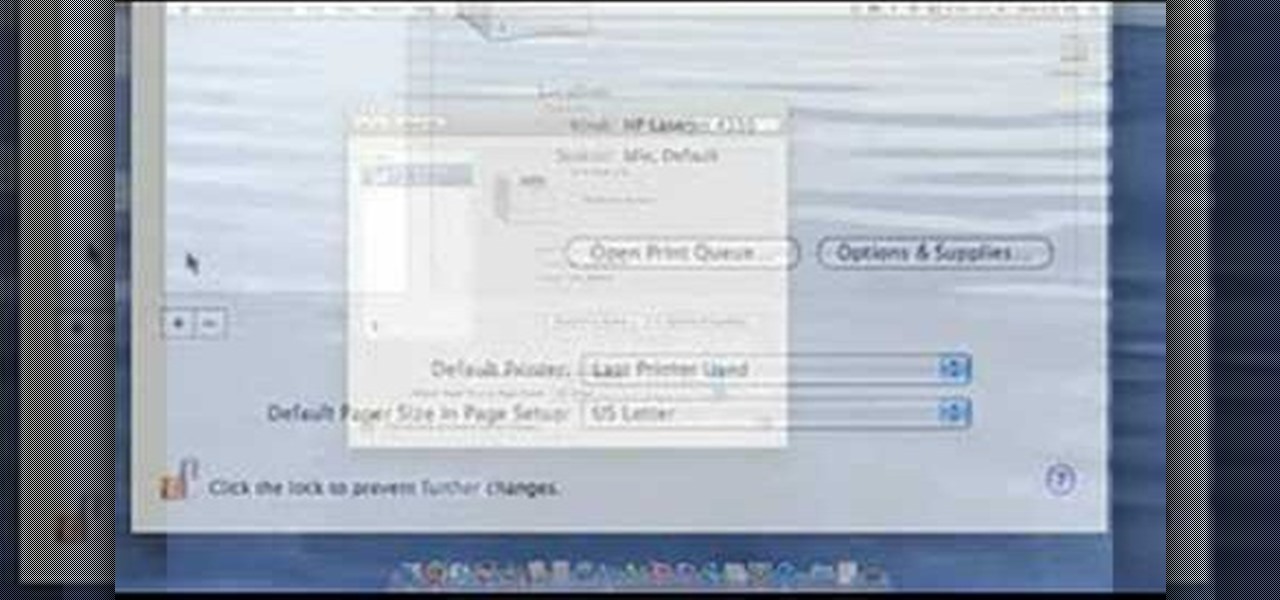
This video demonstrates how to setup a printer on a Macbook Pro.Open the document you wish to open. Go the File menu on the top bar menu and select Print. On the Print dialogue box, you will notice that no printer is selected. Click on the drop down menu to select Add A Printer. Click on the IP found on top of the window. Change the protocol to IPP or Internet Printing Protocol. On the address bar, type in the address of your printer then click on Add. Once done, you can now print your docume...

This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection.

If you don't have a Wi-Fi network, you can still easily SSH into your iPhone. Just follow the steps outlined in this video tutorial. First, you will need a Mac or iPhone along with Fuju. Just download the program. Once you have all of this, click on the Wi-Fi bar and click on Create New Network. As a name, click on iPhone SSH and click Manual. This creates your new network, which you will see on the desktop. Double click on it and then look at your iPhone. Go to iPhone. Connect to the network...
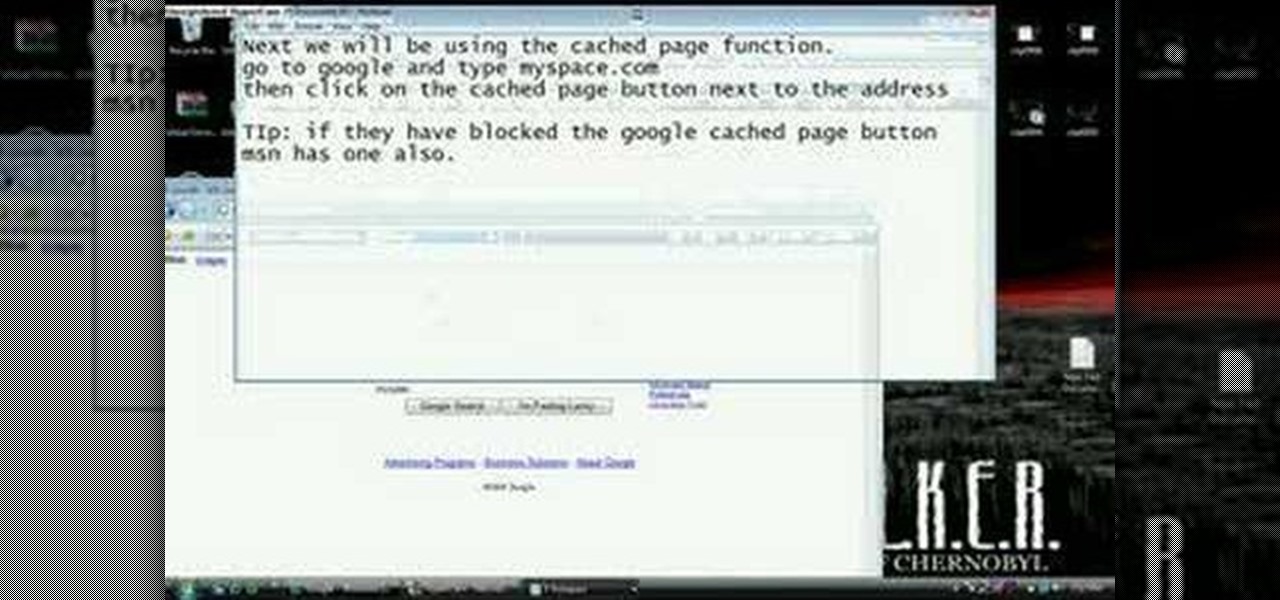
Nowadays many schools and colleges have blocked the social community sites from accessing them through school computers. The video shows how one can access to these sites using a command prompt.
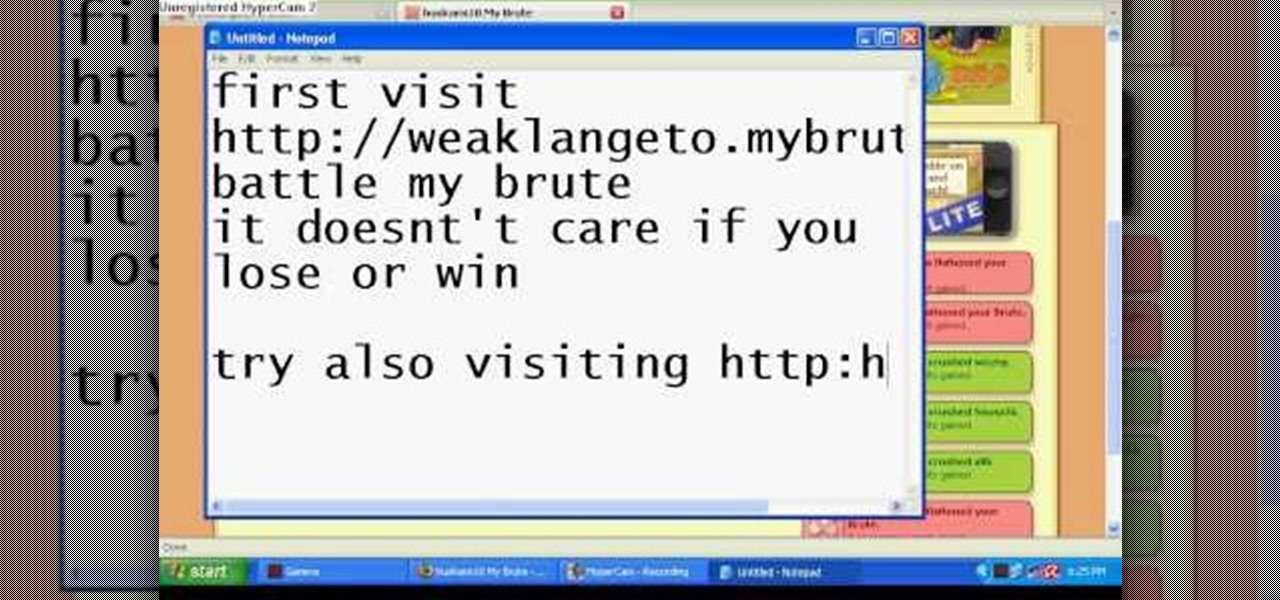
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to hack a wolf or bear in MyBrute (07/26/09). Without Cheat Engine!

All you need to remotely access your computer's iTunes library is your iPhone. Control itunes with your iPhone with this Howcast guide.

All you need to remotely access your AppleTV library is your iPhone. Learn how to control Apple TV with your iPhone with this Howcast guide.
Nmap ("Network Mapper") is a free and open source (license) utility for network exploration or security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw IP packets in novel ways to determine what hosts are available on the network, what services (application name and version) those hosts are offering, what operating systems (and OS versions) they a...

One of the most promising avenues of attack in a web application is the file upload. With results ranging from XSS to full-blown code execution, file uploads are an attractive target for hackers. There are usually restrictions in place that can make it challenging to execute an attack, but there are various techniques a hacker could use to beat file upload restrictions to get a shell.

If you want to carry a variety of network adapters without looking suspicious, a perfect solution is accessing them through Airserv-ng. Tucked away in the Aircrack-ng suite, this tool allows a hacker to plug any number of network adapters into a Raspberry Pi and access them over a Wi-Fi or Ethernet connection.

It's not uncommon for hackers to attempt to move laterally between devices in proximity of a compromised device to maintain a prolonged presence in the network. Malware utilizing USB flash sticks to self-replicate and compromise air-gapped machines isn't a new concept.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tesla says the new version of Autopilot is now as good as the previous one, after having completed over-the-air updates of the driverless software during the past few days.

Tesla has confirmed the EV carmaker has begun to upload videos from models equipped with its latest flavor of Autopilot, as Tesla seeks to "fleet source" data to help improve its cars' machine learning capabilities.

With so many apps being cloud-based, cached data has started to become a problem. This is particularly true if you're low on storage, so developer Dhi decided to do something about it.