This week in Market Reality, we see two companies capitalizing on technologies that contribute to augmented reality platforms. In addition, industry mainstays Vuzix and DAQRI have business news of their own to report.

If you need to do some hardcore multitasking on your Windows PC, a second monitor can go a long way towards getting things done. If you opt to "extend" your Windows desktop across a dual monitor setup, it's as if you have two computers side by side, with each display getting its own set of windows and programs that can be open simultaneously.

When Apple announced its new iPhone 7 and iPhone 7 Plus models in San Francisco, one of the biggest new features was an "IP67" water-resistance rating. Couple that with a few official renderings that show the new iPhone covered in water, and you'd probably arrive at one logical conclusion: The iPhone 7 is waterproof.

When it comes to sharing files between a smartphone and a computer, there are several solutions available for a Windows and Android pairing. But for those of us with Apple devices, the selection of apps in this category isn't quite as great. You can use AirDrop to quickly share files, but searching for files is not so easy.

Greetings comrades! Great leader has ordered that we gain intel on a website owned by the opposition. For all general purposes we will be scanning nmap.org because they really don't care if Big Brother decides to perform a whois on their IP. We will be using Dmitry for the scanning.

This tutorial follows the same idea as my original tutorial for windows, but I've redone it to work with Mac OS X. Here's how to get a meterpreter session from your victim opening a malicious word document:

Here I will show you how to properly dig information on the web that has already been published, you just dont know it.

I mentioned in 2015 I wanted to start a 'DoXing' series, and since I havent seen this on Null Byte, I am now going to introduce this to the community.

School internet filters serve a valid purpose—they keep students from wandering off into the deep corners of the web while still allowing at least some internet access. But a lot of these restrictions are completely ridiculous, to the point where some school districts block access to the educational material in National Geographic or forbid searching terms like "China," "Iran," or "Russia"—because, you know, breasts and commies.

Keeping your online data and identity private is an uphill battle, but with the anonymity network Tor, you have a pretty decent line of defense from prying eyes.

If you read my last tutorial on using SEToolkit, you probably know that SEToolkit is an effective way to make malicious actions look legitimate. But, that was only the beginning... the truth is, Metasploit and SEToolkit belong together, and help each other very well.

Let's say that we want to see what someone is doing on their computer? In this tutorial, we'll be hijacking cookie sessions to do just that!

One of the biggest improvements in Mac OS X Yosemite came to the Spotlight search feature, allowing users to not only search through their applications, but also their emails, text messages, iCloud, and the web.

This is the best how-to's website that I've ever seen, and I wanted to join it. It taught me a lot, but, because I'm here to learn too, please correct me if I'm wrong.

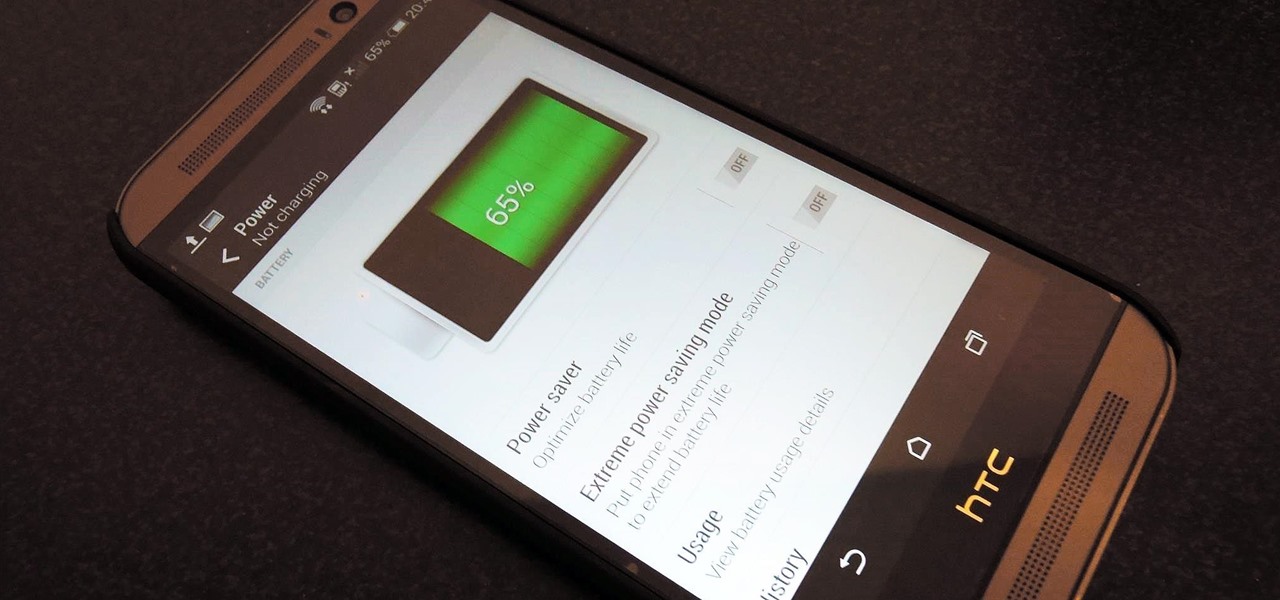
HTC claims to have improved the One M8's battery life by 40% over its predecessor, but there is always room for improvement.

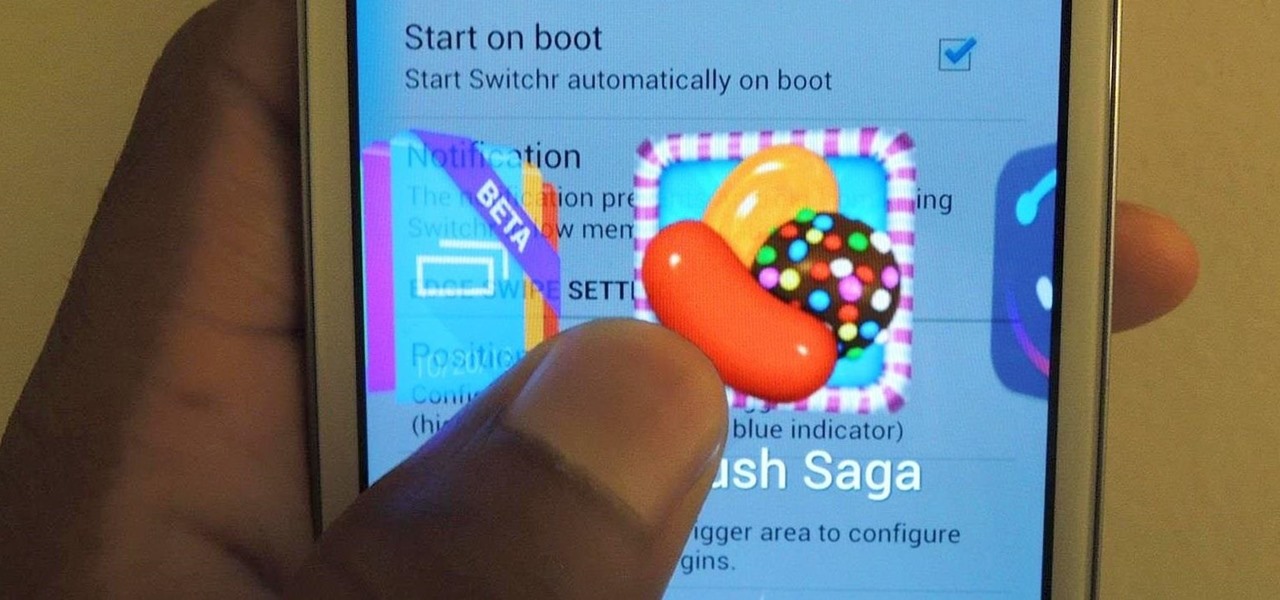
I've covered a few multitasking app switchers before, but none of them are as sleek and smooth as the aptly titled Switchr, a new app developed by Mohammad Adib that lets you move from one app to another quickly and smoothly—just like how I switch between my women. Well, not really, but I would.

Welcome back, my hacker wannabees! Most of my recent posts have addressed using Metasploit’s Meterpreter and what we can do once we have embedded it on the victim’s system. This includes remotely installing a keylogger, enabling the webcam, enabling the microphone and recording, disabling the antivirus software, among many other things. The list is almost unlimited.

In my last hack blog on crashing your roommates Win7 system, we started looking at client- side attacks. As promised, we will be looking at some more client-side attacks.

All of my hacks up to this point have been operating system hacks. In other words, we have exploited a vulnerability usually in an operating system service (SMB, RPC, etc.) that all allow us to install a command shell or other code in the target system.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

This video gives you the lowdown on making a lag switch for gaming. But why would you want a lag switch? What is a lag switch?

One you understand how a subnetwork works on an Internet Protocol (IP) network, creating one becomes very easy. In this five-part video, you'll learn about IP address and subnets, along with creating an IPv4 (IP version 4) address using Class C, which leaves each network with 256 local addresses. If you're new to subnetting, this is where you start!

This how-to video is about how to use command prompt to view the blocked websites at school. This step by step instruction will help one to open the blocked websites at school.

With plans to compete with Niantic and other augmented reality game developers, game developer WarDucks has closed a $3.8 million funding round.

In the realm of internet security, it's becoming clear that augmented reality is not immune to the increasing wave data breaches plaguing users.

Now that it has buried the legal hatchet with Meta Company, augmented reality startup Dreamworld has announced plans to open up pre-orders for its Dream Glass AR headset.

Though Google and Apple have released their own software-based toolkits for AR, components suppliers continue to advance their technology to better support AR experiences on the hardware side.

What happens if you unknowingly connect a malicious USB drive and it starts infecting your entire office network? Instead of having a panic attack and working all night to find a fix, you can just put on a mixed reality headset like Microsoft's HoloLens and point.

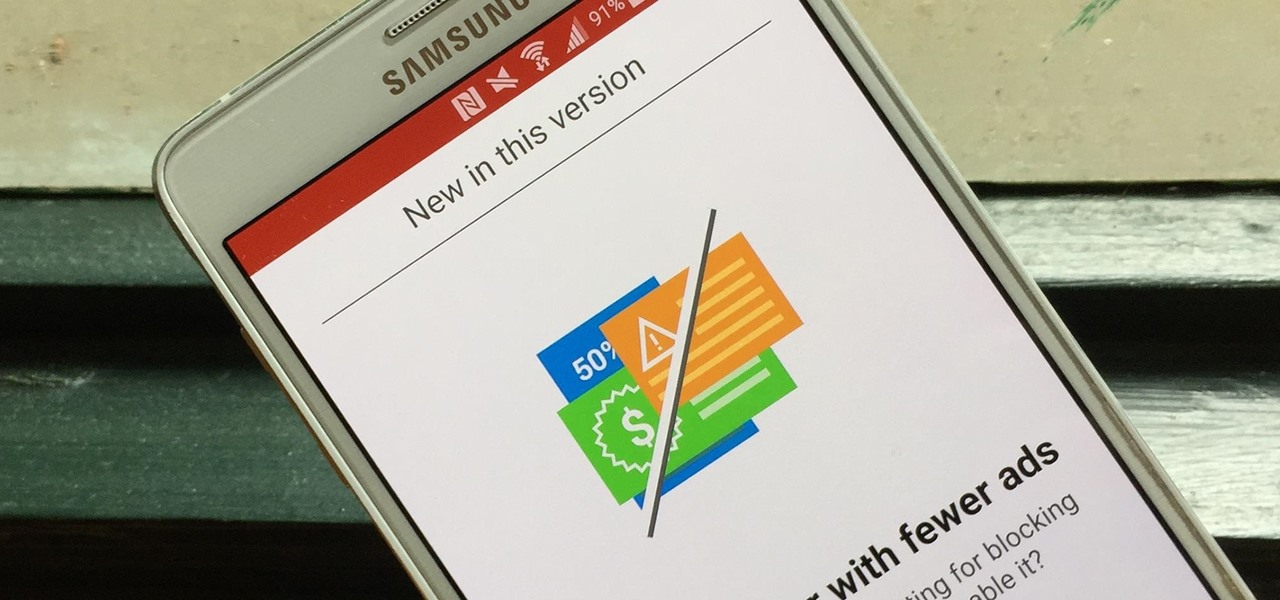
Opera's web browser for Android, Opera Mini, now comes with integrated ad-blocking technology for a less cluttered browsing experience. More importantly, it decreases the amount of data being loaded, which Opera claims increases webpage loading times by 40 percent. This is in addition to the 90 percent data reduction from Opera Mini's compression technology.

This Is for the Script Kiddies: This tutorial is about a script written for the How to Conduct a Simple Man-in-the-Middle Attack written by the one and only OTW.

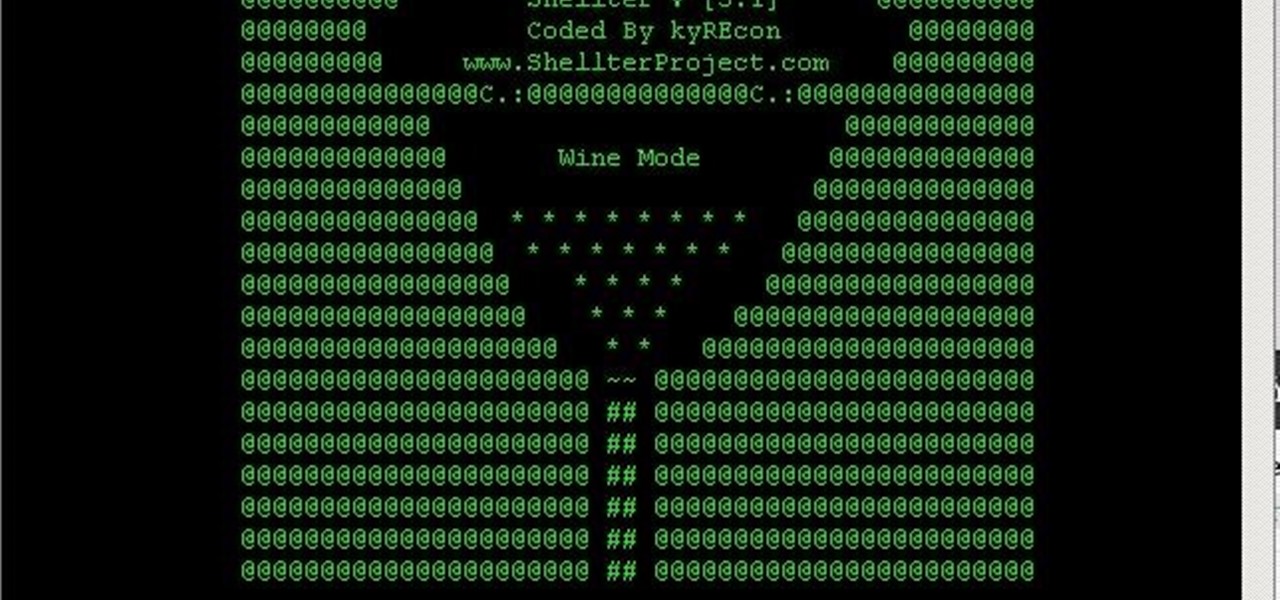
You always wanted to make an undetected payload and make it look legit, Well this is what this tutorial is about, You're going to learn how to backdoor any (Unfortunately only 32-Bit) software, Let's get into it

I've been a diehard Chrome user since its inception, and even more so since Android was released. The ability to sync bookmarks, passwords, and web history across all of my devices made the switch a no-brainer, but what really made me fall in love was the amount of extensions available for it.

Not too long ago I showcased ReCam, a free app that lets you schedule recordings and use your Android device as a security or spy camera of sorts. While useful, this app required you to schedule when to record in advance, resulting in you possibly missing the footage you intended to record (assuming your scheduling wasn't as on-point as you wished).

OK as you all know i was the won who loved ships on the old server, well though they all looked weird this may be the best I've ever made. I made a small replica of the Titanic but its bigger than any other ship i made on the server.

Securing your email address is one of the most important things you can do on the internet. Hackers, spammers, and overly aggressive marketers can turn your Gmail inbox into a heap trash if you're not careful.

As most everyone knows, Android and Apple don't get along so well. Even the users don't get along well, with Android and iPhone users constantly berating and insulting each other online—any chance they get. I should know, since I was one of them, but I'm now rare breed who's learned to appreciate both. People just need to realize that they have their own unique strengths—Android with its customization and Apple with its simplicity.

Checking notifications from all of your social media accounts is half the fun of the Internet, but can become quite tedious—hopping from site to site can take up hours of your time, especially when you're running away from something (in my case, it was always homework/studying).

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...

Dropbox announced Tuesday that a recent security breach compromised a list that included the email addresses of certain Dropbox users. To avoid future complications, the service announced that it would be implementing two-factor authentication, and even more useful, a security page that lets you monitor all activity on your account. In light of this and other recent web security threats, you might also want to know that services like Gmail, Facebook, and Yahoo! Mail have similar pages where y...

In this video tutorial, viewers learn how to bypass and skip Mega Video time line in 10 seconds. This task is very easy, fast and simple to do. If users are not a member on the Mega Video website, they will have a 72 minute time limit when viewing any videos. Begin by downloading and installing the Hide My IP program. Once downloaded and installed, open the program. Then click on Hide My I.P. Now simply refresh the Mega Video page to continue watching the rest of the video. This video will be...