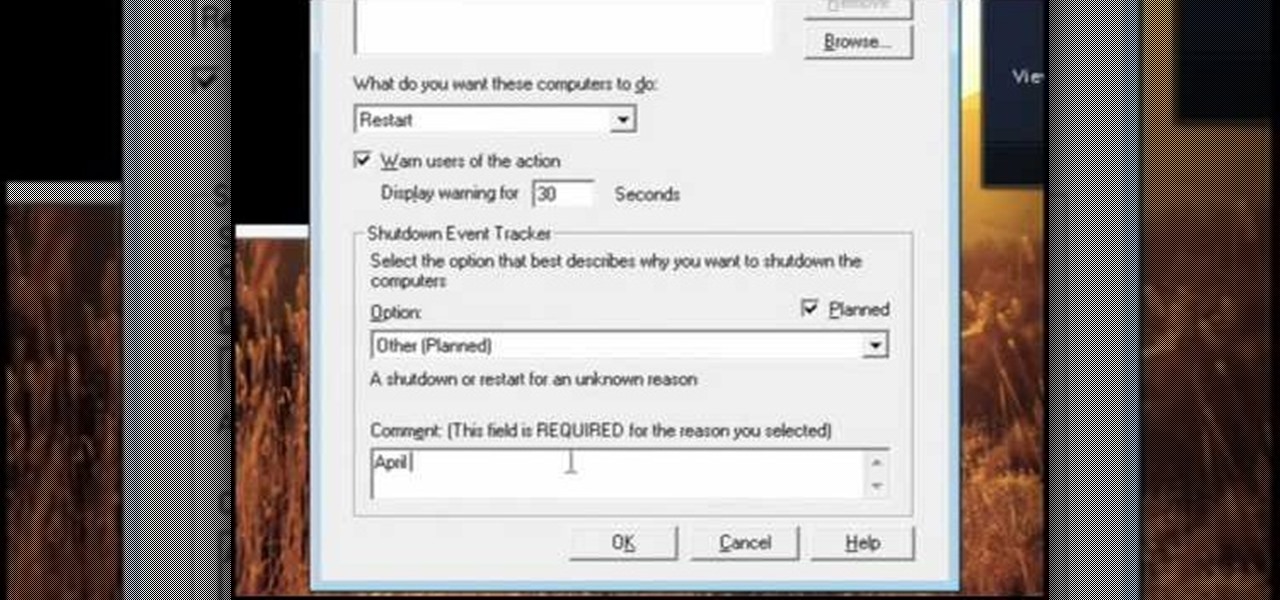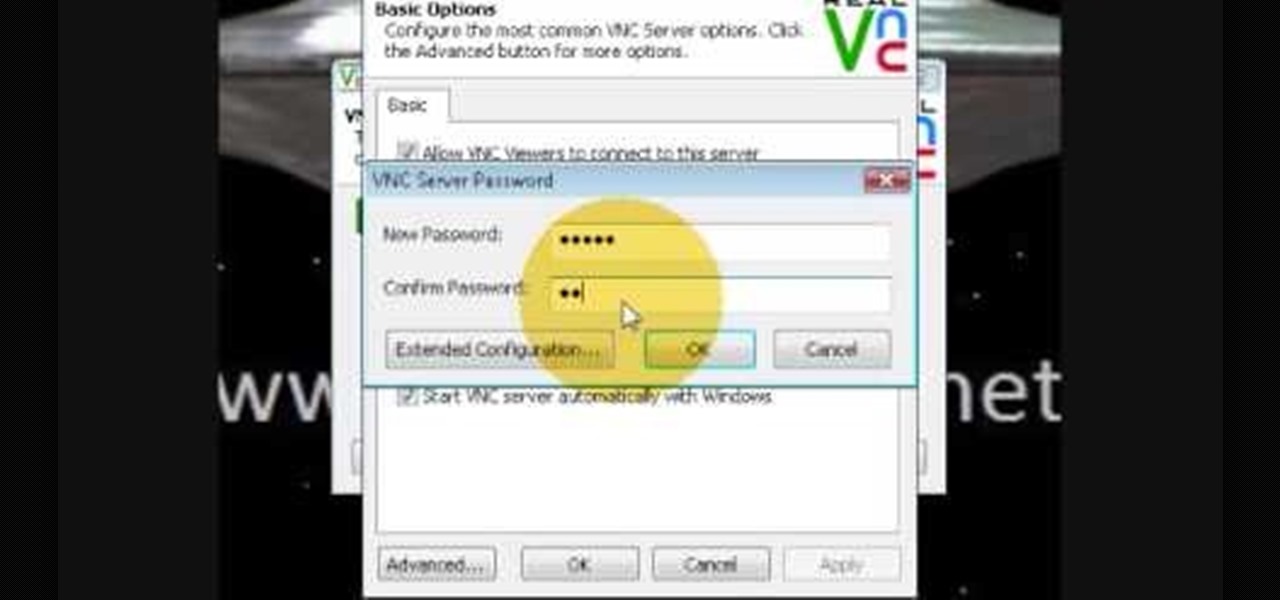
If you want to know how to monitor another computer screen with Real VNC, you must watch this video. Install Real VNC in your computer and computer that you're going to monitor. Remember the folder where you installed it and check the "Create a VNC Viewer desktop icon" checkbox. Write on a paper the IP address of the computer that you're going to monitor. On the VNC Server Status window, click Configure button. On the Authentication field, select VNC password and on the Encryption field, sele...

Hak5 isn't your ordinary tech show. It's hacking in the old-school sense, covering everything from network security, open source and forensics, to DIY modding and the homebrew scene. Damn the warranties, it's time to Trust your Technolust. In this episode, see how to hide secret data inside a photo.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

They're finally here. Apple announced three new iPhone models at their "Gather Round" event in Cupertino, and they're all absolutely gorgeous phones. With bezel-less screens and polished titanium edges, the iPhone XS, XS Max, and XR are truly marvels of engineering — but perhaps the most impressive design feat Apple pulled off is the fact that two of these models are rated IP68 under the IEC standard 60529.

Shodan calls itself "the search engine for internet-connected devices." With so many devices connected to the internet featuring varying levels of security, the special capabilities of this search engine mean it can provide a list of devices to test and attack. In this tutorial, we'll use Python to target specific software vulnerabilities and extract vulnerable target IP addresses from Shodan.

In case you didn't catch the big event in Cupertino, Apple just unveiled two of the most cutting-edge phones ever made — the iPhone 8 and the iPhone X. Out of the many glorious specs that were rattled off on stage, one stands out for being just a little confusing: Both models are rated IP67 under the IEC standard 60529.

Hello everybody. I'm back with Part-2 of this series. In this part we will be programming in C our server and i will be explaining one more "key concept" so everybody got a better understanding on this.

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Unlike in the physical world, on the internet you're actually able to shut people up and block spoilers of newly-released movies, your favorite TV shows, or a sports event you've yet to watch on your DVR.

Welcome back, my hacker noviates! In a recent post, I introduced you to Shodan, the world's most dangerous search engine. Shodan crawls the globe from IP to IP address, attempting to pull the banners of each web-enabled device and server it finds.

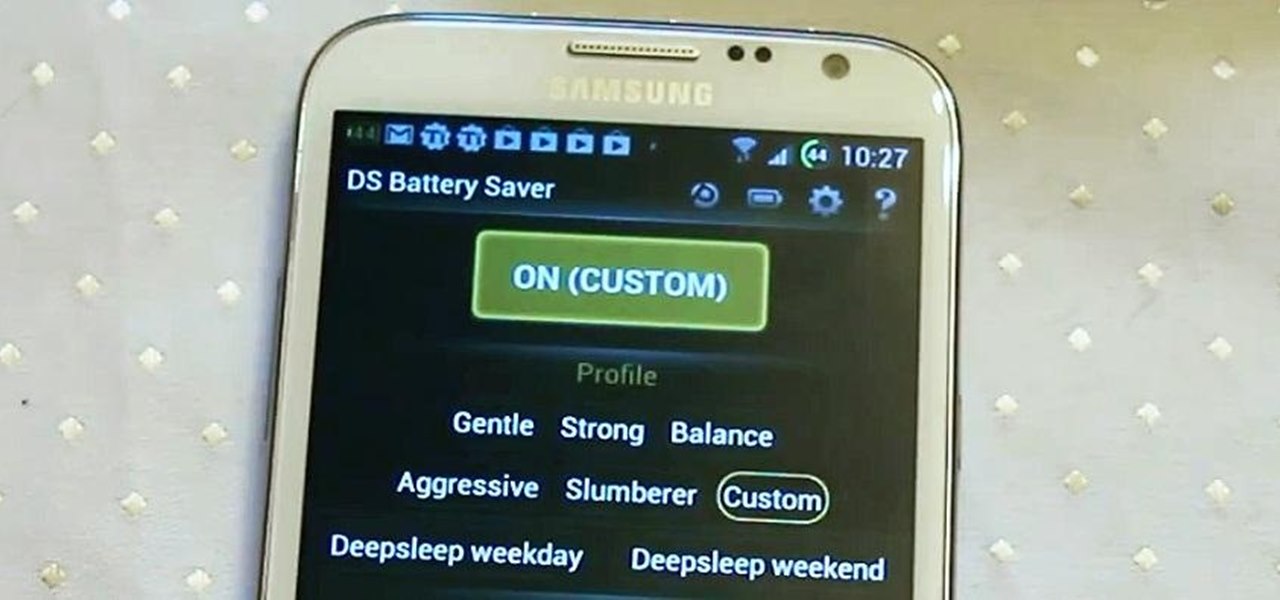
Newer smartphones are more power hungry than ever before, and the Samsung Galaxy Note 2 has a mighty appetite for amps that only Jenny Craig could possibly curb. On average, your Note 2 (or other Android device) lasts for what, a day, maybe two days before dying. Mine barely lasts 8 hours! This is thanks to all of the apps running in the background of your phone, even when you're not using them, eating through all of your CPU, leaving nothing but crumbs.

In this video tutorial, viewers learn how to protect their privacy online. Some information that is exposed every time you visit a website are your I.P. address, operating system and browser. To view what information that you are revealing to a website, visit the site provided in the video. This site will give you all the information that you are exposing in a website. This video will benefit those viewers who visit a lot of websites, and would like to learn how to view the their exposed info...

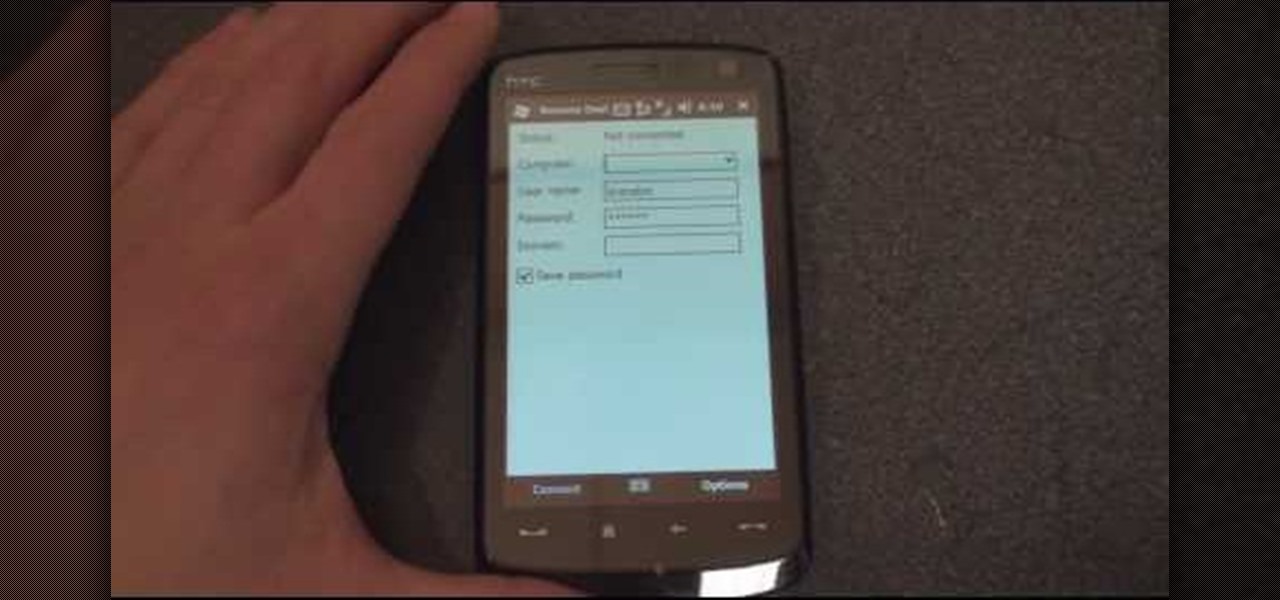
In this tutorial Brandon from Pocketnow.com will show you how to set up and use your remote desktop on a Windows mobile smart phone. Windows mobile remote desktop allows you to remotely access and control your Windows computer from your cellphone device, it is just like controlling your computer but in the palm of your hands. This guide will also show you how to get the Remote desktop software on your cell phone device if you don't already have it. The remote desktop requires for you to have ...

How to Use Your Mac as a Server: Turn your Mac Mini into a server! Yes, that's right, with a little know-how and a little spunk, you can turn an inexpensive Mac Mini computer into a server to provide services over you network. You won't even need the Mac OS X Server, just the Mac OS X Client, so there is no extra software to buy, just the Mac Mini and it's operating system.

Computers all over the world rely on a program called "libssh" to use the SSH communications protocol, which allows trusted users to log in and administer computers remotely. Due to a flaw in libssh, fooling a computer into granting SSH access is as easy as telling it you already have permission. The vulnerability can lead to an attacker gaining complete control over a device.

This guide is written for anyone who is practicing his penetration skills using the Metasploitable 2. The problem that we are facing here is that we have to penetrate to Metasploitable 2 and when this happens we understand that we are not logged in as root but as a user with less privileges!

NMAP is an essential tool in any hacker's arsenal. Originally written by Gordon Lyon aka Fydor, it's used to locate hosts and services and create a map of the network. NMAP has always been an incredibly powerful tool, but with it's newest release, which dropped mid-November of last year, they've really out done themselves.

So you want to create a meterpreter virus, but you keep getting caught by AV. How do you create one that will go undetected? In this tutorial, I'll teach you how to code your own simple virus that will download a powershell payload from an apache webserver and execute it - bypassing antivirus.

Hello again, ***UPDATE: Adding links to the other Two articles****

Hi Folks. This is my first post. I will teach how to create a server and client python reverse shell using sockets and python language. The script i'll post here is going to be very simple, and from here you'll have the possibility to adapt to your own purpose. For example, my original script can download files, upload files, make changes to registry, create user accounts and more. I'm sure you could do it on your own too.

Welcome back, my budding hackers! Recently, I showed you how you could exploit the widely disseminated OpenSSL vulnerability that has to become known as "Heartbleed". Although the world has known about this vulnerability for over a month now, it will likely take many more months—or even years—for everyone to close this vulnerability.

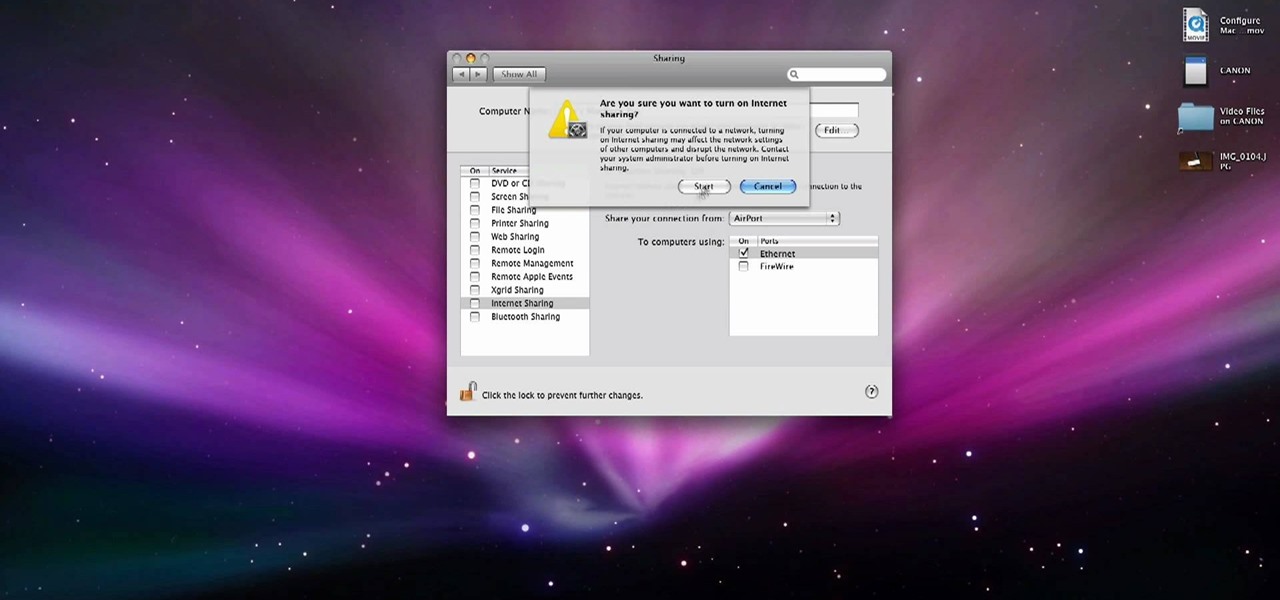
In this video, we learn how to use your Mac as a wireless adapter for Xbox Live. You will need: a Mac, monitor, Xbox, and Ethernet cord. Start out by going to system preferences, then going to the sharing folder. Go to internet sharing and make sure the Ethernet box and internet is selected. Then, click the box next to internet sharing and click "start". Now, go to the network option and go to advanced, TCIP, and then write down your sub maps and router IP address. After this, plug the Ethern...

In this video, we learn how to pull a compilation of computer pranks on a friend. The first trip is a mouse prank where you will open up the control panel and find the mouse settings. From here, you can switch the buttons from left to right and change the speeds of the mouse. Next, you can do network pranks by running cmd.exe as administrator. Then, go and see who is on the network and type in "msg /server:(ip address) and message". You can also do a ghost typing prank, which you will create ...

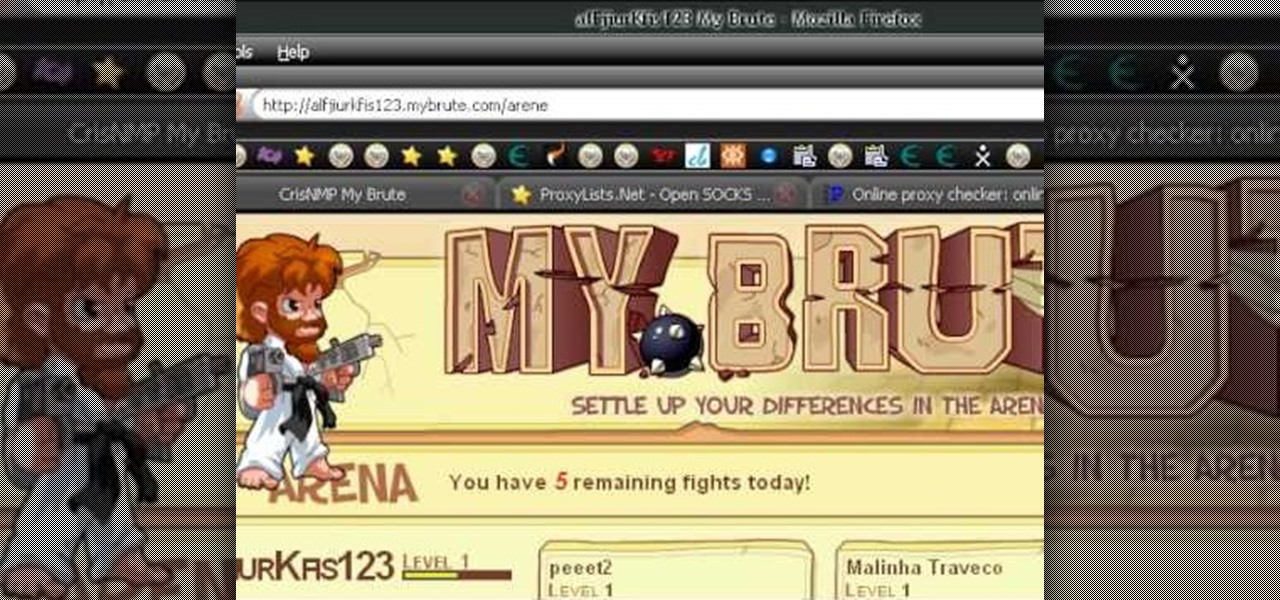
Watch to learn how to get infinite EXP with proxies in MyBrute (04/23/09). It shows how to get exp from pupils you make by passing the current two checks (Flash SOL files and IP check).

Netcat is a featured networking utility which reads and writes data across network connections, using the TCP/IP protocol.

This is a short tutorial on how to use your iPhone as a remote control for your eeePC. First download touchpad from installer.app, as well as install VNSea if you don't have it.

In my first installment in this series on professional hacking tools, we downloaded and installed Metasploit, the exploitation framework. Now, we will begin to explore the Metasploit Framework and initiate a tried and true hack.

If you can't get access to a wifi hotspot or an Internet connection with your PSP, you can use this method to get online. You will need access to a computer that is online, and a USB cord that can connect the computer to your PSP. Then, open up the command prompt on your computer, configure your IP and then add your PSP as a device on the network. This method uses the DNS method of getting to the Internet rather than having to hack a wifi connection.

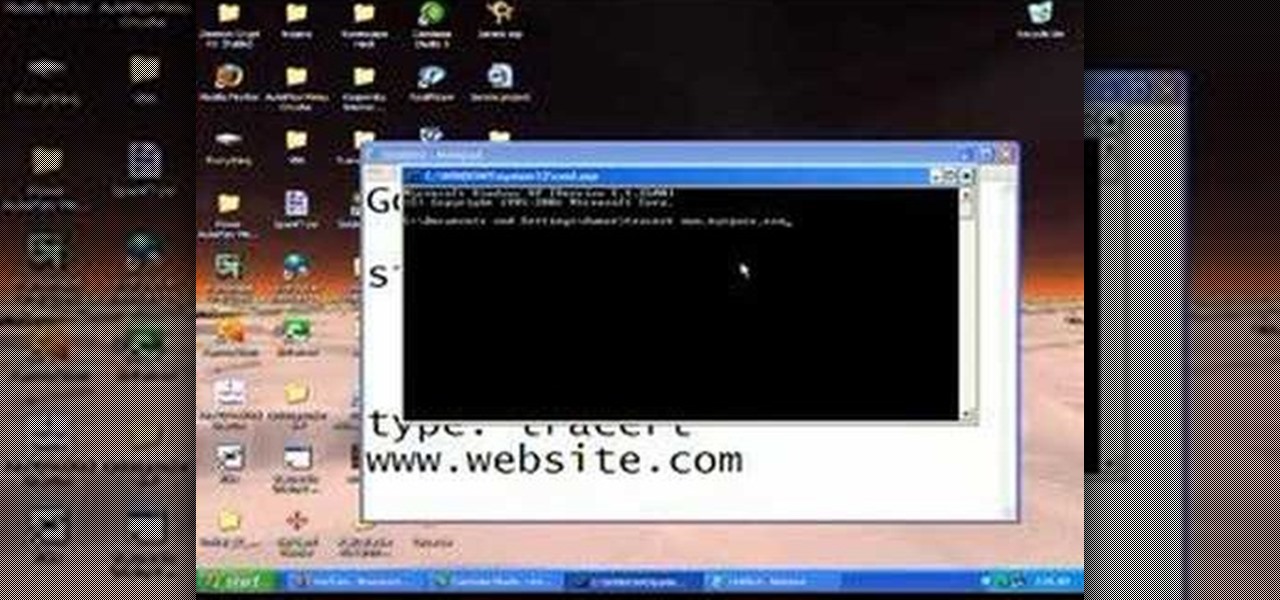
In this video, we learn how to hack school filters to get on Facebook with Tracert. First, go to the start menu and then type in "cmd" into where it says run. After this, type in "tracert" and then the website name. Wait for all of the information to fill in in the black screen. Then, copy and paste the IP address that appears inside. Now you can take this and use it to go to Facebook while you are at school. Or, you can go to any website that you'd like to that you normally can't go to at sc...

If you love Mario games, but desperately wish Nintendo would get their rears in gear and develop some new IP, then Enough Plumbers should be right up your alley. It is a loving Mario spoof platformer, and these videos will walk you through all 25 levels.

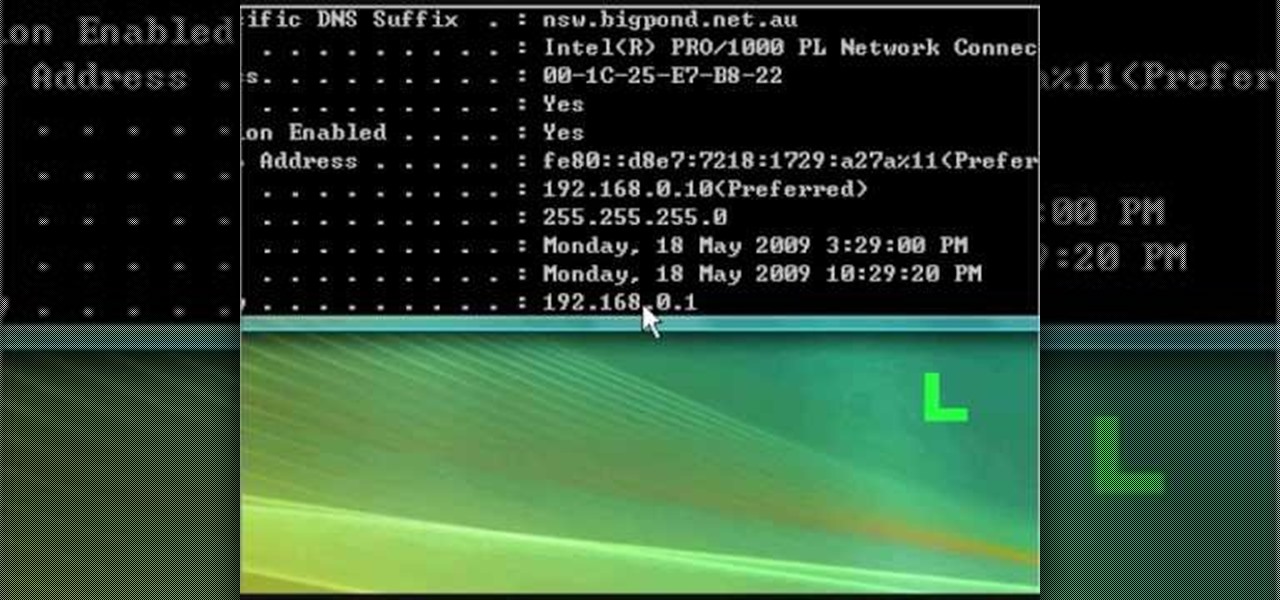
In this tutorial, we learn how to fix security mode for nds Wi-Fi. First, open the command prompt in Windows. Next, type in "ipconfig/all" in the black window that appears. After this, copy your default IP the screen just gave you, then type it into your address bar online. After this, you will be able to log into your security account and make default changes you prefer. Change different station accesses and any other security preferences you want to change. After this, you can change your p...

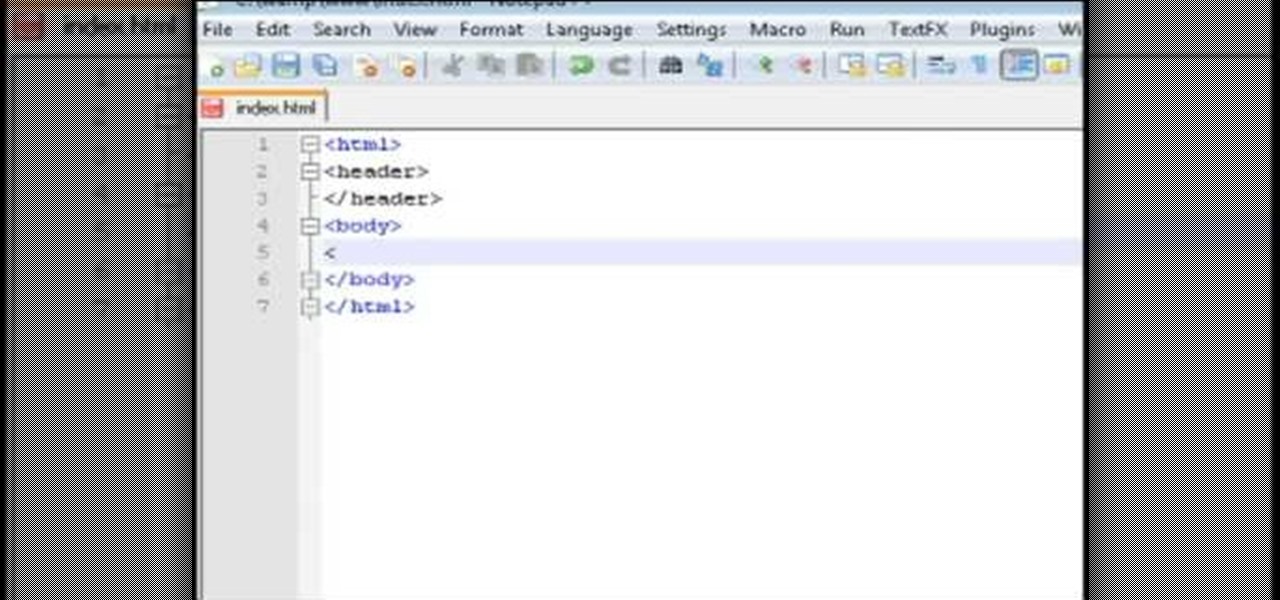
This video tutorial belongs to the software category which is going to show you how to set up a home server from behind a router using WAMP. You will need a free program called wampserver. Go to their website, download and install the program. Then click on the icon and click 'put online' and the local host comes online. To check it, open up your browser and type in local host in the search box and it will show you the default index.php file. Again click on the icon and click 'www directory'....

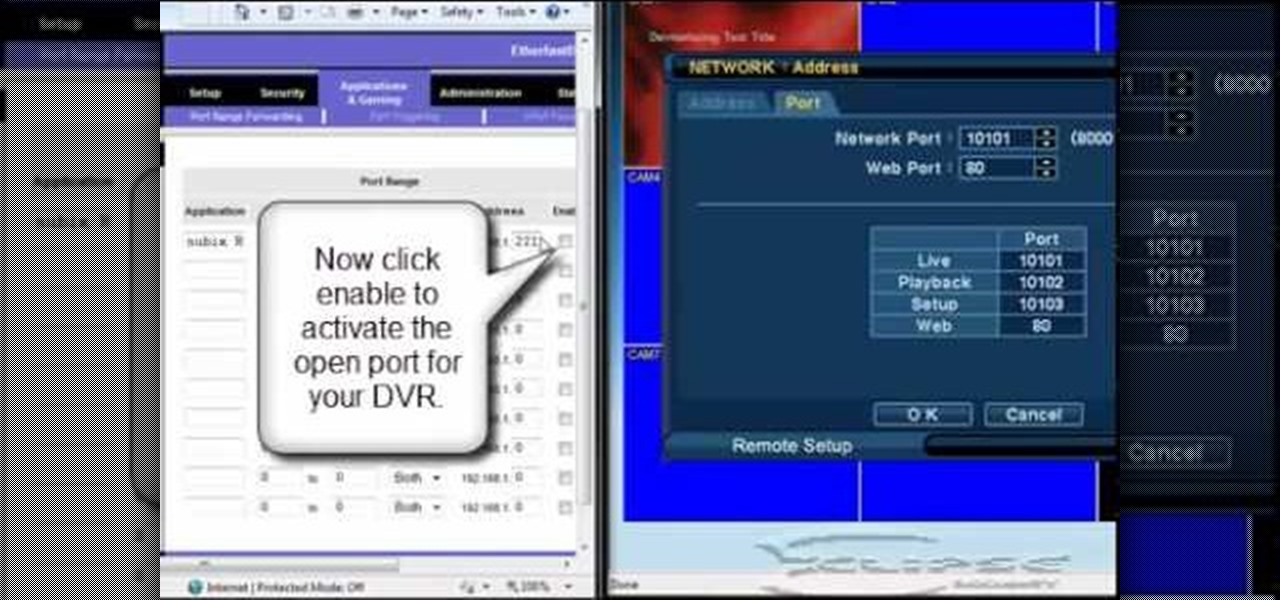
In this tutorial, we learn how to open ports on a Linksys router for your DVR. First, make sure your internet is connected and your DVR is connected to Linksys. Next, log into your Linksys router online and set up your DVR to the "DHCP" section. When you have the information from this, enter this information on your DVR so it has the correct server name. Make sure the IP and other information displayed on your Linksys page is the same as the setup on the DVR page. When finished, change your p...

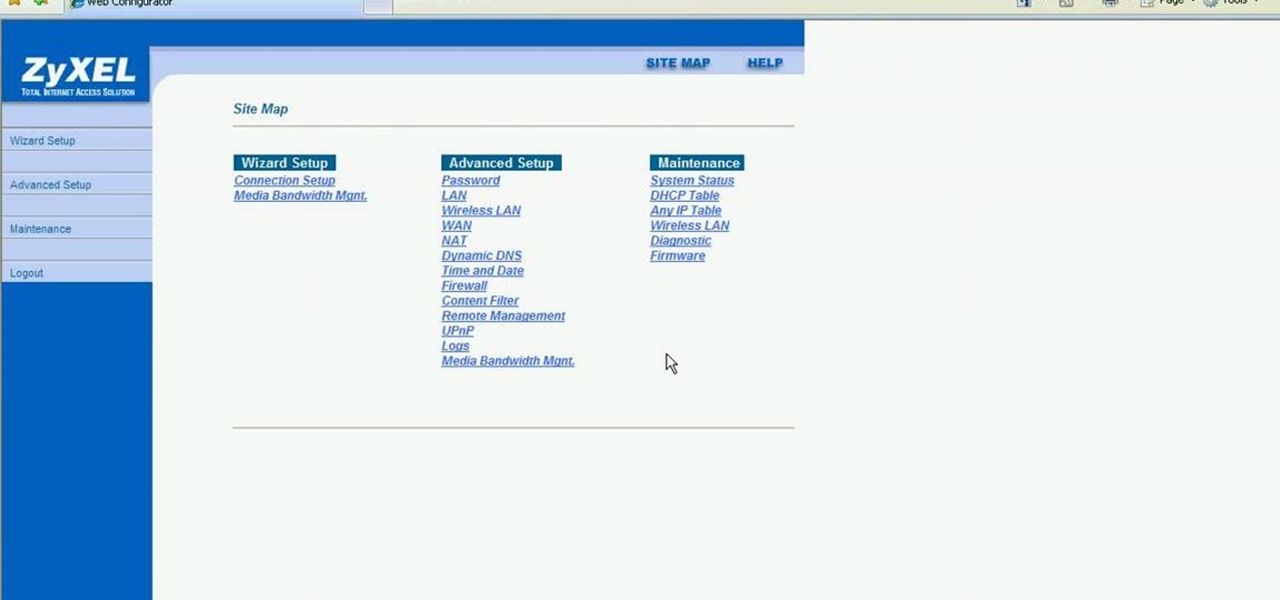
This video shows how to secure a wirelees internet connection on your Zyxel P-660hw-t1. For this, first click on Start button and open Internet Explorer(or any other browser). On the address bar of the browser, type in the IP address of your router. On the next page, enter your password and on the next page, either change the password or ignore. On the next webpage, under Advance setup, click on Wireless LAN. On the next page, click on 8021xWPA. Select authentication required and then click a...

Ever had router trouble? Got router trouble? Well don,t worry the people over from quickcert.com have made this video to help! More specifically a linksys 802.11g router. All new routers come with a standard Ethernet cable, which must be plugged into one of the four ports on the router and connected to your computer as well. This is necessary to change settings, using Microsoft IE (internet explorer) when the routers IP is typed into the address bar. It is strong recommended to change the def...

You can use your Ipod touch to SSH from windows. To do this go to Cydia and download Open SSH and Toggle SSH. Download and install these two applications. You will need to download and install Win SCP on your windows computer to work with the SSH. Now go to your Ipod applications and open the Toggle SSH application. From the welcome screen you can either enable or disable the SSH. Go ahead and enable it. Now close the application and open Win SCP on your desktop. From the first screen in the ...

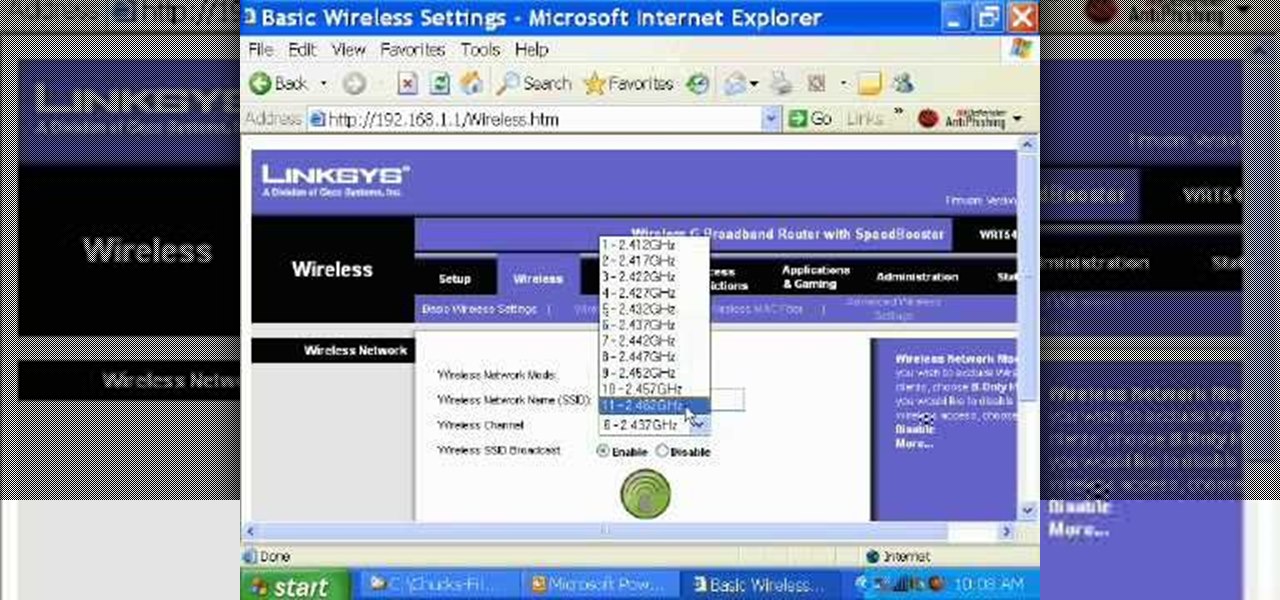
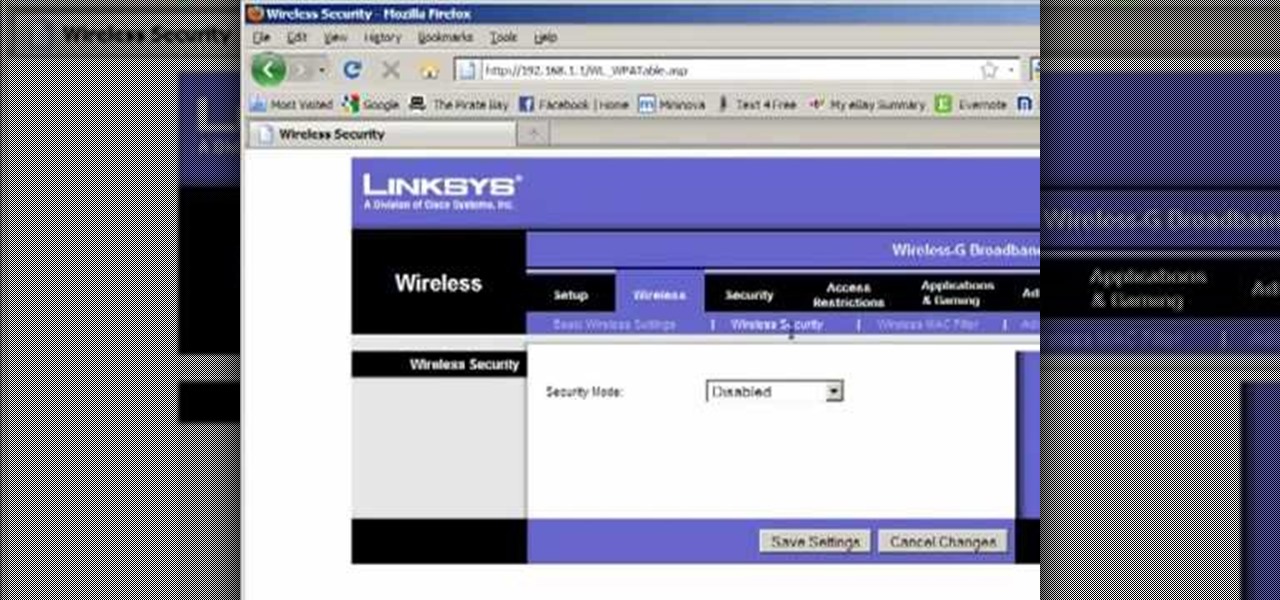
Llewyn demonstrates how to configure your router for Wifi. Access the router by opening up your internet browser and typing in your router's IP address. That will bring up the router configuration page. Now, click on the wireless tab. You can set the wireless network mode to accommodate your computers. As a precaution, set the mode to mixed for greater flexibility. Set your wireless SSD broadcast to enable which will enable your wireless card to actually see the webpage and the internet. You ...

In this video tutorial, viewers learn how to use Remote Desktop on Windows Vista to connect to another computer over a network connection, specifically Windows XP. You can get access to your Vista applications or data stored on a remote computer from your XP PC.