When you're scrolling through your iPhone's home screens, you'll inevitably reach the end and have to either swipe backwards or hit the Home button to return to the first page. Why Apple didn't instill an endless scrolling feature, or at the very least an option for it, is anyone's guess, but just because you can't do it out of the box doesn't mean you can't do it.

I rarely ever turn my desktop off. For starters, it takes a few minutes to boot up, which I hate, and secondly, putting the computer to sleep is perfectly adequate. You really only need to completely shut down your computer every once in a while.

In this tutorial, we learn how to check the brake system for motorcycle safety. First identify the fittings around the master cylinder and the hose that runs down around the bottom fittings. When you squeeze the levers on the bike, check to see if anything is leaking out of this, if nothing comes out you're good. Now, check the back of the back by finding the fittings, then looking to see if anything leaks when you are touching the levers. Make sure you have enough brake fluid and your brake ...

Want to play a beautiful version of "Beautiful Day" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Beautiful Day" on your own guitar, watch this video guit...

Want to play "Until the End of the World" by U2? See how it's done with this free video guitar lesson, which presents a complete (and we mean complete) breakdown of the song and its constituent parts. While this tutorial is geared toward those who already have some knowledge of the guitar, players of all skill level should be able to follow along given adequate time and effort. For more information, and to get started playing "Until the End of the World" on your own guitar, watch this video g...

One of the ultimate goals in hacking is the ability to obtain shells in order to run system commands and own a target or network. SQL injection is typically only associated with databases and their data, but it can actually be used as a vector to gain a command shell. As a lesson, we'll be exploiting a simple SQL injection flaw to execute commands and ultimately get a reverse shell on the server.

Whenever you attend or remotely watch a major Apple event, you're likely to see Phil Schiller, the company's senior vice president of worldwide marketing, unveiling a brand new product on stage. Outside of an official event, Schiller is the second most likely person (after Apple's CEO Tim Cook) you'll find delivering a rare tidbit of new Apple info or perspective to the public.

Facing claims of misappropriation of trade secrets and confidential information by Meta Company, DreamWorld, led by Meta's former employee, Zhangyi "Kevin" Zhong, has fired back with a motion to dismiss the lawsuit.

Responding to the rapid emergence of dangerous pathogens around the world, a new initiative to prevent or contain pandemics was announced in Davos, Switzerland, yesterday. If you ever worried that a highly contagious pathogen could take down your community, or the country, this news is for you.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

When Google introduced the Call Screen feature with the Pixel 3, I had never been more excited to get a Pixel device. This AI feature provided real protection against rising spam and robocalls, which billions of people deal with each year. After a recent update to the feature, you can reduce robocalls and other spam calls to nearly zero.

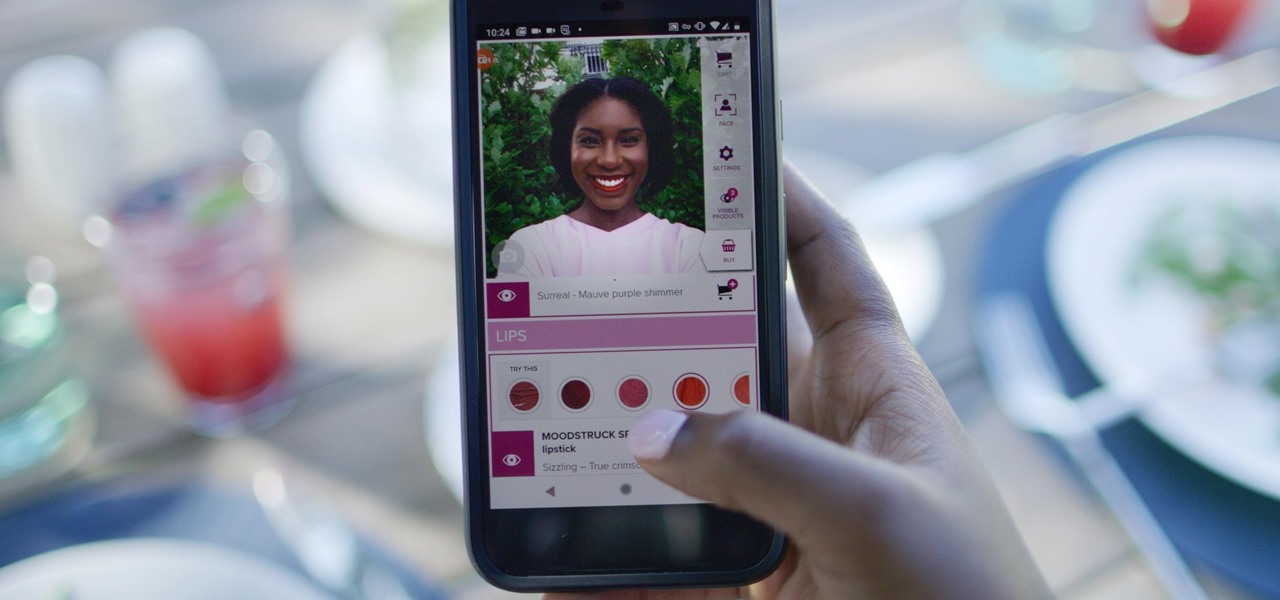
Now that some of the best-known beauty brands are leveraging augmented reality to market and sell products, the rest of the market is beginning to catch up — fast. The latest competitor to add AR to its arsenal is direct sales makeup company Younique.

Months after Next Reality broke the story surrounding the financial troubles at Meta Company, there's a new update in the company's ongoing patent lawsuit.

With the change to a glass back, many of us are concerned about the durability of OnePlus 6. While glass does offer some benefits such as lighter weight, without proper reinforcement, it can easily shatter in one drop. Now we have our our first look at its durability thanks to JerryRigEverything.

There's now more reasons to make sick workers stay home—a new game theory study suggests adequate hand washing and other illness-aversion tactics aren't as useful as we thought to keep you from getting infected when a virus or bacteria is circulating.

For me, YouTube on my Samsung Galaxy S3 is more of a music player, not a video player. I have tons of YouTube playlists for music, but since I'm mostly only interested in listening, it'd be nice if YouTube would continue to play in the background while I use other apps.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

If you find yourself with a roommate hogging limited data bandwidth with video games or discover a neighbor has invited themselves into your Wi-Fi network, you can easily take back control of your internet access. Evil Limiter does this by letting you control the bit rate of any device on the same network as you, allowing you to slow or even stop data transfer speeds for them completely.

During the keynote at WWDC earlier this year, Apple introduced the latest iteration of its mobile operating system, iOS 12. Despite a thorough demo on stage, Apple glossed over new eye tracking features that use ARKit 2. Developers can now use the TrueDepth camera on the iPhone X, XS, XS Max, and XR to determine where your eyes are looking, opening up incredible new possibilities for new apps.

The microphone in a Windows computer is accessible to most applications running on the device at all times and completely without security limitations. Information gathered from recorded audio conversations taking place in the surrounding area of a compromised computer can be used for social engineering, blackmail, or any number of other reasons.

In July 2017, LG announced a new smartphone lineup, the Q series. These devices focus on providing some flagship features at a more affordable cost — features such as an 18:9 1080p display. LG's goal here seems to be adding value for the more budget-conscious users, and in 2018, they've continued the series with the Q7.

One of the standout features of Nova Launcher is its vast customization options. Not only does it includes numerous tweaks to alter the aesthetics of your home screen, but it even has plenty of features that reduce clutter. One area of our device that has a high potential for disarray is our home screen.

Most of us have never put much thought into this, but the question needs to be asked — what exactly happens to all of our online accounts when we die? No, the internet won't just know and delete accounts for you, so you need to plan for life's one guarantee. Because without a plan, things become a lot harder to sort out.

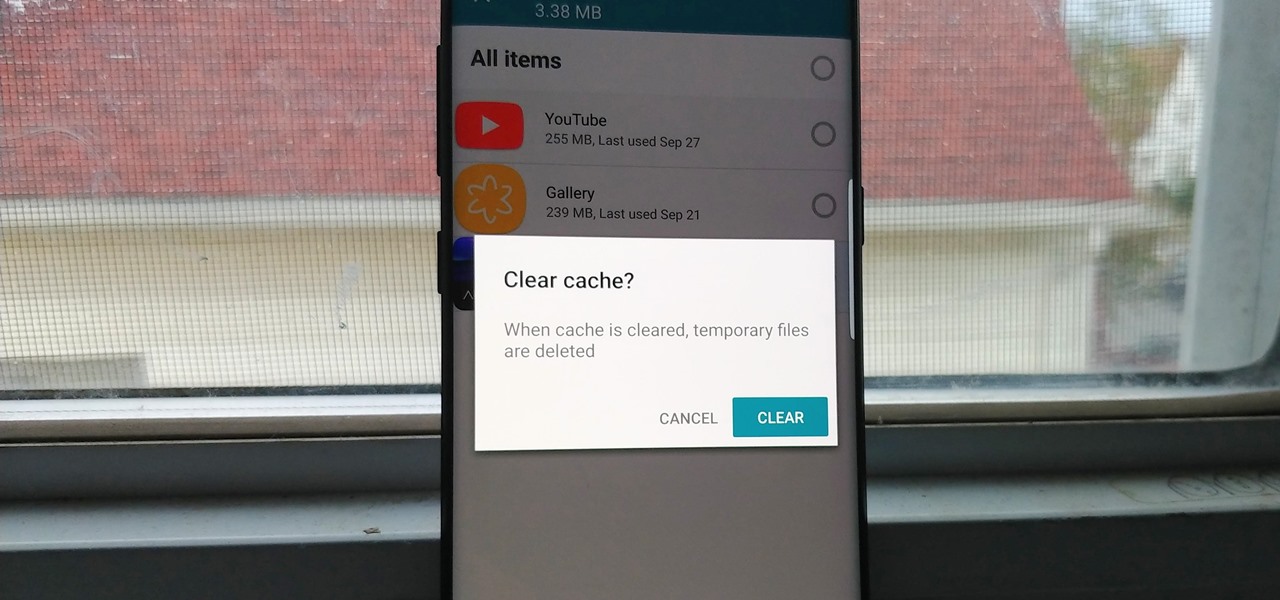
Since the release of the T-Mobile G1, the Play Store has been flooded with apps that claim to improve performance by clearing cache and storage. These apps are typically useless, rarely providing more than a temporary fix which Android undoes immediately. As Android has continued to improve cache and storage management, such apps have become more trivial. However, there are few decent ones out there.

When hacking Wi-Fi networks, having the right wireless adapter is essential. But hunting online for one can be a frustrating experience. To see how the handful of Kali-compatible adapters on the market measure up, I ran a series of tests to benchmark and compare their range, signal strength, and ability to enter monitor mode and perform packet injection. This should help you determine which adapter is right for your own hacking needs.

Google just bought a huge chunk of HTC for $1.1 billion. They're bringing in around 2,000 employees, mostly from the hardware division, and these folks will presumably work under hardware chief Rick Osterloh. There's a massive patent portfolio involved, too, so stop me if you've heard this before — Motorola, anyone?

Coronaviruses are common viruses, and most of us catch one at some point — they cause about 30% of all common colds. A new accidental discovery could help fight these viruses, even the deadlier, emerging ones.

Cholera is rapidly spreading in Mozambique, with over 1,200 people infected. Since the outset of 2017, cholera has spread from the capital city of Maputo (pictured above) to three of its ten provinces. Health officials report other areas in the country are seeing case counts rise, and two deaths have been logged so far.

Call them what you will—moss piglets, water bears, or by their real name, tardigrade—but these intriguing tiny creatures can come back from the brink of death. They can survive boiling, deep freezing, UV radiation, completely drying out, and even a trip to space—without the benefit of being in a spacecraft.

Hospitals are places we go to get well, and we don't expect to get sick or sicker there. But a study from researchers at the Cleveland Clinic, Case Western Reserve University School of Medicine, and Cleveland VA Medical Center in Ohio found that hospital floors in patient rooms were frequently contaminated with healthcare-associated pathogens—often dangerous multi-drug resistant bacteria.

Responding to the emergence of Zika in the US, researchers investigated what type of repellent works best to reduce your odds of a mosquito bite from Aedes aegypti, the mosquito species that spreads the Zika virus.

Cholera may be rare in the US, but cases of the disease have increased worldwide since 2005, particularly in Africa, southeast Asia, and Haiti. An estimated 3 to 5 million people are infected, and more than 100,000 die from the disease globally each year, mostly from dehydration.

Are we about to witness the future of Android OS? Of Google? Of the entire smartphone ecosystem?! Google has just turned 18 today (right?), Android just had its 8th birthday, and the rumor mill is firing on all cylinders in the lead-up to the October 4 launch event where they'll announce their latest hardware and software products.

Injustice: Gods Among Us is one of the most popular games to come out over the last couple of years. It was a hit on video game consoles, and it's got a solid 4.5 rating on both Google Play and the iOS App Store, with almost 2 million people rating the game combined.

Third-party keyboards have been available for iPhone ever since iOS 8, but which ones are worth checking out? There have been many options over the years, and if you want keyboard features like swipe-typing and themes, you're going to have to put Apple's stock QuickType keyboard on the backburner and try out these top hits.

Broccoli is super. Not only is it jam-packed with nutrients like vitamin C, vitamin A, folic acid, calcium and fibre, but it's one veggie that refuses to be just a side-dish. Nobody puts broccoli in the corner.

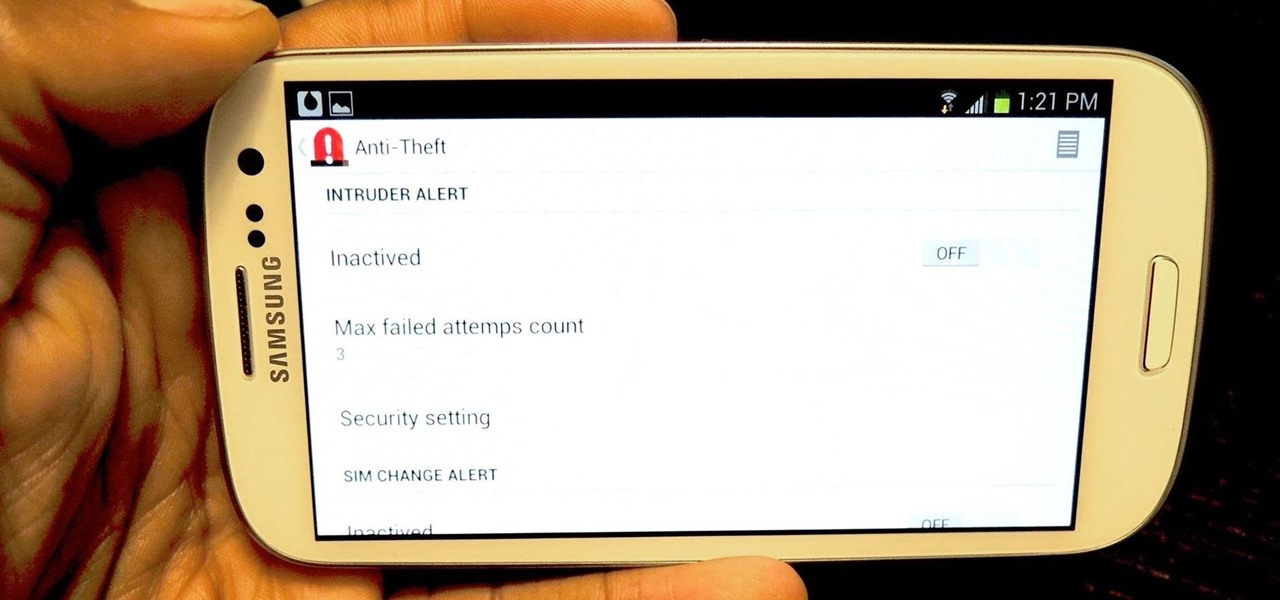
I love surprises. Surprise parties, surprise visits, surprise Patrick... But there are times when a surprise is the last thing you want, like reaching into your pocket to find that your Samsung Galaxy S3 is not where it should be.

The big fireworks day is almost here, but most of you are limited in what you can do when it comes to celebrating the Fourth of July with a bang. Unless you live in a dry area prone to wildfires, one type of fireworks you can probably still legally buy are sparklers.

This summer's going to be a hot one, so skip the water pistol this year and break out the big guns! In this project, I'll be showing you how to build a water balloon shotgun—a high-powered water balloon launcher that's capable of firing 17 water balloons at the same time!