Ron Hazelton explains how to protect your foundation or basement wall from being affected by water that is discharged from your downspout. He explains how downspout extenders can be used to carry the water away from the foundation. Ron will show you three variations of downspouts that you can use. You'll learn how to install each kind of downspout so you can decide which is right for you. If you follow the advice given in this video, you're sure to further protect a very important part of you...

Take a look at this instructional video and learn how to run a USB cable through existing phone cords. You'll need two phone jacks, a USB extender, and a phone cord. Although dual jacks are featured in this video tutorial, single jacks are preferred. The process is fairly simple, what you need to do is open up the jack and cut the USB extender in half. Strip to the multicolored wires and match up the the wires with the opened phone jack's, all except for the white wire which will go to the ye...

Wi-Fi devices are continually emitting "probe frames," calling out for nearby Wi-Fi networks to connect to. Beyond being a privacy risk, probe frames can also be used to track or take over the data connection of nearby devices. We'll explain how to see nearby devices emitting probe frames using Probequest and what can be done with this information.

If you have a subscription with Verizon Wireless to use the mobile hotspot feature on the Motorola Droid Bionic Android smartphone, you can provide internet access to any nearby device with a WiFi connection by accessing the mobile hotspot application on your Bionic. This guide from Motorola will walk you through the process, but be careful because the hotspot feature will drain your battery!

If you just brought home a Windows 7 notebook or desktop PC, but you can't figure out how to configure the WiFi connection to get internet on it, take a look at this guide to learn how to connect your Windows 7 computer to a home network.
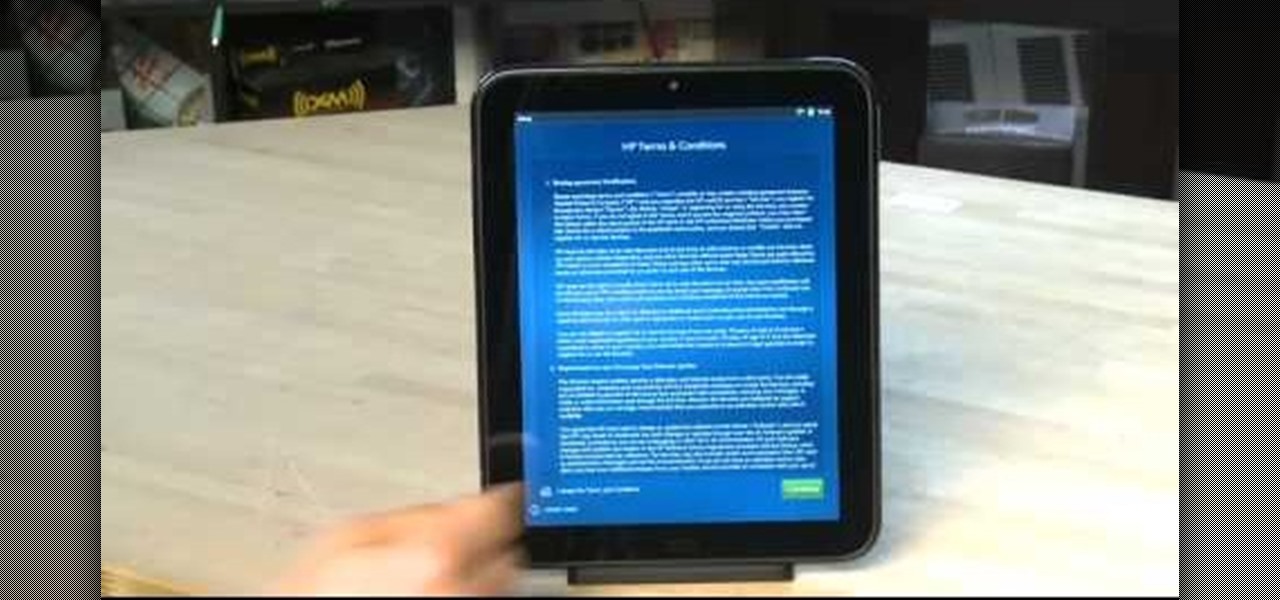
If you were one of the lucky individuals to score a TouchPad before HP discountinued them, you will need to proceed through the initial setup wizard when you turn on the device for the first time, or after performing a data wipe and reset on the tablet. This guide will walk you through everything from accepting the terms & conditions, connecting to a Wi-Fi network, and creating a webOS account for the first time.

Firesheep is a packet sniffing browser exploit that can access the exposed accounts of people on Facebook and Twitter while they use public Wi-Fi connections. This video shows what steps can be taken to protect yourself against someone accessing your Facebook account.

Learn how to update the software on your BlackBerry device over a WiFi or Wi-Fi network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

Learn how to discover and connect to close-by wireless (Wi-Fi) networks on your BlackBerry Pearl 3G. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

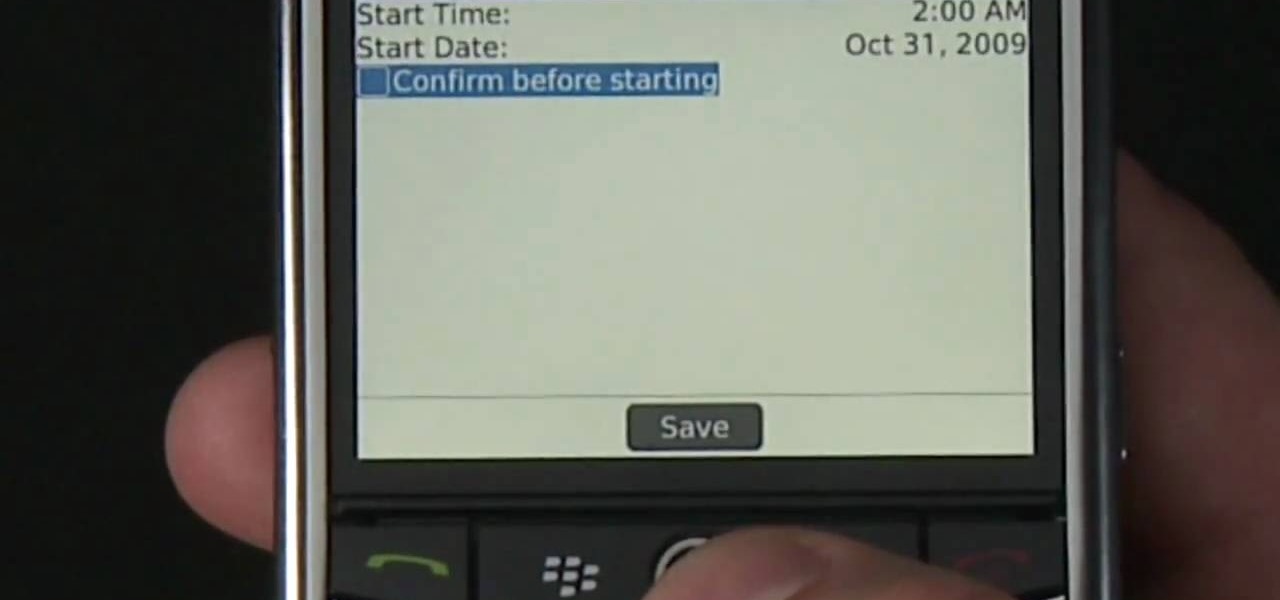
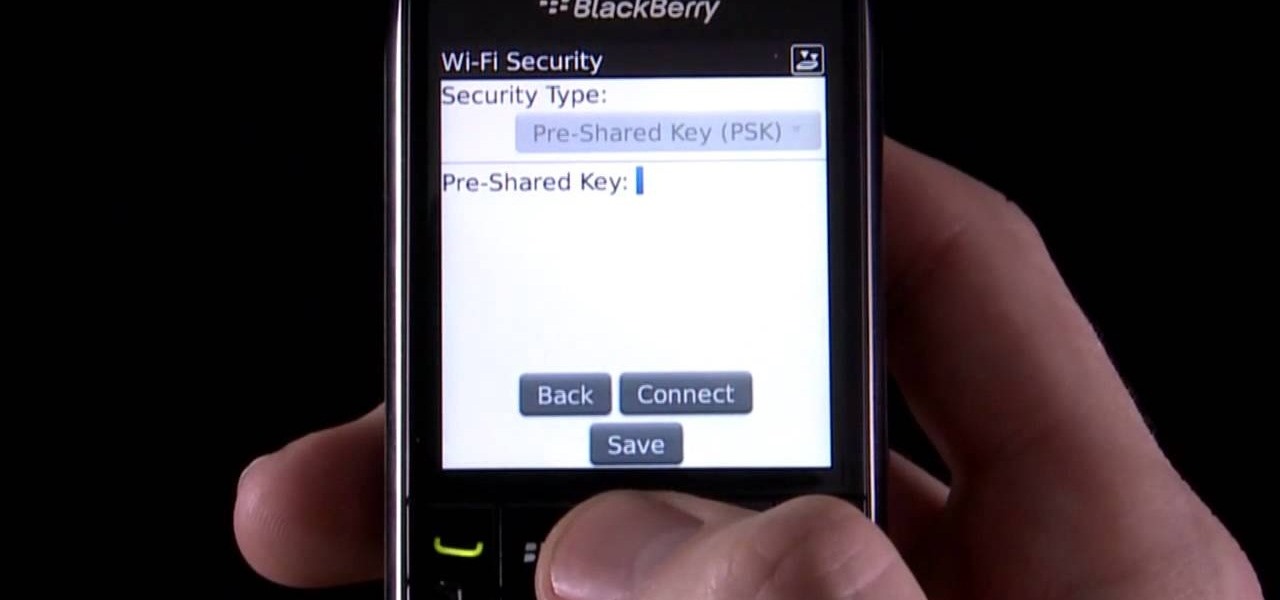
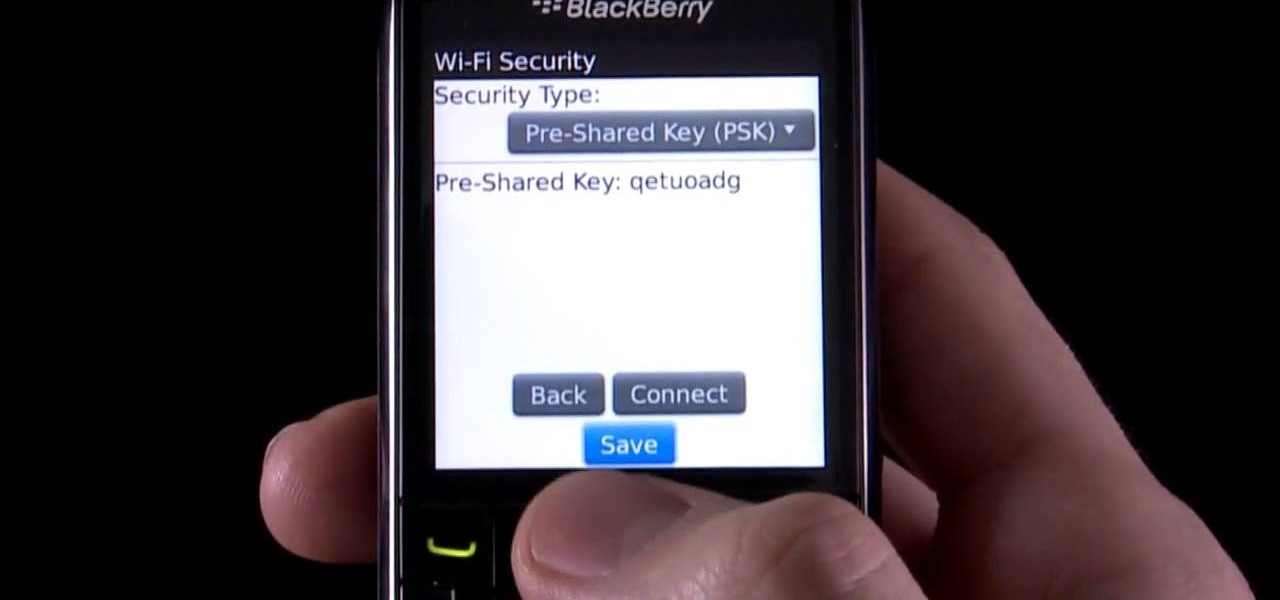
Learn how to force your BlackBerry Pearl 3G to connect to a specific wireless (Wi-Fi) network. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

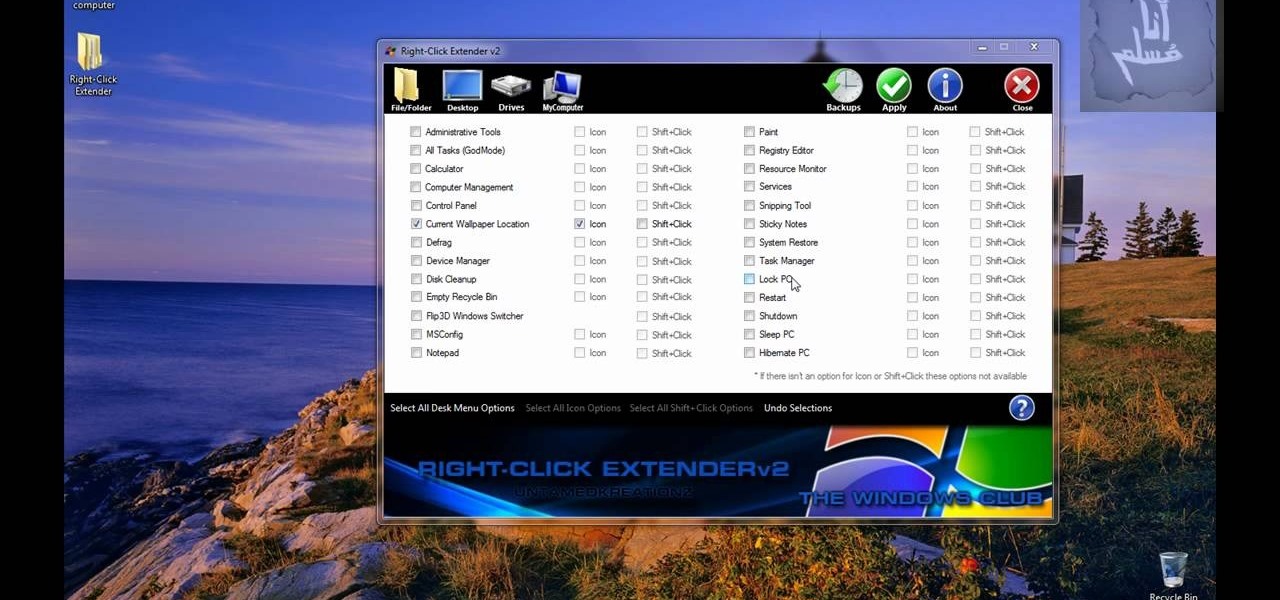
Tired of being limited with your right-click options in Microsoft Windows? There's a program that could help you out, and it's called Right-Click Extender. Insert many different additional items to the right-click context menu.

Pretty soon, every restaurant and store you walk into will know exactly what you're doing. Retail analytics companies like Euclid, ShopperTrak, RetailNext, and Prism Skylabs have penetrated hundreds of food shops and retail stores across the country, installing sensors that track and log customers' moves while they dine and shop.

This video tutorial belongs to the Electronics category which is going to show you how to make a hack pack. This is basically turning a notebook in to something that you can take literally anywhere. Here you will learn how to create a video streaming hack pack to carry around with you and be able to do live internet shows anywhere. For this you will need a netbook, Sony PSP, mobile Wi-Fi thumbstick, microphone and a webcam with Velcro or adhesive. Plug in the mobile Wi-Fi stick for internet c...

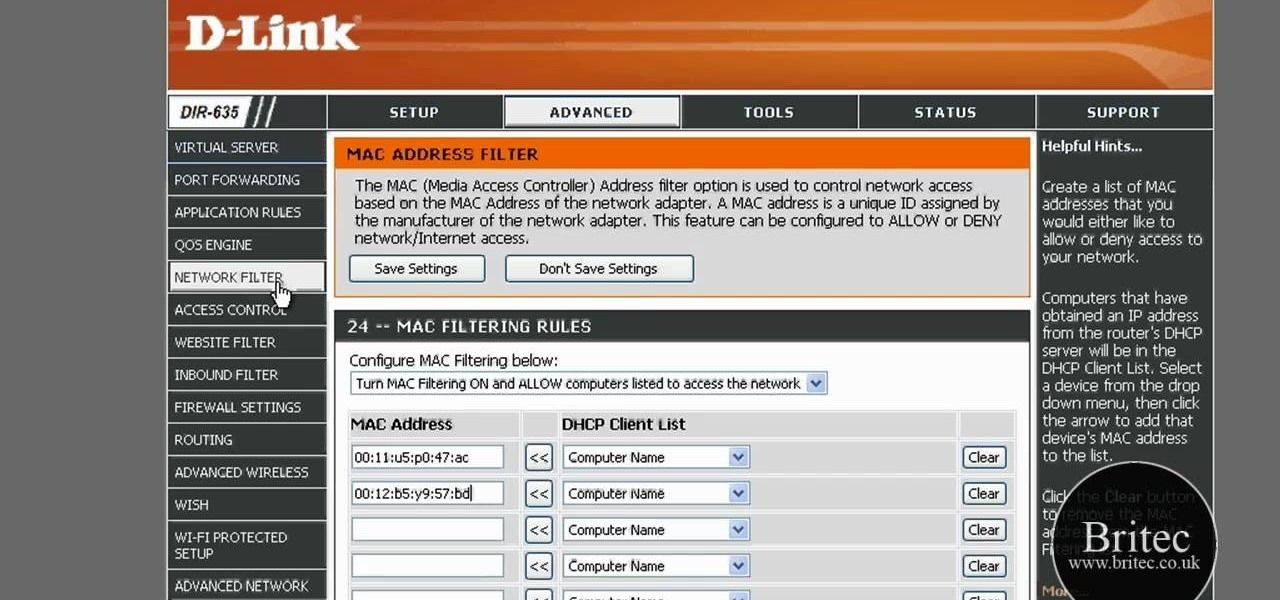
In this tutorial, we learn how to detect all computers connected to your Wi-Fi network. To begin, go to the website, http://msdn.microsoft.com/en-gb/netframework/aa569263.aspx. Once you are on this site, download and install the program. Once it's installed, open the program and then look for the MAC address. Once you find this, go back to the website and enter this into the MAC address line. After you do this, you will be able to see what computers are listed on your network. If you see any ...

In this video tutorial, viewers learn how to fix the Wi-Fi problem on an iPod Touch or iPhone. Begin by clicking on Settings and select General. Then scroll down to click on General and select Reset Network Settings. When a confirmation window pops up, click on "Reset Network Settings". The iPod device will then reboot. Now click on Settings and select Wi-Fi. Then select a network to connect to. This video will benefit those viewers who have an iPhone or iPod Touch, and would like to learn ho...

TooSmartGuys teach viewers how to hack their iPhone using Black Ra1n and Sn0w. First, if you have a jail broken iPhone you should back up your apps by downloading a program called App Back Up. Now, plug your iPhone in and let iTunes load. Allow it to update and you should see the iTunes icon on your phone and the cord picture. Open up Blackra1n and click the button that says make it rain. Your phone reboots and there will be a new app on there called blackra1n. Launch this app and you can put...

After reviewing the international plans for major US wireless carriers, it became obvious they're all pretty bad. Your data is heavily restricted, requiring a daily fee which can cost an extra $100+ on a seven-day vacation. That's when I learned about Google Fi, and how for most travelers, it's the best option.

Wi-Fi signals have limited range, so if you live in a two-story house or work in a larger office, you may have set up multiple routers or repeaters to ensure full wireless coverage. Sadly, Android handles the transition between networks pretty poorly.

Apple's unveiling of the iPhone 6S, iPhone 6S Plus, Apple TV, and iPad Pro dominated the news today, but at the end of their special September 9th event, they quietly released the final version of iOS 9 to developers, called the Gold Master (GM) build.

Your Apple Watch is a fantastic tool that can help you perform daily tasks on your iPhone. Notifications get filtered through it, you can respond to messages on it, and you can even use Apple Pay to purchase goods and services. Your Apple Watch is also a valuable asset when it comes to finding your lost iPhone, too.

Chromecasts can make for some fun nights. Whether you're setting up a collaborative YouTube watch list, letting everyone add to a giant party playlist, or playing games like Cardcast and Big Web Quiz, Google's streaming media stick is a hit by all accounts.

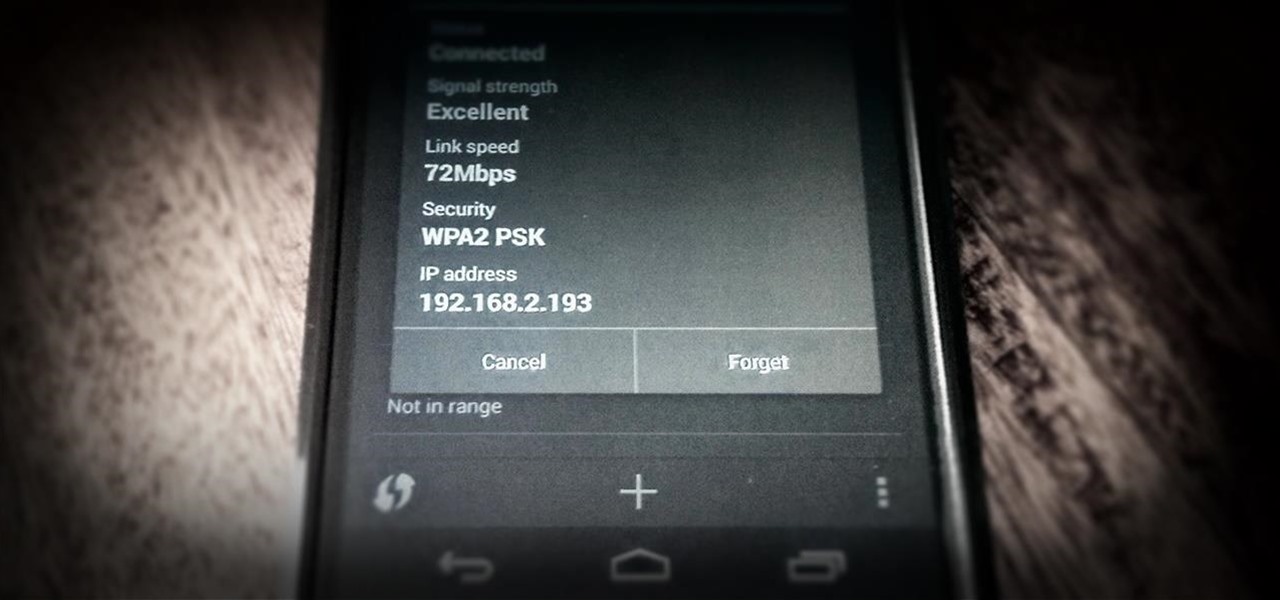
One of the most common complaints that people have about the Nexus 4 would have to be its intermittently poor Wi-Fi performance, a problem that for many, persists through the installation of updates and even custom ROMs.

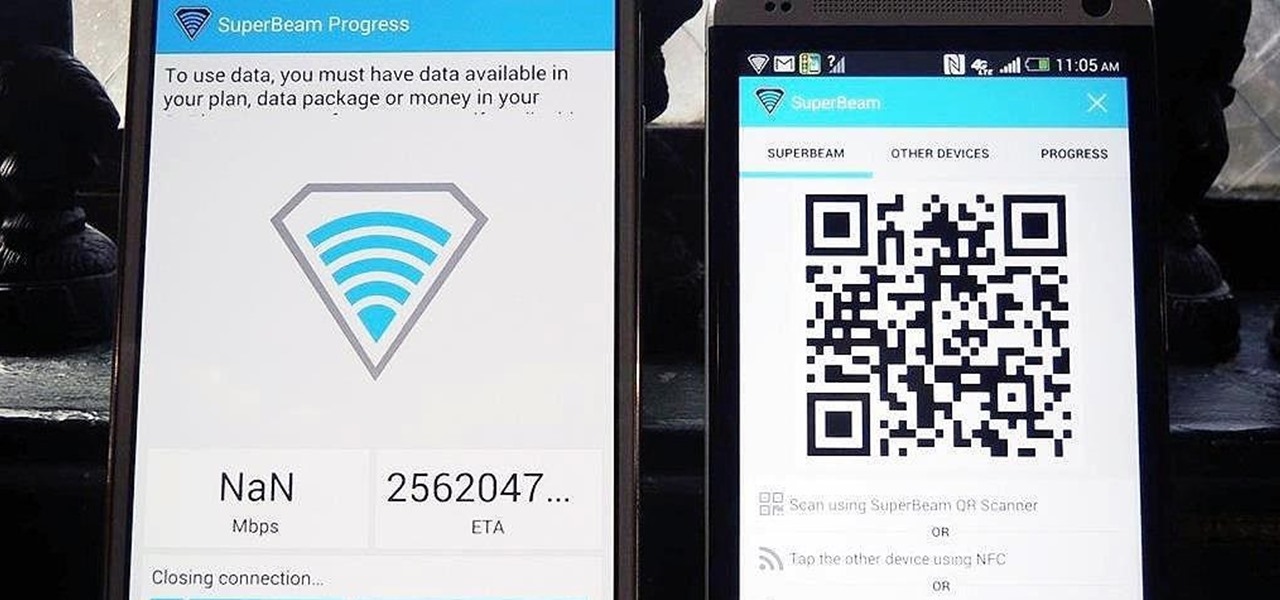
Sending and receiving files between Android devices has no shortage of options—Bluetooth, email, MMS, and Wi-Fi are just a few of the more popular ones that we use.

Applications, features, and software running in the background of your Samsung Galaxy Note 2 can drain a significant amount of battery power, even when your smartphone isn't being used. For this reason, smartphone carriers and developers suggest that you turn off Bluetooth, Wi-Fi, and other battery hogging features when they're not being used.

Pyrit is one of the most powerful WPA/WPA2 cracking tools in a hacker's arsenal, with the ability to benchmark a computer's CPU speeds, analyze capture files for crackable handshakes, and even tap into GPU password-cracking power. To demonstrate how quickly it can hack a WPA/WPA2 password, we'll use it to play a Wi-Fi hacking CTF game anyone can practice for less than $10.

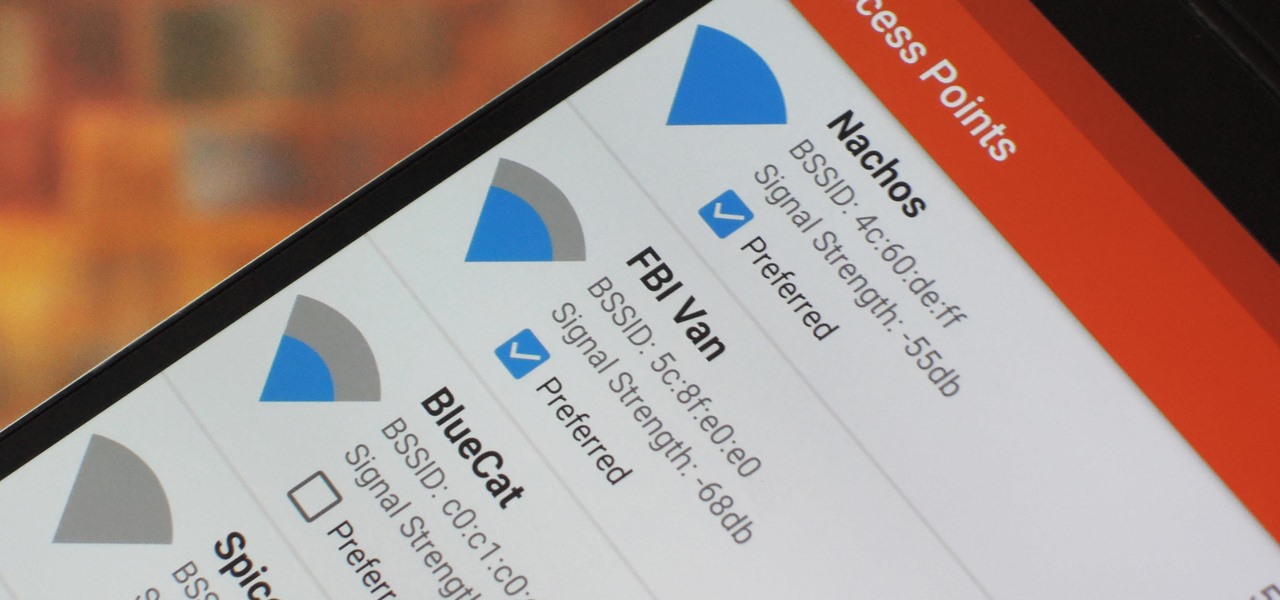
What if you could easily visualize which access point every Wi-Fi device nearby is connected to in a matter of seconds? While programs like Airodump-ng can intercept this wireless information, making it easy for hackers to use and understand is another challenge. Fortunately, a tool called Airgraph-ng can visualize the relationships between Wi-Fi devices from only a few seconds of wireless observation.

There are many ways to attack a Wi-Fi network. The type of encryption, manufacturer settings, and the number of clients connected all dictate how easy a target is to attack and what method would work best. Wifite2 is a powerful tool that automates Wi-Fi hacking, allowing you to select targets in range and let the script choose the best strategy for each network.

These days, eReaders are everywhere. For die-hard book nerds, eReaders offer the convenience of a full library without having to sacrifice shelf space. Sure, there are the paper buffs who swear that you just can't take an eReader with you into the bathtub, but when's the last time anyone actually did that? Face it, eReaders are convenient and here to stay. But there's a dizzying array of information out there, so what should you look for in an eReader?

Did you know that you can improve the Wi-Fi in your home without the stress of changing providers or using a costly professional? The answer lies in a simple app you can use yourself at home, and right now, the NetSpot Home Wi-Fi Analyzer With Lifetime Upgrades is on sale for just $39.99. That's 41% off the regular price of $68.

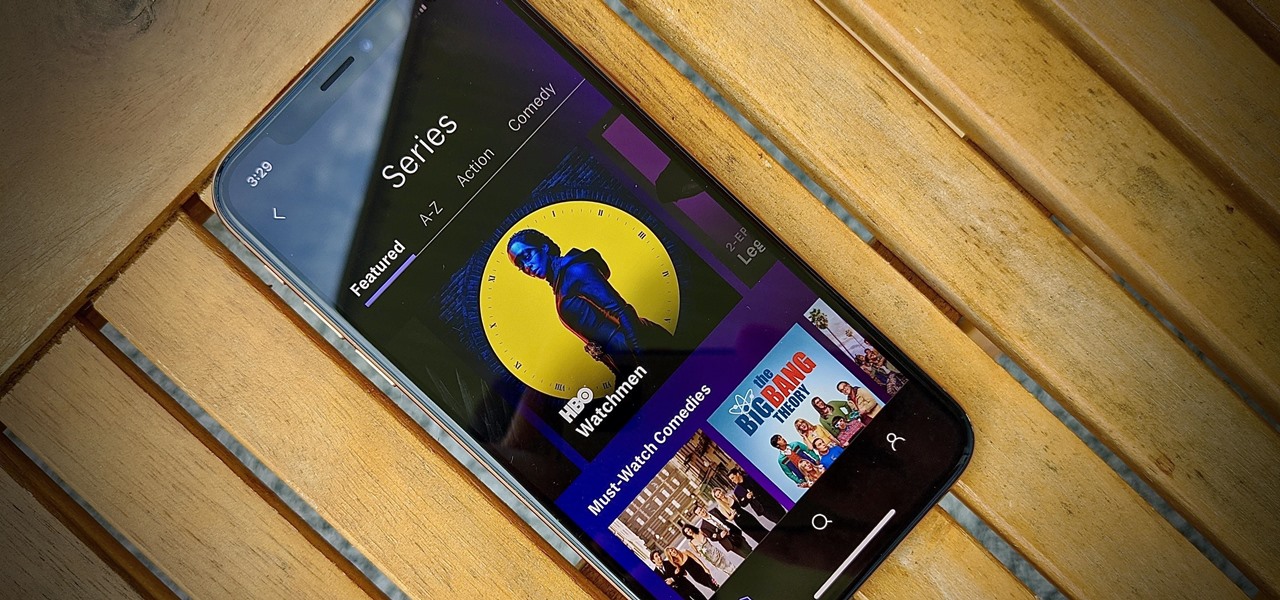
HBO Max is finally here, all while unlimited cellular data plans have never been more available. The two seem like a perfect pair, but you might find that you can't binge "Friends" or "Westworld" on the go. At least, not without downloading episodes beforehand. Fortunately, there's an easy way to fix that.

A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

If your iPhone XS or XS Max has been suffering from Wi-Fi connectivity and charging issues, Apple just released iOS 12.0.1 on Monday, Oct. 8, as an over-the-air update for all compatible iPhones. The main focus of the update is to give fixes for users going through "Chargegate" and experiencing Wi-Fi issues.

Samsung just began rolling out the Oreo Beta 2 to registered users of the Galaxy S8 and S8+. The update's changelog promises the inclusion of the October 2017 security patch. Unfortunately, after downloading the update, we've noticed this is not the case. Omission of the more recent security patch is notable in that it leaves devices vulnerable to several known exploits, such as KRACK.

Once you connect all of your devices to your Wi-Fi router at home, you'll never need that long, complicated Wi-Fi password ever again, right?

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

The biggest pet peeve of many Google Now users has always been the fact that you can't toggle basic system functions with voice commands. In fact, this was such an annoyance that folks even went so far as to apply root mods to get the functionality.

A security analyst has discovered a flaw in Chromecast's initial setup process that allows would-be hackers to assume full control over the online streaming device.

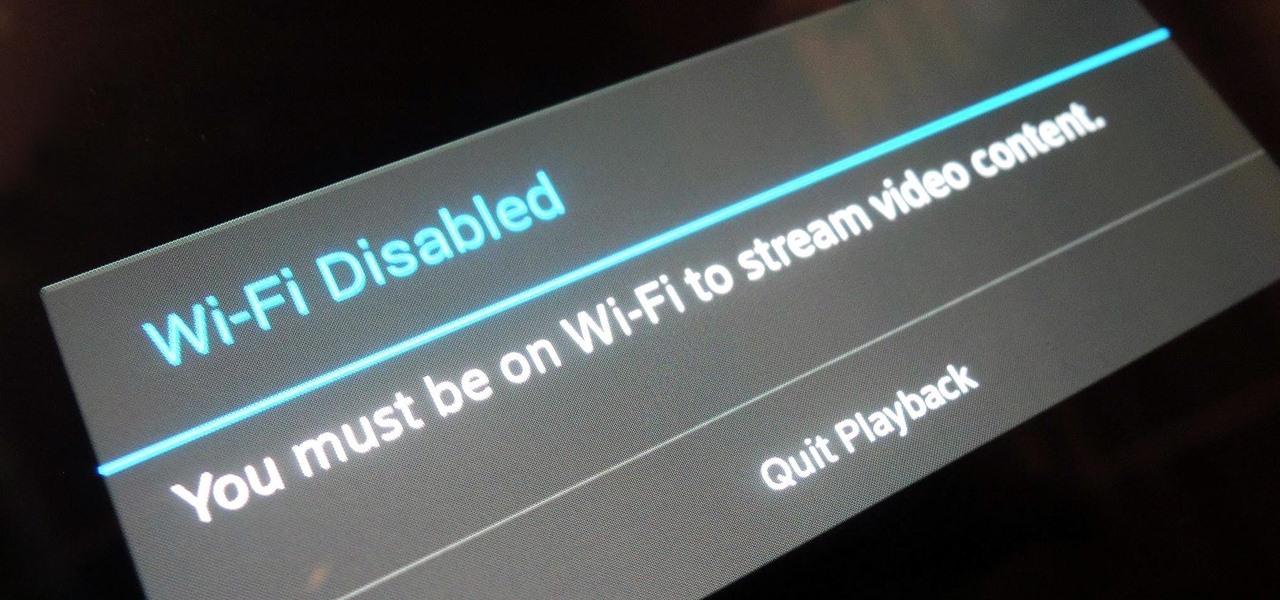
For any multitude of reasons, some apps require you to be connected to Wi-Fi in order to function properly. This could be because they would rather you have a stable connection to enjoy their content, or that they don't want users complaining about the amount of data being guzzled from carrier data plans.