Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

Apple released the iOS 8 Gold Master build to developers shortly after their WWDC event ended on Sept. 9th, which is jam-packed with tons of new features for iPad, iPhone, and iPod touch. The public version comes out on Sept. 17th, but if you can't wait to test out iOS 8, you can get it right now.

Welcome back, my budding hackers. So many of you are interested in hacking Wi-Fi that I have decided to revisit my Wi-Fi Hacking series with some updated and more in-depth material. I strongly suggest that you look at some of my earlier posts, such as "Getting Started with Terms and Technologies" and "Getting Started with the Aircrack-ng Suite of Wi-Fi Hacking Tools," before continuing here. If you're ready, you can also check out our updated 2017 buying guide here.

Airports are terrible germ-infested purgatories where people sit around for hours without Wi-Fi while they anxiously await to get wherever they really want to go. Unfortunately, there isn't much we can do about waiting, but this little Wi-Fi hack could help make the waiting a little less boring.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.

Check out this helpful video to learn how to install Skype mobile video chat on your HTC Thunderbolt. First, download the file here then follow all of the instructions to get your Android smartphone running Skype video chat on Wi-fi and 4G.

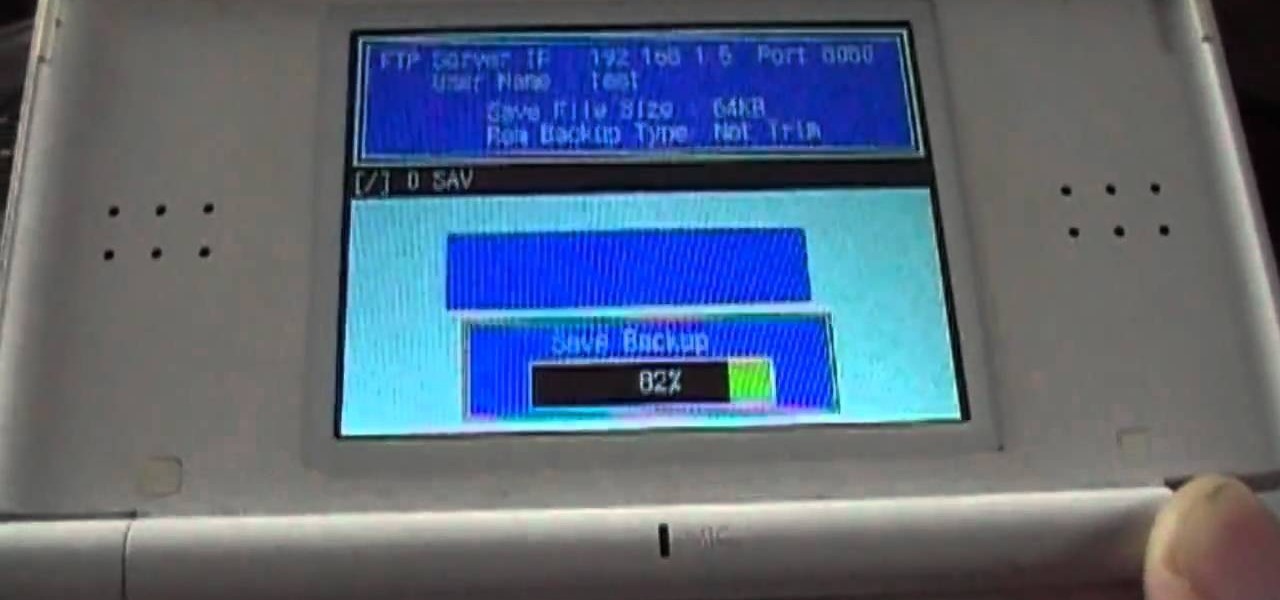
If you'd like to capture footage from your Nintendo DS, either to share online or make walkthroughs or playthroughs with commentaries, download all of the necessary files from Lifehacker, then watch this video for step-by-step instructions on how to get capturing. For recording gameplay this way, you'll need a DS or DS Lite, microSD card, NDS flash cartridge, Wi-Fi connection, SD card reader and a computer (along with all of those files you need to download).

In this clip, you'll learn how to use an Apple iPad as a wireless monitor for a still camera. In order to replicate this hack yourself, you'll need an iPad, Eye-Fi Pro X2 SD card, My Wi and Shutter Snitch. For detailed, step-by-step instructions, and to get started sending pictures directly from your digital camera to your iPad, watch this video guide.

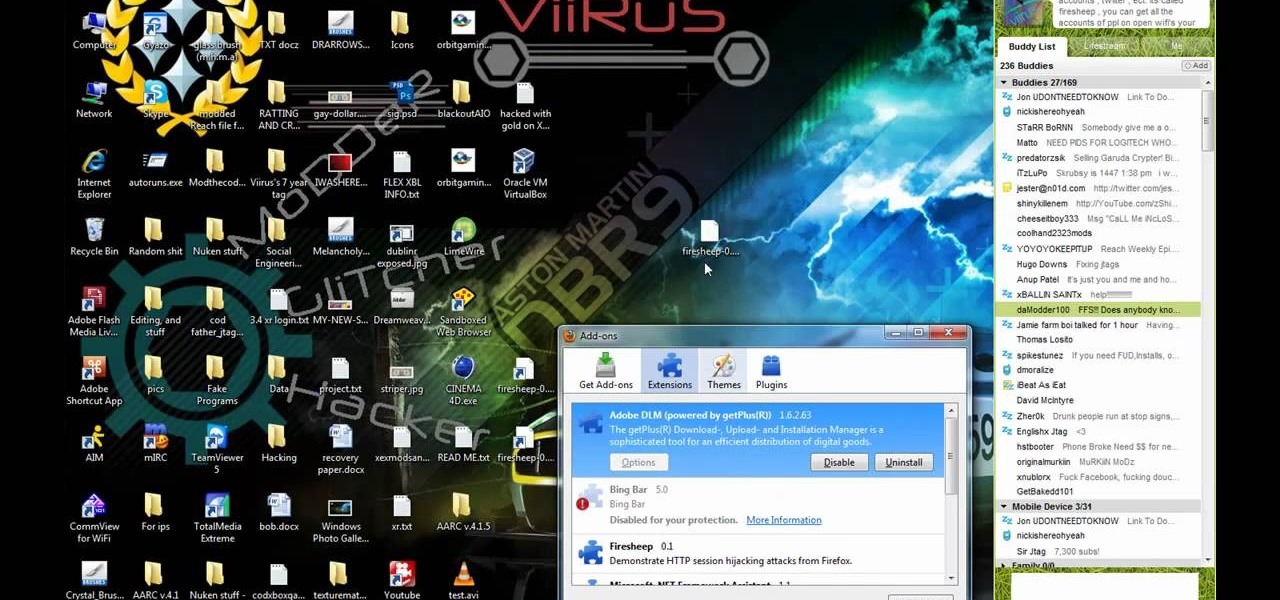
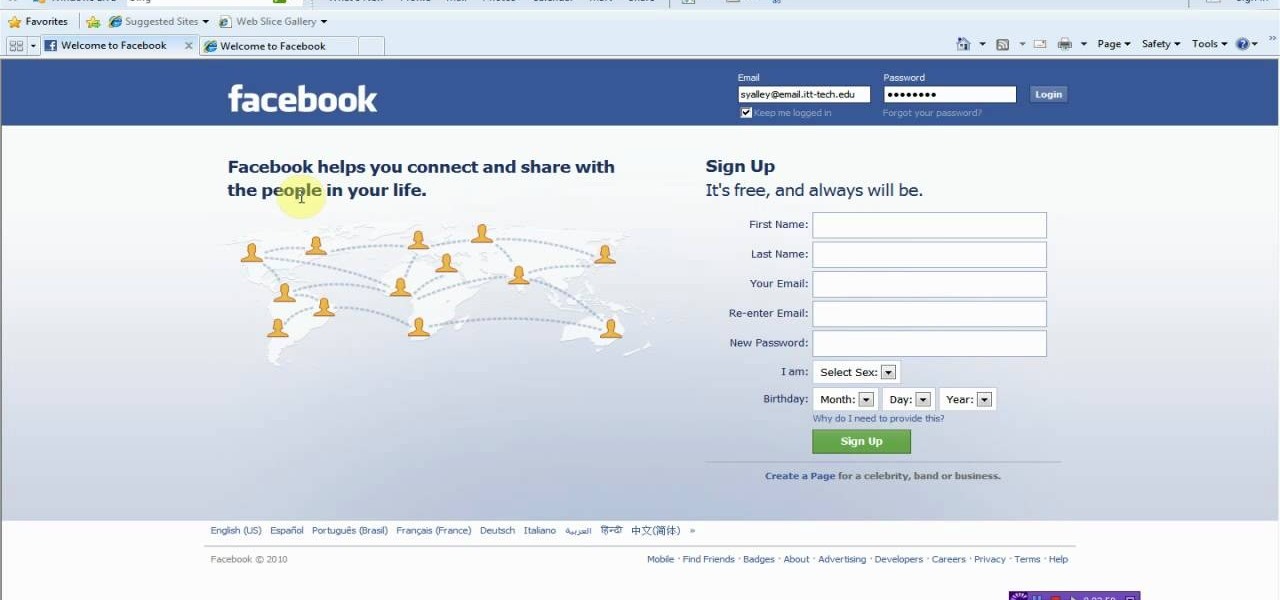
Ever wanted to hack your friends' Facebook accounts? With the Firesheep Mozilla Firefox browser add-on, it's easier than ever. Before you can use Firesheep to sniff account cookies, however, you'll need to download and install it. This clip will teach you everything you'll need to know.

Firesheep! It's a good reason to be cautious when using public Wi-Fi. But is it reason to stay off of open networks altogether? Certainly not! There are, in fact, a few simple steps you can take that will make you invulnerable to the malicious Firesheep Firefox addon. Learn how to protect yourself against Firesheep with this video guide.

If you're feeling extra adventurous with your new Android-based Samsung Galaxy S phone, aka Vibrantor Captivate, watch this video tutorial to learn how to root it in a few quick steps. Rooting your Android phone may give you a few benefits over a regular version, such as easy wi-fi tethering, better keyboard and even multi-touch browsing.

No Wi-Fi? No problem. All you need is a Bluetooth-enabled phone and laptop to surf the Web from anywhere.

This is a video tutorial on how to set up a very simple foil parabola to increase your wireless signal at your home.

Kitchen utensils and computers, that's right! This video will show you how to increase your computer's wireless connection using a strainer!

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

MacOS isn't known as an ideal operating system for hacking without customization, but it includes native tools that allow easy control of the Wi-Fi radio for packet sniffing. Changing channels, scanning for access points, and even capturing packets all can be done from the command line. We'll use aliasing to set some simple commands for easy native packet capture on a macOS system.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

This video will show you in eight steps how you can get and use wifi and dsi to use with your Nintendo. This is a helpful tool because it can be a little confusing to get started using different technologies without clear instructions.

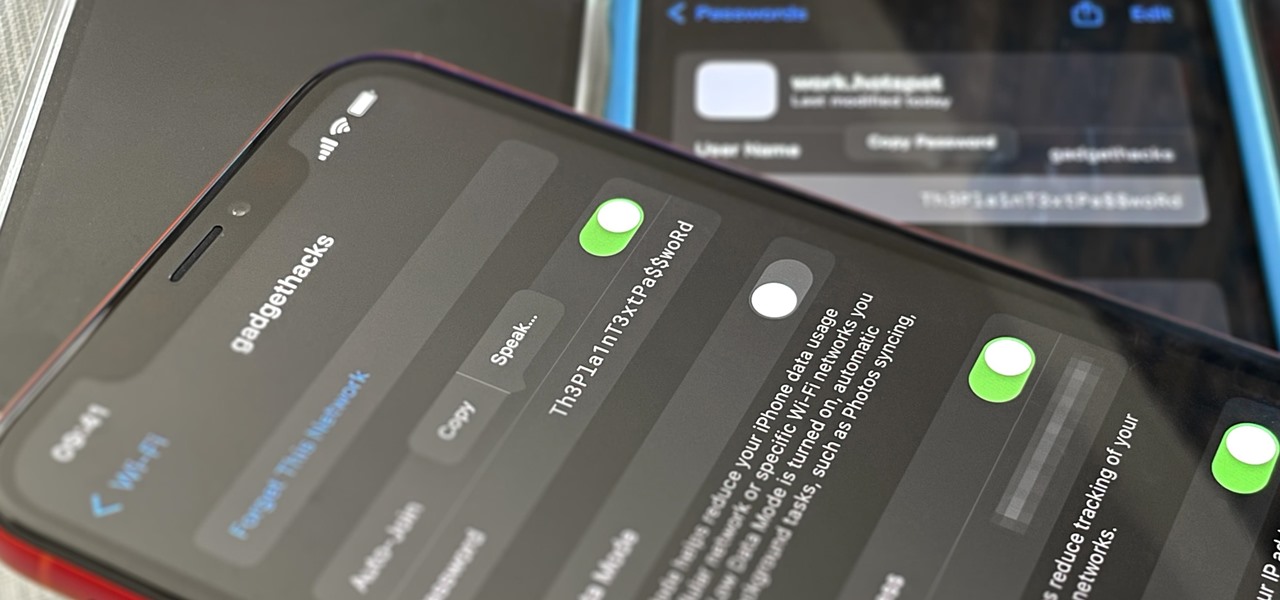
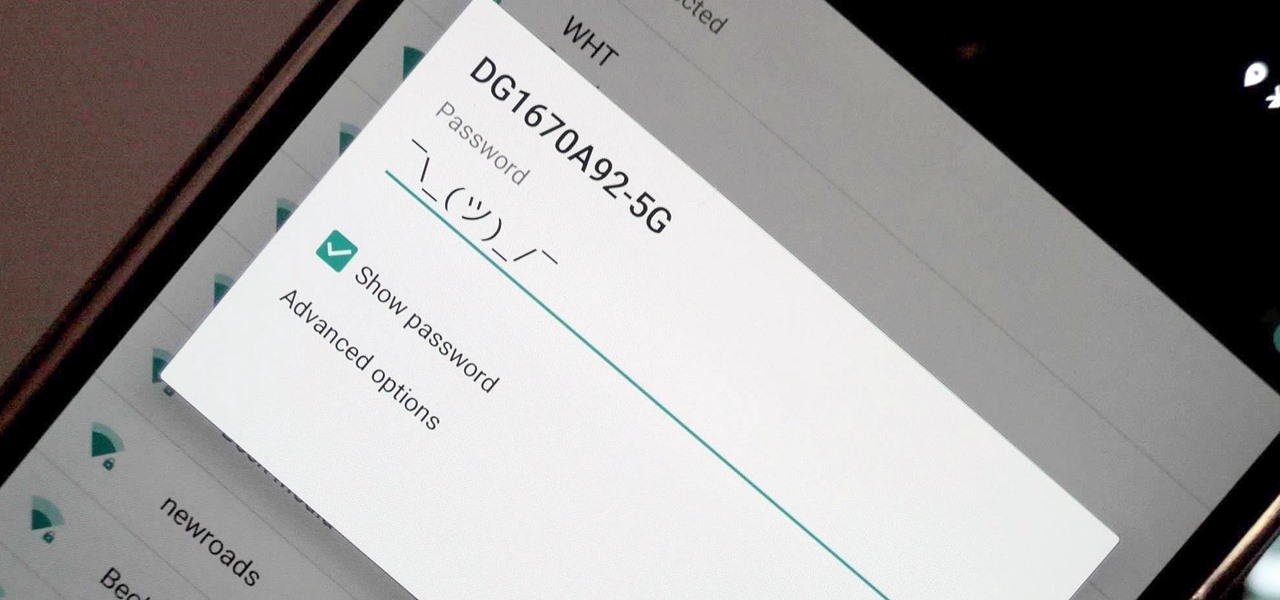
Your iPhone goes with you pretty much everywhere you go, and unless you have unlimited data on your cellular plan, you've probably connected to dozens of Wi-Fi hotspots over the years. Wi-Fi passwords are saved to your iPhone so you can auto-connect to the router or personal hotspot again, but finding the plain text password for a network hasn't always been easy.

Ever found yourself not able to connect to a Wi-Fi network on your Android device that you know damn well was there? The worst part is that you know it's your device, because you can see everyone else around you on that network! WHAT GIVES?!? Well, maybe it has something to do with your phone’s Wi-Fi country code!

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Some of us woke up at the KRACK of dawn to begin reading about the latest serious vulnerability that impacts the vast majority of users on Wi-Fi. If you weren't one of those early readers, I'm talking about the Key Reinstallation Attack, which affects nearly all Wi-Fi devices.

Researchers at MIT's Computer Science and Artificial Intelligence Laboratory have created Wi-Fi technology that identifies where you are, which may eliminate the need for passwords.
I've recently been on holiday in Europe, staying in a hotel that was part of a big chain that included many in the local area. A quick review of the wi-fi within range of my room showed that there was another in the chain that was in range of my Yagi Turbotenna, which naturally got me thinking. If I wanted an anonymous internet connection, this could be quite handy.

Windows 10 is the most cloud-oriented version of Windows to date—yet, while this means you get some nifty new features, it also means some of your personal data is being shared with Microsoft's servers.

Before you head to class, work, or sleep, you're probably doing the same thing over and over again—toggling off system settings like Wi-Fi, sound, data, or brightness, depending on the circumstances. Schedules and routines can help increase efficiency, so while you abide to a particular schedule, so should your Android.

Samsung is helping photographers in getting more utility out of their cameras with their new Samsung Smart Camera App. With it, your device becomes a powerful viewfinder for your Samsung camera, allowing you to not only frame shots, but control multiple aspects of the camera, right through your phone.

If you lend someone your phone, even if it's just for a second, there's a chance they can enter an app and see something you'd rather they didn't. Whether it's a personal email or a private photo, there are plenty of reasons why you'd want to keep snoops out of certain apps.

Whether it's because you have nosy family and friends or you're just cautious about losing your device, having a passcode on your Android smartphone is essential for protection. However, you don't always need or want a passcode, especially when you're home alone or in your car on the way to work.

As the protectors of all things good, the Federal Communications Commission is usually busy behind the scenes pissing off Slim Shady, giving out fines for indecent nipple exposure at certain halftime events, and warning the NSA about losing any "confidential" phone information they steal from us.

Welcome back, my greenhorn hackers. When Wi-Fi was first developed in the late 1990s, Wired Equivalent Privacy was created to give wireless communications confidentiality. WEP, as it became known, proved terribly flawed and easily cracked. You can read more about that in my beginner's guide to hacking Wi-Fi.

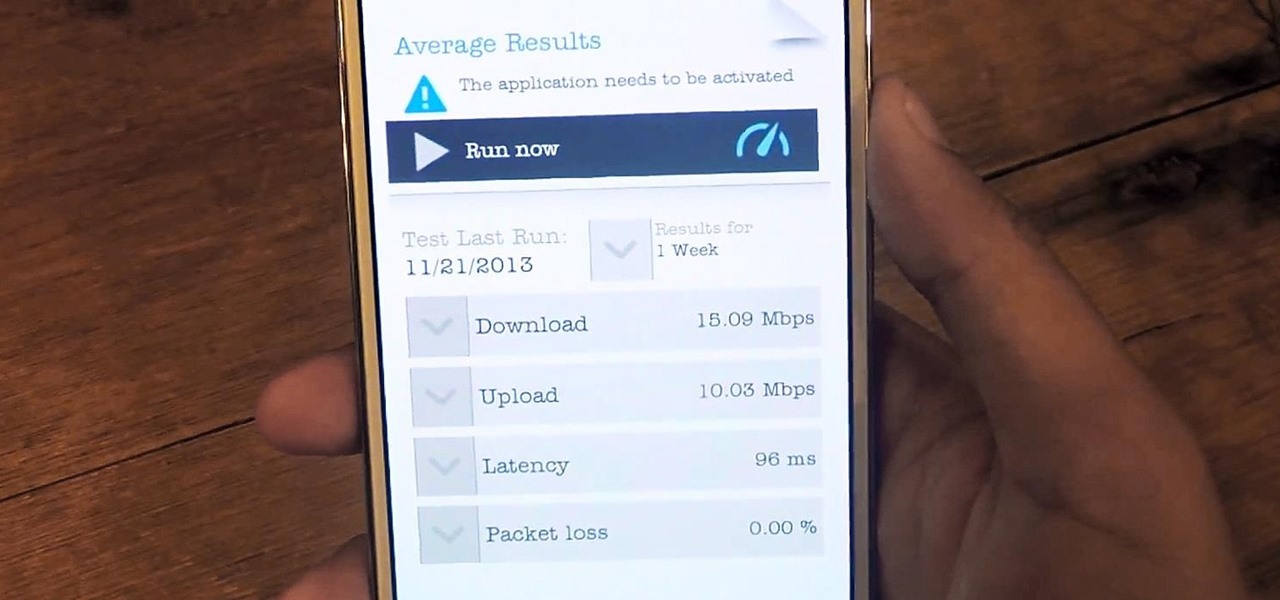
Whether you're pressed against your bedroom window, hidden deep inside your linen closet, or lounging on the rooftop, finding that area of maximum Internet speed around your house is usually just trial and error. And when you finally find the sweet spot, apps like Speedtest.net can help you determine how fast your Wi-Fi or cellular connection is overall on your computer or smartphone, so you know your full capabilities. But, if you want to know exactly how fast your Samsung Galaxy Note 2 is u...

Android has released a new application called ezNetScan, which is a free app that scans the wireless network you're connected to and gives you a full log of all of the devices connected to that network. This isn't new for smartphone users, let alone Android users. Fing has been around for a while and does practically the same thing that exNetScan does. It gathers information such as the IP and MAC addresses, device vendors, and ISP location. But while Fing is a great program, it does lack a f...

Want to take advantage of your neighbor's super fast Wi-Fi connection? If they're smart, they probably have it password protected (otherwise you wouldn't be reading this, would you?). But if you have an Android phone, you can get back at them for always parking in your spot and slamming the door when they get home at 2 a.m.—by stealing...er, borrowing, their connection.

If you don't want to go through the hassle of setting up a formal network between two Macs, but still want to transfer files between the two, take a look at Airdrop. Airdrop is a built-in utility found in Mac OS X Lion (10.7) that will allow you to easily drag and drop files to another computer belonging to you or a friend.

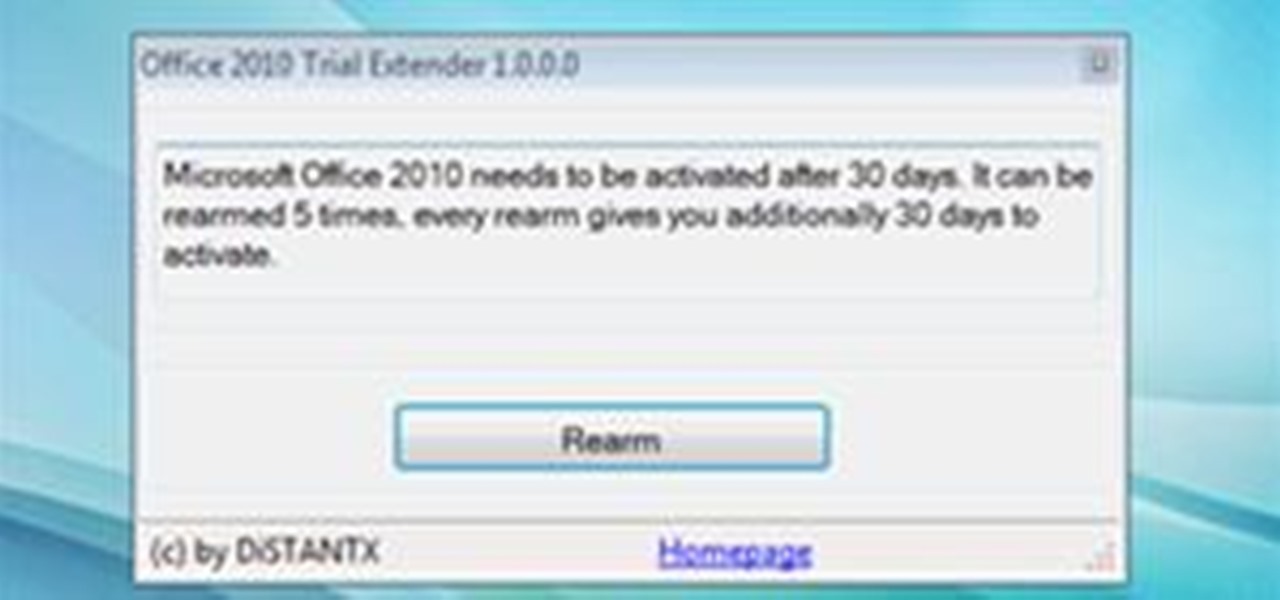
via LifeHacker Windows: If you want to squeeze all the use out of Office 2010 before you're required to pony up for a license, free utility Trial Extender will extend the free trial period up to 6 months, no command-line work required.

With the Wigle WiFi app running on an Android phone, a hacker can discover and map any nearby network, including those created by printers and other insecure devices. The default tools to analyze the resulting data can fall short of what a hacker needs, but by importing wardriving data into Jupyter Notebook, we can map all Wi-Fi devices we encounter and slice through the data with ease.