Android devices are known for their USB and Wi-Fi tethering abilities—rooted or unrooted—which comes in handy for those that travel and need internet on their laptops in areas that don't have any Wi-Fi networks available, but have a strong cellular signal.

This video presents how to connect to your iPod Touch or iPhone using SSH (Secure Shell) without using Wi-Fi connection.
A macOS computer can reveal a lot of information about the owner, including which Wi-Fi network they have permission to access. With an Arduino-based attack, we'll use a five-dollar setup to inject a rogue Wi-Fi network and steal the list of trusted Wi-Fi networks, allowing us to see where the computer has been.

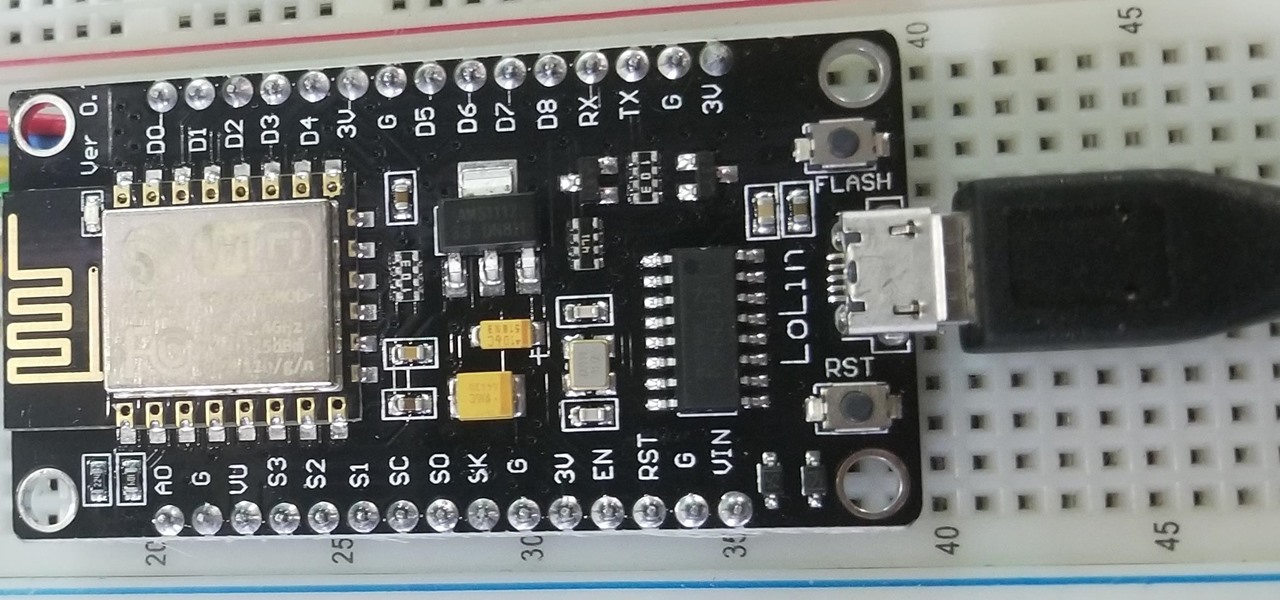
Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

So you want to know what that person who is always on their phone is up to? If you're on the same Wi-Fi network, it's as simple as opening Wireshark and configuring a few settings. We'll use the tool to decrypt WPA2 network traffic so we can spy on which applications a phone is running in real time.

Figuring out the Wi-Fi at a new location is challenging enough. Connecting to said Wi-Fi should be as easy as possible. Unless someone you know is already connected on their iPhone, you're probably used to the usual routine of heading to the Wi-Fi page in the Settings app to get yourself online. Luckily, there's now a much better way to do so.

Apps can collect a lot of data. Even if they don't have permission to access your GPS or camera, they can still read other sensors and learn a lot more than you'd think. Your gyroscope could be used as a keylogger. The light sensor could read your visited links. But if you're on Android 10, you don't need to worry about this.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

When you don't have a steady cellular signal or immediate Wi-Fi access but need to communicate with others around you, you can set up an off-the-grid voice communications network using a Raspberry Pi and an Android app.

While having no internet connection is definitely a bad thing when you need it, you can at least bide your time until you're back online with a hidden Easter egg inside of the Google Chrome browser. This gem unlocks a secret side-scrolling game that can keep you busy during your downtime.

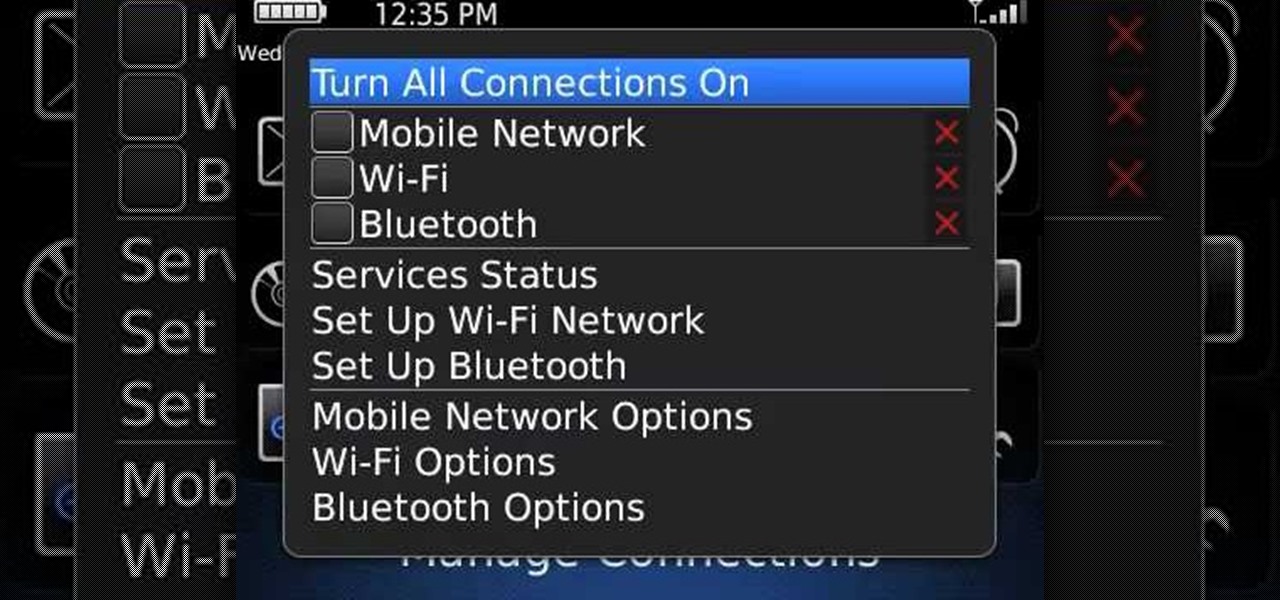
Learn how to use the Manage Connections pane to control mobile network, Wi-Fi and Bluetooth connections on your v5 BlackBerry phone. This clip will show you how it's done. Whether you're the proud owner of a BlackBerry smartphone or are merely considering picking one up, you're sure to be well served by this video guide. For detailed information, including step-by-step instructions, take a look.

The most common Wi-Fi jamming attacks leverage deauthentication and disassociation packets to attack networks. This allows a low-cost ESP8266-based device programmed in Arduino to detect and classify Wi-Fi denial-of-service attacks by lighting a different color LED for each type of packet. The pattern of these colors can also allow us to fingerprint the tool being used to attack the network.

I spend a lot of time helping friends and family with their tech problems, like clearing a browser's cache, scanning a Windows computer for malware, and speeding up a Mac. However, the issue I deal with most frequently revolves around forgotten network passwords.

It's hard enough to keep tabs on the battery life of one device, let alone all of the different gadgets that a typical consumer owns in this day and age. Say your smartphone is running low on juice, so you switch to your tablet only to find out that it's almost dead as well. Better hope your laptop is fully charged, right?

One of the first things most people ask for when staying with a friend is the password to the Wi-Fi network. Even if you trust your friends to the end of the earth, a super secure password can be a pain to share with them, especially if it's just a bunch of random characters.

If the Nexus 7 wasn't your first Android tablet, you may have noticed something different with the user interface when compared to other Jelly Bean tablets. You may not know exactly what it is off the top of your head, but it's there.

Whether it's using precious data or wasting battery power, switching between Wi-Fi and cellular service on your Android device can be a hassle. If your Wi-Fi is off, you may not know about free hotspot networks in the area you're in, leading you to waste network data (which more than likely is not unlimited). If your Wi-Fi is on all of the time, this leads to quicker battery depletion. There are already a few Android apps, like Auto WiFi Toggler, that combat this problem, but they just period...

Pokemon's Darkrai is one of the most coveted levels of the game. With this tutorial, learn how to find Darkrai in a few easy steps, as well as secure a Membership Pass and a Mystery Gift in Pokemon Platinum. So grab your Nintendo DS and follow along!

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

There's a 2800mAh battery powering the Samsung Galaxy S5, but even it's no match for the constant day-to-day torture you put it through. Taking photos, watching videos, and playing games can make your fully charged S5 powerless in no time.

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

Cracking the password for WPA2 networks has been roughly the same for many years, but a newer attack requires less interaction and info than previous techniques and has the added advantage of being able to target access points with no one connected. The latest attack against the PMKID uses Hashcat to crack WPA passwords and allows hackers to find networks with weak passwords more easily.

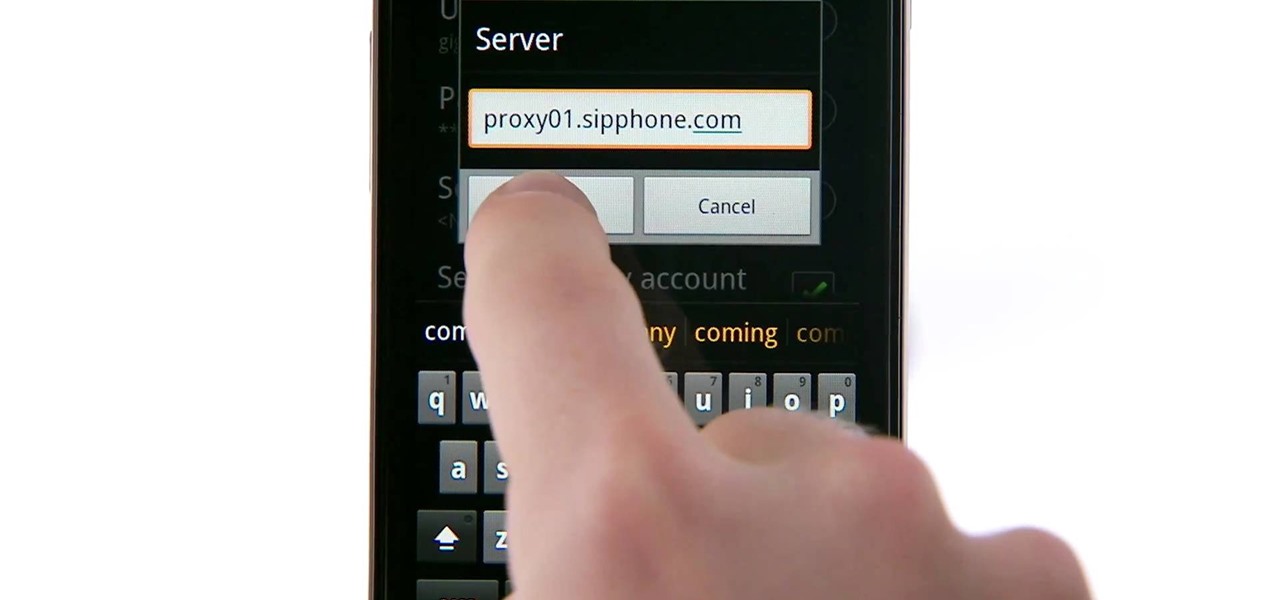
If you've got Android 2.3 Gingerbread running on your Google Nexus S smartphone, try out this cool feature. Set up a SIP (Session Initiation Protocol) account, and you'll be able to make Internet calls over Wi-Fi. You'll be able to talk to anyone with VoIP.

Tethering lets you share your Desire HD's 3G Internet connection with a second, Wi-Fi enabled device. Learn how to use it with this quick, official guide from HTC.

This video tutorial presents instructions on hacking a weak Wi-Fi Protected Access, or WPA, wireless network. To follow along, and replicate this hack yourself, you'll need knowledge of the deauthentication, or DeAuth, process. For more information, and to get started hacking WPA networks for yourself, watch this hacking how-to.

In this tutorial, we learn how to set up a Wi-Fi network with a Linksys router. First, go to your cable modem and remove the yellow Ethernet cable. After this, plug the Ethernet cable into the very first port of the router and plug the other end into your computer. After this, connect any other electronics you have with cables, then plug the router into the wall to give it power. Next, turn the power to the modem and router back on. When finished, you should see a new Wi-Fi network appear in ...

This tutorial gives a start to finish explanation of how to make an Internet Wi-Fi router with Windows Vista. With real time computer screen video and narrative, it is easy to follow along at home.

An internet connection has become a basic necessity in our modern lives. Wireless hotspots (commonly known as Wi-Fi) can be found everywhere!

In 2019, the Raspberry Pi 4 was released with specs including either 1 GB, 2 GB, or 4 GB of memory, a Broadcom BCM2711B0 quad-core A72 SoC, a USB Type-C power supply, and dual Micro-HDMI outputs. Performance and hardware changes aside, the Pi 4 Model B runs Kali Linux just as well, if not better, than its predecessors. It also includes support for Wi-Fi hacking on its internal wireless card.

In this video tutorial, viewers learn how to disable their Wi-Fi SSID broadcast on a Linksys's router. Begin by opening your web browser and type in this address: Press Enter to access the page. Then type in your user name and password. Click OK. Now click on the Wireless tab and check Disable under "Wireless SSID Broadcast". Finish by clicking on Save Changes. This video will benefit hose viewers who use a Linksys's router, and would like to learn how disable their broa...

How to disable Wi-Fi SSID broadcast on an Apple AirPort in seven simple steps. Open your AirPort Admin Utility application. Find your network's name and double-click it or press the Configure button on the bottom right of the screen. Enter your password and click OK. The Configure "Apple AirPort Express" Base Station should open. Click on AirPort tab. Select the "Create a closed network" check box. Click OK on the dialogue box. Click the Update button on the lower right part of your screen. D...

Does your network begin to crawl right around the time your sinister-looking next-door neighbors get home from work? Do you harbor suspicions that one or more of them may be stealing your Wi-Fi? It's easy to find out. And equally easy to give freeloaders the boot. In the guide below, we'll show you how to secure your wireless connection in three easy steps.

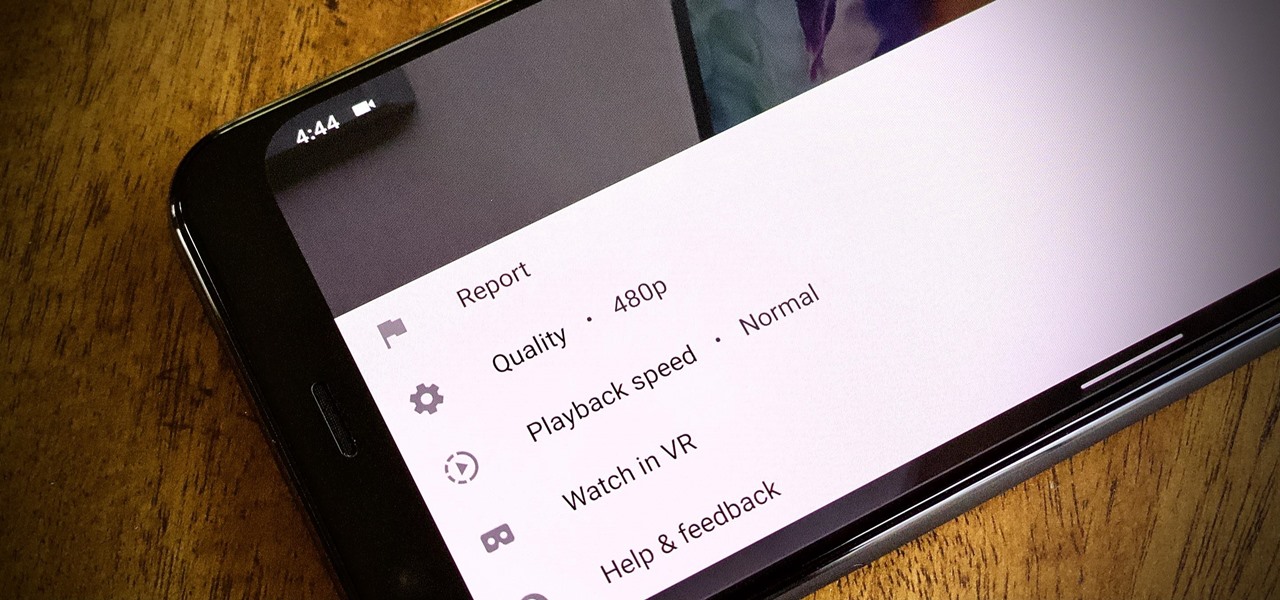
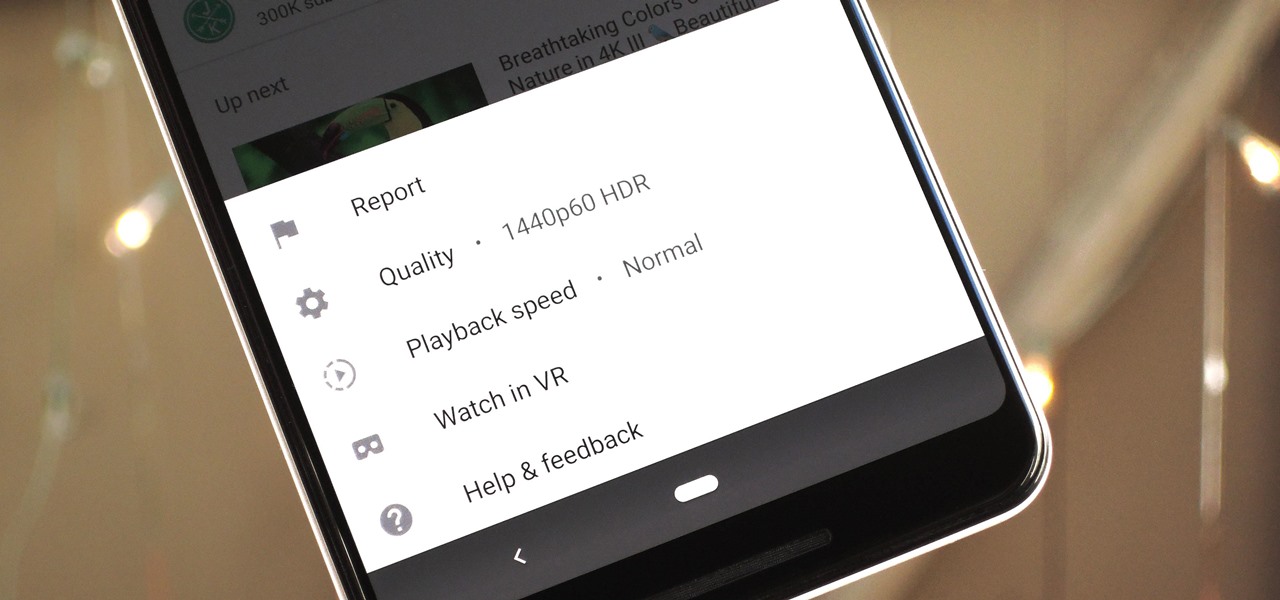
To reduce stress on internet bandwidth during the COVID-19 pandemic that the novel coronavirus is causing, Google decided to set YouTube's default video quality to 480p. That said, even when you could stream at HD quality without adjusting anything, you still couldn't switch the default to whatever you liked. We have a few methods on hand to help you change that.

The YouTube app will default to 480p playback when you first open a video. It's supposed to switch to your screen resolution a few seconds in, but this isn't always the case. The regular YouTube app doesn't let you change this behavior, but like most things with Android, there is still a way.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

Google's new Pixel and Pixel XL flagships are some very powerful smartphones, but as with any high-tech gadget, they're only as capable as the user allows them to be. So if you're a proud new Pixel owner, it's time to bone up on a few new features to help get the most out of your device.

The introduction of smartphones has been what some may see as a step backwards in technology regarding batteries. The first cell phone that I had would last 3-4 days on a single charge; however, the lack of functions minimized the use that is saw.

There are many different applications and games on the Nintendo 3DS that can take advantage of an active internet connection over Wi-Fi such as Netflix or the eStore. Unfortunately, since the 3DS is a mobile device, you won't always have access to the internet. If you have a mobile hotspot on a smartphone or tablet, you can share the internet connection over wireless with the gaming handheld.