Your Apple Watch only looks as good as the band that it's bound to, but if you're looking to purchase one directly from Apple, expect to spend anywhere from $149 (for the Milanese Loop) to $449 (for the Link Bracelet).
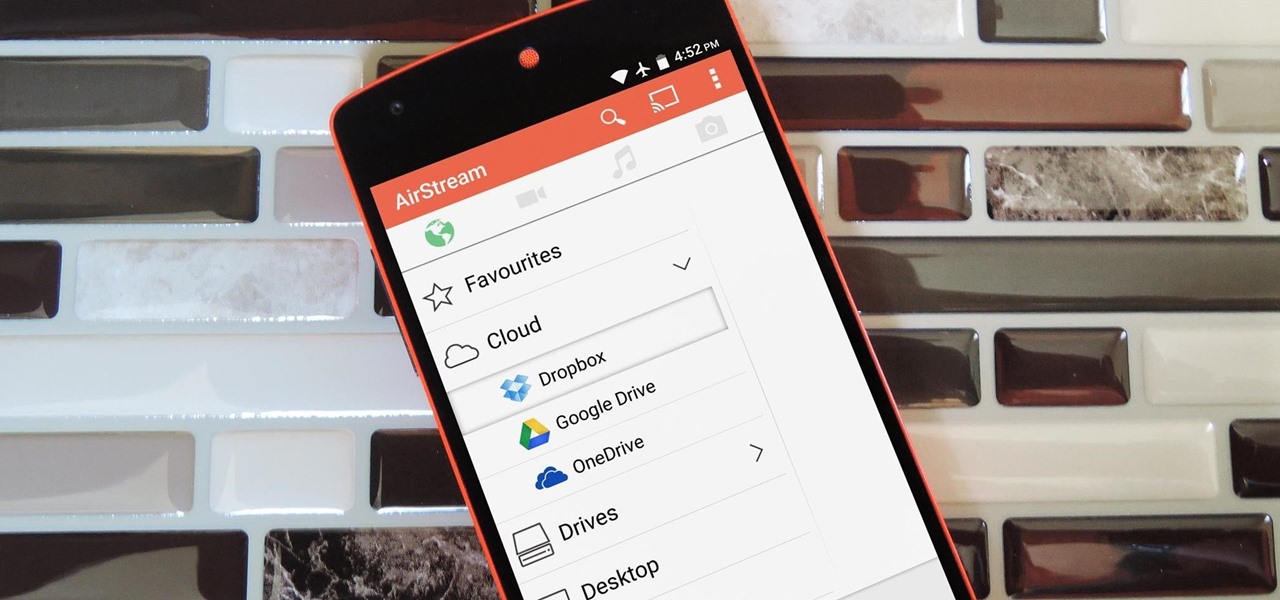
Smartphones generally have limited storage, but counter this issue with an always-on internet connection. This led to the proliferation of cloud storage services, which allow us to store and access our large media libraries remotely.

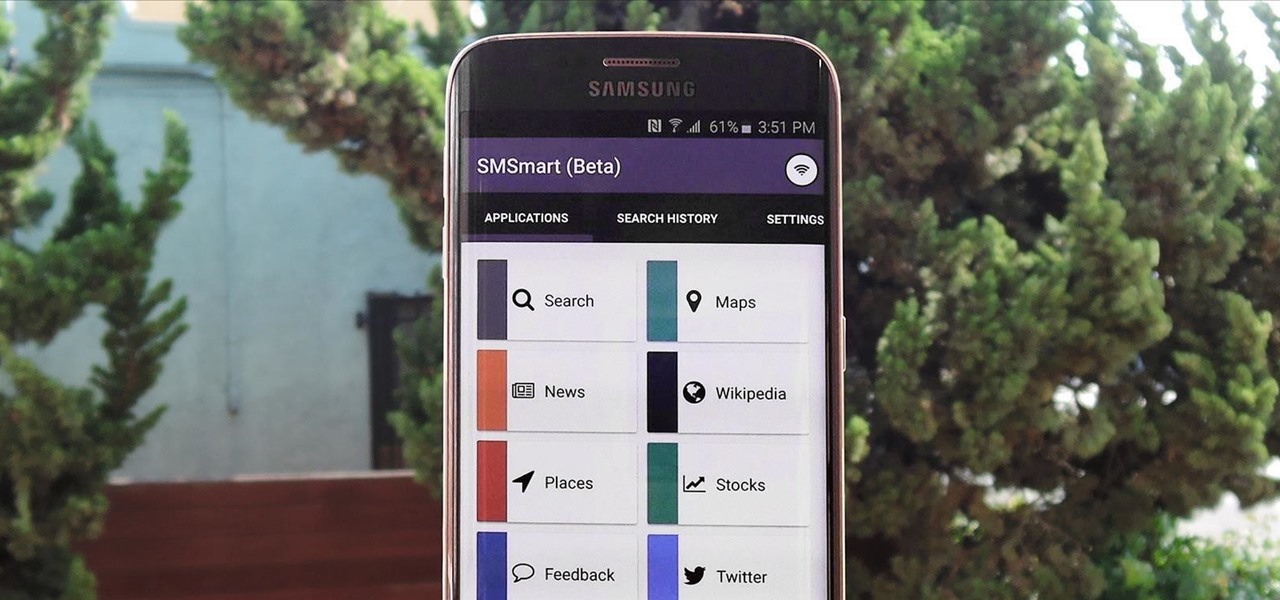
Depending on how many Watch-compatible apps you have, the Home screen on your Apple Watch is either insanely clean or absurdly messy. When I first synced my Watch with my iPhone, I was attacked with a huge honeycomb of apps, strewn across my Home screen in no particular order.

It probably doesn't happen much, but occasionally you'll run into a frozen or bugged-out app on your iPhone or other iOS device. That's where force-closing comes in, allowing you to close any app manually through a few clicks and swipes.

There's a built-in timer feature on the iPhone's Camera app that helps you set up your device, step back, and take a photo before time runs out. This feature is useful when there isn't another person around to take a photo of you, or when you don't want to be missing from a memorable group picture. Unfortunately, timers don't always work well. With a timer, no one can sit behind your iPhone to see if the picture is perfectly focused and framed, but that's where your Apple Watch comes in.

The buttons on most Android devices are laid out (from left to right) in a Back, Home, Recent Apps format. Samsung is the lone exception to this rule, which flip-flops them, so this can make for an inconsistent experience if you own multiple Android devices.

Recently, a group of Duke University students got together to tackle an age-old problem with mobile devices. You see, mobile data coverage isn't exactly ubiquitous, and many folks have restrictive mobile data plans, which means internet connectivity is not always an option.

For some strange reason, not all variants of the Samsung Galaxy S6 and S6 Edge have a menu option for changing the backlight timeout for their capacitive keys. According to user reports, only the AT&T variant of these phones has such an option.

Smartphones are great at keeping us busy with games, social media, and messaging apps, but there has been a recent push for them to also help keep us safe (and I'm not talking about from hackers, though that is equally important).

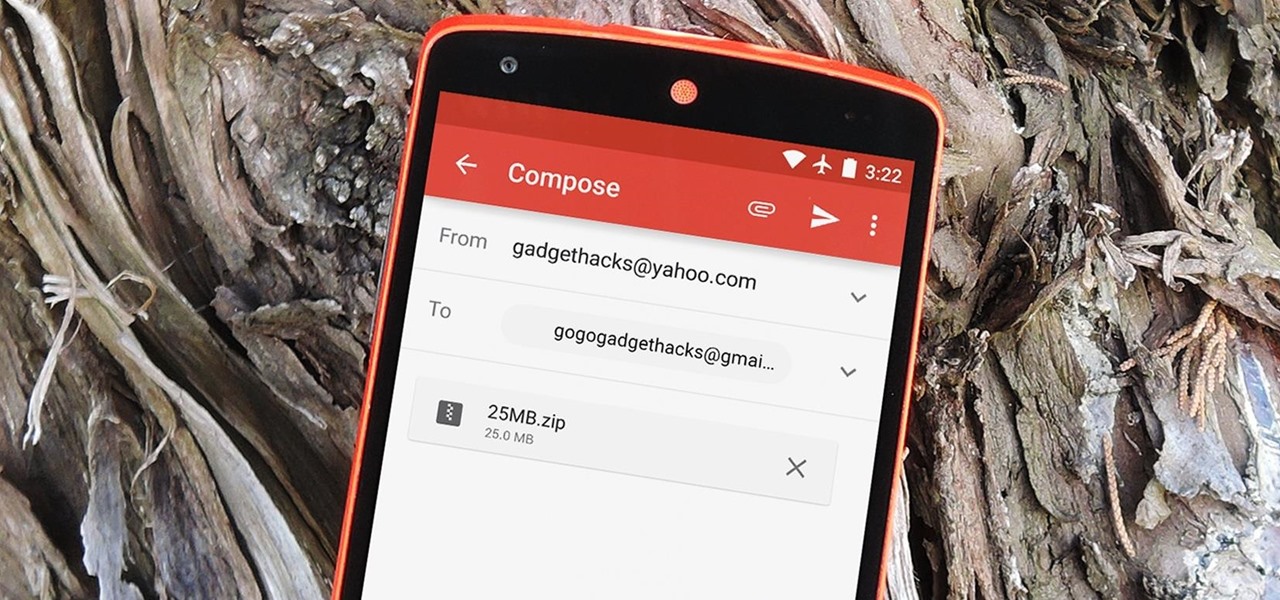
The Gmail app recently became stock Android's central hub for all of your email accounts. Instead of being limited to just Gmail accounts, the app can now handle POP3, IMAP, and exchange service email accounts, making it a one-stop shop for all of your emailing needs.

Sideloading apps on Android is incredibly easy—you just have to enable "Unknown sources" in your device's Security settings, then you're free to run an APK installer file to get the app installed.

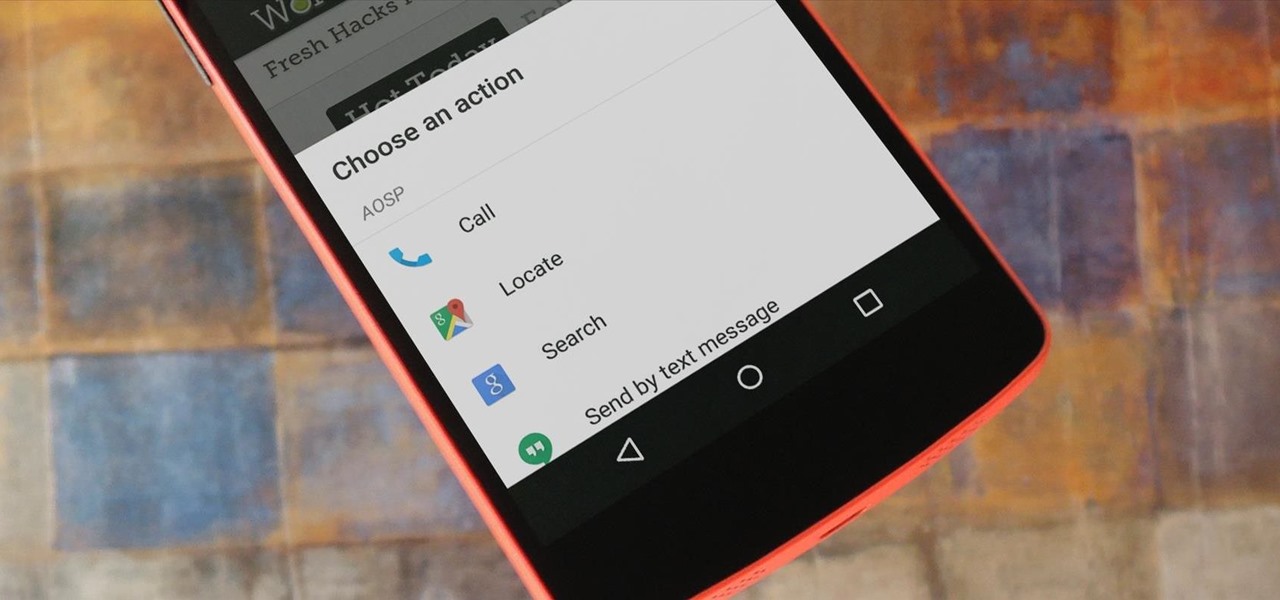
For the most part, when you're copying text on your Android device, it's because you intend on pasting it into a different app than the one you're currently using. For instance, you might be looking at a posting on Craigslist. So you copy the seller's phone number, then head to your home screen, switch over to your phone app, paste it into your dialer, and finally make the call.

One of the many additions that appear on Android 5.0 Lollipop is a handy menu that lets users correct for or simulate different types of color blindness. While Google didn't flip the switch on this new feature until Lollipop was released, it turns out they had been working on it for quite some time.

I always over-order when I call in for pizza delivery, because I love having leftover pizza. Because there's so much flavor packed into the sauce, cheese, and whatever toppings you've ordered, pizza adds flavor to salads, cocktails, and can even act as the base to a quiche. Press it into a waffle iron to make a pizza panini, cut it into triangles and make the best Bloody Mary ever, or use it as the base for a lively quiche.

Whether you live in foggy California or icy Massachusetts, you've more than likely struggled with a cloudy, vision-impairing window that makes even the shortest commute impossible.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

Are you stranded in a hotel room with no kitchen, but craving the comfort of a home-cooked meal? Fear not, I have found some interesting ways to cook food without the luxury of an oven, stove, microwave, or even a toaster!—also known as "hotel room cooking."

Welcome back, my tenderfoot hackers! Those of you who have been reading my posts here for awhile know how much I emphasize good reconnaissance. Novice hackers often jump into a hack/exploit without doing proper recon and either fail or get caught. Experienced and expert hackers know that 70-80 percent of a good and successful hack is dependent upon successful and accurate reconnaissance.

Welcome back, my greenhorn hackers! In previous Wi-Fi hacking tutorials, I have shown you ways to create an Evil Twin, to DoS a wireless AP, and to crack WEP and WPA2 passwords, but in this tutorial, I will show you something a little bit different.

Welcome back, my novice hackers! New hackers often ask me the same question: "What is the easiest platform to hack?" My response is always the same—it is not a platform, but rather a particular piece of software that is easiest to hack, which is on nearly every client-side system. That software is Adobe Flash Player.

Despite what some in the tech-world would like you to believe, iOS isn't totally locked down, free from user customization. Take your home screen, for example. Not only can you change your app icons and move them wherever you'd like, you can actually choose to hide them all. If you have a wallpaper that's just begging to be shown off, this trick is for you.

With a 13 megapixel camera that can record in full 4K, there's a lot to love about the Samsung Galaxy Note 3 from a photographer's perspective. The image quality in my photos and videos are top-notch and nothing to complain about, but as with all things tech, things could always get better.

Welcome back, my neophyte hackers! Many newbie hackers seem to be confused regarding the process or methodology to employ a successful hack. Most want to simply go straight to the exploit without doing the due diligence to make certain that the hack will work and you won't get caught.

Welcome back, my greenhorn hackers! Earlier in this series, I showed a you a couple of different ways of fingerprinting webservers. Probably the easiest way, is to use netcat and connect to port 80 and pull the webserver banner.

Welcome back, my greenhorn hackers! After the disaster that was Windows Vista and the limited and reluctant adoption of Windows 8 and 8.1, Windows 7 has become the de facto standard operating system on the desktop/client.

Welcome back, my greenhorn hackers! In a previous tutorial on hacking databases, I showed you how to find online databases and then how to enumerate the databases, tables, and columns. In this guide, we'll now exfiltrate, extract, remove—whatever term you prefer—the data from an online database.

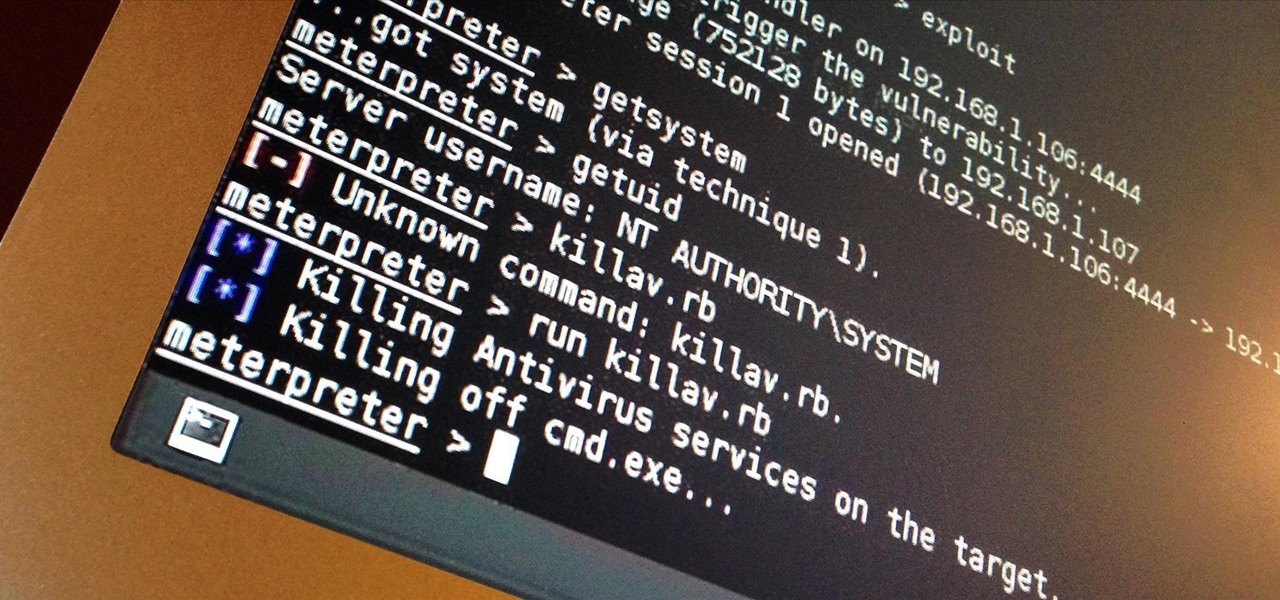
I've done numerous tutorials in Null Byte demonstrating the power of Metasploit's meterpreter. With the meterpreter on the target system, you have nearly total command of the victim.

Welcome back, my fledgling hackers! The database is the hacker's "pot-of-gold," as it contains information that is very valuable to both the business and the hacker. In this, the second of my series on hacking databases, we're on the "hunt" for Microsoft's SQL Server. Although far from the most commonly used database (Oracle hold's that title), Microsoft's SQL Server is very often found in small-to-medium sized businesses. Even a few big businesses use it.

Welcome back, my neophyte hackers! As part of my series on Wi-Fi hacking, I want to next look at denial-of-service (DoS) attacks, and DoSing a wireless access point (AP). There are a variety of ways to do this, but in this tutorial we'll be sending repeated deauthentication frames to the AP with aircrack-ng's aireplay. Remember, hacking wireless networks isn't all just cracking Wi-Fi passwords! Our Problem Scenario

Welcome back, my hacker apprentices! My recent posts here in Null Byte have been very technical in nature, so I thought that I'd have a little fun with this one.

Welcome back my fellow army of hackers! Today we'll be hacking a website. Hacking is technically not the right word used here. It should be defacing! So we are going to deface a website...

Welcome back, my fellow hackerians! Today we'll be hacking Facebook profiles on your local network. You may think, "How is this useful, nobody but me is using my network." Well, you can use this on other Wi-Fi networks that are available for free (like at Starbucks) and crack their precious Facebook profile!

Welcome back, my newbie hackers! We've already saved the world from nuclear annihilation and covered our tracks afterwards, but the world is still threatened by a malicious, megalomaniacal dictator with missiles and nuclear weapons.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

The Samsung Galaxy S III is undoubtedly a great phone, but still has some minor issues to work out.

Still have an old tape deck installed in your car? This nifty hack lets you upgrade to the digital age without sacrificing your love for cassettes. There's nothing wrong with some low-fidelity tunes in your car every now and then, but if you want to listen to the tunes on your iPod or smartphone too, it's a lot easier (and cheaper) than buying a new in-dash player that supports line-in connections. Just add some wireless capabilities to you tape deck! All you need is a cheap cassette adapter,...

What's your Twitter handle worth? If it's considered "desirable" (aka short and simple), it'll get you around 100 bucks, or, if you prefer, the affections of a teenage girl.

When I left off on our last hack, we had hacked into the ubiquitous Windows Server 2003 server by adding ourselves as a user to that system so that we can return undetected at any time. The problem with this approach is that a sysadmin who is on their toes will note that a new user has been added and will begin to take preventative action.

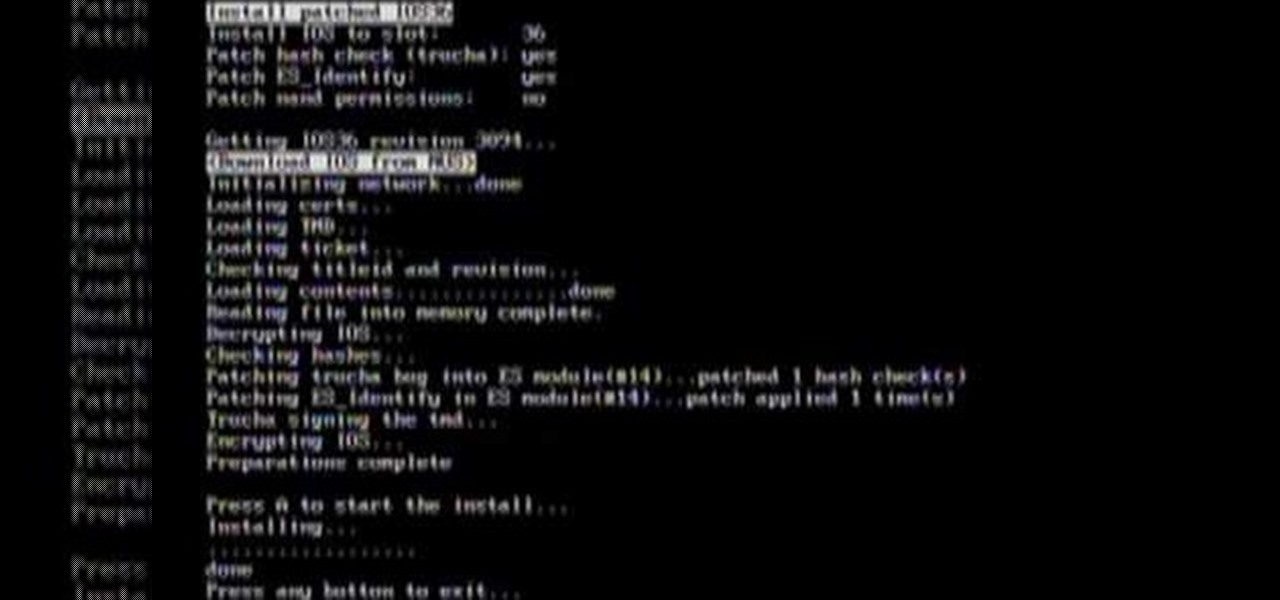
Trucha Bug Restorer is a powerful piece of homebrew software that you can use on your Wii to make sure that it is formatted properly in order to play burned games and use other hacks. This video will show you how to use it to set up an installation of cIOS on your Wii, which is the program that allows you to play burned backup copies of games.