News: The Consequences of Hacking
Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Mostly all hackers like to have a laugh. We like to have fun! We like to troll. And maybe, even cause some havoc once in a while. But, while we do this, we must always stay in the line of the law.

Here are some awesome hacks about storing your lingerie and a tip to keep them fragrant too.

Welcome back, my rookie hackers!

Eggs are a staple food for most Americans, which is no surprise, considering how necessary they are in savory and sweet recipes alike. On their own, they're usually not too eggs-citing. However, these clever egg hacks will make your egg-making easier, more fun, and more interesting.
Salt is one of my favorite ingredients, by far, and also one of the most overlooked foods in the kitchen. This is probably due to the fact that it's an essential component of almost any recipe; because salt is a necessity, it's easy to forget how dynamic and versatile it can be as well.

OR rather How to make the Backdoor Persistent: Hello, my Cold and Merciless Hackers,

Welcome back, my tenderfoot hackers! A short while ago, I started a new series called "How to Spy on Anyone." The idea behind this series is that computer hacking is increasingly being used in espionage and cyber warfare, as well as by private detectives and law enforcement to solve cases. I am trying to demonstrate, in this series, ways that hacking is being used in these professions. For those of you who are training for those careers, I dedicate this series.

There are a few ways to successfully cheat on a test without getting caught, Here's one of them! Like most, office and school supplies will be needed. For this one though all you pretty much need is an eraser. By the time you're done with this hack, you'll be getting straight As for sure.

Welcome back, my hacker novitiates! As you know by now, the Metasploit Framework is one of my favorite hacking tools. It is capable of embedding code into a remote system and controlling it, scanning systems for recon, and fuzzing systems to find buffer overflows. Plus, all of this can be integrated into Rapid7's excellent vulnerability scanner Nexpose.

Holidays are a time for good food and good drink, but more often than not, we substitute good drink for, well, cheap drink. However, cheap wine doesn't have to be bad.

Welcome back, my rookie hackers! I recently began a series on using Metasploit, and my goal with it is to teach you the very basics the incredibly powerful hacking tool has to offer while progressively moving on to the more advanced features.

Impress your friends with this simple yet great way to serve a watermelon. Perfect for parties. You'll never create triangle-shaped slices of watermelon ever again with this hack. You only need a watermelon (could also work with other melons), a sharp knife, a cutting board, and some friends!

Welcome back, my tenderfoot hackers! I have written many tutorials on hacking using Metasploit, including leaving no evidence behind and exploring the inner architecture. Also, there are my Metasploit cheat sheets for commands and hacking scripts.

Welcome back, my hacker novitiates! Recently, I demonstrated a hack where you could redirect traffic intended for one site, such as bankofamerica.com, to your fake website. Of course, to really make this work, you would need to make a replica of the site you were spoofing, or better yet, you could simply simply make a copy of the original site and host it on your own server!

Welcome back, my budding hackers! In my continuing effort to build your basic Linux skills for hacking, I want to show you how to build a secure "tunnel" to MySQL.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

Welcome back, my neophyte hackers! There are innumerable ways to hack a system. We must not overlook any of the possibilities if we want to "own" the system. As systems become more and more secure, we need to be vigilant in our search for weaknesses. In this hack, we'll look at abusing the trust that a user innately has for software updates to install our own listener/rootkit on their system.

Sugru is some pretty versatile stuff. The company's slogan is "Hack things better," and for good reason. It sticks to aluminum, steel, ceramics, glass and plastics, it's waterproof and heat-resistant, and it can be molded into any shape you can imagine. Anything from your kitchen cabinets to your bicycle can be improved with some Sugru and a little creativity, and gadgets are no exception. Here are 10 of the coolest hacks to fix or upgrade your smartphone, tablet, or camera.

Welcome back, my hacker apprentices! Although there is a multitude of different hacker types, the one target they all share is the database. I often refer to the database as the hacker's Holy Grail, or the ultimate prize for an effective hack.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

Here's a list of the lifehacks shown in this video: Banana Foil

Welcome back, my hacker trainees! A number of you have written me regarding which operating system is best for hacking. I'll start by saying that nearly every professional and expert hacker uses Linux or Unix. Although some hacks can be done with Windows and Mac OS, nearly all of the hacking tools are developed specifically for Linux. There are some exceptions, though, including software like Cain and Abel, Havij, Zenmap, and Metasploit that are developed or ported for Windows.

Do you ever wonder how all these celebrities continue to have their private photos spread all over the internet? While celebrities' phones and computers are forever vulnerable to attacks, the common folk must also be wary. No matter how careful you think you were went you sent those "candid" photos to your ex, with a little effort and access to public information, your pictures can be snagged, too. Here's how.

Want to learn how to build a robot out of Snap Circuits? I'll show you how to combine Snap Circuits parts from three different sets (the Snap Circuits rover, Snap Circuits Micro, and the Snap Circuits motion detector) to make a simple programmable motion activated robot. For a complete step-by-step build of the robot, visit my project at Instructables: http://www.instructables.com/id/Hack-the-Snap-Circuits-Rover/

Welcome back, hacker novitiates! In the next few hacks, we will be breaking into Windows servers. In this installment, we will learn to add ourselves as a user to a Windows 2003 server. Of course, when we have added ourselves as a user, we can come back any time and simply log into our account without having to hack into the system and risk detection.

This guide goes over the basics of 3D video recording and the mechanics behind it before delving into something a little more specific. The host discusses how to build a rig that allows for adjustments to be easily made to the interaxial distance and convergence of the two cameras.

If you've got an Nintendo DSi, you already know you can do a ton of fun things. But, did you know you can also watch DVDs on your hand held player? That's right, and this video will show you how to do it. In addition, this hack also lets you do it without using Adobe's Showckwave player.You'll want to watch this vid on high resolution and at full screen so you can see all the steps to convert movies on your Nintendo DSi.

GTA 4 is a sweet game, and now you can get into the guts of it and create some sweet mods for yourself. Cars, weapons, perspectives, and many, many, many more mods can be created. Follow the steps and open the doors to new cools things with this great game on Sony PS3.

Grand Theft Auto: The Ballad of Gay Tony might not be new anymore, but it still rocks and there aren't a lot of videos on how to mod it properly. This is one such video. It will teach you everything you need to know to modify the game for a flashed or hotswap-capable Xbox 360. Try this out and learn how to hack GTA 4 ps3.
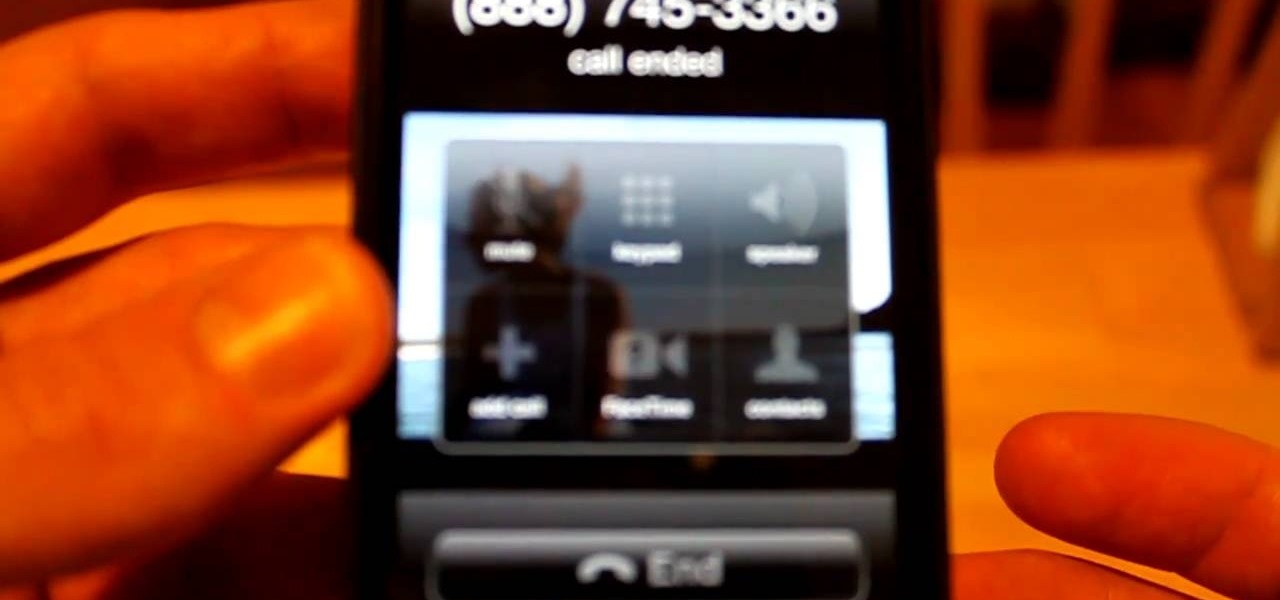
Want to make a phone call on an iPhone 4 running Apple's iOS 4.1, but don't know its passcode? Not a problem. In this clip, we learn a simple trick that will allow you to bypass the lock screen entirely and permit you to view the phone's contact list and place phone calls to any number you like. This glitch has been fixed with iOS 4.2, so treasure this hack while it still lasts! This will let you unlock someones password on an ipod or iphone touch.
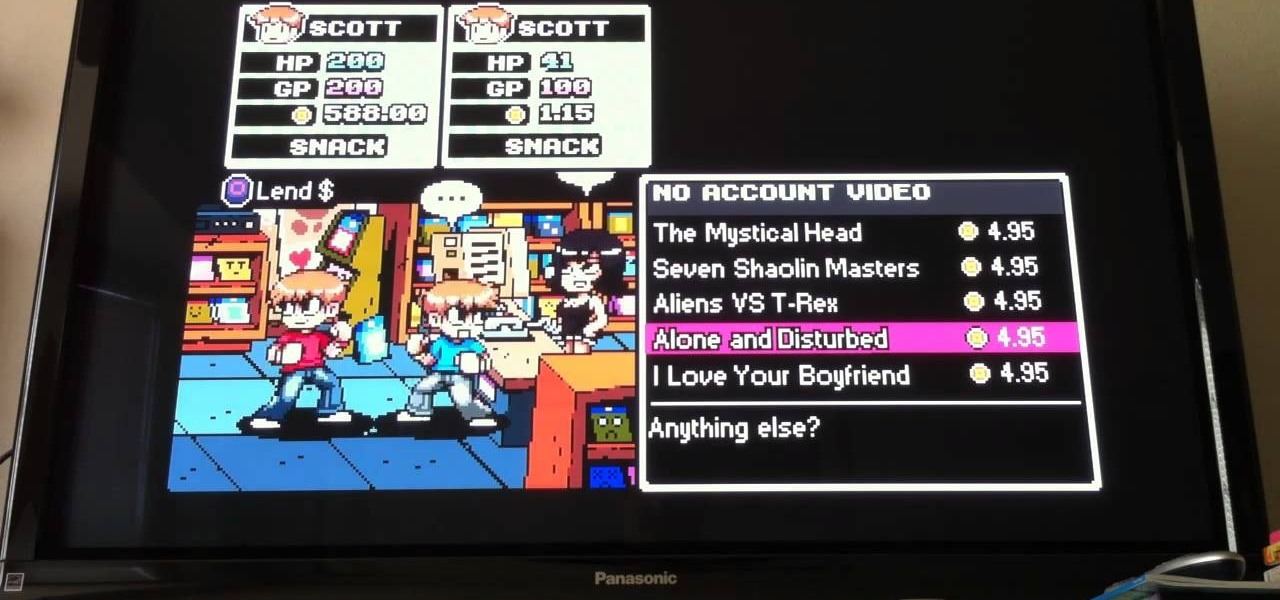
Scott Pilgrim vs. The World: The Game is surprisingly hard for either Xbox 360 or Playstation 3. If you have the PS3 version, this video will show you a great trick for leveling up and getting nearly infinite money quickly.

This is actually quite amazing. If you own an HTC DROID ERIS cell phone, then that cardboard container it came in can be turned into that tiny, but terrific Google Android Bot. The Android Bot logo is known across the world now, and it's odd that their box can be broken down perfectly to recreate it. Was this on purpose, or accident? Anyway, Nextraker found the secret, and he's going to show you how it's down. With just a few basic cuts, you too can have your own little green Bot.
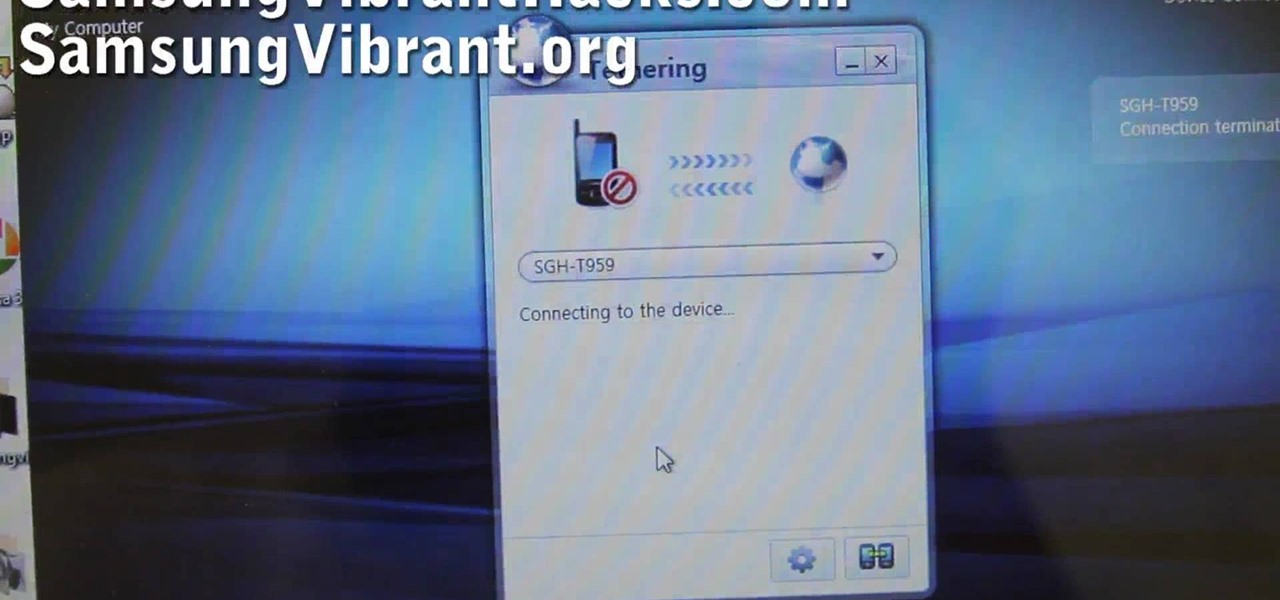
Looking for instructions on how to do USB tethering with a Samsung Vibrant smartphone? You're in luck. This free video tutorial will see that you need everything you need to know. (Note, however, that this hack will require you to download the free Samsung Kies application.) For more information, including detailed, step-by-step instructions, and to get started using USB tethering on your own Galaxy S phone without rooting it, watch this guide.
It's official! You can jailbreak whatever devices you want without fearing reprisal from the federal government! WIN! If you were worried about the legal implications before, worry no longer, and start taking advantage of your devices! This video will show you how to hack an iPhone 3GS, 3G, or 2G or iPod Touch 2G / 1G using a program called redsn0w. It's quick, easy, and will allow you to do so much more with your device there's really no excuse not to do it.

If you still own and use an original XBox console, good for you! You've got a little piece of history right there that most people just tossed or sold to a game store for $10. This video will show you how to replace the paltry 8gb hard drive that the console came with with a big honking 120gb drive. This will allow you to store more data, and since hacking the original XBox is the best reason to keep it around at this point, you should probably make sure that you can do that.
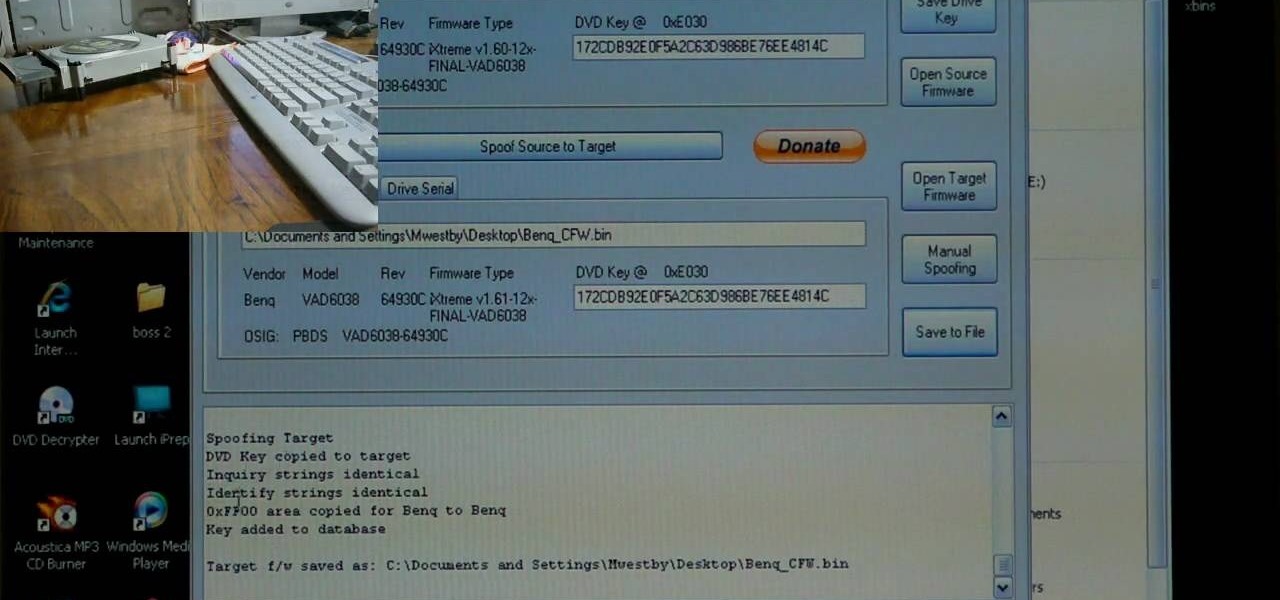
If you've already flashed your XBox 360's disc drive, then congratulations, you've accomplished the most challenging step involved in hacking you XBox. You aren't done though. As Microsoft keeps updating it's firmware to try and fend off hackers, you must keep updating your custom firmware to thwart their efforts. This video will show you how to upgrade your flashed BenQ XBox 360 disc drive's firmware to IXtreme 1.61 using Jungle Flasher 1.61. NOw you can play your burned games with a greater...

Flashing the disc drive on the XBox 360 is the first step of truly hacking your XBox 360, enabling it to run whatever discs you like but also putting you at risk for being banned from XBox Live. Microsoft has used several different kinds of drives in the console over the course of its lifespan, so you have to check what type of drive you have before you attempt to flash it. This two-part video will show you how to flash the Hitachi 78FK drive used in many XBox 360's.
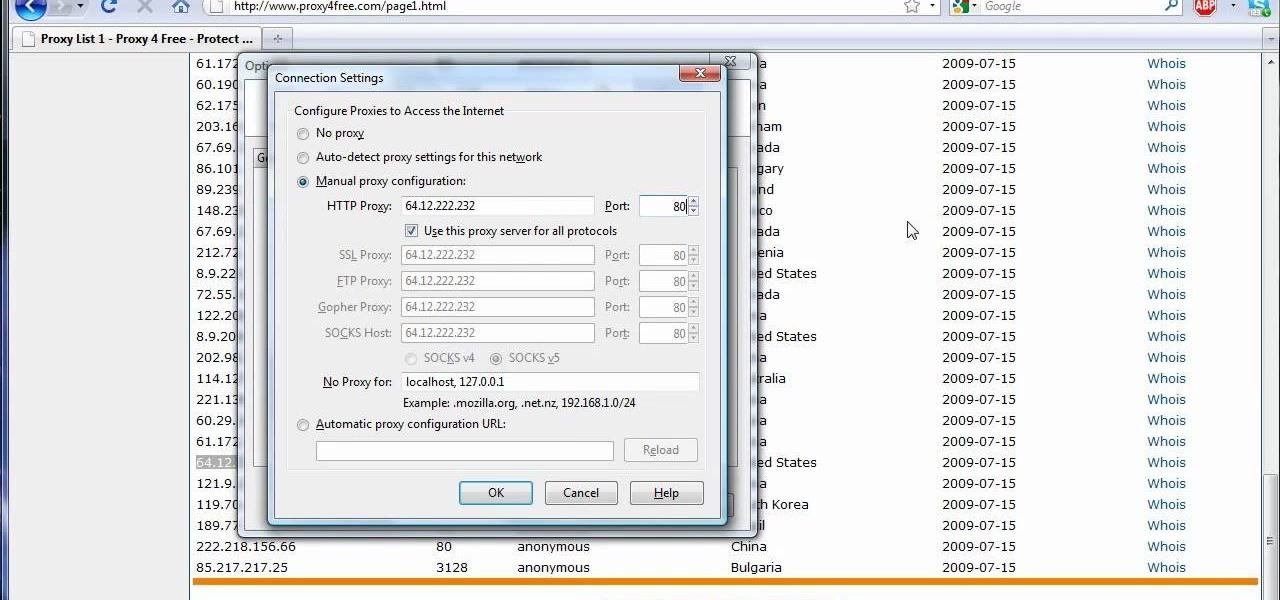
The video shows us how to use a proxy server with Firefox to hide your IP address. you can actually use this to avoid the hacking and various things that are blocking you from websites. Firefox is one of the easiest way to do this and for doing this you need to Google search the free proxylist and then you can select a proxy from the one which is related to the country you are residing in. Then copy that proxy server and then go to tools and click on options and under advanced tab click on ne...

There are a couple of limitations that Microsoft put in to Windows 7 upgrades that can prevent users from upgrading and ultimately force them to do a clean install. First limitation is that they won't let you to upgrade Windows 7 if you run Windows 7 release candidate that was released earlier this year, which they won't let you to upgrade to a download Windows edition. If you are running Windows vista ultimate you cannot upgrade windows 7 professional. We have to buy an ultimate edition then...
This is a very lengthy explanation on BTD playing. There's a lot to actually know about the strategy of Bloons Tower Defense.