In addition to the fingerprint scanner, the Samsung Galaxy S6 has all of the basic lock screen options that other Android phones have: swipe, pattern, PIN, and password. There also just happens to be a secret sixth option called "Direction lock" that protects the device with a series of customizable directional swipes—only it's hidden in an unsuspecting settings menu.
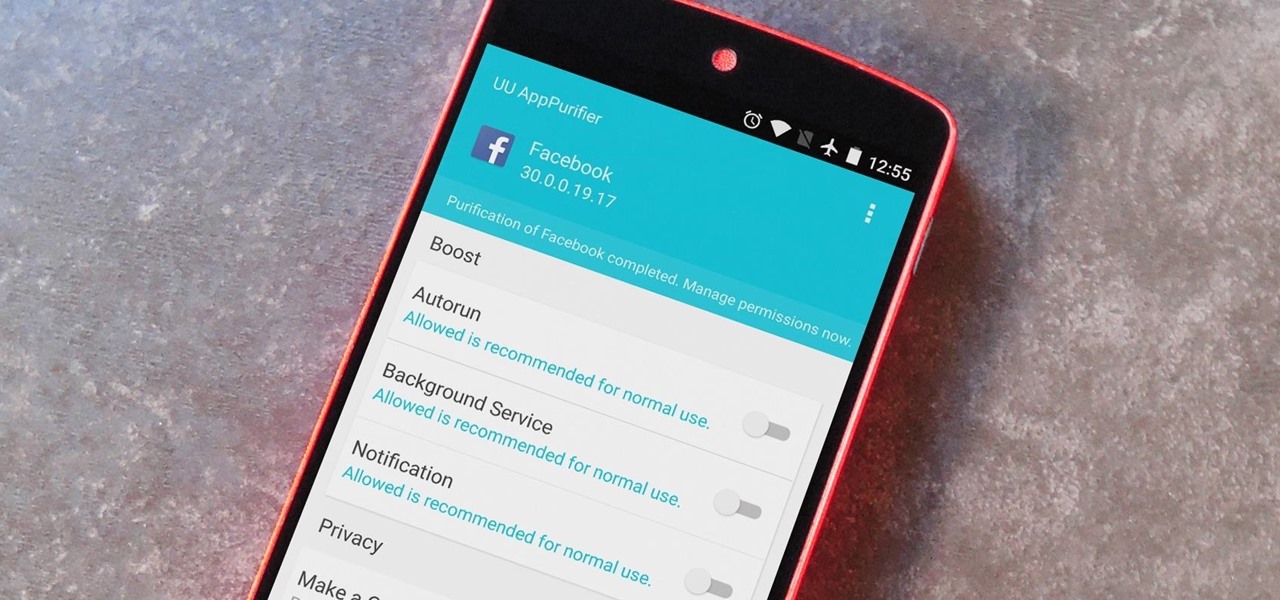
When it comes to app permissions, Android takes an "all or nothing" approach. You have no granular control over what data apps can access, so the only way to prevent an app from seeing your location or starting up on boot, for instance, is to not install the app in the first place.

Upon getting the new Samsung Galaxy S6 Edge here at the office, there are countless things we wanted to do before actually diving in and using the device. One of those things is removing all of the unnecessary pre-installed applications we never asked for.

With 16 megapixels and optical image stabilization technology, it's safe to say that the Samsung Galaxy S6 is well-equipped to take badass pictures. Packed with additional camera modes, like Panorama, Selective focus, and Virtual shot, there's always a way to capture an image as intended.

Whether it's for handling your business's social media account or just for personal reasons, like trolling an ex-girlfriend's page (not that I've ever done that) or posting on behalf of your pup, there are instances where having two different Facebook accounts on one device is simply easier than switching back and forth.
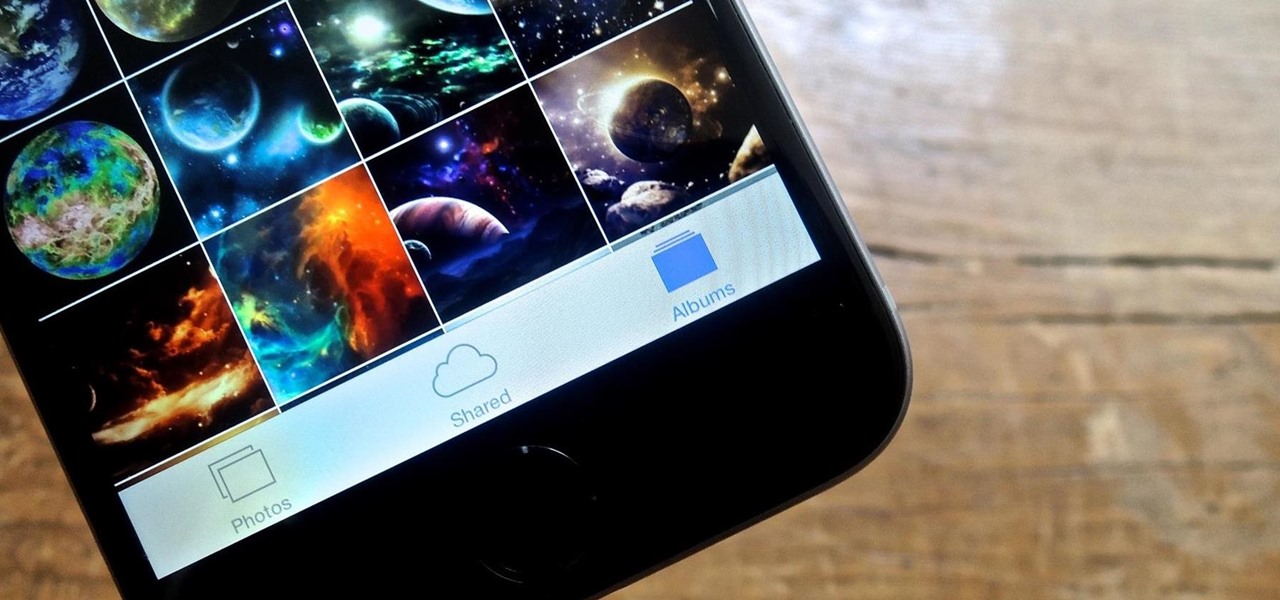
With the sheer number of pictures stored on my iPhone, using the tap gesture on the status bar is extremely convenient and time-saving when I want to reach the beginning of my Camera Roll album in the Photos app.

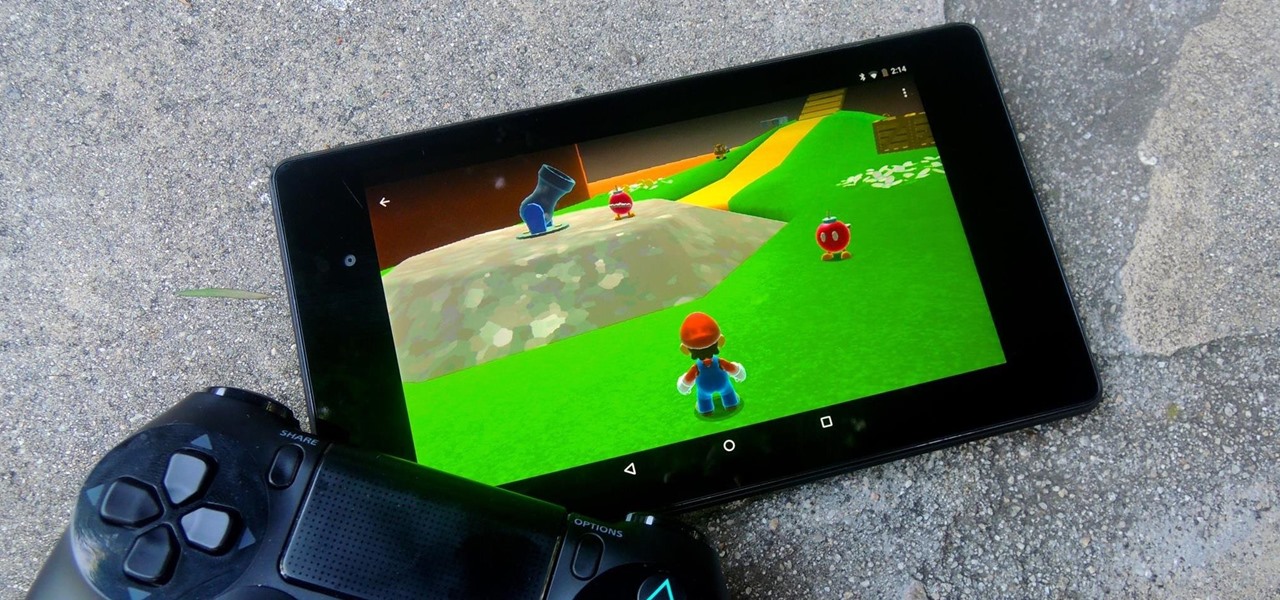
If you're jonesing to play some Super Mario Run on your Android phone, you might not be able to get your fix for some time—at least, until Nintendo figures out the best way to keep piracy down and security high. But if you can't wait for the first official appearance of Mario on Android, we've got the next best thing...

Cleaning the clutter off of your desktop every so often is a great idea. Unfortunately, that doesn't mean that you're actually going to do it. Whatever the reason, you may not have time to get everything organized, but luckily there is a way to temporarily "clean" your desktop in a hurry.

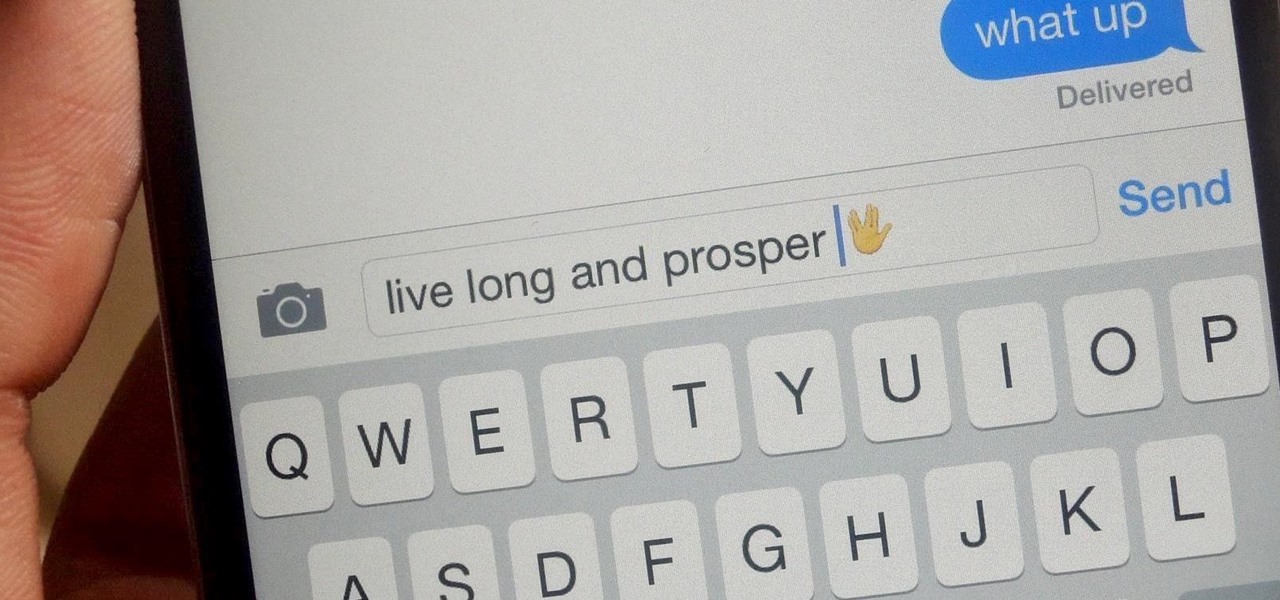
If you're a Trekkie, you might be surprised to find that Spock's popular Vulcan salute can actually be used as an emoji on your iPhone. With the public release of iOS 8.3, you'll now have updated unicode for more diverse emojis.

Get some tinfoil hats and make a time machine because we are about to go back to the 90s and learn about some phreaking.

HTC's fitness-tracking application, Fun Fit, has made its way to the Google Play Store for all to enjoy. And while fitness apps are a dime a dozen, Fun Fit offers what its name implies—fun. Like plenty of other fitness apps, Fun Fit is able to track calories burned, steps, distance, active time, walking time, and running time. Where the app differs is in its presentation.

Your iPhone's home screen is a tricky thing. You can sort your collection of apps in any order you'd like, but where you place those apps is a totally different story. App and folder placement follows a strict grid on iOS from left to right, top to bottom. No exceptions, and that's how Apple wants it. So you might think without a jailbreak you're stuck with this layout — but you're wrong.

With wearable tech becoming the latest trend in electronics, it's a shame that most smartwatches are locked down to one ecosystem. If you purchase a smartwatch, you can expect that it will not work with devices from competing manufacturers. That will be the case for the Apple Watch when the product finally hits shelves, and it has been the case for Android Wear devices like the Moto 360 for quite some time now.

Yes, they're called volume keys, but they can do much more than adjust your volume. With minimal effort, you can do some amazing things with these physical buttons, like secretly record videos, toggle on your flashlight, scroll through pages, control your music, and much more. And while using them to wake your screen is useful, let's take it a step further and show you how to use them to completely unlock your device, even if the screen is off.

Step 1: Introduction: Hello! Hackers

Welcome back my fellow hackers. Today I'm going to teach you how to preform an Idle Scan. You may be asking what is an Idle Scan. Its a very stealthy scan because you don't use your own ip you use a zombie (in computer terms).

Icebox cakes are some of the most satisfying, easy desserts to put together. This version made out of ice cream sandwiches takes the cake, literally, because the layers are almost pre-made for you. Simple and pretty when cut and served, it will be love at your first creamy bite. Depending on whether you want a layer of chocolate crunchies in your ice cream sandwich cake or not, this could be either a two-ingredient ice cream cake or a four-ingredient one. If you don't need the crunchy layer, ...

Welcome back, my amateur hackers! Over the course of the next year, we will be developing our own zero-day exploits. In my first article in this series, I introduced you to buffer overflows, which are the source of some of the most lethal exploits, particularly the "remote code execution," so we are focusing our exploit development here on a buffer overflow.

A group ironically called the "Guardians of Peace" hacked into Sony Pictures' computer systems and released a mountain of internal information such as medical records, leaked scripts, work complaints, and even celebrity aliases.

One of the golden rules to cooking a Thanksgiving turkey is to place it on a roasting rack before it goes into the oven. Missing this step and cooking it directly on the pan will burn the bottom of the bird, resulting in overcooked, dry meat.

Who says you have to cook on Thanksgiving? If you need a break, have surprise guests in town, or simply don't want to be in the kitchen cooking all day long, never fear: you have options.

You wouldn't send your GPS coordinates to a completely random stranger just because he or she asked you for it, right? So why are you constantly sharing your location (and other data) to apps on a daily basis?

Welcome back, my nascent hackers! We have spent a lot of time in previous tutorials focused on hacking the ubiquitous Windows systems, but the vast majority of "heavy iron" around the world are Linux or Unix systems. Linux and Unix dominate the world of Internet web servers with over 60% of the market. In addition, Linux and Unix servers are the operating system of choice for major international corporations (including almost all the major banks) throughout the world.

In my opinion, the greatest food hacks are the ones that help you cut way, way down on dishwashing. That's especially true when it comes to baked goods, which usually involves dirtying up a couple of mixing bowls, measuring cups and spoons, some kind of stirring implement, and the baking pan itself.

There comes a time in relationships when two people decide to move in together, and when this happens, you learn two things:

To prevent melted ice cream from leaking out of the pointy bottom of a cone, plug the hole up with a marshmallow before adding any ice cream on top. This will also give you a nice treat when you're almost finished, as the marshmallow will absorb some of the ice cream.

Welcome back, my budding hackers! When we are looking for ways to hack a system, we need a specific exploit to take advantage of a certain vulnerability in the operating system, service, or application. Although I have shown you multiple ways to exploit systems here in Null Byte, there are still many more exploits available that I have not yet shown you.

Automated tattoos are now a reality, with 3D printers being hacked into tattoo machines. Multiple people have posted videos of their 3D printer that can "print" tattoos, with one of the more impressive ones shown in the two videos below.

Welcome back, my greenhorn hackers! Lately, much of the discussion here on Null Byte has revolved around evading detection and not getting caught hacking. Several of you have written me asking for a series on evading detection and forensics, and while I began a series 5 months ago on just that, we have changed hacking platforms from BackTrack to Kali, which has a much more highly developed forensic toolset.

Welcome back, my hacker apprentices! To enter the upper echelons of hackerdom, you MUST develop scripting skills. It's all great and well to use other hacker's tools, but to get and maintain the upper hand, you must develop your own unique tools, and you can only do that by developing your scripting skills.

Welcome back, my apprentice hackers! As many of you know, I have been hesitant to adopt the new Kali hacking system from Offensive Security. This hesitancy has been based upon a number of bugs in the original release back in March of 2013 and my belief that BackTrack was easier for the novice to work with.

Welcome back, my greenhorn hackers! In my continuing effort to demonstrate to you how to hack the ubiquitous Windows 7, we will going after that notoriously vulnerable Adobe Flash that is on nearly every client Windows system (you are not likely to find it on servers).

Welcome back, my novice hackers! We've done a number of tutorials using one of my favorite hacking tools, Metasploit. In each of them, we've used the msfconsole, which can be reached through either the menu system or through simply typing "msfconsole" from the terminal.

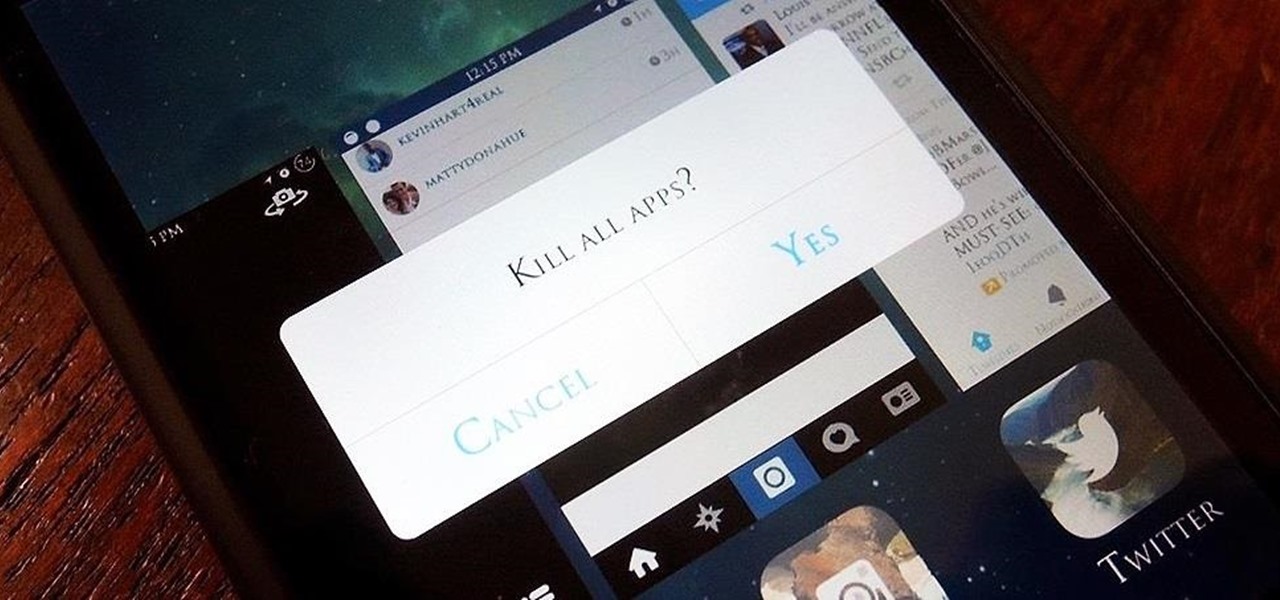
When lending our iPhone to our kids, siblings or friends, it's not uncommon to have it returned with what seems like a million apps open in the background. What's worse is being too lazy to close all those open apps, in turn having our battery drain much faster than normal.

Welcome back, my neophyte hackers! Have you ever had a neighbor that you're certain is up to no good? Maybe you've seen him moving packages in and out at all hours of the night? Maybe you've seen people go into his home and never come out? He seems like a creep and sometimes you hear strange sounds coming from his home? You know he's up to no good, but you aren't sure what it is exactly.

Most of us are used to just grabbing a bag and throwing it in the microwave when we want popcorn. It's easy, convenient, and requires little to no cleanup. But what about those times when you're away from home and don't have access to a microwave?

Just days after news spread that Snapchat could be exploited by spammers, an anonymous group of hackers have released the private information of over 4 million users of the popular photo-sharing application.

Welcome back, my tenderfoot hackers! So many readers in the Null Byte community have been asking me questions about evading detection and hacking undetected that I decided to start a new series on digital forensics.