Welcome back, my neophyte hackers! In today's hack, we're going to have a bit of Halloween fun. Have you ever had a boss who made you miserable with his micro-management and nagging? Maybe you thought he unfairly fired your friend/colleague? Well, now here's your chance to get a bit of revenge and keep him or her off your back!

Have you ever noticed how your home screen and lock screen wallpaper moves underneath your notification, app icons, really anything on display? It's a cool effect, but to some, might be a bit jarring. On top of that, it also uses up precious battery life. If you're sick of seeing this parallax effect on your iPhone, here's how to turn it off.

Welcome back, my rookie hackers! Many newbie hackers focus upon the technical aspects of hacking and fail to give enough attention to social engineering. In fact, I would say that technical hacks should ONLY be attempted if social engineering attacks fail. Why bother spending hours or days trying to hack a password if someone will simply give it to you?

Welcome back, my fledgling hackers! One of the first issues any hacker has to address is reconnaissance. Before we even begin to hack, we need to know quite a bit about the target systems. We should know their IP address, what ports are open, what services are running, and what operating system the target is using. Only after gathering this information can we begin to plan our attack. Most hackers spend far more time doing reconnaissance than exploiting.

Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

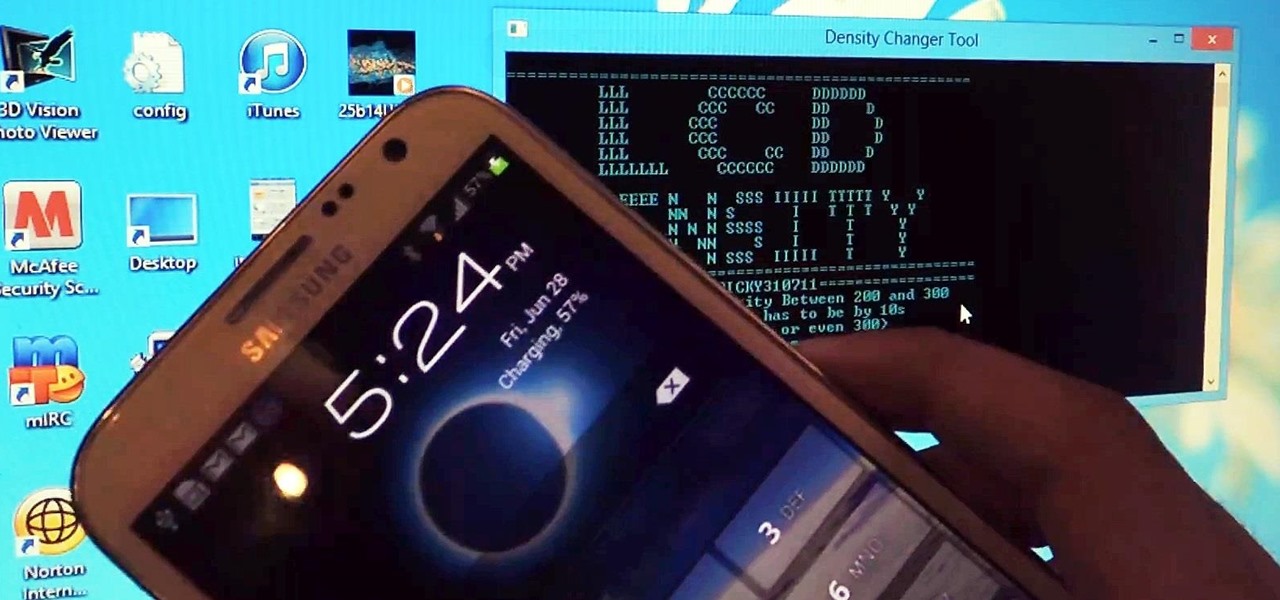
There are a ton of cool features available on your Samsung Galaxy Note 2, but if you're a softModder, you can make your phone do just about anything.

With more people joining the internet scene each day it's important that it's security is.. well it has to be good. Of course everything can be hacked and that's the way hackers work. They know there IS a vulnerability but they don't don't know the rest. in this article i'll try to explain the big difference between HTTP and HTTPS

Who am I? First let me introduce myself. I am Th3skYf0x, an -well lets call it

Welcome back, my nascent Hackers! In my last blog, we looked at a passive way to gather information necessary for a hack. The advantage of using passive recon is that it's totally undetectable, meaning that the target never knows you're scouting them and you leave no tracks. The disadvantage, of course, is that it's limited to only some websites and not entirely reliable.

If you thought humans were reading your résumé, think again. Robots do, and their one solitary objective is to systematically crush the hopes and dreams of those who don't make the cut. Instead of paying a few humans to read thousands of résumés over a couple weeks, many companies use computer programs that can do the job in less than an hour. In fact, at least 90 percent of Fortune 500 companies use what they call an applicant-tracking system, aka rejection machines.

Welcome back, my neophyte hackers! Several of you have written me asking how to crack passwords. The answer, in part, depends upon whether you have physical access to the computer, what operating system you are running, and how strong the passwords are.

Pringles are just as well known for their cylindrical packaging as for their suspiciously addictive fried crisps. Yes, that's crisps—not chips.

Most of us have a designated spot where we like to charge our devices, but no one likes to look at a giant, tangled mess of cords. That's why inductive chargers are so awesome. They allow for wireless charging, and are a lot easier on the eyes. But what if you don't even want to leave the charging module sitting out? This relatively simple hack by YouTube user lobbamobba lets you hide the charging module inside a nightstand or other piece of furniture so that you can juice up your device with...

For most people, the battery life on a DSLR is more than sufficient, but if you want to do a really long exposure or time-lapse, one charge might not last long enough to get the shot you want. You can always connect it to an extension cord to charge while you shoot, but that can be really annoying to work around.

Samsung bucked the trend and threw hard keys onto the Galaxy S3 while most manufacturers are going the soft key route. This hack will add on-screen buttons to your TouchWiz-based ROM. You'll need a root file manager with a system writable text editor—I recommend ES File Explorer for this, but feel free to use whatever you want. If using ES, hit Menu, Settings, go down to Root Settings, and check Root Exploerer, Up to Root, and Mount File System.

Despite the security concerns that have plagued Facebook for years, most people are sticking around and new members keep on joining. This has led Facebook to break records numbers with over 1.94 billion monthly active users, as of March 2017 — and around 1.28 billion daily active users.

So, you've finally managed to get addicted to one of those free farming games, like Farm Story or Tiny Village. You play the game nonstop now, and the only thing stopping you is that dreaded on-screen notice to come back in 23 hours to finish farming or building. Come back in 23 hours… WHAT?!? Most of these free games will start charging you at this point. Time becomes a luxury. Well, not anymore, thanks to XDA Developer StupidIdea, who made a time-tricking app called GMD Speed Time (that's t...

Back in 2010, iOS developer Daniel Amitay developed a camera security app for iPhones that used an unlock screen almost identical to that of the iPhone.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

Until recently, brainwave-reading devices have pretty much only existed in science fiction. Sure, electroencephalography (EEG), the technology that powers these devices, has been used in medicine and psychiatry since the late 1800s, but diagnosing people's brains and reading their minds are two totally different things. The first EEG headsets available to the public were used mostly in gaming and even in fashion, but in the last few years, they've gotten a little more sophisticated.

Since most devices these days are mobile and wireless, a lot of people have a bunch of old hardware from a decade or two ago sitting around unused, just wasting away in dusty boxes. Look familiar?

In this video, I show you a technique for hacking a four foot mega magnifying lens out of your old projection TV. Not only are these TVs everywhere, they can be found easily—for FREE!

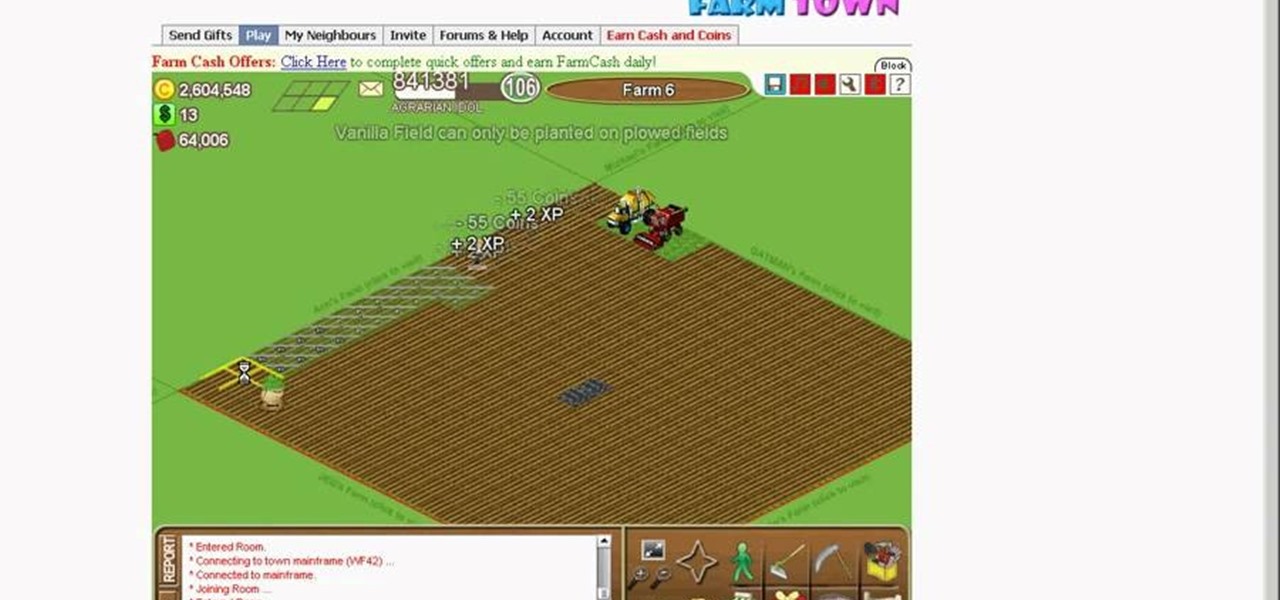
By overlapping your Farmtown crops, you can up the production output for your fields. There's a bit of a trick to being able to layer your crops in such a way that the game will allow. However, you can still manage to accomplish this without having to resort to cheat codes, mods or hacking the game. Just follow along with this tutorial - you can even keep your accessories like flowers and bird baths! Put your longest growing crop on the bottom.

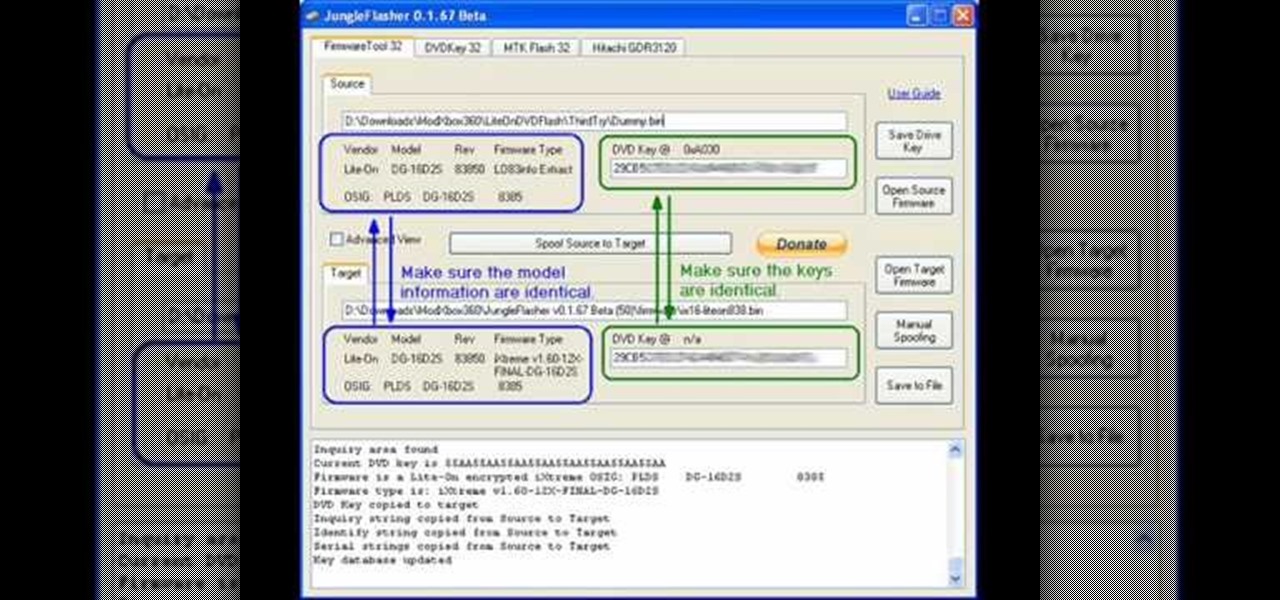
If you're tired of paying $60 for new XBox 360 games or waiting years for them to get cheaper, you should probably mod you system. This will allow you to play burned copies of games for free (no time to get into the moral implications here). The first step in that process is flashing your disc drive and installing custom firmware on it that will recognize your burned game discs. This video will show you how to flash the Lite-On drive used in many XBox 360's. If you don't have the Lite-On driv...

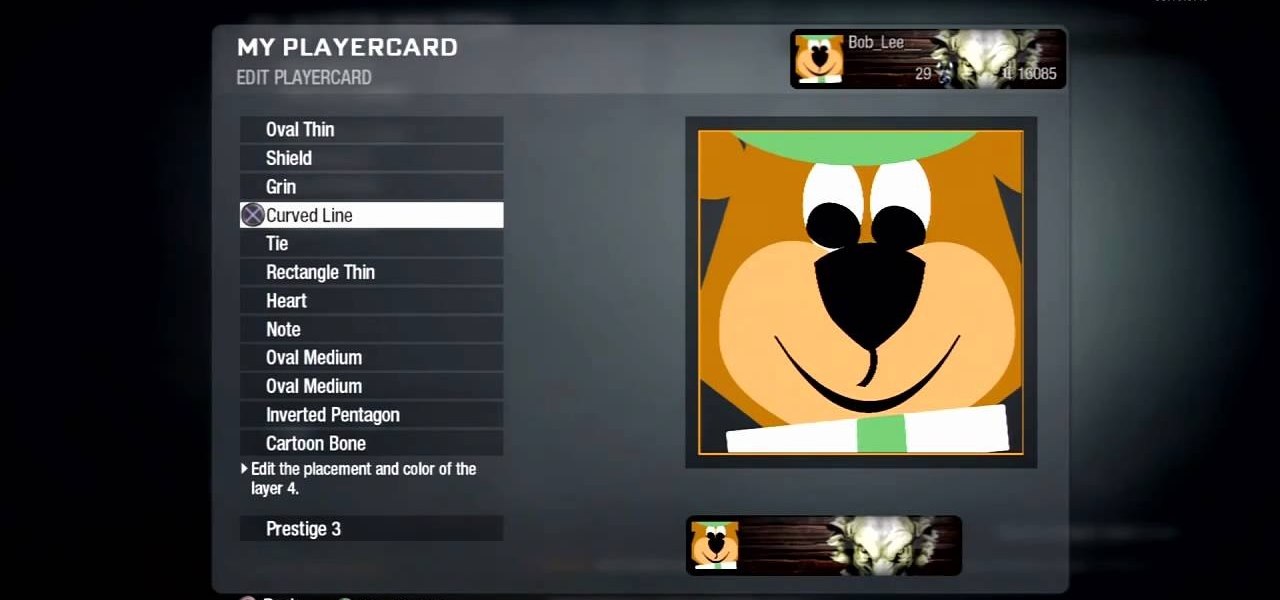
Are you smarter than the average bear? Show the world by using Yogi Bear as your Black Ops playercard emblem. This clip will teach you everything you'll need to know to draw a custom Homer Simpson emblem in the Call of Duty: Black Ops Emblem Editor.

Unlock the "Closer Analysis: Hidden Intel" trophy in Call of Duty: Black Ops! This achievement is won by finding the hidden intelligence documents in Missions 1, 2 & 4.

Want to earn the "Sally Likes Blood" achievement on the Regular difficulty setting in the single-player campaign of Call of Duty: Black Ops? Here's how you do it.

Want to learn how to do quick scoping in BO? It's easy: use the variable scope and zoom in to the second or third level of magnification. Voilà. No more two-second delay when shooting. For a complete walkthrough of how to quick scope, watch this gamer's guide.

So, how do you get your family together in FrontierVille on Facebook? One way is with the Dinner Triangle. If you family gets lost out in the forest or behind a tree or building, then all you have to do is ring the Dinner Triangle and they'll come running. See how to use it!

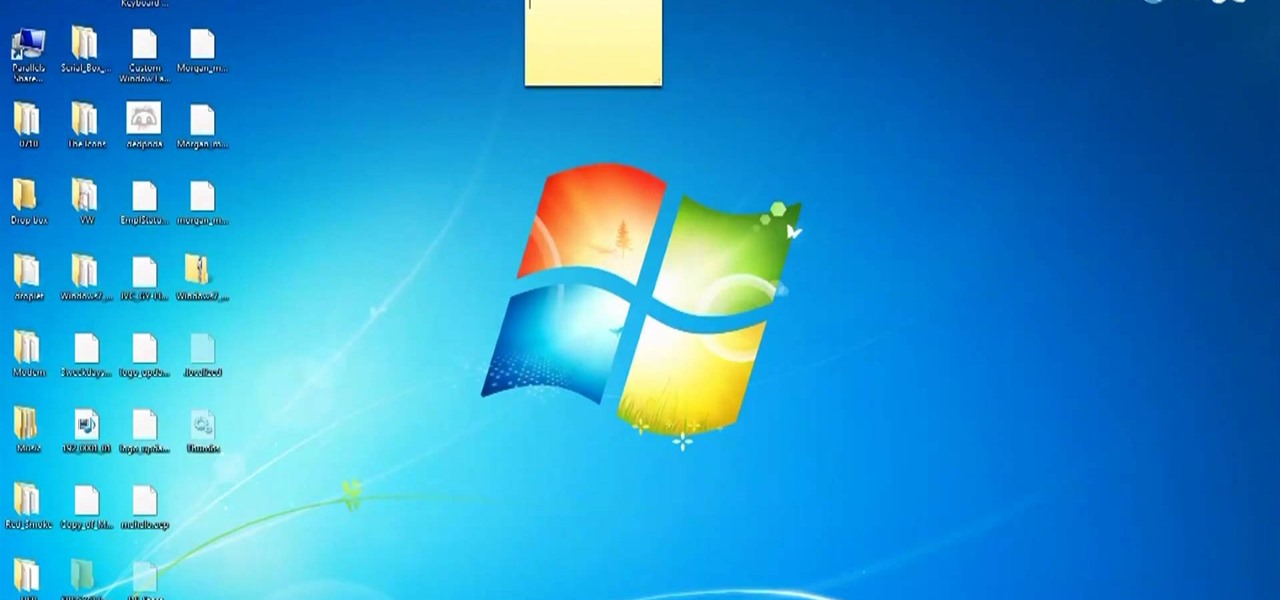
Interested in hacking the power button on your Windows PC to put your computer to sleep instead of shutting it down? This Windows 7 tutorial will show you how it's done! It's easy! So easy, in fact, that this home-computing how-to can present a complete overview of the process in just over a minute's time. For more information, including detailed, step-by-step instructions, watch this Win 7 user's guide.

In this Electronics video tutorial you will learn how to use Bluetooth connectivity to share cell phone files. You are not hacking in to other people's phones as you need their permission to access their phones. You can change ringtones and pictures or share them with your friends. For this both people have to have Bluetooth on. Go to options > Bluetooth > visibility > shown to all. Now go back to Bluetooth and make sure it's ON. Now select 'paired devices'. The same steps have also to be fol...

The Evo 4G does a lot of fancy things. Unfortunately, a lot of those fancy things are power-intensive. Interested in getting the most out of the HTC Evo 4G's battery? Whether you're the owner of an HTC Evo 4G Android smartphone or just covet one, you're sure to enjoy this Evo owner's guide from HTC Evo Hacks, which presents a complete, step-by-step walkthrough of how to improve your Evo's battery life. For complete details, take a look!

In this tutorial, we learn how to use salty hashes to keep passwords secure. A hash is stored in a database that is hashed with an algorithm, so not everyone can see exactly what your password is. When you type your password into a website, it doesn't actually register as words, it registers as a hash. This keeps your passwords secure so not everyone can see them. Salting is when you use random pits and attaching them to your regular hashes so not every password is the same. The salt is what ...

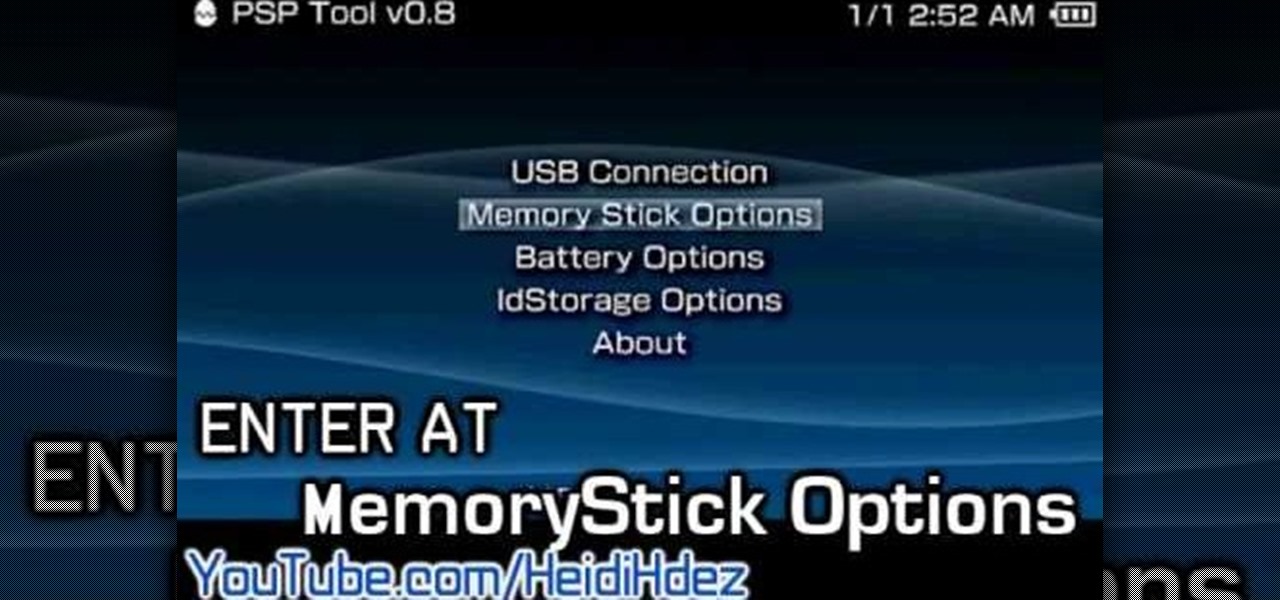
Hacking the PSP is a complicated process, and there has been some demand for a software tool that would make the process easier. This video has that solution. It explains how to use a program called PSPtool to create the magic memory stick and Pandora's battery much more easily than you could otherwise. Follow these instructions and play those homebrews!

In this clip, learn how to make a fast, cheap and super easy mount for your your bicycle to display safety lights. Wearing bike lights at night will help you stay safe in the dark and if you want to avoid the cost of getting lights custom fitted, this hack is perfect for you. All you will need is some PVC pipe and some grip tape (like the kind used for tennis rackets). Follow along and get started. This mount is flexible and fits most standard lights or flashlights.

In this tutorial, you will learn how to hack an ordinary pen and turn it into a Mont Blanc worth $200. Mont Blanc is known for its smooth writing style and enviable design and with this clip you can get all the perks of this luxury brand for about 15 bucks.

If you move around a lot, you may notice that you can't play the same DVDs from country to country. The world is separated into different regions, and not all movies will play in all places. There are ways around this security measure, however, if you follow this tutorial.