Hey readers! This tutorial will be the entry point for the introduction of buffer overflows. Something like requesting user input is a very common place for vulnerabilities to pop up and we will definitely have fun while trying to make programs crash. But for now, let's start with how we can get input from a user.

There are few kitchen tools as elusive as the oyster knife. Many people—even seafood lovers—don't own one. If you do own one, it probably gets used so infrequently that it gets sent to the very back of the shelf where it proceeds to get lost. Then you accidentally find the knife once a month when you don't need it, but can't for the life of you find the sneaky little thing when you do need it.

As many of you know, I firmly believe that hacking is THE skill of the future. Although the term "hacking" often conjures up the image of a pimple-faced script kiddie in their mother's basement transfixed by a computer screen, the modern image of the hacker in 2015 is that of a professional in a modern, well-lit office, hacking and attempting to development exploits for national security purposes. As the world becomes more and more digitally-dependent and controlled, those that can find their...

Animal masks are always a popular option for Halloween, not just because you can pair them with practically any outfit, but because they never go out of date. They've been a staple of Halloween costumes starting from the 1900's, but possibly even prior to that. George Takei, of Star Trek popularity, even left a hilarious comment on Accoutrements' Horse Head Mask Amazon page, making puns left and right about the animal mask—a testament to how trendy these faux mammalian skins really are.

I love cheap, nutritious food: lentils, rice, toor dal, and other beans and grains. Even popcorn. The only problem is that they usually come in floppy plastic bags that make measuring ingredients more difficult. I usually open up one corner of the bag only to have everything come spilling out all at once whenever I try to pour out measured amounts.

Parents, grandparents, aunts and uncles, and even older siblings have all likely dealt with handing their smartphones over to young children. No matter if they want to play games or watch cartoons or record funny noises, you're handing over a very personal device to those who can mess up what they don't know.

As you may have already heard, the worst bug in OpenSSL history went public yesterday, dubbed Heartbleed. While we can go deeper into the technical details of it later, the short version is that OpenSSL, the library used to encrypt much of the web running on Linux and Apache has been vulnerable for up to two years.

Welcome back, my budding hackers! I've written several listener guides on creating a malicious PDF or malicious Word document that would carry in it a payload with the Meterpreter, or reverse shell enabling you to own the system. One of the hurdles to using these techniques is the antivirus (AV) software on the target system. For instance, if you try to email a malicious PDF or Word doc, it's likely that the victim system will alert the victim that it contains a virus or other malware.

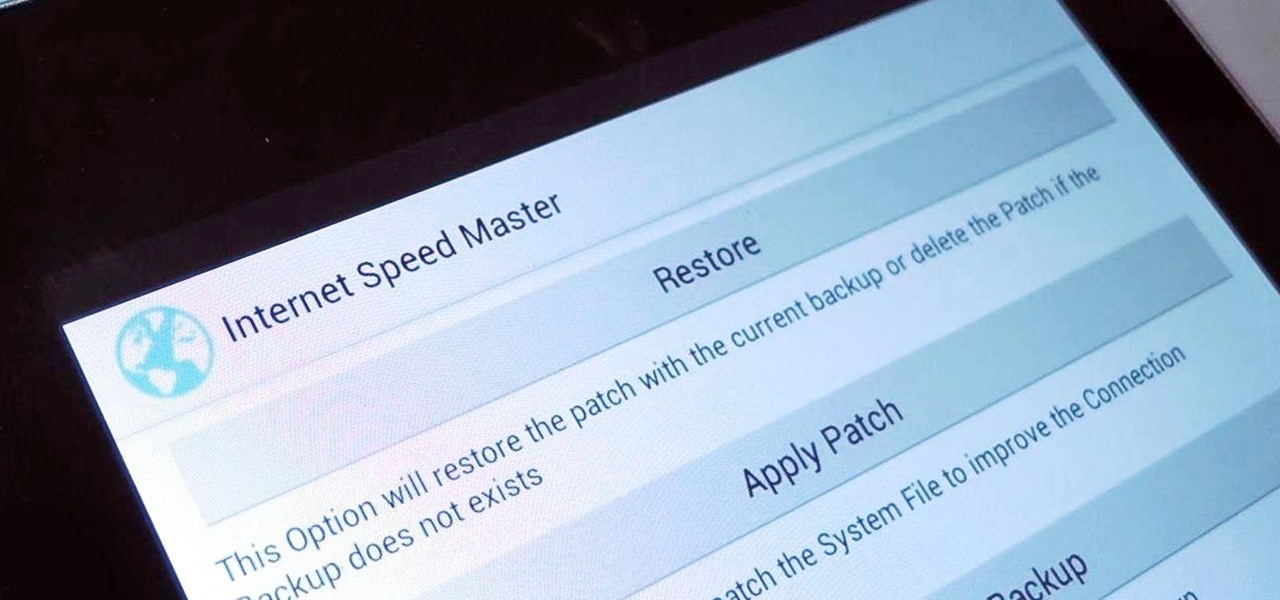
Even if you have the fastest internet connection in the world, it's not going to be fast if your Android device isn't optimized to use all of the bandwidth. I have pretty fast speeds at home, but every now and then my web surfing on my Nexus 7 tablet is halted in its tracks—for seemingly no reason.

A lot of people have problems with their cats urinating inside the house, leaving behind the retched odor of cat pee. Others get frustrated when feral or stray cats pee on their porch, patio, or anywhere else outside of their house, as it's not the most welcoming odor when guests arrive.

What's the meaning of life? That's the age-old question; but can it ever really be answered? I mean, isn't life just a big game anyway? Perhaps, a game of inches?

Sometimes you just want to grill. It doesn't matter where you are, what you have, or whom you're with—you just want a delicious burger and you don't care what it takes.

Camping is wonderful isn't it? You get to go out into the wild, build a fire, pitch a tent, and tell ghost stories. My favorite part about camping isn't any of those things, though. No, the best part about camping in my opinion is the food. Whether it be planking freshly caught fish, roasting hot dogs, melting s'mores, or cooking hobo dinners, the food is always the most memorable part of camping to me because you get to eat stuff outside of the norm.

There’s a good chance that you’ll be alone in life one day, and no... I’m not talking about a couch-bound, dateless loser with a pocket pussy and a bag of potato chips. I’m talking about alone. In the wilderness. Hungry. Cold. Lost. You can’t stay in one place too long, so it would be nice to have something to carry your belongings in. Maybe it’s post-apocalyptic land where you’re the sole survivor, and all the backpacks and rucksacks in the world are but mere ash. Either way, knowing this si...

There are a total of 242 stars in Super Mario Galaxy 2 on the Nintendo Wii — 120 normal stars, 120 green stars and 2 bonus stars. If you've already found all of the stars in Worlds 1, 2, 3 & 4, now it's time for World 5!

In this Computers & Programming video tutorial you will learn how to make a favicon for your site in Photoshop CS3. A favicon is a little symbol that shows up on url bars and also on browser tabs. Open a new project in Photoshop by pressing ctrl+N. Select height and width to 64 pixels and click OK. Now open the title tool and type in whatever you want. In the video, it is ‘F’. Open the background layer and do a color overlay of black. Now change the color of the title to white so that it ...

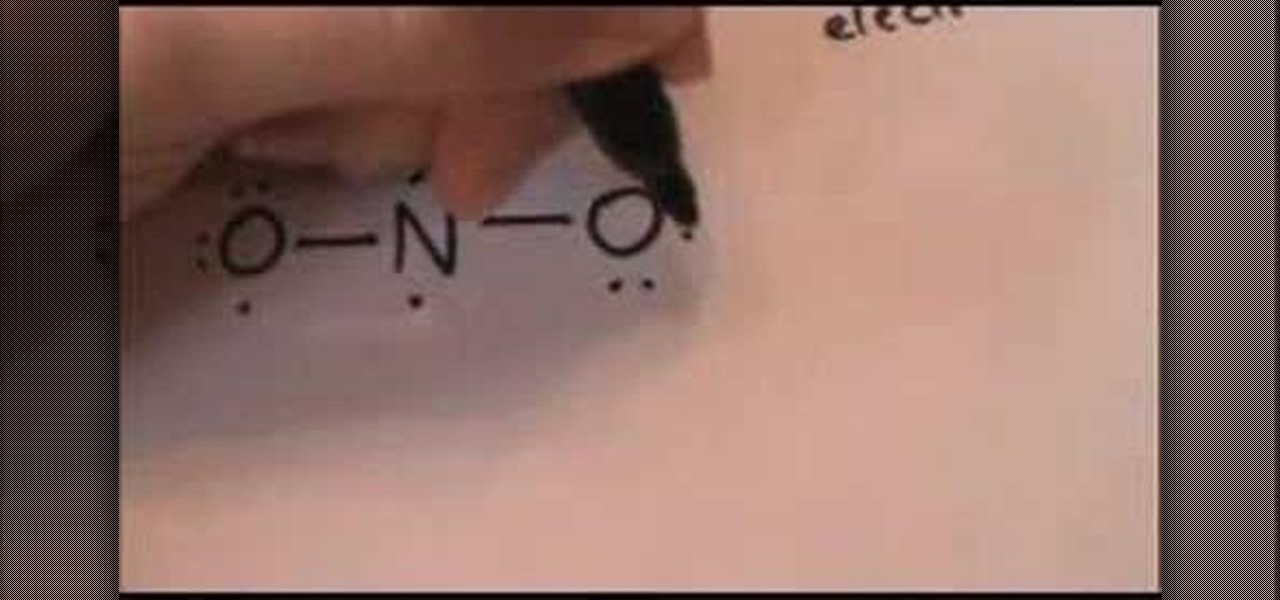
This video shows you how to draw the Lewis electron dot structure for the nitrite anion- first you start by drawing the symbols o, n and o, in that order, and then you proceed to draw two dots on the top of the n, and one on each other side.On the 'o' on the far left, you draw two dots on the top, and two dots on the left, putting just one dot on the bottom and the left- the right 'o' mirrors this pattern.Next you link all three letters with two lines, using the single dots on the left and ri...

Second Class Boy Scouts work on building their outdoor survival and camping skills. Compass work, nature observation, camp tools, and swimming are areas where new skills are mastered and demonstrated. A second class scout, having completed all the requirements, should be able to lead a hike, care for his own equipment, set up a campsite, and perform basic first aid.

Greetings all. Before I get into the tutorial, I would like to mention that I am fairly new to Null Byte (been lurking for some time though), and what really appeals to me about this place is its tight, family-like community where everyone is always willing to help each other and the constant search for knowledge that inhabits this subdomain is a driving motivator for me to join in. I'm glad I arrived at the right time. Anyway, wipes tears (not really)...

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

With all of the technology available today, which do you use to be your personal alarm clock? You can have a huge, bulky alarm clock, you can use your computer, and you can have one of those small, portable analog clock, but why use them if you have an iPhone? The iPhone has a built-in alarm clock that's perfect for cutting down on the bulk of life. So, how do you use it? Best Buy has answers. The Best Buy Mobile team explains how simple it is to set an alarm on an iPhone with the built-in cl...

This video will go over how to insert a check box in Microsoft Word for printing or for electronic distribution. With just a few clicks you can get a check box. You can even add different symbols or styles for your check box.

You've written the great American novel, and you want to make sure that your story stays yours. Register your copyright and preserve your intellectual rights. In this video, learn how to copyright produced material.

The "Hacker" style was created for hackwars.net for their avatar system. You can basically take the simple shapes as seen at first in the video and draw pretty much any kind of character. Just go wild! Don't forget to add the thick black line around the outside. It really makes this style. Check out this video drawing tutorial and learn how to sketch a Hacker style kid with a bazooka.

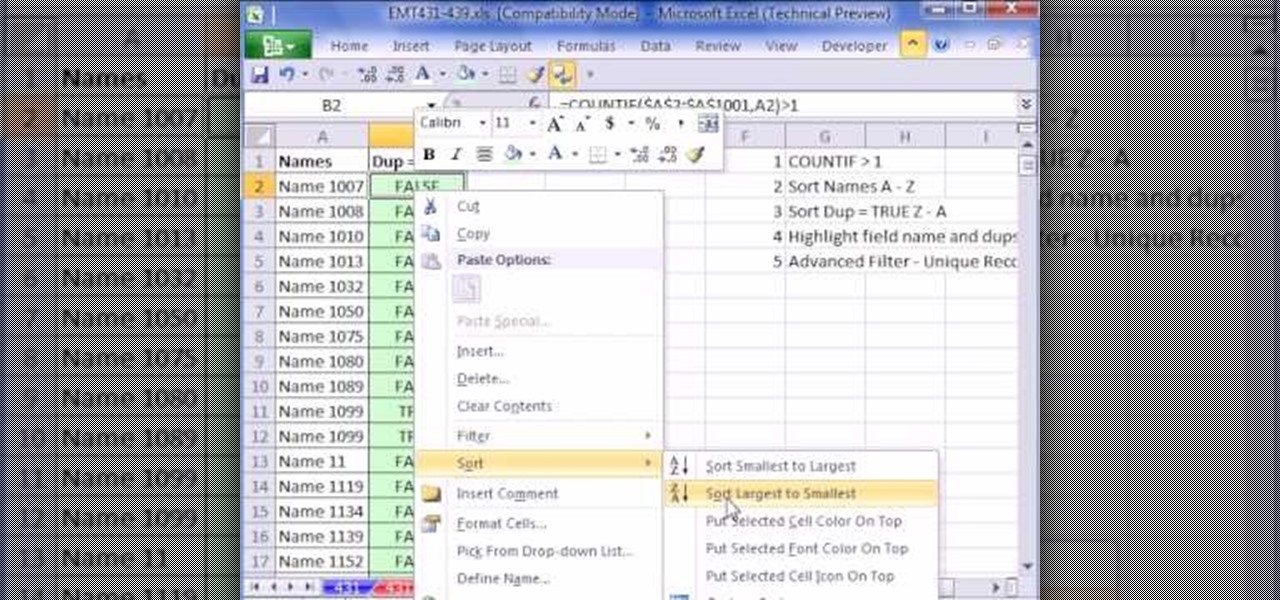
This video is about finding duplicate entries in excel sheet. The example excel sheet contains different names. There are around 1000 different names in the sample excel sheet. CountIf(range,criteria) formula has been used to do the comparison and return of results in True or False mode. Type =CountIf( now move your left arrow key, this will generate the formula like =CountIf(A2. Now press Ctrl+Shift+Down arrow, this will select all the available values in the column. Now press F4 to lock it ...

This video shows how to make a rotating SWF logo in Photoshop. Choose any desired logo that will be used later in the SWF file. Save the logo to the desktop. Use any kind of editing pogram. Make sure we only have what we want showing the area coloured with small squares is invisible. Open any version of Adobe Flash. Create a new "Actionscript 2" file. Then set workspace size to 240X320 and background color to match the picture we choose before. Make sure we select Flash Lite 2.0. Then go to F...

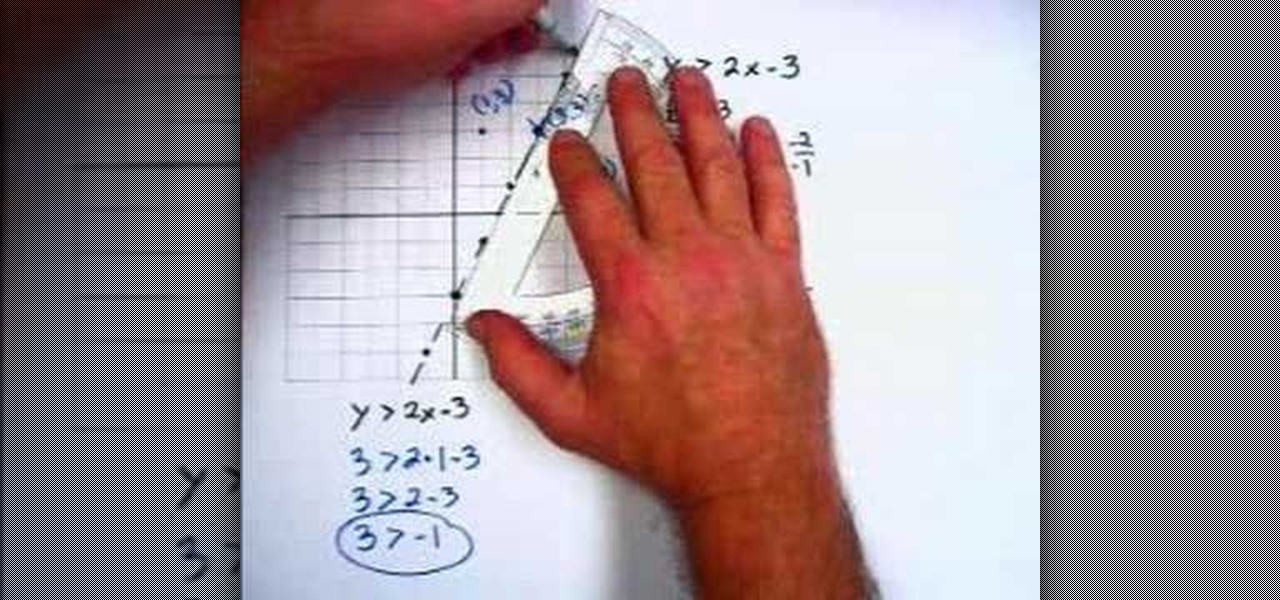
In this video the instructor shows how to graph linear inequalities. A linear in a equation is almost similar to a linear equation except for the sign in the equation. Now treat the in equation as a linear equation and graph the line. So substitute the lesser than or greater than symbol in the liner in equation with the equals to sign and graph the equation. Find the slope of the equation and identify the points that the line passes through. Now take a point on the either side of the pointed ...

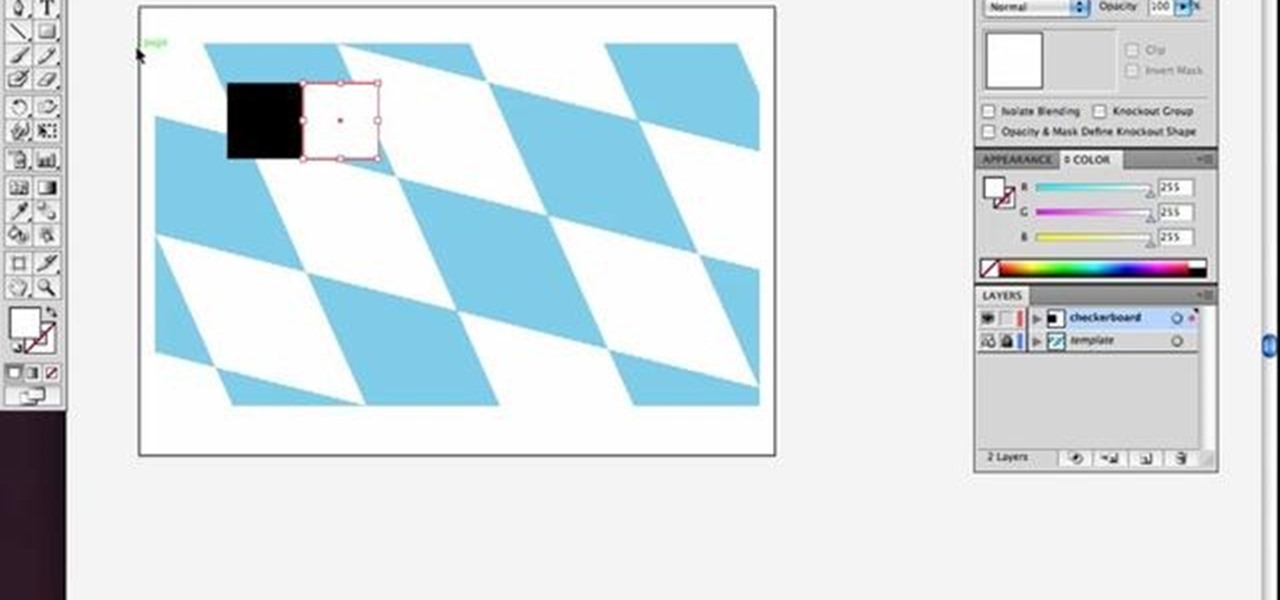
Check out this simple Adobe Illustrator CS4 tutorial to learn how to create a skewed checkerboard pattern. This technique will save you the trouble of having to use the Option and Drag method multiple times. Veerle Pieters expertly takes you through this easy pattern technique. For more Adobe Illustrator tutorials, search for Illustrator on WonderHowTo.

Pruning a rosebush removes old and dead growth, improving the health of the plant and making room for new buds.

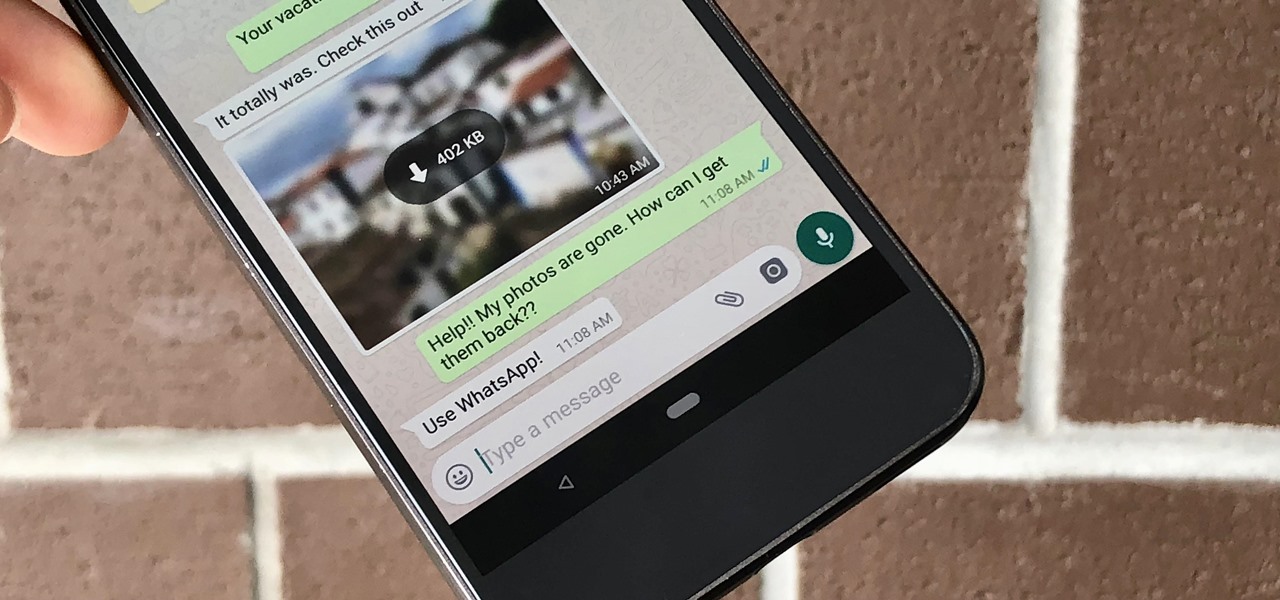
Thanks to cloud storage's increasing accessibility, permanently losing photos is becoming less and less common. Still, if you accidentally delete a picture from your smartphone without first making a backup of some sort, that data is pretty much toast — unless we're talking about photos from WhatsApp.

Earlier this week we showed you how to use multiple accounts on Instagram, and now Facebook is rolling out a similar feature for its Messenger app, as well as a few other features.

There's a feature in Google's Photos app for Android, iOS, and the web that lets you create shared albums with your friends and family. It's really a useful feature that makes it fun and easy to collaborate on an album with a person or persons of your choosing.

Welcome back, curious hackers! In today's tutorial, we will be diving deep into the manipulation of Google Operators, commonly referred to as "Google Dorks" in order to access Surveillance Cameras and other control panels.

Free trials are a great way to test out products before a purchase, or simply for the exploitation of free stuff for that limited amount of time. Some trials last a few days and some last even a month or two, but no matter what—these trials will always expire. But like most things in life, there is a way to get around such limitations.

Learn how to do the "Sleazy Slide," also known as the "Dirty Slide" line dance, with this video tutorial. This 18-count, 4-wall country western line dance is often done to "Wild Thing" by Tone Loc, "Funky Cold Medina" by Tone Loc, or "Cleopatra" by Pam Till, among others. Follow the steps in this how-to video, and you'll be doing the "Sleazy Slide" in no time.

Crayola Color Explosion™ lets you create wild multicolored effects with a single color-reveal marker! The unique clear-ink marker works only with black Color Explosion paper, revealing hidden colors for amazing designs. Drawings can be done freehand or with stencils. A great project to do with your kids!

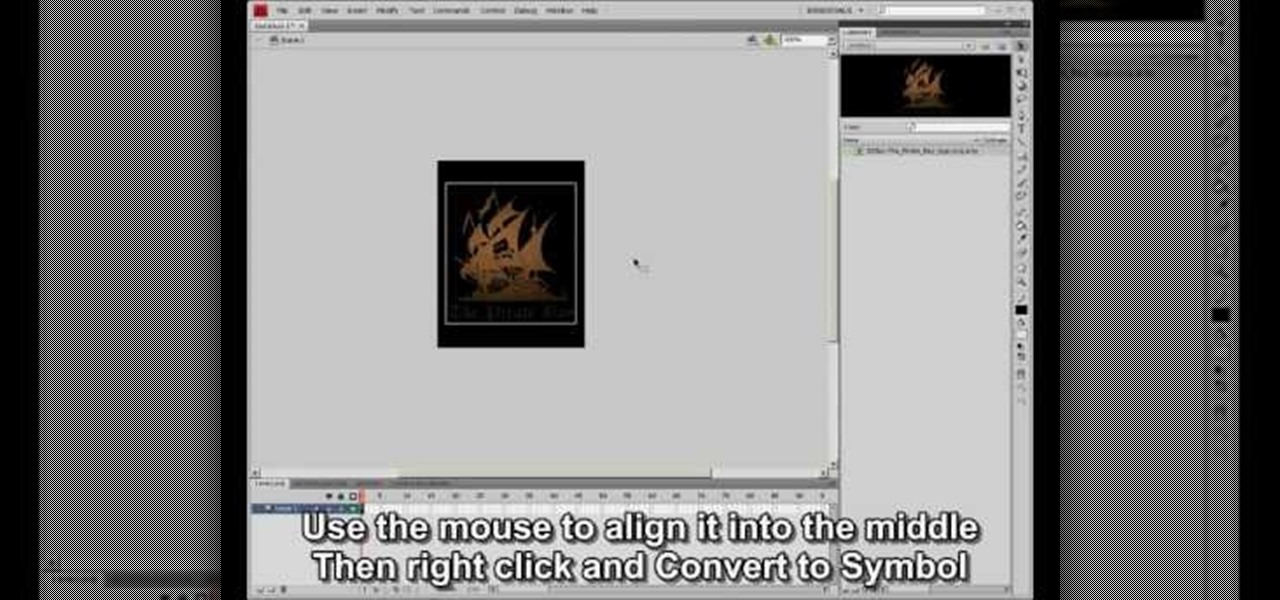
1. The following Steps shows how to open a URL in a Web Browser, using a Button Click from a Flash Application. 2. Open a new Flash Application and place a Rectangle Shape from Tools and inside place a Text Box and Enter a Text named "URL". 3. Then convert it to Symbol by Right Click->Convert to Symbol and selecting type as Button. 4. Goto Button Properties and Name the button instance as "btnurl" 5. Then in the Action Screen Create a OnRelease() Event function for Button "btnurl" 6. use a me...

Learn how to play "Now Or Never" from High School Musical 3, an acoustic guitar tutorial. Follow along with this demonstration, tabs and lyrics here:

Picture-in-picture mode on Chromebooks is almost identical to the one found on Android phones. Once activated, it transforms your video into a small window so you can do other things while watching. But the Chrome OS version is actually a bit better thanks to the addition of an Android 11 feature.

Your Galaxy's lock screen already lets you know there's no SIM card installed if it's missing on your device, so there's really no need to have a persistent icon for it on the status bar. If you want to hide the pesky symbol and accompanying notification for good, there's a nifty app you need to check out right now.