
How To: Schedule Ringtone Silence for Weekly or One-Time Events on Your Samsung Galaxy Note 2
We've all had that moment when we enter into a classroom, meeting, or theater and completely forget to put our cell phones on silent.


We've all had that moment when we enter into a classroom, meeting, or theater and completely forget to put our cell phones on silent.
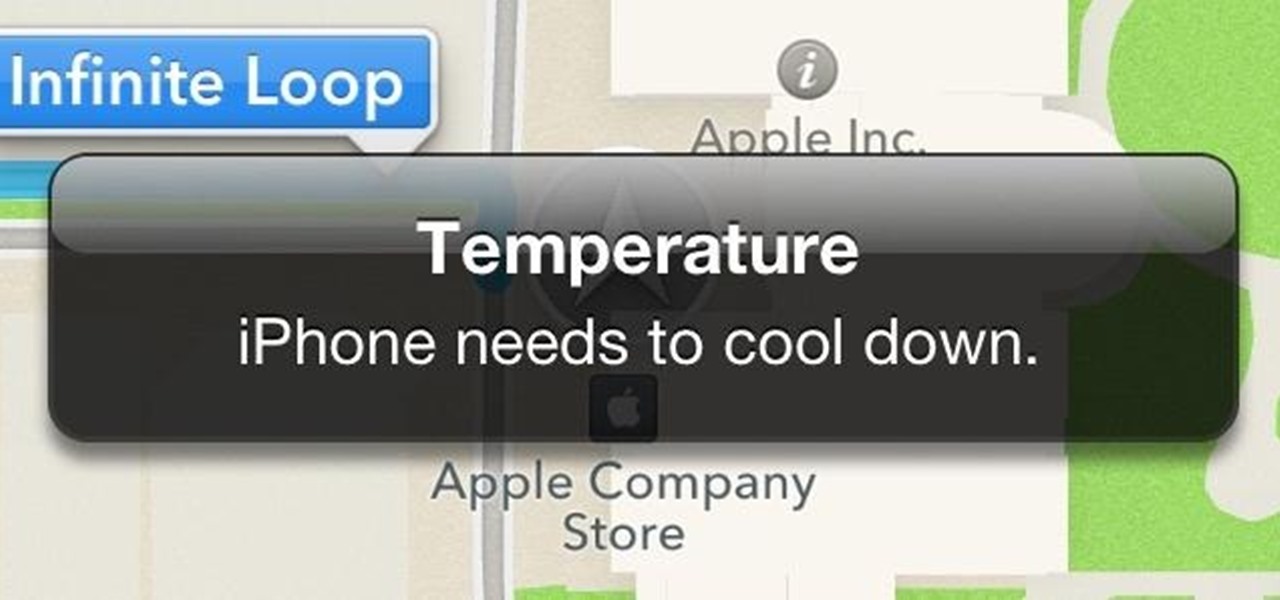
A few months ago I was driving around trying to find a store using Apple Maps (a terrible situation in and of itself), when my iPhone decided to shut off in the middle of giving me directions. I had no idea what happened, and when I looked at the screen, I saw this: My phone had never overheated and I really didn't know what to do. Needless to say, I couldn't really get to where I was trying to go without those directions. I pulled over and waited for the phone to cool back down, which took a...

Social media is where we post our thoughts for the world to see, but sometimes a little more exclusivity is needed. And that's where Scrambls comes in.

Tethering your Android phone basically turns it into a mobile hotspot, allowing you to funnel a 3G or 4G internet connection from your phone into your PC or laptop via USB. As you might expect, phone carriers brought the hammer down in an effort to stop users from getting around the fees they charge to normally allow you to do this.

In this tutorial, we learn how to solve the circumference with pi. You will first need to know what to equation to figure out circumference is. C= (pi) x (diameter) is what the equation is. So, to figure out the circumference, first figure out what the diameter is. Once you have this, multiply it by pi. This will probably be on your calendar as a symbol, but you can also type it in as 3.14. After you multiply these two numbers together, the number you get is what the circumference is. Make su...

This is a video tutorial on how to create a mouseover link (button) in Flash. According to the author, this is an extremely easy task, the first step of which is to select the file in which the button is to be made. Then, on the extreme right-hand side, in the middle of the column of icons, one has to choose the button icon, and then select which shape and color of the button one would prefer. The text is then typed in the text box selected over the button, and converted into a symbol by pres...

The beehive is a woman's hairstyle that resembles a beehive. It is also known as the B-52, for its similarity to the bulbous nose of the B-52 Stratofortress bomber. It originated in the USA in 1958 as one of a variety of elaborately teased and lacquered versions of "big hair" that developed from earlier pageboy and bouffant styles. The peak of its popularity was in the 1960s, and it was especially popular in the United States and other Western countries. The beehive remains an enduring symbol...

If you are interested in learning more about feral cat colonies and what you can do to help, let our expert explain how you should interact and what you should do with these wild cats. In this video series you will learn how to bait and trap feral cats for spaying and neutering.

If you’re camping outdoors, you’ll probably need to know how to make a campfire at some point. Fire is an important tool to have for cooking food and purifying water, for warmth and light, and for protection from wild animals at night. In this video series, learn the proper way to make a safe, long-burning campfire. Our expert, Brian Rajchel, will show you how to choose the right area in your campsite for the fire, how to build a fire pit, how to start a fire without matches, and how to prope...

I must admit, upon learning that the NFL was broadcasting the contest between the New Orleans Saints and Chicago Bears on CBS, Amazon Prime Video, and Nickelodeon, the latter was the only option I wanted, purely for the novelty of the experience.

In 2018, Niantic unveiled its in-development augmented reality cloud platform for smartphones, the Niantic Real World Platform. A demo showed Pikachu and Eevee cavorting in a courtyard, darting in front of and behind potted plants and people's legs as they walked through the scene. This would be the future of Pokémon GO.

Thanks to the COVID-19 virus, the whole country is staying home. That means no dining out, no going to bars, no live music, and, sadly, no movie theaters. While you might think that means you'll have to wait to see movies like "The Invisible Man," "Emma," and "The Hunt," think again. Because of the pandemic, you'll be able to watch these movies on your phone earlier than ever.

While Apple's AR wearables development continues clandestinely, its mobile ecosystem is laying the foundation for the software side of its smartglasses, with Apple Arcade serving as the latest example.

Samba can be configured to allow any user with write access the ability to create a link to the root filesystem. Once an attacker has this level of access, it's only a matter of time before the system gets owned. Although this configuration isn't that common in the wild, it does happen, and Metasploit has a module to easily exploit this security flaw.

Apple's ARKit has built a considerable lead in terms of features over Google's ARCore, but Google's latest update to ARCore adds a capability that makes the platform a bit more competitive with ARKit.

Augmented reality gaming pioneer and Pokémon GO mastermind Niantic is putting the pieces on the gameboard to prepare developers and gamers for the launch of its AR cloud platform.

I've been using the Galaxy Note 10+ as my daily driver for a while now. I love it, but as with any phone, it loses its pizzazz after a while. But since it's an Android phone, there's always a way to add fresh features and functionality to the UI.

Developers and enterprise customers chomping at the bit to get their hands on HoloLens 2 may not have to wait much longer, as Microsoft passed one of the remaining hurdles needed to release their new tech into the wild.

Niantic's Harry Potter: Wizards Unite offers players an augmented reality look into the world of witchcraft and wizardry. The Wizarding World and Harry Potter novel series is full of unique and interesting characters, which is why it makes sense that Wizards Unite offers you to take the role of one of three "Professions" — Auror, Magizoologist, and Professor. The question is, which one do you pick?

Imagine an Instagram feed filled with a wild array of vivid color. Beautiful right? But when you look at the photos in your iPhone or Android phone's albums, they're all just too dull to pull off that dynamic look. There's no doubt that colorful images are more eye-catching than dull ones, so how do you get your photos to overflow with vibrant color? The answer: Add it in post.

It's confession time. Through a couple of sources, I managed to get an early look at the HoloLens 2. But I was sworn to secrecy, and I take my tech oaths seriously (shame on you, leakers).

Great news if you're looking to upgrade to either the S10e, S10, or S10+. Samsung has a trade-in program that's offering potentially massive discounts of up to $550 if you preorder one of their flagships right now — but only for certain phones.

The North remembers...that smartglasses are the future! Game of Thrones jokes aside, the smartglasses startup opened its doors, and we visited its Brooklyn store to get our hands the consumer-focused Focals smartglasses.

This week, we continued our NR30 series highlighting the leaders of augmented reality space by profiling the venture capitalists and strategic corporate investors that sustain the industry.
After months of beta testing, Siri Shortcuts has finally arrived on all iPhones that support iOS 12. Anyone familiar with Workflow will understand how useful it is to set custom Siri commands for your favorite apps. Of course, your favorite apps need to be compatible with Shortcuts in order to take advantage of the new feature.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

Apparently, it's Google Week for the augmented reality business. Now that ARCore has a firm foothold in the app ecosystem, Google is making a case with educators and marketers that the apps should have a place in schools and campaigns, and the company is also encouraging developers to learn how to build apps using ARCore.

Google Lens is a fantastic addition to Google Photos for Android and iOS that allows your smartphone to identify a number of things in your pictures, like landmarks and contact info. Using this power, you can even find out how to buy almost any product you've taken a photo of — you don't even need the barcode.
Samsung Internet offers excellent features that enhance the mobile web browsing experience, often through its extensions. A QR code scanner, ad blockers, tracker blockers, and more work directly in the browser, so you can do exactly what you want to do on the web.

Samsung's big reveal of the Galaxy S9 and S9+ at Mobile World Congress revolved around its "reimagined" camera and augmented reality capabilities.

IFTTT is an application that allows you to automate certain tasks on your iPhone or Android. It can communicate with a myriad of apps and services on your phone by creating applets that perform actions automatically — actions you'd normally have to do manually. Finding those applets, however, can be a little difficult.

The internet is constantly under siege by bots searching for vulnerabilities to attack and exploit. While conventional wisdom is to prevent these attacks, there are ways to deliberately lure hackers into a trap in order to spy on them, study their behavior, and capture samples of malware. In this tutorial, we'll be creating a Cowrie honeypot, an alluring target to attract and trap hackers.

How can a drug used to treat cancer be effective against viruses, too? The answer lies in the drug's shared target — specifically, cellular components that control the activity of genes. A new research study showed that one such type of drug, histone methyltransferase inhibitors used in cancer clinical trials, has activity against herpes simplex virus, too.

For a company more associated with debugging computer programs, Google's parent company, Alphabet, is making a name for itself by taking on the real thing — mosquitoes.

Malaria is a massive worldwide health problem. The Centers for Disease Control and Prevention estimate that 212 million cases of malaria occurred worldwide in 2015 and 429,000 of the infected people died.

For younger children, a day at the playground is not complete without some sandbox time. Long a favorite of children and parents, sandboxes could also be sheltering dangerous pathogens.

It is not just a bad summer for ticks — it has been a bad decade for the spread of tick-borne infections. New surveillance from the CDC reports rapid expansion and increase in cases of babesiosis, a sometimes life-threatening disease, in Wisconsin.

Everything from disposed of drugs to hormones and disease-causing bacteria — anything that is rinsed or flushed down the drain — can contaminate wastewater.

Move over whole wheat — white bread may be back in style after a new study shows that it may be your gut microbes that decide what kind of bread is best for you.

As if being pregnant did not come with enough worry, a new study found that certain antibiotics are linked to an increased risk of spontaneous abortion, or miscarriage — a terrifying finding for any expectant mother.