How To: Disable User Account in Windows 7
This video will help you how to disable user account in windows 7. This is very easy to employ. Watch the video and follow all the steps to disable user account in your PC.


This video will help you how to disable user account in windows 7. This is very easy to employ. Watch the video and follow all the steps to disable user account in your PC.
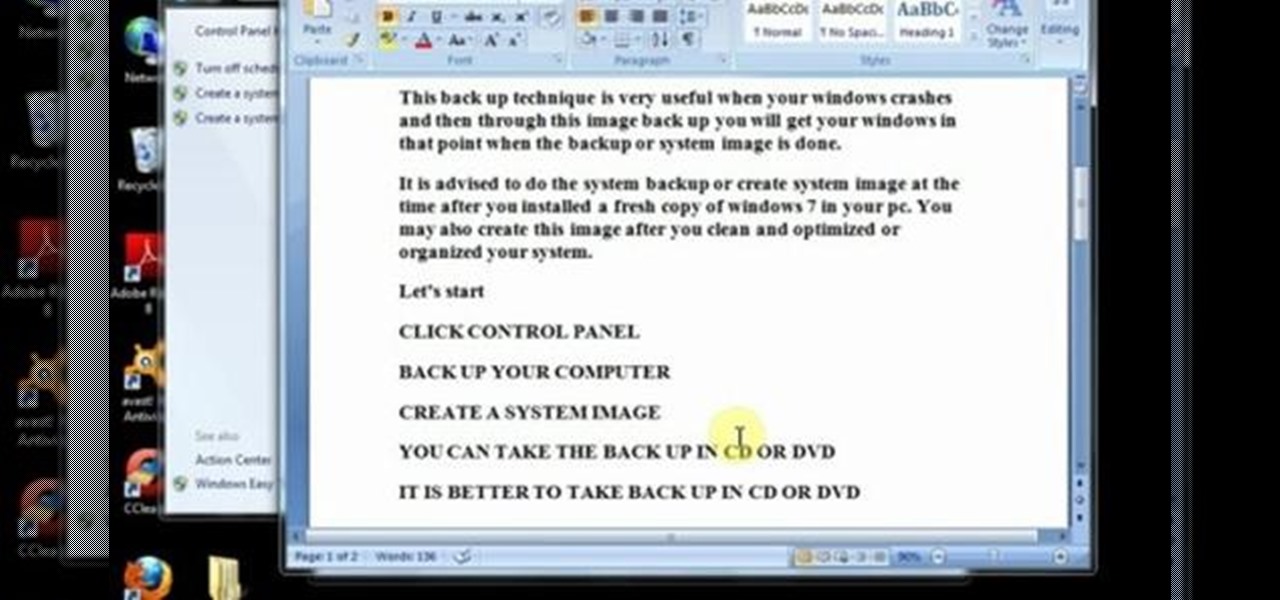
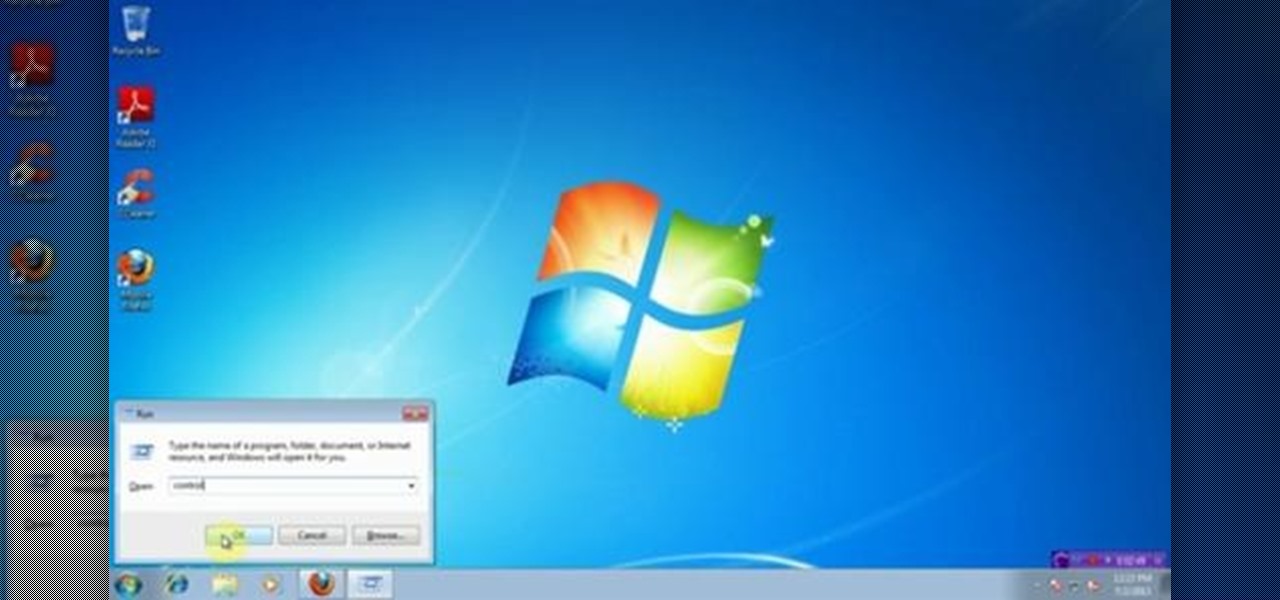
This video will help you how to create system image backup in windows 7. If you create an image of your system you could restore after crashes. Watch the video and follow the steps to create system image backup in your PC.

This video will provide an idea how to set, change and remove administrator password in your computer. Watch the video and follow the steps to change administrator password in windows.
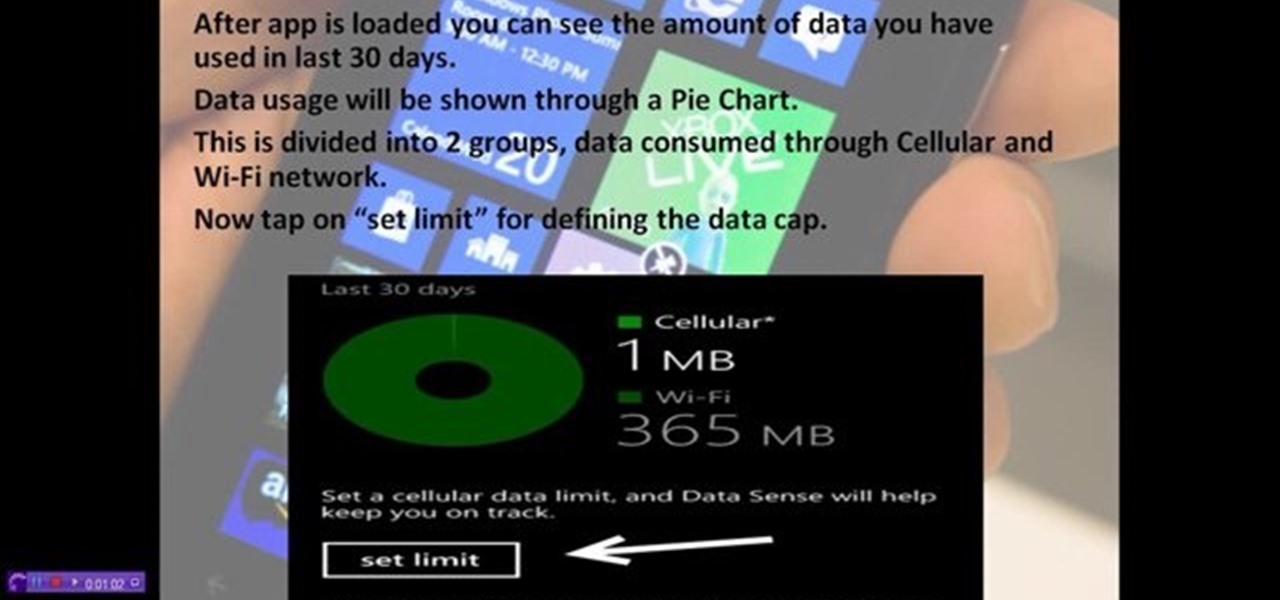
How to control and limit your internet usage in your windows 8 phone? You may want to restrict your internet usage and want to set limit for apps also. If you set your usage limit internet will stop automatically after reaching the limit. Follow the video to employ in your own phone.
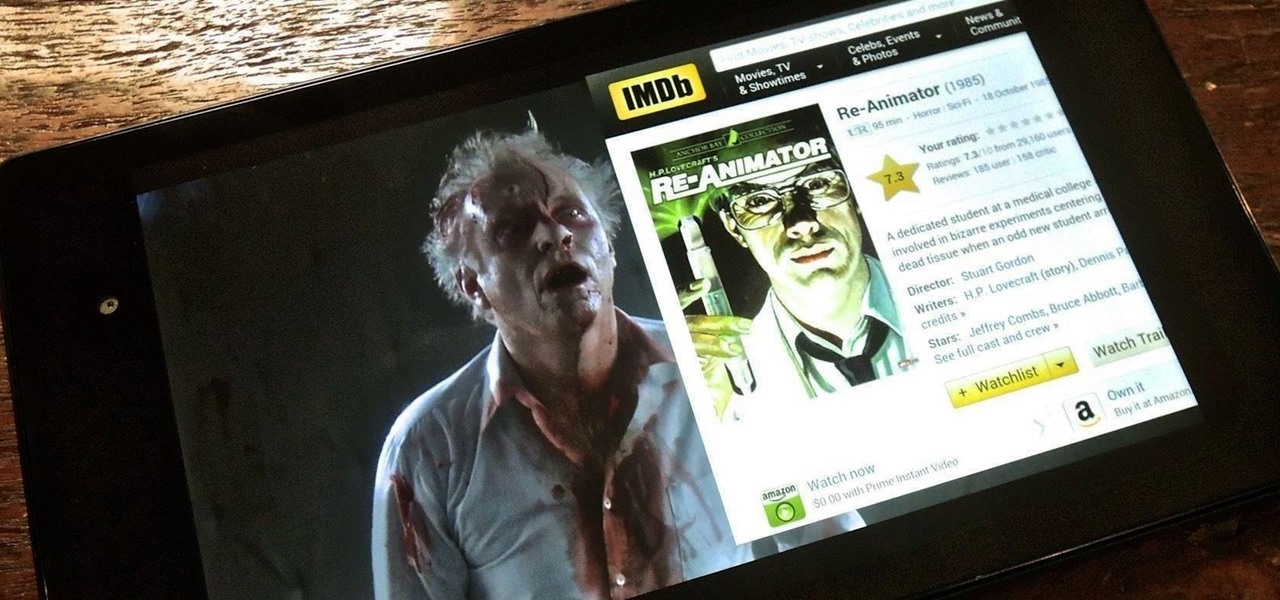
Efficiency is one integral attribute that I need from my Android device. I want to be able to multitask like a maniac and do things on the fly. While multitasking itself is nothing new, actually being able to watch Netflix while scrolling through IMDB at the same damn time was reserved mainly for newer Samsung-ier devices.
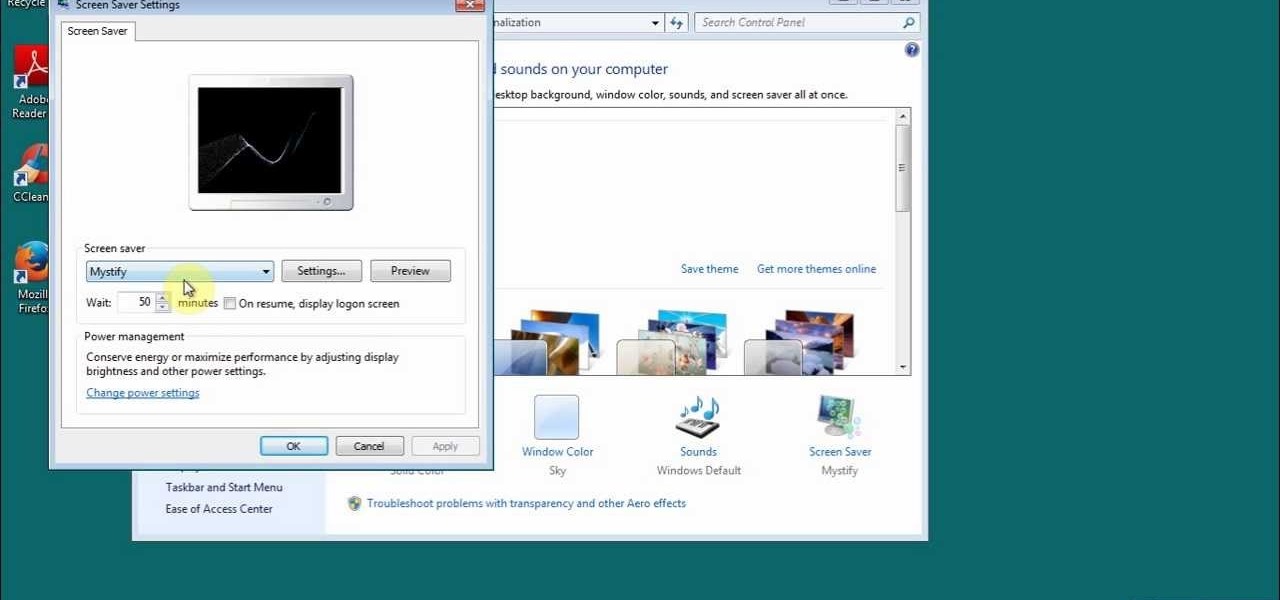
If you want to learn how to set up a photo slideshow screensaver in Windows 7, just follow all the steps from this video.
When this problem occurs most Windows users feel desperate because it can happen' at any point, every 10 seconds, minutes, hours - you name it and they don't know how to solve it.
It is typical to share video and files for those who are not friendly with windows 8. But with the help of this video you can share all which you want.
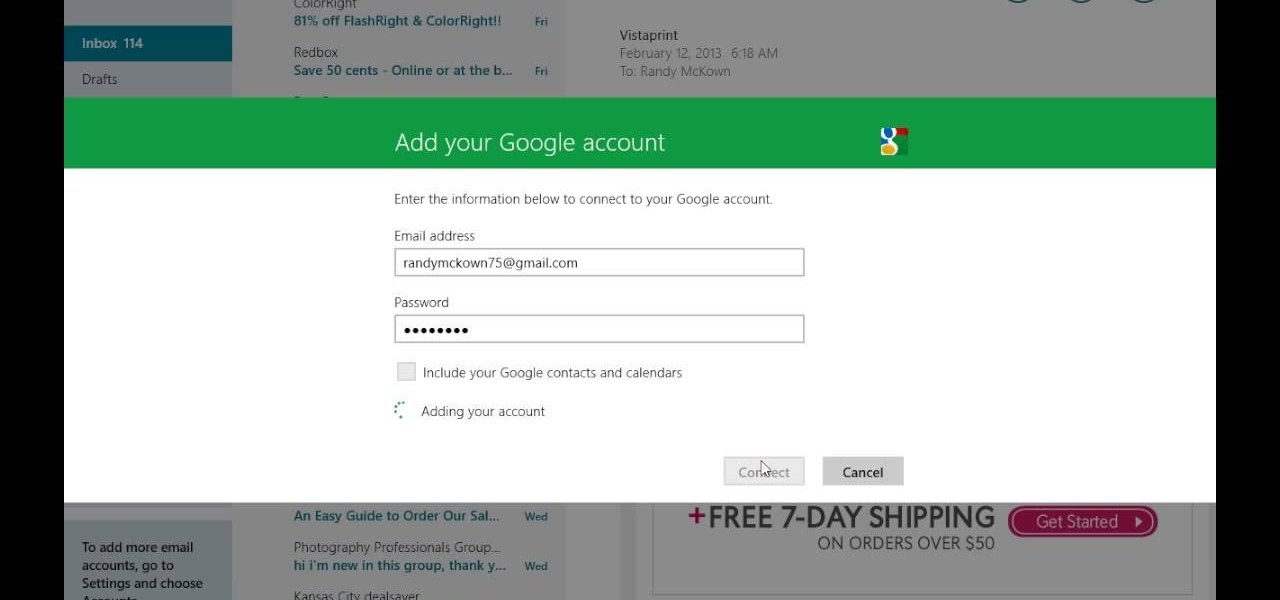
With the help of this video you can easily setup your mail apps in windows 8. Just follow the steps, shows in this video. We are thankful to Randy Mckown for this video.

This video demonstrates all the steps for how to install the popular Firefox browser in Windows 8. It will guide you throughout the final installation procedure.
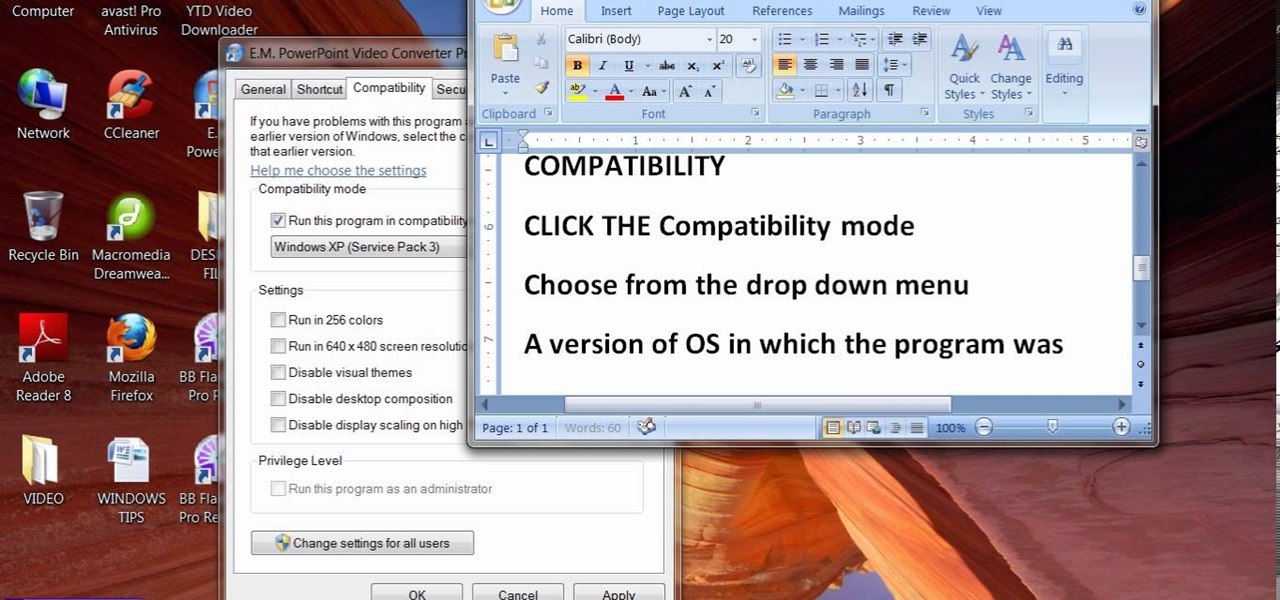
When people upgrade their windows few software don't run on new OS. How to fix the problem? Setting program compatibility solves the issue. Watch the video we made and submitted earlier in You tube.
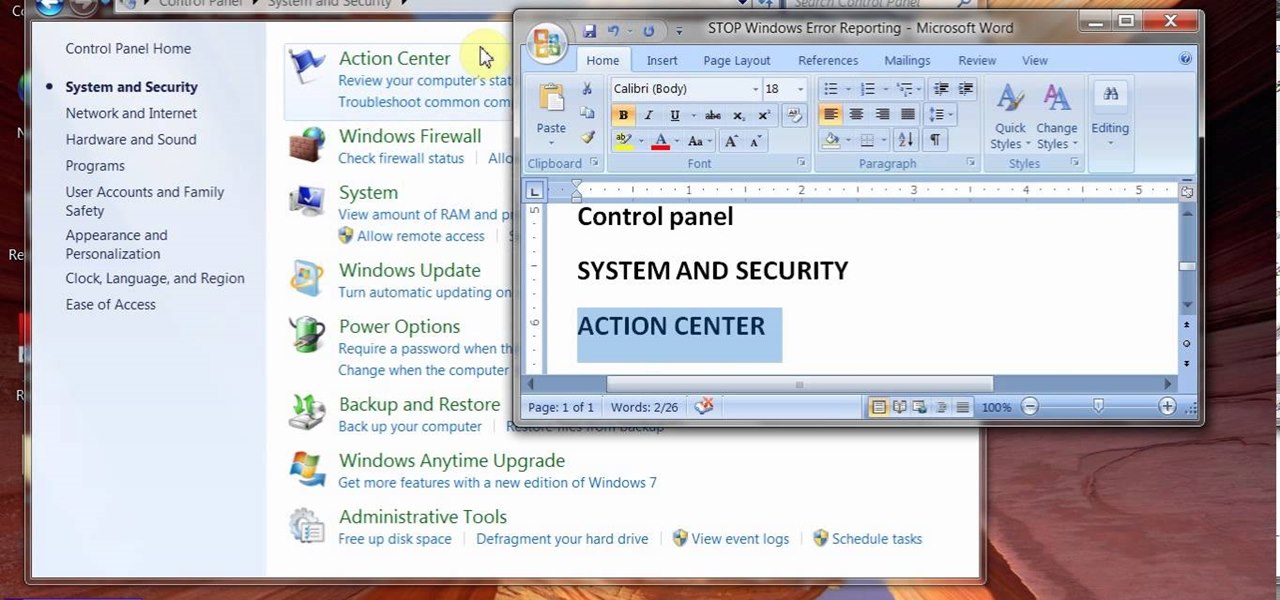
Error reporting in windows 7 sometimes create problem for users. They want to stop or disable this error reporting. Here are the steps to follow for stopping Error Reporting.

Using a second monitor is great for multitasking, especially if you tend to max out your computer's brain power on tons of simultaneously running apps that you want to see, well, simultaneously. That second screen becomes more like a lifesaver.

Archive files are great for portability and saving space, but a lot of people don't know they can also be encrypted. There are a lot of archiver programs out there, but most of them can open a file that's been encrypted using other software, as long as you're using a recent version.

PowerShell is an essential component of any Windows environment and can be a powerful tool in the hands of a hacker. During post-exploitation, PowerShell scripts can make privilege escalation and pivoting a breeze, but its execution policy can put a damper on even the best-laid plans. There are a variety of methods, however, that can be used to bypass PowerShell execution policy.

Who doesn't love cartoons? Whether you want to take up a creative hobby over the holidays, learn animation for an exciting new side hustle in 2021, or buy the dream gift for the person in your life who loves all things animated, this deal is one to take advantage of today. Right now, you can pick up The Ultimate Cartoon Animator 4 Pro: Windows Bundle — with an amazing 74% discount — for just $49.99 (regular price $196).
One of the biggest reasons to go with an iPhone over an Android device is Apple's interconnectivity. iPhones, iPads, and macOS devices are all connected in a way that allows seamless transition between devices. Android lacks such a feature by default, but that isn't the end of the story.

Imagine for a moment that a VPN is like putting on a disguise for your computer. This disguise works to change your IP address, secure your traffic with encryption, and mask your location to bypass regional restrictions. This makes it a helpful tool for both whistleblowers and journalists. VPNs are also built into the well-known Tor Browser.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

These days, there is hardly a place in America that doesn't have access to the internet. But with web usage fees and ridiculous cell phone provider contracts, sometimes it's still necessary to go a little DIY when it comes to staying connected.

Photobombing, the act of covert sabotage on a photographer and unsuspecting subject, can be a terror. This malicious and disingenuous art form has steadily grown since it first received significant coverage in 2009.

There's nothing more inherently awesome than looking up into the stars and wondering WTF is really out there. Outer space is one of those rare items that a Google search cannot provide all of the answers for.
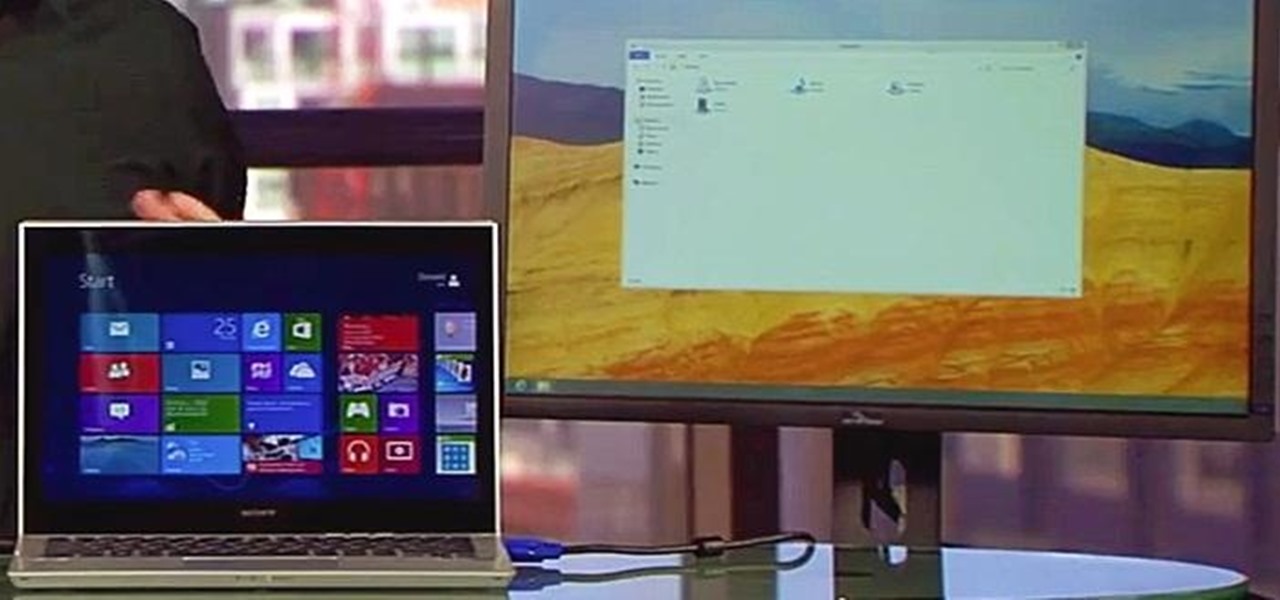
The new Windows 8 operating system pushes the Metro interface hard, but not all of your apps will play nicely in Metro, which means you'll need to resort to the traditional desktop environment for some of your favorite programs. As a result, it has left many users picking between the two—Metro or traditional? Fortunately, there's a way to run them both simultaneously with the use of second monitor. In the video below, Donald Bell of CNET explains how you can run both interfaces simultaneously...
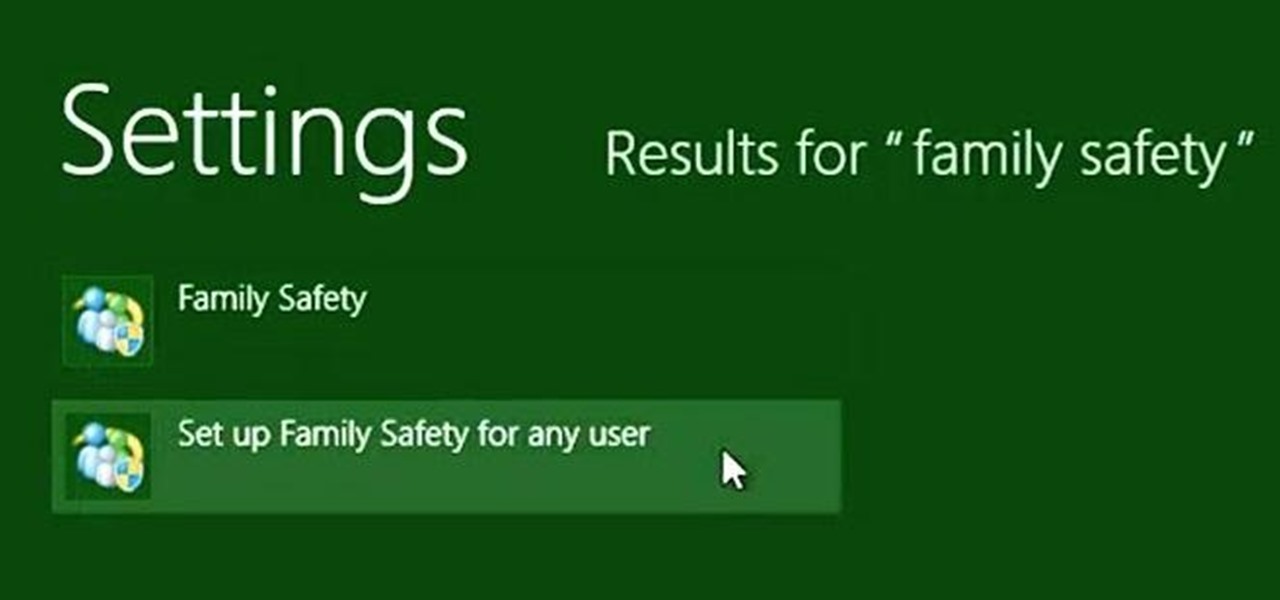
The internet is full of information and entertainment, but if you have children, you might want to put a cap on what sites they have access to. While it may be a free world out there, it doesn't mean that little Mickey should be free to roam the web during his downtime (or uptime, if you know what I mean).

One of the most played-up features of Windows 8 is that it's so much faster than previous versions. So fast, in fact, that Microsoft had to change the way that users access the BIOS because 200 milliseconds just isn't enough time to hit the right key. It may take some getting used to, but it's probably a welcome change for most people, considering that the "right" key is different depending on what type of computer you're running the OS on.

Security researcher Nadim Kobeissi has discovered that the Windows 8 SmartScreen feature, meant to screen downloads for malicious software, actually reports the data about which applications users are installing to Microsoft. He also says that "the Microsoft server is configured to support SSLv2 which is known to be insecure and susceptible to interception." The two main concerns are the ability of law enforcement to subpoena Microsoft for the information and of hackers to intercept user data...
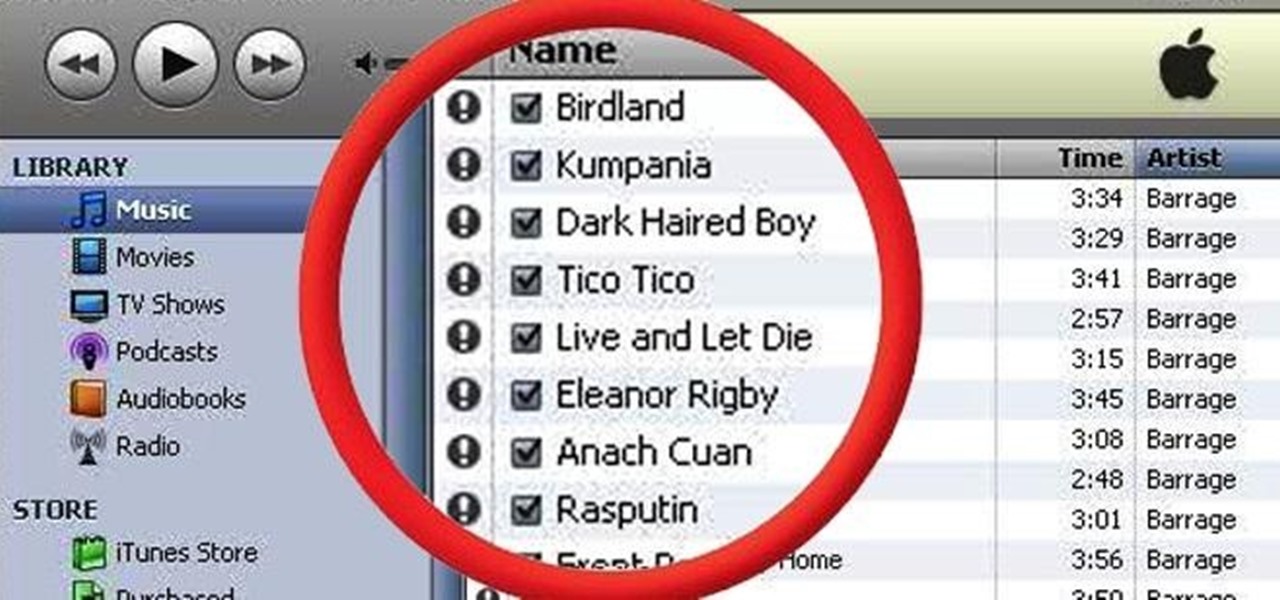
If you've ever mistakenly moved your music files around without relinking them in iTunes, you might now be noticing that you have a long list of tracks asking you to relink them. You could go through them one by one, redirect them to the new file location, then delete any copies. Or you could try to track them all down and delete the old references. But come on, who wants to spend that much time when you can clean up your library using this clever method using only Notepad on your Windows com...

While it may not sound scary right off the bat, Blue Coat Systems now has an intermediate certificate authority. If you don't know what a certificate authority (CA) is, or who Blue Coat is, who cares, right? But you should... whether you use Mac or Windows.

This is my first article on here, it's based off of a project that I'm working on at school which is on three ways to bypass windows user password's. If all goes as planned and you all would like I'll work on part two and part three and post them as soon as I can. I do have to give credit to Puppy Monkey Baby and The Defalt, both of whom are my classmates at college and have helped me with writing this article.

Google's latest Nexus device is big, bold, and beautiful—and now it's got root. Thanks to some quick work by legendary Android developer Chainfire, the Nexus 6 already had a clear-cut root method before most stores even had it in stock.

Whether or not you believe that the government is snooping around in our private emails, texts, and phone calls, it wouldn't hurt to protect ourselves a little better in the digital realm.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

"You can never know too much" is a saying you hear all the time. Funny thing is, I have no idea where it originated, and neither do most of the people who continually say it. Nevertheless, it's a statement that very few would argue with.

TouchDevelop is a browser-based programming tool that allows anyone to build your own Windows 8 apps directly from any touchscreen device, including iPad, iPhone, Windows Phone, Android, PC and Macs. Once the script is created and the app proves to work, it can be placed in the Windows Store for free or purchase.

It's easy to run Kali Linux from a live USB on nearly any available computer, but many publicly accessible laptops and desktops will be locked down to prevent such use. School, work, or library PCs can be secured with a BIOS password, which is often an easily recovered default password. Once you have access, though, you can use a USB flash drive to run Kali live on any PC you find.

Visualization is one of the obvious commercial applications for technology such as Microsoft's HoloLens. The ability to see the assets of a project in different scales—from micro to larger-than-life—with a quick air tap will play a large part in the coming augmented reality revolution. Whether the assets are art for a game, interior design, raw financial data, or architecture, data visualization will play an important role in the future. This is due, in part, to our ability to absorb informat...
Google Play Music has been my go-to music service ever since its release. The free cloud storage for 50,000 songs and full access to Songza-powered radio stations make it a great music app, even without the $10/month streaming service.
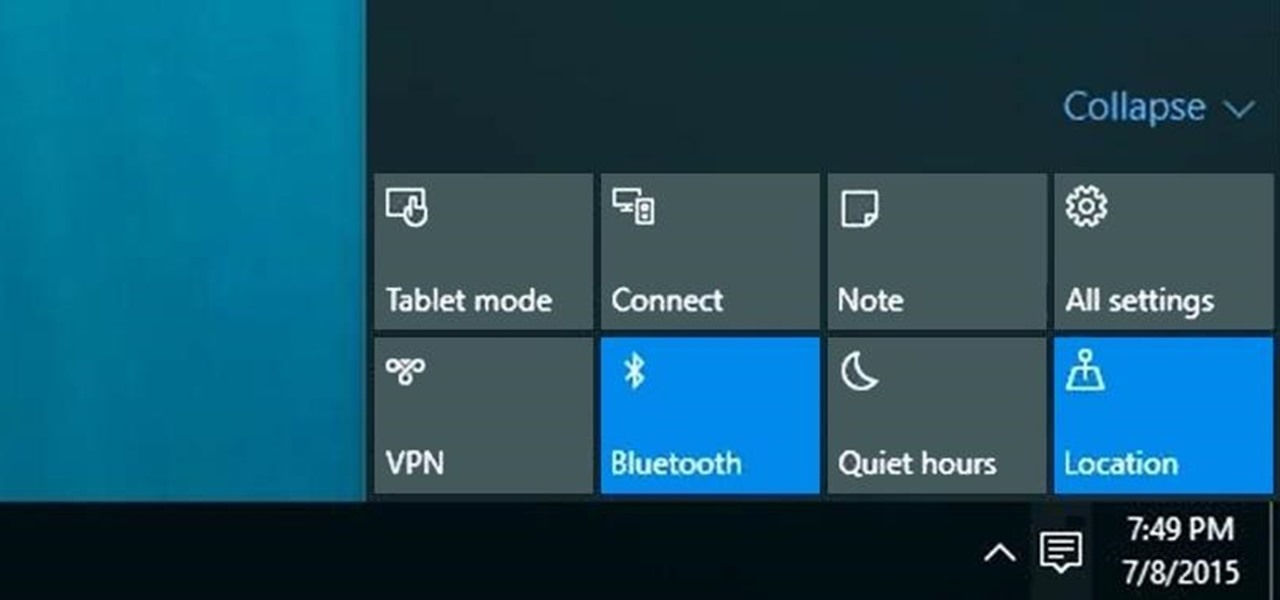
The world's most commonly-used desktop operating system is getting a huge makeover in the form of Windows 10. While there are many sweeping changes in this new version, some of the smaller tweaks may prove to be the most useful.

On Thursday morning, May 28th, Google announced an upcoming version of Android—and within a few hours, a preview build of this so-called "Android M" release was made available to select Nexus devices.