
News: Our Writers' & Editors' Must-Have New Phone Accessories
It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.


It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.
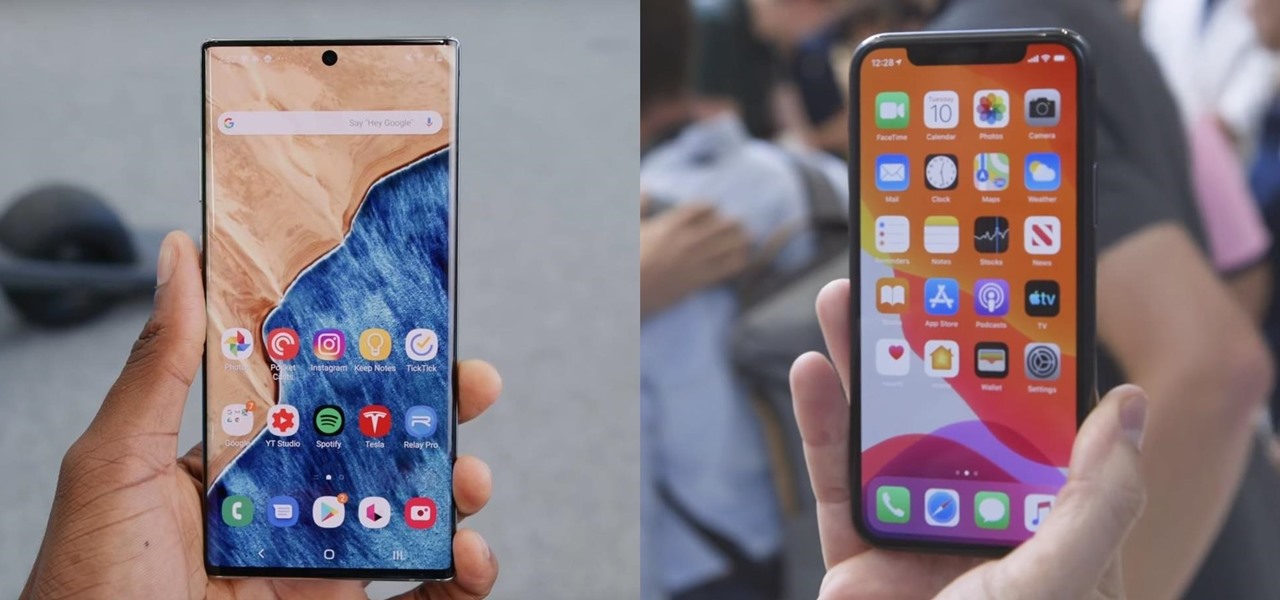
Samsung decided to shake things up this year. In the past, the Galaxy Note series was one large phone. This year, it's two phones: the Galaxy Note 10 and Note 10+. So for the first time in a long time, we can compare the latest standard iPhone, the 11 Pro, to a Galaxy Note device.

iPhones with Face ID all retail for at least $999, which many still believe is just too much for a smartphone. But that's okay, because Apple just introduced the iPhone 11 for roughly $700. It's not necessarily the best value, though, because the iPhone 11 already has some stiff competition in this price range.

After months of back and forth, ZTE is finally making their return to the United States. The last phone the Chinese company released here was the Axon 7 Pro, a low priced flagship phone that competed well against the OnePlus 3 and 3T at the time. Its successor is the Axon 10 Pro, which adopts the same strategy.

For years, Samsung has been behind the curve when it comes to fast charging. Up to the Galaxy S10, most of their phones used the very slow Adaptive Fast Charging system. Whether it was the Galaxy Note 7 fiasco or some other reason, Samsung has been reluctant to push the charging envelope. Until now.

Every fall, we can expect a few things: leaves changing colors, cooler temperatures, and Samsung and Apple releasing new phones that fanboys and fangirls will argue about until the following year. This year, Samsung is mixing it up, releasing two phones in the Galaxy Note series. Let's see how the larger phones compare.

The PlayStation 4 has been around since 2013 and has brought with it countless game releases since then. One thing that hasn't changed, though, is the strict device restrictions on the PS4 Remote Play feature for streaming your games. The capability has always been there, but you still had to have an iPhone or Sony smartphone to get the best experience possible — until now.

In recent weeks we've talked about the growing trend of smartglasses makers moving the brains of their devices to smartphones, and now a veteran of the space has joined that movement.
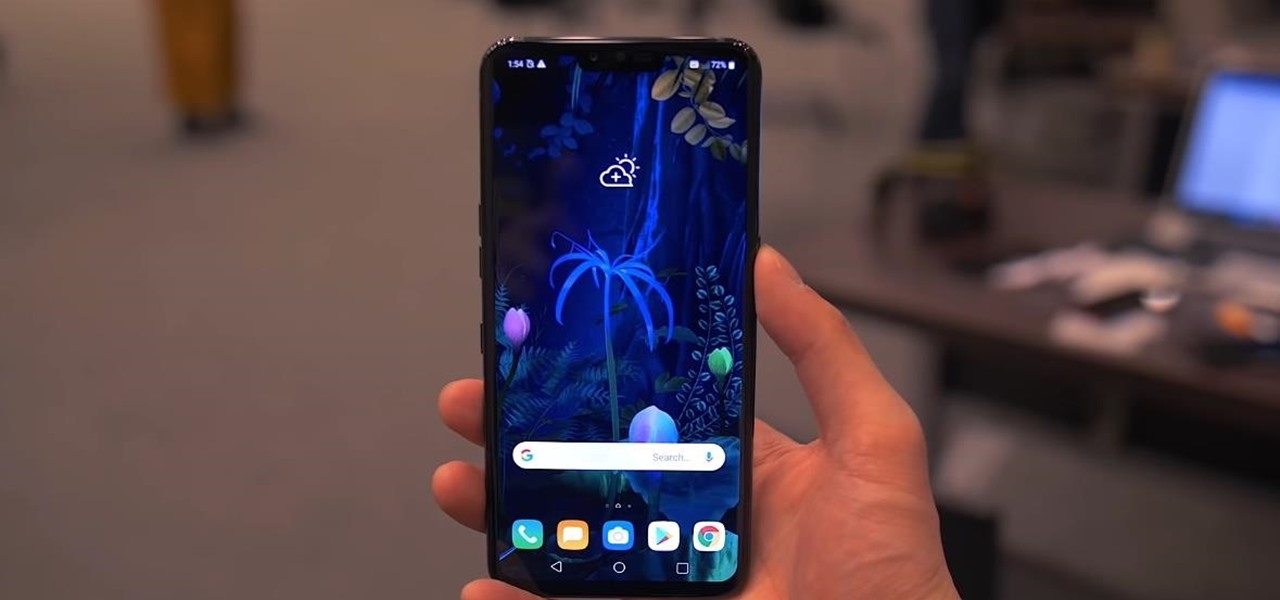
Similar to last year, LG is mixing up its releases. Instead of the G series in the first half of the year and the V series in the second half, LG is releasing both heavy hitters together. However, unlike last year, this is a true upgrade from its predecessor, the LG V50 ThinQ 5G.
After months of waiting, it looks like HMD has finally answered the call. Nokia's parent company is finally releasing a true flagship phone — one that isn't just an enhanced version of a previous phone and actually brings something new to the table. That phone is the Nokia 9 PureView.
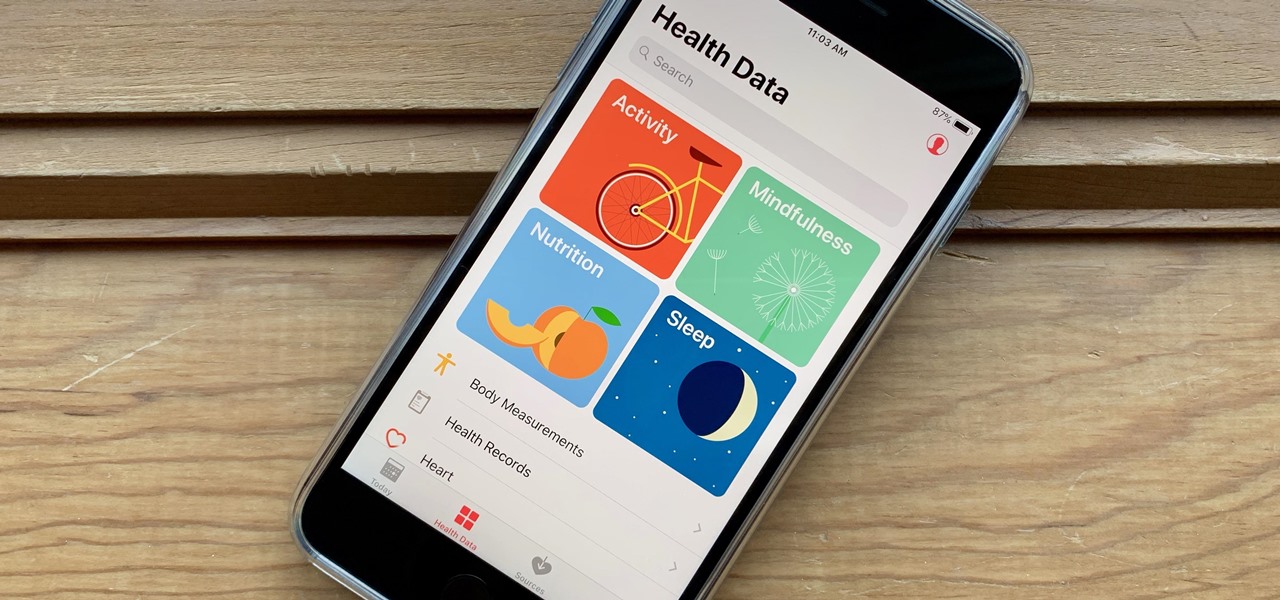
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

Publicly, things have been pretty quiet over at Meta, the augmented reality headset and software startup based in Silicon Valley. But that doesn't mean that the company doesn't have a few strong opinions about the state of AR in 2018.

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

The iPhone XS, XS Max, and XR aren't the newest devices from Apple Inc., but all three have a serious problem in Messages. When sending a friend an SMS/MMS text rather than an iMessage, the phrase "Number changed to Primary" appears in front of every message. What gives? If this issue is driving you mad, there are a few tricks that may exterminate the bug until Apple gets around to issuing a patch.

Late last year, we got a little surprise from Razer. The gaming company released its first smartphone, and as expected, it targeted gamers. Branded as a gaming phone, it started a trend which several other companies followed soon after, including ASUS, Xiaomi, and even Samsung. So as you can imagine, many are excited about its successor.

Android does a great job at multitasking. Split-screen mode and picture-in-picture are terrific at letting you manage more than one app at a time. But there are some limitations. For instance, when you're playing a video and you open a second video in split-screen, the first one pauses. Thankfully, Samsung has a fix for this.

Hackers and makers are often grouped under the same label. While hackers draw on computer science skills to write programs and find bugs, makers use electrical engineering to create hardware prototypes from microprocessor boards like the Arduino. We'll exercise both sets of skills to program a $6 NodeMCU to display the status of a Wi-Fi link via an LED, allowing us to monitor for jamming attacks.

The hype train that left the station years ago has reached its first stop, and now we finally have access to the Magic Leap One, the device many have claimed would revolutionize the augmented reality space at launch. But is that really true?
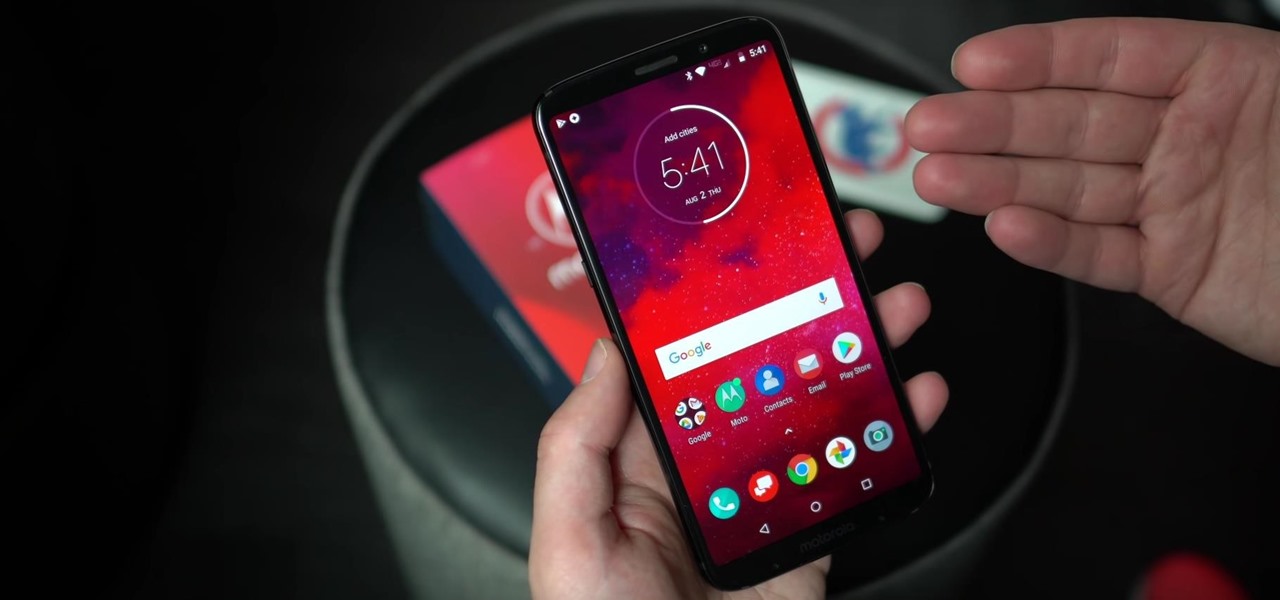
In 2018, Motorola is no longer the same brand that introduced the world to the Motorola Droid. The once iconic company is now part of the "Others" group, scrambling for fifth place. The newly-announced Moto Z3 perfectly embodies their current state with competitive specs ... if it came out last year.

When you want to post a breathtaking landscape or picture-perfect portrait that you just took with your DSLR camera to Instagram, Facebook, or some other social platform, there's an easy way to do so — even if you don't have a computer handy, which is typical when you're out and about.

While the security behind WEP networks was broken in 2005, modern tools have made cracking them incredibly simple. In densely populated areas, WEP networks can be found in surprising and important places to this day, and they can be cracked in a matter of minutes. We'll show you how a hacker would do so and explain why they should be careful to avoid hacking into a honeypot.

If preorder delays are any indication, the iPhone X certainly has some buzz. But does the X have the quality to support that buzz in the long run? After all, a $1,000 (or more) iPhone feels more like an investment than a smartphone purchase. The question on any prospective buyer's mind should be, "Is this thing worth it?"

Nvidia's decades-long development of graphics processor units (GPU) for PCs has given it a major leg up in the driverless space.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

The Raspberry Pi loads an operating system from whatever SD card you insert, allowing you to keep different operating systems on separate SD cards depending on which OS you wish to run. A tool called BerryBoot cuts down on the number of SD cards needed by providing the ability to boot multiple operating systems from a single SD card, similar to Boot Camp for Mac computers.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

We fight cancer in a variety of ways, but no matter whether drugs, biologics, or our immune cells are part of the battle, they can do a better job fighting back cancer if we can help them find the tumors.

A disease called "citrus greening" has devastated and permanently altered citrus production in the United States, but a vaccine that could protect orange trees may be part of a winning strategy to beat the bacteria that is killing the trees.

Android has several features built into the platform that improve user experience but require extra attention to prevent a security breach. By modifying these settings, you can drastically reduce the possibility of someone exploiting your device or intercepting information.

Bitcoin, the decentralized cryptocurrency notorious for its status as the currency of the dark web, seems to be shedding its shady past and is now enjoying soaring highs not seen since 2014. The highly volatile online commodity reached parity with an ounce of gold back in March amid speculation of a pending ETF approval from the Federal Trade Commission. Since then, Bitcoin has doubled in value and analysts predict a bitcoin could reach $100,000 in value in 10 years.

At this point in our series on creating a customized hacking container, you should be able to use Docker to save and retrieve customized instances of Ubuntu from your own machine. Make sure to revisit part one and part two if you need a refresher.

Mobile gaming still isn't on par with video game consoles or PCs, but we've come a long way from Snake. Modern games running on the latest smartphones boast downright impressive graphics—even more so when you consider how compact the system has to be in order to fit in people's pockets.

The Oculus Rift is finally shipping to customers in more than 20 countries, and we're getting a good idea of how the device holds up from the initial reviews. You'll see some common threads throughout: along with an impressive virtual reality experience, the device is very comfortable with a solid design.

Good day people, today we will examine some basic, for some people well-known attacks, also we will take a look at some advanced attacks.

Welcome back, my greenhorn hackers! The Holy Grail of any hacker is to develop a zero-day exploit—an exploit that has never been seen by antivirus (AV) and other software developers, as well as intrusion detection system (IDS) developers. In that way, you can exploit systems with your newly discovered vulnerability with impunity!

If you have no desire to get a separate Mac desktop computer, but want to either supersize your laptop's screen for gaming or need to get additional screen real estate while you work, then connecting your MacBook, MacBook Air, or MacBook Pro to an external display is the right call.

There is something so satisfying about dipping your spoon into a perfectly smooth slice of cheesecake. There is something a bit less satisfying about it if the top of the cheesecake is cracked and cratered.

In my opinion, biscuits made from scratch (American biscuits, that is, not the British kind) are just flat out amazing, but I'm typically too lazy to actually make them. That's why I always have a can/tube of refrigerated biscuits on hand. They're not only good for quick biscuits and gravy or as a simple side of bread, they can be used for so much more—sweet or savory!

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

Why did I write this when they're tons of scanning tools available.