A while back, I wrote review of my favorite hacking movies of all time. Two of my key criteria were; (1) how realistic was the hacking, and (2) are the hackers portrayed as the "good guys." This past winter, a new hacker movie was released, appropriately named Blackhat starring Chris Hemsworth (from Thor fame) as a blackhat hacker who is released from prison to stop a notorious and destructive hacker that only he can stop. Although the movie did very poorly at the box office, I thought it was...

There's nothing more jarring than the sound of your morning alarm. Even hearing it on others' phones, hours after your own abrupt wakeup, can cause you to flinch in fear. Though we depend on that shrill sound to get up each morning, it's actually better to wake up naturally—so don't even think about hitting that snooze button.

Oops... did you forget to connect to a Wi-Fi network before streaming HBO GO on your iPhone? While those episodes of The Wire may have been absolutely life-changing, your three-digit cellular bill is definitely going to hit you a little harder.

Sitting in a cubicle and never seeing sunlight during the workday is unpleasant to even think about—and sitting in a flourescent-light cube can have terrible effects on both our work performance and overall attitude. Yet there are ways to counteract the effects of cubicle sitting, even if you can't sit in a sunny office or work from home.

We all carry a bit of anxiety around with us. Is our boss still annoyed because we could barely stay awake in yesterday's pre-dawn meeting? Will our friend hate us forever because we forgot to call them back two weeks ago? Whatever worries pop up in your mind, whether they're monumental or insignificant, it can be hard to quiet those nagging voices, but you can shut down your nonstop mind with a bit of relaxation, distraction, and action.

Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

French toast is one of those things that everybody kind of knows how to make, but few people know how to do really well. And while the dish originally does hail from France (its original name, pain perdu, means lost or wasted bread), it has become a beloved American breakfast dish.

Welcome back, my aspiring hackers! Many of you have installed Kali Linux as a virtual machine (VM) using VMware or VirtualBox, while others have installed Kali (or BackTrack) in a dual-boot system. The drawback to installing these hacking systems as a VM is that it then requires an external wireless adapter (your wireless adapter is piped through the VM as a wired device, eth0), but it makes for a great place to test your hacks while honing your skills.

Can you cook a steak or salmon filet that's straight out of the freezer and get good results? Ordinarily, I would say no. Usually your steak ends up a sad grey mass fit only for the family dog and the fish is burned on the outside with an icy, undercooked center.

Watermelon is the perfect snack for hot temperatures. It's hydrating, crisp, and refreshing, especially when it's chilled. Yet some people aren't content with leaving a good thing alone, which has given us many watermelon-based innovations, some great (vodka-filled watermelons) and some delightfully strange (square watermelons).

Whisking liquids seems somehow quaint, especially since there are good, cheap devices out there like immersion blenders and hand mixers that can whip cream, turn egg whites into meringue, and mix batters for you.

Bees are the key to pollination and healthy vegetation, and wasps may help by assisting in pest control, but despite their benefits in the world, they're still a real pain in the ass if they're in your face.

Even though I often end the workday exhausted and just want to wrap rotisserie chicken parts in a store-bought tortilla and shove it in my eating hole, I generally try and take a couple of minutes to warm up said tortillas before I begin my meal. But if you're starving, do you really need to take the time? Do warm tortillas really make that much of a difference?

Are you searching for a homemade cat repellent solution? This article will cover natural indoor and outdoor deterrents for every scenario where cats are causing trouble. The first part will cover home remedies for training cats to stay away from furniture and other restricted areas inside your house. The second part will cover outdoor repellents for keeping cats away from your garden, plants and yard. Step 1: Indoor Repellents for Training Cats

The lengths people will go to for a grilled cheese sandwich are amazing. They'll use irons, wafflemakers, or whatever appliance that produces enough heat to produce the perfect combination of golden, grilled bread and oozy, melting cheese. I personally favor my cast-iron skillet or the oven for making a really great grilled cheese sandwich. If I'm feeling lazy, then a toaster oven will do. But what if you're at work or in a dorm and the break room only has a toaster?

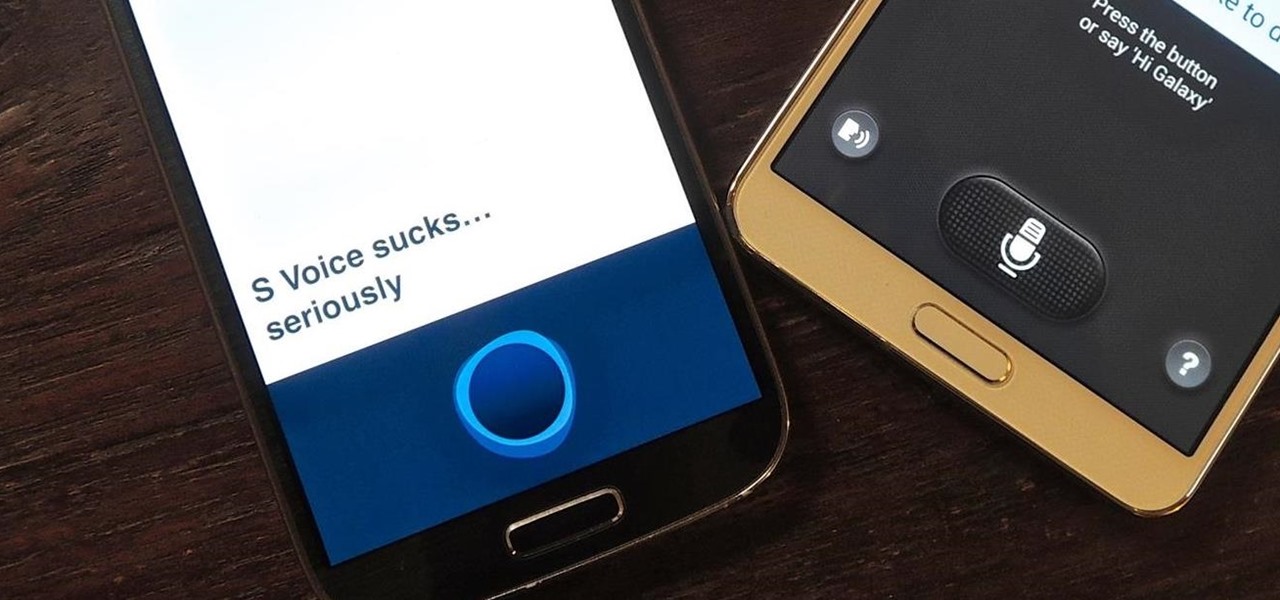
One feature of Samsung devices that's less useful than I had expected is S Voice, the voice assistant that ships with all new Galaxy devices. The voice is annoying, the features are lacking, and it's an all around subpar product. With Google Now, Siri, and now Microsoft's Cortana, Samsung needs to really step up their game—even on the new Galaxy S5.

The Problem If you are working on a car restoration project, then you are going to faced with rust damage. This problem can’t be overlooked, as the entire project depends on repairing and eliminating rust. This would be like laying down new carpet to a house that was flooded, without cleaning the mess and making necessary repairs before laying the carpet down. The problem will still be there and the new carpet will be ruined.

Welcome back, my budding hackers! One of the keys to becoming a professional and successful hacker is to think creatively. There is always a way to get into any network or system, if you think creatively. In previous tutorials, I have demonstrated ways to crack passwords on both Linux and Windows systems, but in this case, I will show you a way to get the sysadmin password by intercepting it from a Remote Desktop session.

Welcome back, my hacker apprentices! I recently began a new series on digital forensics to show aspiring hackers what the forensic investigator can do and see while investigating a cyber attack. This is the second installment in that series and will focus upon network forensics. In other words, what can a network forensic investigator learn about the attacker during an investigation and how.

Some people put up their holiday decorations as soon as Thanksgiving is over. Some wait until Christmas Eve. Right now, the only thing in my whole apartment that would tip you off is a tiny little fake tree on the counter. I've been planning on decorating all month, but I haven't quite gotten around to it yet.

Welcome back, my hacker trainees! A score of my readers have been begging for tutorials on how to hack Wi-Fi, so with this article, I'm initiating a new series dedicated to Wi-Fi hacks. This will probably be around 6-9 articles, starting with the basics of the technologies. I can hear you all groan, but you need to know the basics before you get into more advanced hacking. Then hopefully, developing your own hacks.

Welcome back, my hacker apprentices! In recent weeks, the revelation that the NSA has been spying on all of us has many people up in arms. I guess I take it all in stride as I just assume that the NSA is spying on all of us—all of the time. Don't get me wrong, I don't condone it, but I know the NSA.

How to patch a hole in drywall / plasterboard / Sheetrock. Everyone at some stage in their life will need to patch a hole in drywall / plasterboard / sheetrock. Instead of doing some dodgy patchwork, watch this video to see how simple the job is. The steps are as follow in point form. This method is particularly suitable for holes that are larger than about 100mm or 4 inch's in size.

When the power goes out, having the ability to contact others becomes extremely important, and your cell phone can be one of the most important tools to have. But if the power is out for an extended period of time, battery life becomes a constant problem.

One of the more enjoyable parts of Christmas (other than opening gifts of course) is going out to find the perfect tree, struggle bringing it into the house, and decorating it. As the years went by, I realized that our tree looked exactly like every other tree in the neighborhood: the same lights, the same angel at the top, and the same red, green and white ornaments.

Creative Commons is awesome—really. If an image, video, or audio file is tagged with a CC license, that means you can use it as long as you give appropriate credit to the owner. For bloggers with no money for pricey stock media, it's a godsend. When you license your own media under CC, you can choose how you want it to be used by others and whether or not it can be used commercially.

Notes: My guides are setup like old Lego instruction booklets; picture intense/text lacking. Just remember you're building from the ground up, each step is a layer to go onto the previous layer.

Valentine's Day is almost here, and if you're like me, you're scurrying to do something special for your mate. The standard chocolates and flowers just isn't cutting it anymore, and you can only make so many homemade cards before it becomes banal and meaningless. So, what can you do that shows you put some work into it, while not breaking the bank?

Ever needed to know the the basics of metal inert gas welding? This beginner's guide displays the necessary safety gear, such as the all-important welding mask and deer skin gloves. You'll also learn of some basic equipment options for gas cylinders, welding wires, feeders, and the essential parts of a welding gun. Follow these safety guidelines before getting started with MIG welding.

On May 17, Apple announced that Lossless Audio playback for Apple Music was finally coming to subscribers in June. The long-awaited option will let users stream songs at a much higher quality than ever before. Still, in the fine print, Apple noted that you wouldn't be able to listen to the best sound quality — Hi-Resolution Lossless — on your iPhone without a DAC.

In this series of video clips you’ll learn tips and techniques for making your own rock and stone jewelry. Expert Candace Copeland demonstrates the process of making a necklace step-by-step, offering advice on choosing the beads, stones, gems and other supplies like tools and wire you’ll need to get started. She also offers examples of rock jewelry that makes a great gift for a man or woman. With these easy instructions and a little inspiration you’re well on your way to becoming a jewelry de...

Curious about the basics of metal inert gas welding? Watch this instructional welding video for some vital safety tips. A shielding gas tank contains 3,000 psi of pressure, so keep your welding equipment safe distance from your high pressure tanks. To run a bead, you need to set your wire feed speed and your voltage in order to begin welding with an average angle iron. This video provides all of the preliminary steps to running a short bead.

Sound Recognition was introduced with iOS 14, and the accessibility feature uses on-device intelligence to detect 13 different sounds and then notify you whenever it hears one. Apple increases that number to 15 with the addition of two more detectable sounds in iOS 15 that it should have included from the get-go.

When we got our first look at US Army soldiers testing Microsoft's modified HoloLens 2 last year, it still looked very much like the commercial edition, with some additional sensors attached.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

If you ask Apple Support if the 18-watt power adapter that came with the iPhone 11 Pro, iPhone 11 Pro Max, and four different iPad models will work with the MagSafe Charger and your new iPhone 12 or 12 Pro, the answer is "yes." But that's not the whole story.

Your iPhone's almost out of battery power, there's no wired or wireless charger in sight, and you left your portable power bank at home. You don't want your battery to die, but you still need to use your iPhone. This is when Low Power Mode comes in handy, but you could be wasting valuable time and power if you're activating it the wrong way.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.