After finding and monitoring nearby wireless access points and devices connected to them, hackers can use this information to bypass some types of security, like the kind used for Wi-Fi hotspots in coffee shops, hotels, and in flights high above the ground. By swapping their MAC address for that of someone already connected, a hacker can bypass the MAC filter and connect freely.

The bootloaders on the AT&T and Verizon Wireless variants of the Samsung Galaxy Note 3 still cannot be unlocked, despite the $1,400+ bounty that arose late last year. Nine months later and still nothing. But just because we can't "unlock" the bootloader doesn't mean we can't get around it.

International, T-Mobile, and Verizon customers all share something in common—their carriers provide unlocked Wi-Fi tethering for free. Of course, you still pay for the data used, but they don't charge you extra simply for using your Samsung Galaxy S4 as a wireless hotspot.

In order to make a retro wireless handset, you will need the following: vintage handset, a momentary switch, a resister, a Blue tooth headset, wires, a drill, and a blue LED and mount.

One of the coolest feature of the 3G iPhone is the high speed, always on, Internet connection. Having a constant connection to the Internet is pretty much a must have for any dot com mogul. The main problem with the iPhone is the screen is too small to do any serious Web surfing. Yes, it’s great for Twitter or checking up on emails but blogging from it is an exercise in frustration. Fortunately, there is a way to extend that 3G connection onto your laptop by turning your iPhone into a wireles...
The Citrix Receiver is an app that allows you to securely access your desktop and business applications directly from your Droid Bionic smartphone. You will first need to make an account at the Citrix site, and from there you can decide what you want to have access to on your phone. On the Android app launcher, be sure to pick the Citrix Receiver app so that you can login with your Citrix account.

This how to demonstrates how to use your Apple iphone as a spy camera to spy on others. If you're suspicious, paranoid or just downright creepy, this video can show you how to convert your Apple smart phone into a device for surveillance on others.

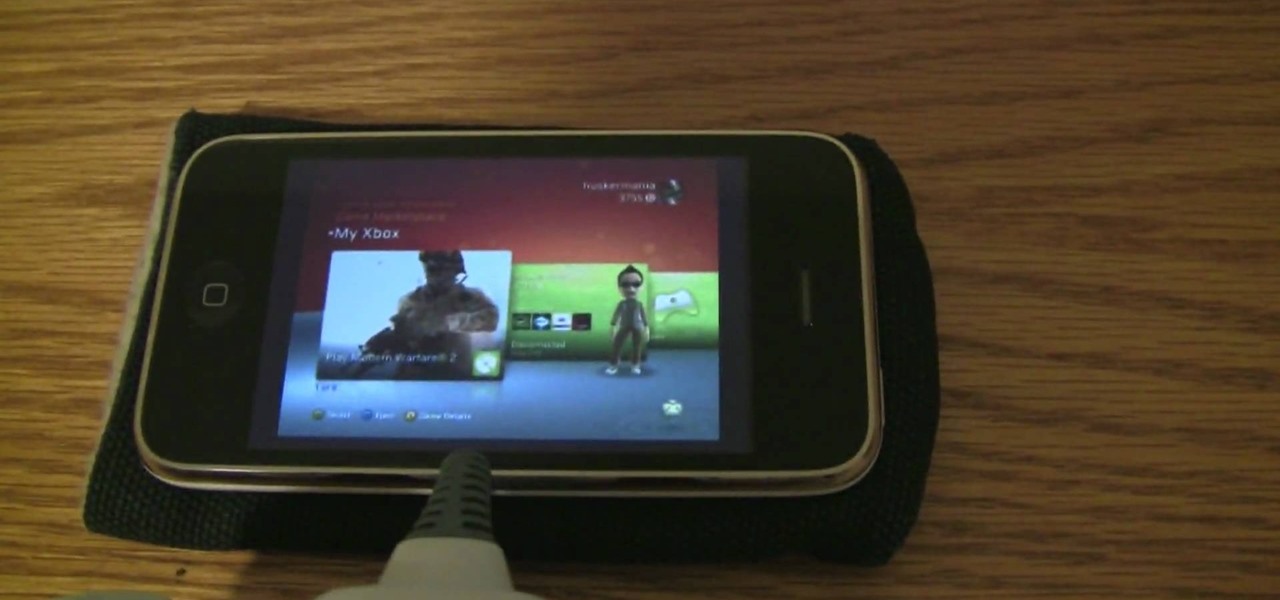
This video will show you how to play on your Xbox 360 using your iPhone 3GS. In order to do that just follow these steps: You will need to get a Slingbox Solo, a composite cable and the Slingbox Player installed on your device. Now you will need to plug in the composite cable into the Slingbox Solo and into the Xbox 360. Connect the Slingbox with the wireless router and with the internet modem. Now configure the network and connect with the iPhone. The last thing to do is to start the Xbox 36...

Other World Computing provides a guide for advanced users demonstrating the upgrade or replacement of a hard drive in a Mac Mini Server computer. This comprehensive video takes you through all steps from tool selection to re-assembling the Mac Mini Server and it is recommended that the video is watched right through before attempting the procedure. In particular, it demonstrates the difficulty of opening up a Mac Mini using a small putty knife. Once the case is off, the three wireless antenna...

To remove your airport card from your Power Mac, you're going to have to know what you're doing… see how to remove the airport card from the Power Mac desktop computer.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to share Internet access at highway speeds.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to build and use a handheld automated warspying device.

In this clip, you'll learn how to find and connect to WiFi networks on a desktop or laptop computer running the MS Windows Vista operating system. For more information, including a complete demonstration of the process and detailed, step-by-step instructions, watch this home-computing how-to.

Not only can your T-Mobile G1 phone get Internet access by itself, you can also use it as a router or modem for your home wifi network. All you need is to download a single app from the market, install it, and you're ready to set up your home wifi network!

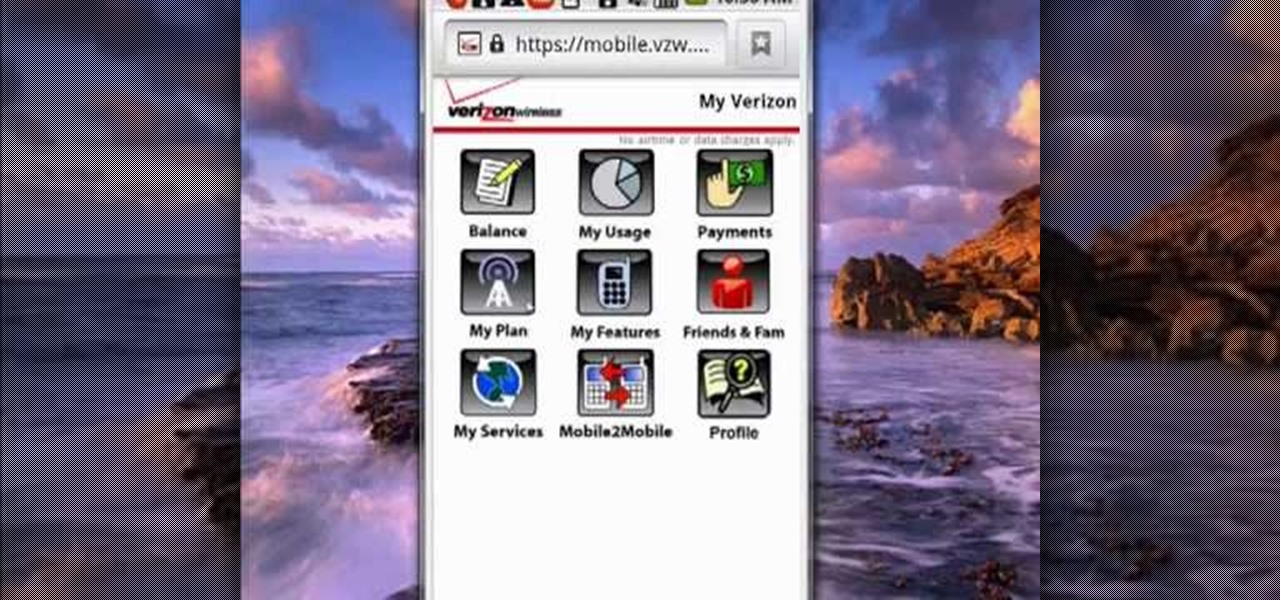
Want to monitor your Verizon Wireless service and data usage from an Android phone? This brief video tutorial from the folks at Butterscotch will teach you everything you need to know. For more information, including detailed, step-by-step instructions, and to get started keeping an eye on your own minutes and data transfers, take a look.

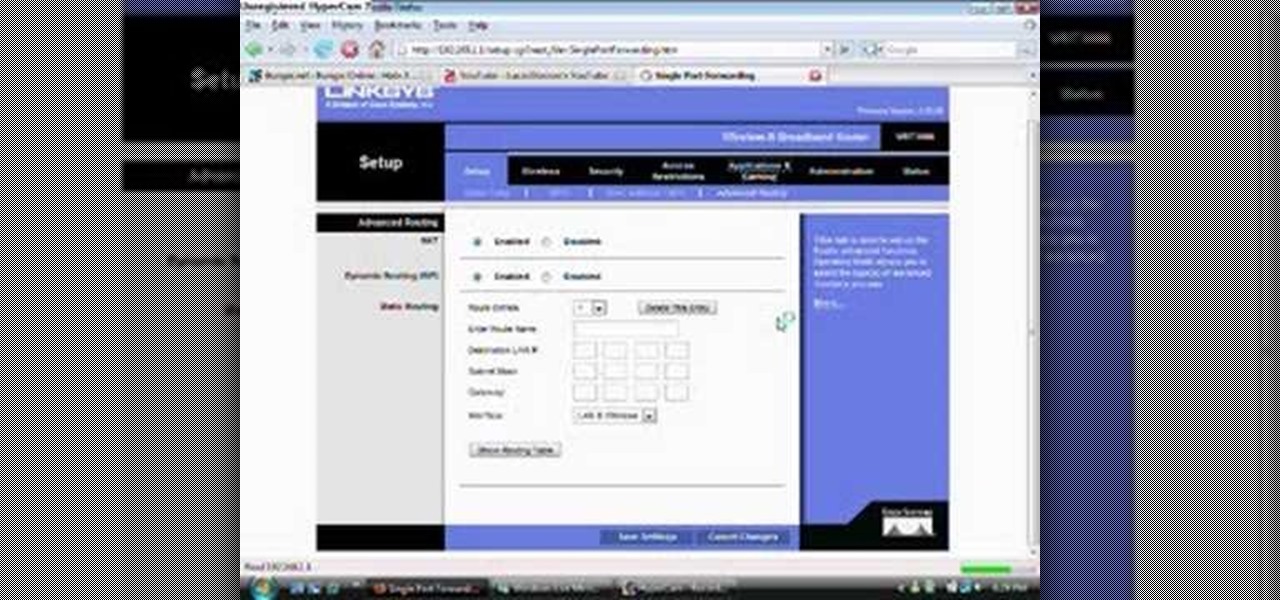
Need to change the NAT type on your wireless Linksys router to play games over the Internet on Xbox Live? Boy and/or girl, have you ever come to the right place. This home networking how-to will get you up & gaming in no time flat.

Sparky is a wireless, web-based video-chat robot from the Gomi Style crew. You can learn how to make your own Autonomous Telepresence robot using spare computer parts, some old toys and a bit of custom software (that we provide at gomistyle.com). This robot is operated with a Make controller circuit board. Sparky is a retired electric wheel chair with a monitor as a head.

This video walks through basic security configuration for a WRT54G Wireless Router. Also provides a default password list.

This is the second episode of Full Disclosure by InfinityExists.com. This episode includes how to crack WEP encryption, and why it can be cracked so easily.

Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

I see that there are a lot of people that want to install and try the Aircrack-ng program for wireless auditing. But have problems because their Linux knowledge isn't that great. This How-To video tutorial explains step by step exactly what you have to do. No loud background music.

Stay secure on public wireless networks by making your own FREE virtual private network (VPN). This tutorial shows you how to set up an OpenVPN server and connect to it from your laptop.

This video shows you two methods to connect to XBox Live using a laptop. For the first method, go to your start menu and open up your control panel. In the control panel window find the area marked Network and Internet and select the option View network status and tasks. In this new window, select Change adapter settings in the left hand pane. You will be presented with another window that has your network connections listed. Right click on your Wireless Network Connection and select properti...

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

It's frustrating to go and listen to music just to find that your wired earbuds more closely resemble a tumbleweed you can't easily unknot. Cords tangle, are vulnerable, and make it hard to do so many of the things music makes easier — like working out, commuting, and cleaning. The Raycon E50 Wireless Bluetooth 5.0 Earbuds are completely wireless earbuds that are on sale now for $64.99 — a full 45% off their regular listed price of $119.

Still listening to music and podcasts on your laptop or phone speakers? Mute that right now and switch to a powerful speaker that sounds incredible — which also happens to be on sale for less than fifty bucks. Right now, you can get the Motorola Sonic Sub 530 Wireless Bluetooth Speaker for just $49.95 — that's a 16% discount off the regular price of $59.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

After entering into settlement talks with Epic Games over the gaming giant's trademark challenge, Nreal is now ready to open up the floodgates to potential early adopters in the augmented reality space.

It's new phone season — new handsets are releasing every few weeks, we're seeing endless software updates, and the holidays are right around the corner.

We already know that major players like Magic Leap have been planting the seeds of augmented reality for mainstream consumers through wireless partnerships with AT&T, NTT Docomo, SK Telecom.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

It's common for IoT devices like Wi-Fi security cameras to host a website for controlling or configuring the camera that uses HTTP instead of the more secure HTTPS. This means anyone with the network password can see traffic to and from the camera, allowing a hacker to intercept security camera footage if anyone is watching the camera's HTTP viewing page.

OnePlus will be releasing a new phone in the second half of 2018, specifically, an upgrade to their T-series. Over the past two years, #T versions have come out about five months after their predecessors and have included small updates that fix any problems from the previous OnePlus device. While we do know a bit about OnePlus 6T, what it could be is much more exciting.

What do you get a co-worker for Christmas, Hannukah, or Kwanzaa when he or she already has a Meta 2 headset?

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

Traveling is a rich and rewarding experience. When you don't speak the language, however, your trip can present some tricky obstacles. Google knows this, which is why they will now automatically translate user reviews in Google Maps and Google searches.

Bose Corp is the latest company trying to make another dollar off of you without your permission. Bose Connect, the companion app to the swag $350 Bose headphones, is not the Jane to your Jack that maybe we all hoped it to be.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.