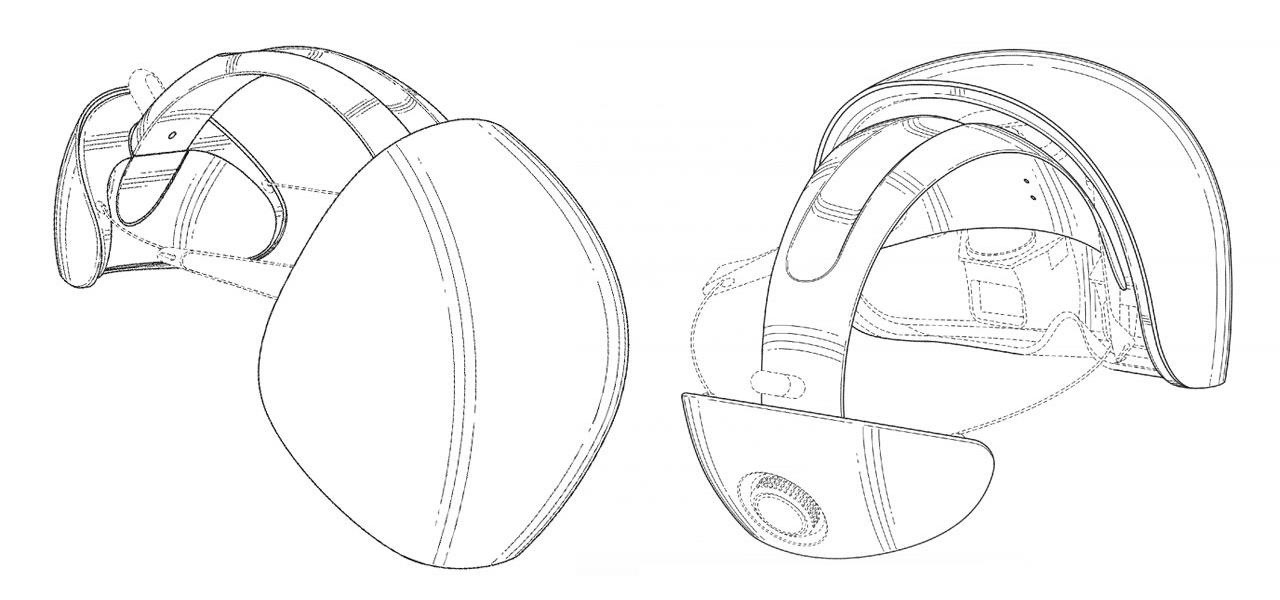
We've experienced the HoloLens, learned a lot about the Meta 2, but almost nobody knows exactly what to expect out of Magic Leap's mixed reality headset. Thanks to a patent dug up by Quartz (which we saw first on Tech Insider), we now might have a better idea.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.
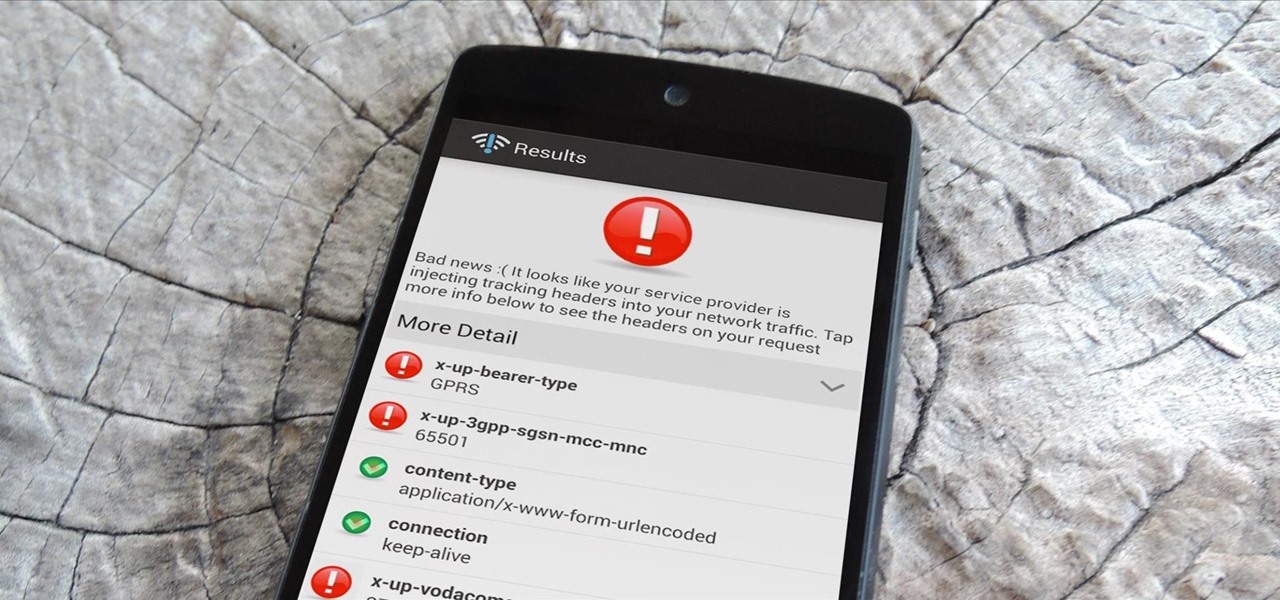
A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

Admit it, since childhood you've thought to yourself, "When oh when will they finally make Smell-o-vision?" And while that technology hasn't yet made it to our living rooms, we may soon be a step closer towards that particular American dream with the oPhone.

I've already showed you how to magically unlock your Samsung Galaxy S3 with the simple wave of a hand, but why stop there? Sure, you could go out and purchase a Samsung Galaxy S4 so you have Air Gestures that let you control the lock screen, SMS, sound, wireless, and more.

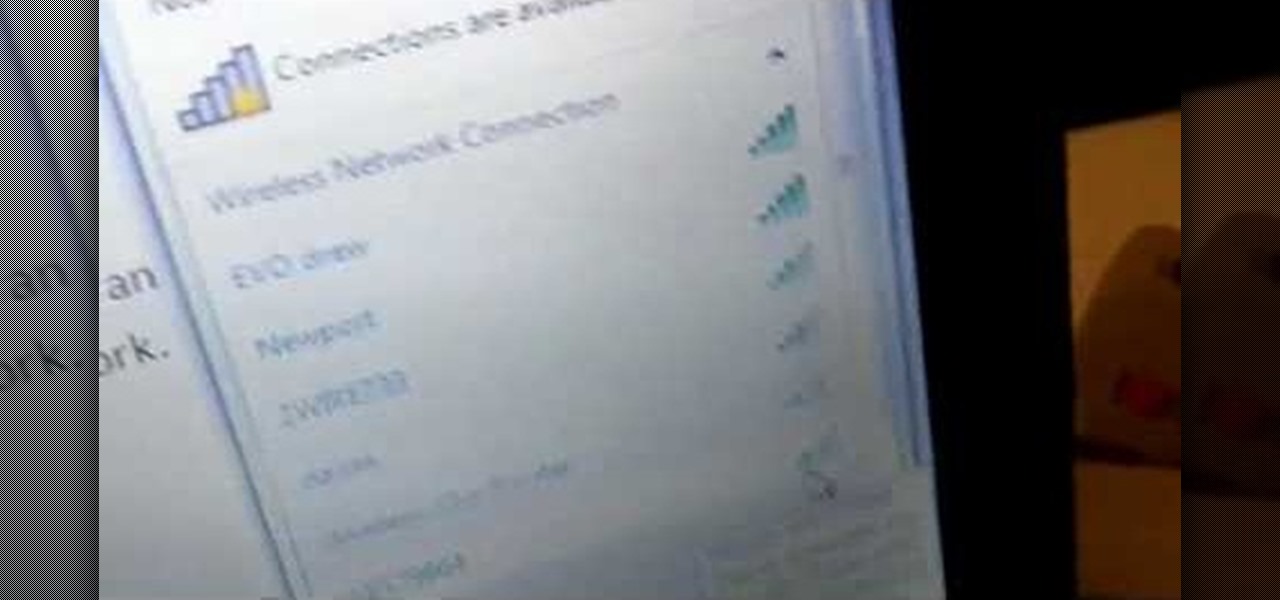
People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

This two part segment will show you how to use the Wi-Fi tethering mobile hotspot functionality on your Motorola Droid Bionic smartphone for free after rooting it. Segment 2 of the guide will walk you through using Radiocomm to hide your tethering usage from Verizon Wireless so you're less likely to get caught.

There are so many different devices today that have Wi-Fi capabilities--notebooks, handheld gaming devices, tablets, and more. Why not share some of the 3G and 4G internet that streams into your Motorola Droid 3 with the other electronics you carry with you? You can turn your Verizon Wireless Droid 3 smartphone into a mobile Wi-Fi hotspot using the mobile hotspot menu on the android phone.

With the new iOS 4.2 (and 4.2.1) firmware for all mobile Apple devices, printing from your iPhone, iPad or iPod Touch has become easy… well, maybe not. Despite the new AirPrint software in iOS 4.2, it can still be difficult to print papers and photos from your mobile device since Apple removed AirPrint from the Mac OS X 10.6.5 software update, due to some kind of legal dispute.

The Canon EOS 7D digital SLR is the first Canon EOS camera that can trigger off-camera Speedlites with the cameras build in flash. The integrated Speedlite transmitter is fully compatible with the Wireless E-TTL Flash System. See exactly how all this works and how to use your flash functions.

Make your router run on VTEC by injecting it with Tomato Firmware. Tomato Firmware gives you excellent tools such as being able to monitor bandwidth consumption, boost WiFi signal, track results with graphics and much more.

The iPod has become a common household item. With each new release, the iPod comes with more features, a steady progression from music to videos, and now as a phone. But did you know that there's a way to turn your iPod into a remote control? Take a look at this instructional video and learn how to give your iPod remote control features with some internal tweaking. You need a Logitech bluetooth wireless set in order for this mod to work.

It may be intended as a toy, but this gizmo can be hacked for more than just watching a remote-controlled car's video spy cam. This HUD (heads-up display) comes with the Wild Planet Spy Gear Video Car, but it's said that you can purchase the video headset separately. And it's not really a HUD, because you can't see through the video images, but it's close enough to be handy for all sorts of things, like computers, iPods, robots, wireless cameras, and gaming. Who wouldn't like to Call of Duty ...

Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, you'll need the following items: (a) a piece of parabolic cookware, (b) heavy tape, (c) a USB WiFi stick, (d) tin snips, and (5) a USB extension cable. For detailed instructions on building your own wireless signal extende...

The Raspberry Pi Zero W and Pi 3 Model B+ include integrated Wi-Fi, Bluetooth Low Energy, and more than enough power to run Kali Linux. They sound like perfect all-in-one penetration testing devices, but the lack of support for monitor mode and packet injection usually meant buying a supported Wi-Fi adapter. Now, it's possible to use monitor mode on the built-in Wi-Fi chip with Nexmon.

With the rapid demise of the 3.5 mm headphone jack, Bluetooth is fast becoming our best option for universal audio. The problem is, with over a decade of it being a standard component, many of us still own a reliable pair of wired headphones that we don't want to gather dust. Well with one tool, you can have your cake and eat it, too.

Design flaws in many routers can allow hackers to steal Wi-Fi credentials, even if WPA or WPA2 encryption is used with a strong password. While this tactic used to take up to 8 hours, the newer WPS Pixie-Dust attack can crack networks in seconds. To do this, a modern wireless attack framework called Airgeddon is used to find vulnerable networks, and then Bully is used to crack them.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

The rumors surrounding the next iPhone and Apple's ambitions toward augmented reality have been going on for months, and a fresh development brings back the idea of Apple's Smart Connector bringing the two together. The Verifier, an Israeli news site, claims the next suite of iPhones (iPhone 8, iPhone 7s, and 7s Plus) will all sport Smart Connectors for both AR and wireless charging.

Apple's anxiously awaited iPhone 8 with a 5.8-inch OLED display is all set to launch this September, alongside the iPhone 7s variants. However, according to MacRumors, which cites information from a number of Barclays analysts, stock will be very limited, and most won't ship until late in the fourth quarter.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

Greetings aspiring hackers. I have observed an increasing number of questions, both here on Null-Byte and on other forums, regarding the decision of which USB wireless network adapter to pick from when performing Wi-Fi hacks. So in today's guide I will be tackling this dilemma. First I will explain the ideal requirements, then I will cover chipsets, and lastly I will talk about examples of wireless cards and my personal recommendations. Without further ado, let's cut to the chase.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

Do you have an Alfa AWUS036NH Wi-Fi adapter that claims it can go to 2000 mWs, or some card that can supposedly transmit power over 1000 mW? If so, you may have run into problems setting your card's TXPOWER higher than 30 dBm, which is about 1000 mW. Well, I will show you how to break that barrier and go as high as you want!

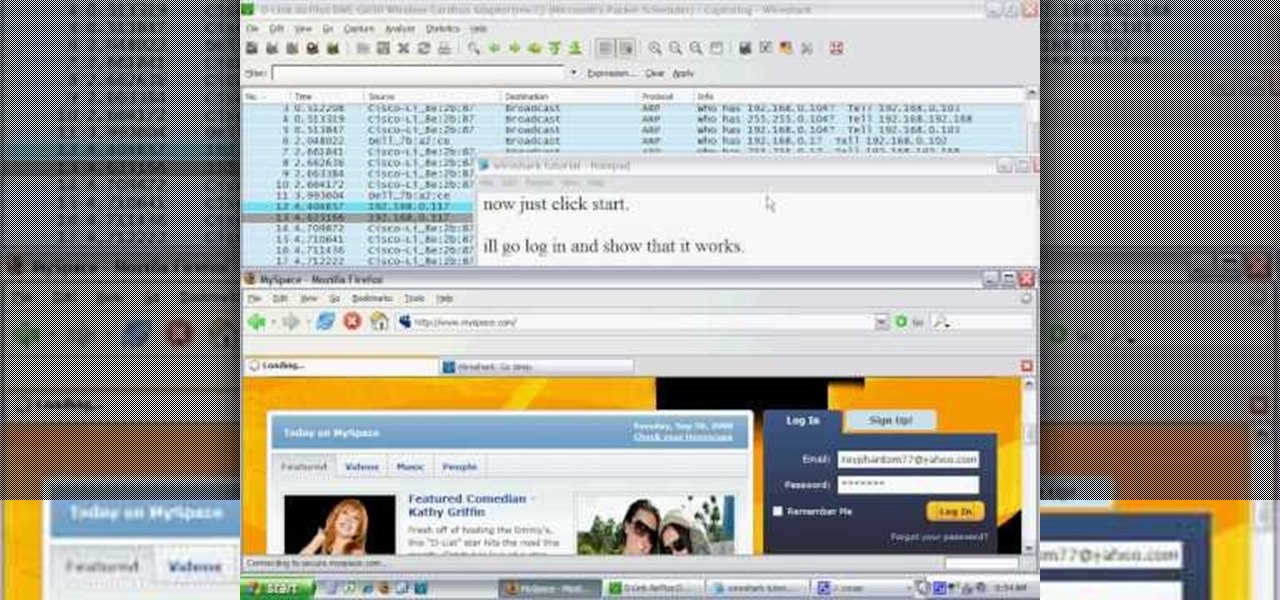
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!

If you have an iPhone or an iPod Touch then you probably think that the only places you can listen to your MP3 files are on your laptop, your i-gadget of choice, and your car. But in reality anything that you can groove to on your iPhone or iPod Touch can be listened to - and transferred to - your PlayStation 3.

In this video we learn how to sync your Powertap. First, go to your setup screen by pulling down mode and select and going through the find. Then, click clear and find your main menu. Use the select button to scroll until you get to the number 5. Hit mode and then your hub ID number can be entered in. From here, hold down the select button for two seconds until it starts to blink. Then your hub will start to become activated. If you have a wireless speed sensor do the same thing as well. This...

In this clip, learn how to set up the HTC EVO's Hot Spot app. This app is very useful and by using it you can connect up to 8 other devices to your 4G internet via tethering and use your phone as a wireless modem. This app will cost you an additional 29.99 a month but if you are an Internet junkie, it will be worth it. So, follow along and watch this step by step for setting it up.

Bruce Dorn from Canon breaks down the exposure and Speedlite controls on the Canon 5D Mark II. His explanations are especially helpful as he gives certain shooting scenarios in which tweaking these settings will improve your overall image quality.

PerformanceBikes will show you how to install a bicycle computer. Whether you have a simple computer or a more advanced computer you be able to see the basic instructions. Start by reading the instruction, install the handle bell mounts, install the wireless transmitter. You then install your spoke magnet, then calibrate your computer for your wheel size. Make sure you have read your own particular directions. If its not working, make sure you re-read your instruction, check your set up or ch...

Both your Wii and your PC need to be connected to a router that has an internet connection. If you have a wireless router, the Wii can connect to it without any additional hardware. Instructions are provided with the Wii.

Are you an aspiring filmmaker? If so, you might not have made it to Steven Spielberg status just yet, which means you could learn a thing or two. Eos Lighting has made this video to help teach you a little bit about sound on a video camera.

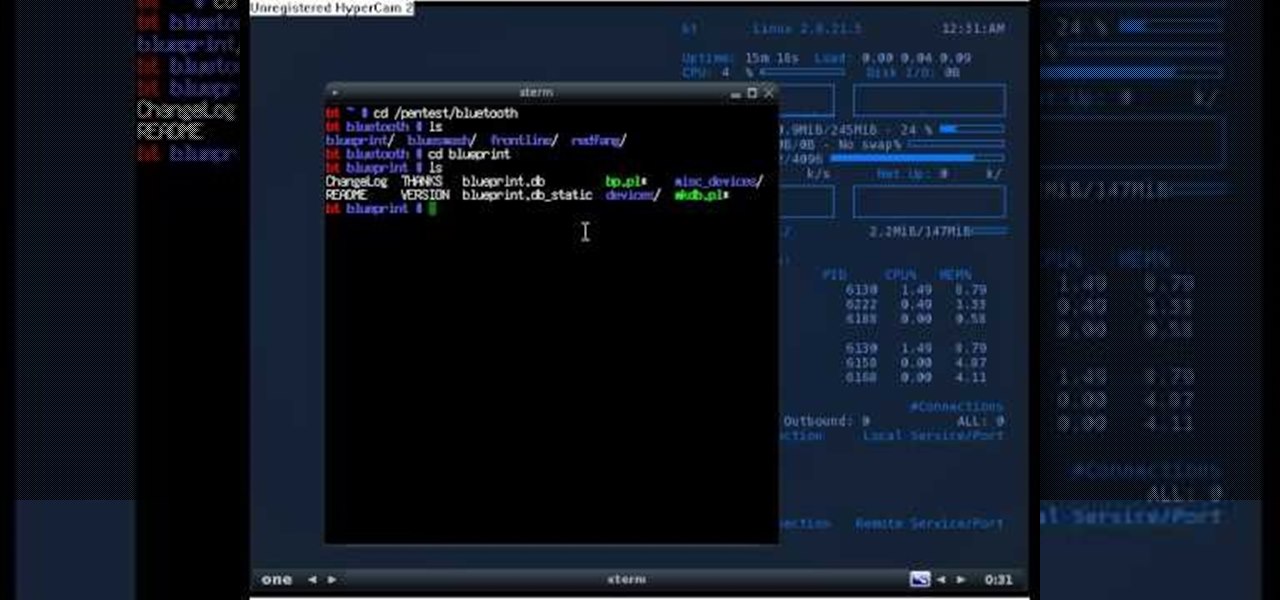
If you're new to the Bluetooth hacking world, here's a little background on using Linux BackTrack to hack a Bluetooh device: Linux Backtrack is a Live DVD device that offers security tools - like password crackers - that allow you penetrate networks.

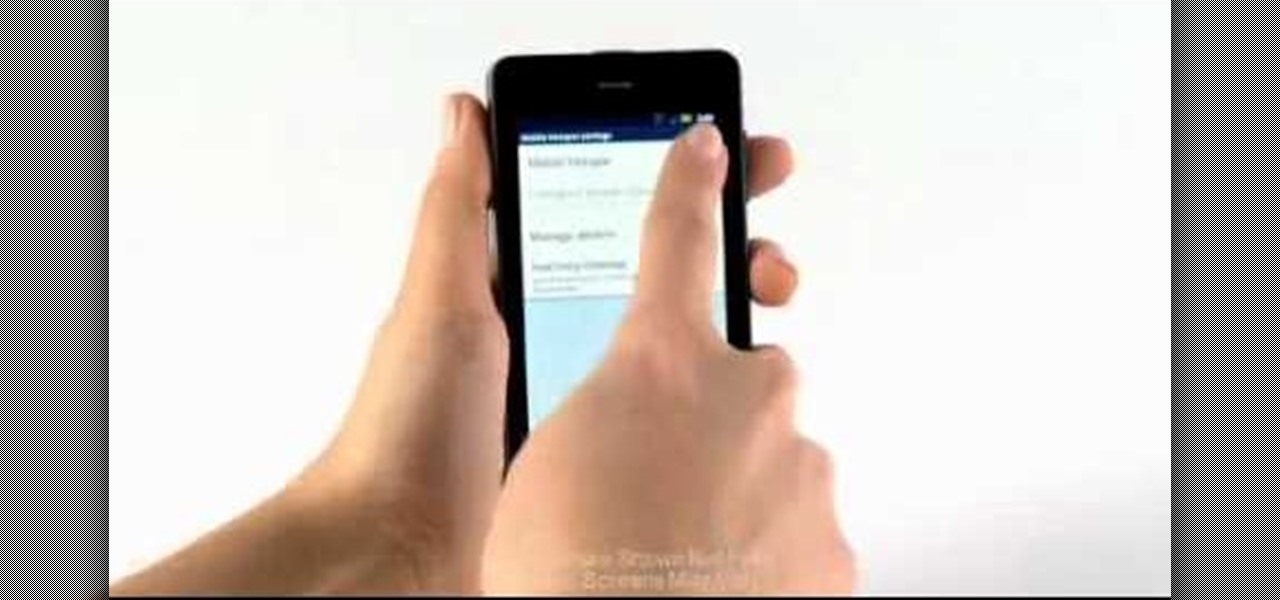
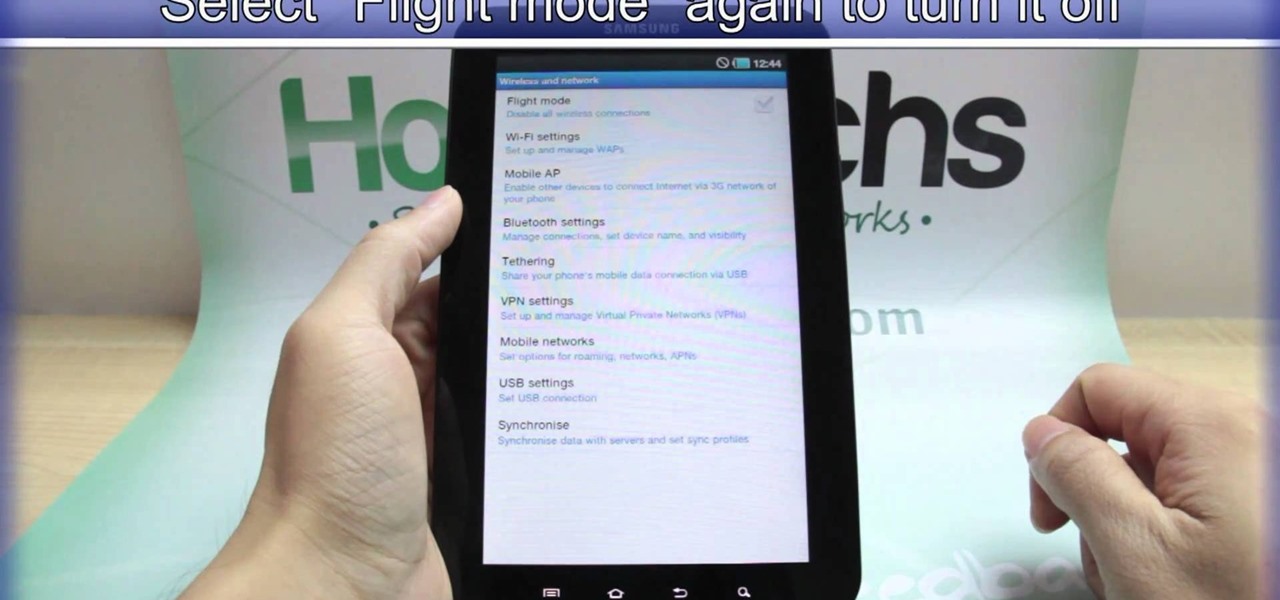
Taking a trip soon? Well, make sure you can still enjoy your Samsung Galaxy Tab up in the air. Turning on the Airplane Mode allows you to use your device safely mid-flight. This video shows you exactly how to active it on your Android tablet. Hit MENU < SETTINGS < WIRELESS & NETWORKS and then select FLIGHT MODE at the top. This will activate it. You can press it again to deactivate it. You can also turn on or off FLIGHT MODE by pressing the power button on the side.

Need to browse the web on your new Samsung Galaxy Tab? Well, first you're going to have to set up Wi-Fi on the Android device. This video shows you the complete steps to getting connected! Press MENU < SETTINGS < WIRELESS & NETWORKS < WI-FI SETTINGS and then select WI-FI to turn in on. Next, choose your network, enter the password and press CONNECT. It's that easy.

Unlock your Samsung Vibrant or Captivate's hidden potential by running a custom ROM on it! Loading custom ROMs lets you do fun things with your Vibrant/Captivate like overclocking it, and even turning it into a wireless hotspot with WiFi tethering. For all of the details, and to learn how to put a custom ROM on your own phone, take a look.

Unlock your HTC HD2's hidden potential by running a custom ROM on it! Loading custom ROMs lets you do fun things with your HTC G1 like overclocking it, and even turning it into a wireless hotspot with WiFi tethering. For all of the details, and to learn how to put a custom ROM on your own HTC HD2, take a look.

Unlock your Samsung Behold 2's hidden potential by running a custom ROM on it! Loading custom ROMs lets you do fun things with your Behold 2 like overclocking it, and even turning it into a wireless hotspot with WiFI tethering. For all of the details, and to learn how to put a custom ROM on your own Behold 2, take a look.