10 conversational Spanish phrases that you can use in a coffee shop. Includes ordering drinks and asking about wireless Internet. Subtitles are included for help with pronunciation. Speak Spanish at a coffee shop.

Wireless networks. Nowadays, everyone uses 'em, but most don't secure 'em. On average, I can drive up and down any block in my city and find at least one or two open or semi-open networks on any given day. With some changed MAC addresses for good measure, an attacker can use your network as a spring board for who knows what. When the police come a few days after, they are coming to your door—and not to talk about how nice your lawn is. Don't be that guy.

Leaving your wireless router at its default settings is a bad idea. The sad thing is, most people still do it. Once they've penetrated your network, hackers will change your router settings so they'll have an easy way back in. This allows them to change your network into a shell or proxy so they can forward their traffic anonymously through you when committing other dirty deeds.

Wireless contracts and phone-buying programs continue to become more and more confusing. As if you didn't have enough to worry about with regards to the rising costs of services and the elimination of contracts with mobile providers, Verizon Wireless will soon institute a new charge that puts the grub in "money-grubbing." Sadly, this isn't one of those April's Fools pranks that are running rampant on the web today. Starting next week, the largest mobile phone provider in the United States wil...

We assumed the novelty of the Apple iPhone would have worn off by now. We were wrong. It could get better than TapTapRevolution and Shazam.

These days, eReaders are everywhere. For die-hard book nerds, eReaders offer the convenience of a full library without having to sacrifice shelf space. Sure, there are the paper buffs who swear that you just can't take an eReader with you into the bathtub, but when's the last time anyone actually did that? Face it, eReaders are convenient and here to stay. But there's a dizzying array of information out there, so what should you look for in an eReader?

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

An amazing price for a full featured wireless micro-remote, using the iphone or ipod touch as its brains.

Bluetooth capability allows your mobile phone to connect to a computer, lap top, a wireless head set, or even your car. With most states rushing to pass no cell phones while driving laws, a Bluetooth device keeps you connected. Watch this video cell phone tutorial and learn how to hook up and use the Bluetooth features on your Blackberry Curve. Use the Bluetooth capability on a Blackberry Curve.

It is always a bittersweet moment to find yourself looking back on the fond memories that seem to have taken place in the distant past. When your favorite song from 10 years ago comes onto the radio, or when a sudden scent reminds you of the summers you spent as a child—these types of moments tend to trigger the fondest of memories. For this week's challenge, we'd like to see a photo that captures a nostalgic feeling, whether it be your favorite childhood food, meaningful memorabilia you've s...

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

One of the most exciting new features announced by Google+ was the ability to broadcast hangouts live via YouTube, which was recently demonstrated with the very first Google+ Hangout On Air with +will.i.am of the Black Eyes Peas.

German photographer Peter Langenhahn's process is incredibly laborious; similar to photographer Lori Nix, he can spend up to three months on a single photograph. But while Nix spends the time constructing elaborate sets, Langenhahn is anchored to the computer, editing.

Love folk art but could do without the folk? Prepare to have your heart stolen by a self-folding origami automaton.

The Toronto International Film Festival is but a distant memory, though we are still getting compliments on all the awesome footage we shot, both for our Midnight Madness coverage and interviews with directors like Don Coscarelli and Rob Stewart. But here's the thing - we had big, large help. Even though we've been at it for 5 years, shooting an event like TIFF is never easy! It's hectic and unpredictable and as a result, getting good looking footage can be difficult if you don't have the rig...

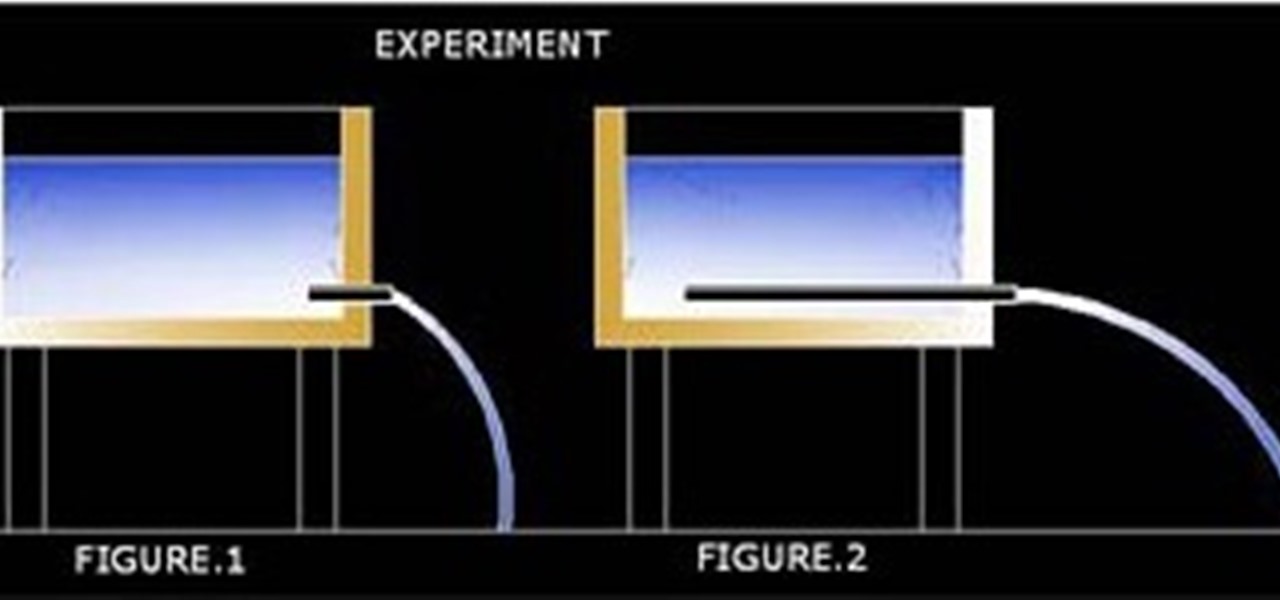
An experiment was carried out at our laborataries to investigate the flow through two pipes of same diameter fitted at the same height from water level inside of a water tank as shown. It is found the longer pipe line inside the water tank generates a higher speed resulting more powerfull flow. Flow in this pressure pipe develops due to gravitational accelaration on a horizontally flowing water column also, when it is an enclosed stream of flow. If this length is short it is not possible to d...

The G3 in Call of Duty would be so much nastier if it was just fully automatic right? There are lots of semi-automatic things in video games that really would be more fun if they shot faster, and now they will no matter what XBox 360 game you're playing. This video will show you how to put a rapid fire button mod on an XBox 360 wireless controller. Fire away. Put a rapid fire button mod on an XBox 360 controller.

If you're having a little trouble operating your newly purchased Motorola Nextel i1000plus cell phone, let Sprint help you out. This Sprint interactive mobile phone tutorial takes you through every step necessary to fully familiarize yourself with the i1000plus cell phone by Motorola. This instructional tour will help you learn how to use Nextel Direct Connect - Digital Walkie-Talkie, Nextel Online - Wireless Web, Mobile Office Email, Nextel Mobile Text Messaging, 100-Number Phone List Direct...

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Consumer Electronics for Dummies. Just watch this video tutorial to learn how to position home theater surround-sound speakers, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to set up a WiFi network on a mac, For Dummies.

Welcome to the second part of the Arch Linux installation tutorial! We are installing Arch because of the amount of users who want to learn how to get into Linux. Arch is a simple, minimalistic distro, designed not to hold the users hand, but to push them to know their system and customize it to the core. This will make you feel accomplished, as well as give you the extra edge of being knowledgeable of the GNU/Linux operating systems.

In this video tutorial, viewers learn how to find their computer's MAC (or physical) address in a Windows computer. This task is very easy, simple and fast to do. Begin by clicking on the Start menu and open the Run program. Then type "cmd" in the Run box and press OK. When the black command prompt opens, type in "ipconfig /all" and press Enter. The computer's MAC address will be listed as Physical Address under Wireless Network Connection. This video will benefit those viewers who use a Wind...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

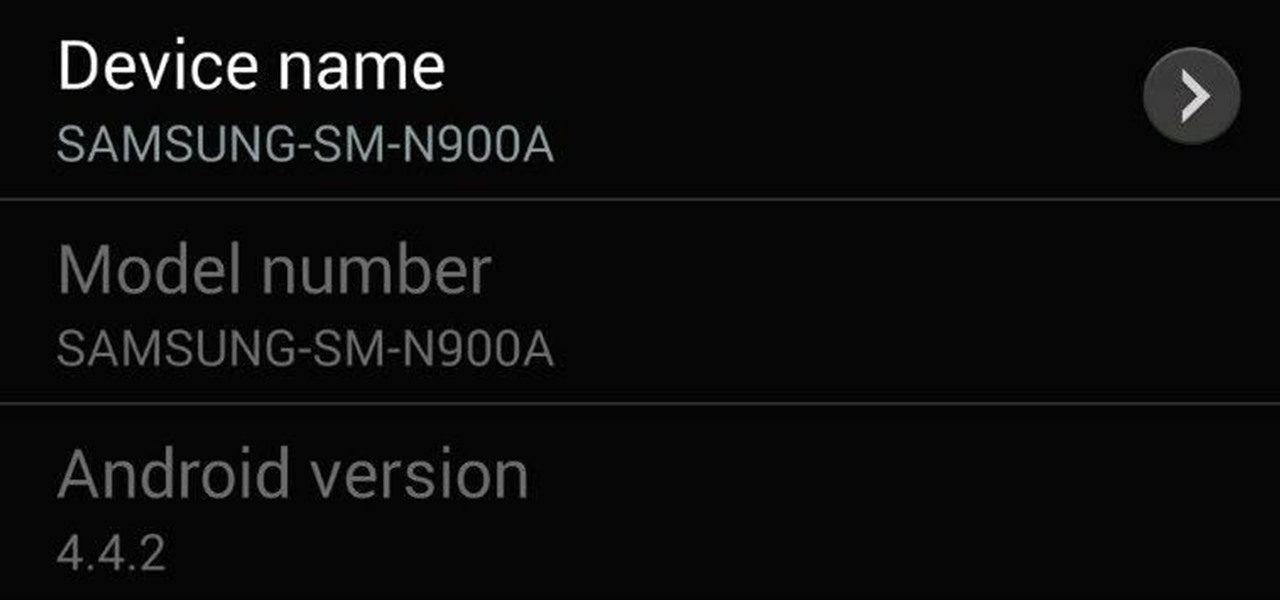
After leaks and rollouts from rival carriers, AT&T has finally released their official Android 4.4.2 KitKat update for the Galaxy Note 3. If you haven't received your update notification, force a manual check by going to Settings -> More -> About Device -> Software Update -> Check for Updates. Make sure you're connected to Wifi and have at least 50% battery remaining. This update includes:

Julian Oliver created the Transparency Grenade in January 2012 for the Studio Weise7 exhibition at Labor 8. It's a transparent device with a "payload" built from an ARM Chip, an Arduino Nano, a mic, and a strong Wi-Fi antenna. It taps into wireless networks and logs emails, webpages, images, and voice to a publicly available online map showing its "detonation" location. Apparently, development for an Android version (sans the pretty plastic shell) is under way thanks to interested donors. See...

Ever wonder what you look like to someone else as you walk, talk? How it looks from above, behind, or to the side? Seeing yourself in a video flattens the experience into two dimensions, but this wireless camera rig experiment from Instructables member BigRedRocket brings it into the third dimension:

Life is getting more and more convenient. You can pick up a wireless signal at nearly any coffee shop these days (Starbucks is now officially free in every location across the nation), as well as airports, libraries, hotels and more. However, along with this convenience comes the risk of security breach. Passwords. Emails. Account numbers.

Can a well-directed thought be as good as a mouse click? With an Emotiv EPOC headset, the answer is yes. And then some. Though Emotiv describe their device as a "high-resolution, neuro-signal acquisition and processing wireless neuroheadset," we're quite content to call it a thinking cap.

Ogre is a "Tank" built around a Zamor launching system nicknamed "Hailstorm". For more information, visit http://www.teamhassenplug.org/robots/...

Microsoft Research and Carnegie Mellon University have teamed up to to create an armband that projects a touchscreen interface directly on to your skin. The best part? Skinput knows which part of the body you've tapped, based on the sound that's matched against skin, muscle or skeleton.

Tinkernut demonstrates how to crack a wifi connection, as well as how to better secure your own personal connection. Also included in the video gallery is Tinkernut's previous tutorial on the same subject.

Many people all around the world have been using Korean Anycall Galaxy S (SHW-m110s), because the price is reasonable and easy to used. But after they buy this phone they always saw two clocks in the front screen while the phone locked, one is Local clock and the second is Seoul clock. The most of the user always want to remove it but they can’t do it, now I’ll show you how to remove it step by step. Step 1: Go to Settings Step 2: Wireless and Network Step 3: Mobile Networks Step 4: T Roaming...

When i went to class today, a good friend asked me a question. He wanted to know what the best hacking software was to basically do everything. What i told him was this: Well there isn't an "Ultimate" tool boot there are a number of tools which deserve a "Medal." So what i'm trying to say here... What are some of the best hacking tools available right now? For starters i created a list with some of the tools.

Add a little extra life to old books you'll probably never read again by transforming them into a sneaky secret book safe, an e-book reader case, a picture frame, or even a book planter for your indoor succulents.

Sharing your internet connection with others through wifi, is easy. follow the steps and your Mac will emit a wifi signal. Step 1: Open System Preferences. Step 2: Open Sharing, in Internet and Wireless Section. Step 3: Select the Option of Internet Connection You Have on the Computer. I use ethernet connection. Any of the options on the list still work.

ProjectExciteBike is a device that harnesses the manpower pedaling speed of an exercise bike and in turn, converts the energy into a single control button on a gamepad (which would translate as the "gas pedal" for racing games). This particular project works with XBox 360, but can be adapted for other systems as well.