
How To: Hack Your Neighbor with a Post-It Note, Part 1 (Performing Recon)
Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.


Using just a small sticky note, we can trigger a chain of events that ultimately results in complete access to someone's entire digital and personal life.

The last quarter of 2017 brought us some downright excellent smartphones. Between the iPhone X, Pixel 2, and Note 8, consumers have more fantastic options than ever when choosing a new device. It's now the perfect opportunity for Samsung to set the tone for 2018 smartphones with their exceptional S9 and S9+.

Welcome back, my aspiring hackers! As I mentioned in earlier posts, the best hackers (or at least those not behind bars) have a keen understanding of digital forensics. If I am tasked to intrude upon an enemy's file server to retrieve war plans, such as in this tutorial, it is essential to my country's (and my own) well-being that it not be traced back to me. Understanding digital forensics helps us to leave without a trace and never have a trail back to us or our employer.

This video shows you two methods to connect to XBox Live using a laptop. For the first method, go to your start menu and open up your control panel. In the control panel window find the area marked Network and Internet and select the option View network status and tasks. In this new window, select Change adapter settings in the left hand pane. You will be presented with another window that has your network connections listed. Right click on your Wireless Network Connection and select properti...

What started as an accessibility setting for hearing aids turned out to be a super helpful tool for anyone with a good set of Bluetooth headphones. The problem is that most iPhone and iPad users still don't know about it. If you're one of them, you need to see what this underrated gem in iOS and iPadOS can offer you.

Wireless charging is pretty much ubiquitous among modern iPhones and Android smartphones, but the technology has brought a lot of clutter with it.

There are many tools out there for Wi-Fi hacking, but few are as integrated and well-rounded as Bettercap. Thanks to an impressively simple interface that works even over SSH, it's easy to access many of the most powerful Wi-Fi attacks available from anywhere. To capture handshakes from both attended and unattended Wi-Fi networks, we'll use two of Bettercap's modules to help us search for weak Wi-Fi passwords.

After entering into settlement talks with Epic Games over the gaming giant's trademark challenge, Nreal is now ready to open up the floodgates to potential early adopters in the augmented reality space.

We already know that major players like Magic Leap have been planting the seeds of augmented reality for mainstream consumers through wireless partnerships with AT&T, NTT Docomo, SK Telecom.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

Magic Leap's business strategy for bringing augmented reality to the mainstream has become even clearer via its latest funding round.

After years of rumors and waiting, Samsung's first foldable smartphone is finally a reality. The phone itself is a bit wild, but with Samsung going so far out of their comfort zone with this one, there were some bumps in the road that caused a delayed release. The launch has been pushed back yet again, but when it does hit stores, it could end up being one of the most influential devices in years.

Ever since the announcement of the Razer Phone, a wave of gaming smartphones started to hit the market. With ASUS being such a big name in gaming, it made sense for them to throw their hat in the ring. The result is the ROG Phone. And with this first try, ASUS has topped the rest, creating a gaming phone others should try to emulate.
The "controversial" Pixel. No phone in the history of Google's Pixel lineup deserves this title more than the Pixel 3 XL. For some (including myself), the design is a welcome change that embodies the modern design of 2018 flagship phones. For others, it has an ugly huge display notch that destroys symmetry.

Three new iPhones means you have to make a choice: Do you go with the smaller iPhone XS, the larger iPhone XS Max, or the cheaper iPhone XR? There's lots to like about each model, but if you want to make an informed decision, it's time to learn what each has to offer. Here's what the iPhone XS Max brings to the table.

To quote MKBHD, cheap phones are getting good. Each year we are seeing manufacturers start to offer more for much less. This not only translates to cheaper flagship phones, but better budget phones. The latest example of this is the Alcatel 3V, which is redefining what you can get at $150.

A new smartglasses powerhouse is rising in Europe, led by two of the region's leading brands, optical systems company Zeiss (also known as Carl Zeiss) and telecommunications giant Deutsche Telekom.

A weak password is one that is short, common, or easy to guess. Equally bad are secure but reused passwords that have been lost by negligent third-party companies like Equifax and Yahoo. Today, we will use Airgeddon, a wireless auditing framework, to show how anyone can crack bad passwords for WPA and WPA2 wireless networks in minutes or seconds with only a computer and network adapter.

If you're in the market for a new smartphone, you'll likely scan spec sheets and read reviews of the top phones, compare display size and technology, RAM amount, and processors. But one factor that is often overlooked is cell reception — and for T-Mobile subscribers, there's only one device that has flagship specs and an exclusive antenna that will actually improve your signal.

The Watch Dogs video game series came out in 2014, enamoring audiences with the idea of a seemingly magical smartphone that could change traffic signals, hack web cameras, and even remotely control forklifts. This may sound like science fiction, but The Sonic uses a customized flavor of Kali Linux to allow you to unleash the power of Kali from any smartphone — all without the need to create a hotspot to control it.

Apple's anxiously awaited iPhone 8 with a 5.8-inch OLED display is all set to launch this September, alongside the iPhone 7s variants. However, according to MacRumors, which cites information from a number of Barclays analysts, stock will be very limited, and most won't ship until late in the fourth quarter.

The Raspberry Pi is a credit card-sized computer that can crack Wi-Fi, clone key cards, break into laptops, and even clone an existing Wi-Fi network to trick users into connecting to the Pi instead. It can jam Wi-Fi for blocks, track cell phones, listen in on police scanners, broadcast an FM radio signal, and apparently even fly a goddamn missile into a helicopter.

An app from the development team at ts-apps has the potential to make your Android device smarter than it's ever been. At first glance, you'd think it's just an ordinary home screen folder—but depending on what you're doing at a given time, the folder can show a completely different set of apps.

Google is on a mission to bring a better messaging experience to Android users. We've seen them try and fail over the years with various messenger apps, but this time, they're taking a different approach by working with industry leaders to create a new messaging standard. The result is RCS Universal Profile, or simply Chat, and it's finally catching on.

We don't know exactly what form 5G cellular technology will take, but it intends to bring faster Wi-Fi-like performance to mobile devices. While that'll provide major advantages to lots of connected technology, PC Magazine notes that it could be what augmented and mixed reality needs to become widely adopted.

The awesome thing about Android is that you rarely need to settle for what comes stock on your device. If your music app sucks, switch it. If you don't like your home launcher, swap it for a better one.
A shady practice in place by AT&T and Verizon Wireless—and possibly more wireless carriers—was recently uncovered. Outgoing data requests sent from devices on these service providers are being injected with a Unique Identifier Header (UIDH) that allows websites, the carriers, and potentially even government agencies to track your online activity.

No matter how organized your workspace is, chances are you still wind up with tangled cords dangling off your desk. Sure, there are a lot of ways to keep your cables separate, from strategically placed binder clips to stretchy socks, but none are as fun as using a LEGO minifigure.

I've already showed you how to magically unlock your Samsung Galaxy S3 with the simple wave of a hand, but why stop there? Sure, you could go out and purchase a Samsung Galaxy S4 so you have Air Gestures that let you control the lock screen, SMS, sound, wireless, and more.

People are always looking for ways to save money, and for the most part, saving money and cheating the system are synonymous when it comes to things like free internet access. Practically every new gadget is capable of connecting to the web, which means more and more people are looking for ways around those hefty internet bills.

This two part segment will show you how to use the Wi-Fi tethering mobile hotspot functionality on your Motorola Droid Bionic smartphone for free after rooting it. Segment 2 of the guide will walk you through using Radiocomm to hide your tethering usage from Verizon Wireless so you're less likely to get caught.
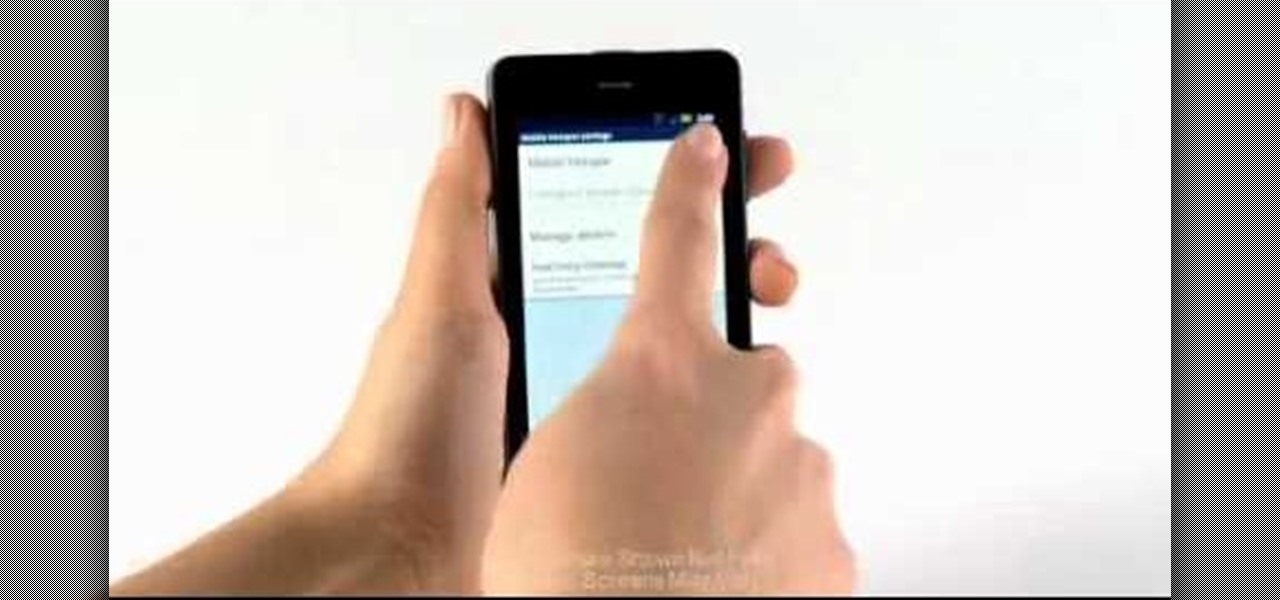
There are so many different devices today that have Wi-Fi capabilities--notebooks, handheld gaming devices, tablets, and more. Why not share some of the 3G and 4G internet that streams into your Motorola Droid 3 with the other electronics you carry with you? You can turn your Verizon Wireless Droid 3 smartphone into a mobile Wi-Fi hotspot using the mobile hotspot menu on the android phone.
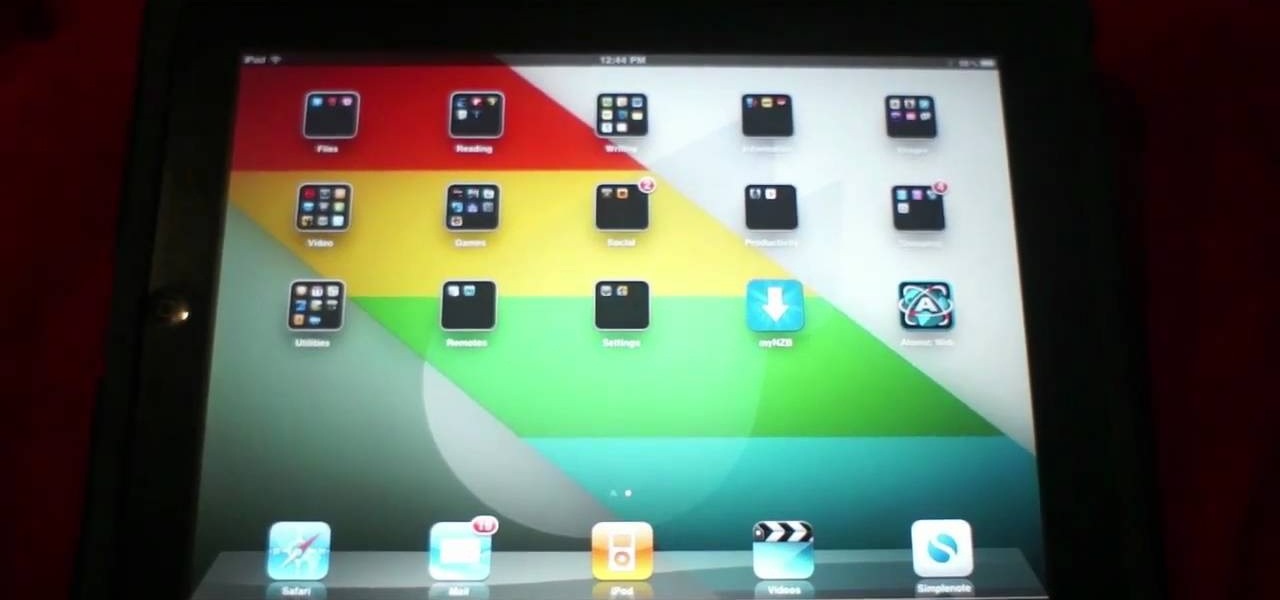
With the new iOS 4.2 (and 4.2.1) firmware for all mobile Apple devices, printing from your iPhone, iPad or iPod Touch has become easy… well, maybe not. Despite the new AirPrint software in iOS 4.2, it can still be difficult to print papers and photos from your mobile device since Apple removed AirPrint from the Mac OS X 10.6.5 software update, due to some kind of legal dispute.

The Canon EOS 7D digital SLR is the first Canon EOS camera that can trigger off-camera Speedlites with the cameras build in flash. The integrated Speedlite transmitter is fully compatible with the Wireless E-TTL Flash System. See exactly how all this works and how to use your flash functions.

Make your router run on VTEC by injecting it with Tomato Firmware. Tomato Firmware gives you excellent tools such as being able to monitor bandwidth consumption, boost WiFi signal, track results with graphics and much more.

The iPod has become a common household item. With each new release, the iPod comes with more features, a steady progression from music to videos, and now as a phone. But did you know that there's a way to turn your iPod into a remote control? Take a look at this instructional video and learn how to give your iPod remote control features with some internal tweaking. You need a Logitech bluetooth wireless set in order for this mod to work.

It may be intended as a toy, but this gizmo can be hacked for more than just watching a remote-controlled car's video spy cam. This HUD (heads-up display) comes with the Wild Planet Spy Gear Video Car, but it's said that you can purchase the video headset separately. And it's not really a HUD, because you can't see through the video images, but it's close enough to be handy for all sorts of things, like computers, iPods, robots, wireless cameras, and gaming. Who wouldn't like to Call of Duty ...

Want to boost your WiFi reception? Have an extra wok or parabolic collander? This video tutorial demonstrates a simple hack that will allow you to build an effective radio antenna that will significantly increase the gain of your WiFi signal. To replicate this hack at home, you'll need the following items: (a) a piece of parabolic cookware, (b) heavy tape, (c) a USB WiFi stick, (d) tin snips, and (5) a USB extension cable. For detailed instructions on building your own wireless signal extende...

Does your video camera not have a headphone jack? This cool idea enables you to use a pair of headphones to monitor what your video camera is hearing in real time.
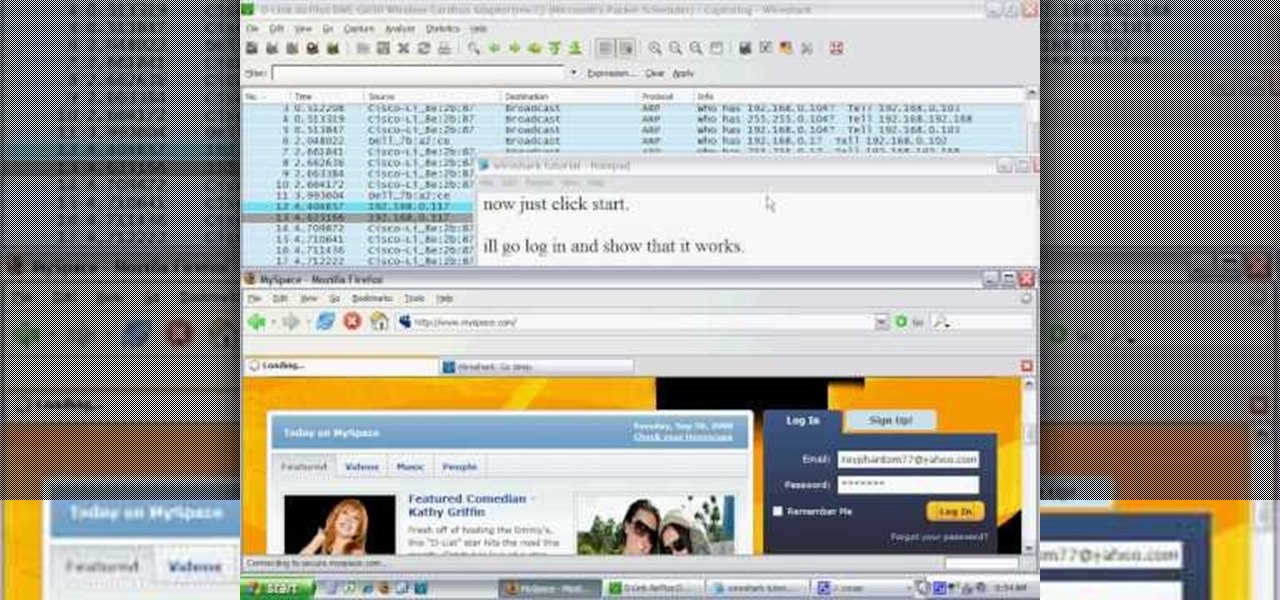
If you're trying to hack someone's wifi, a useful bit of software you may want to try is called Wireshark. Wireshark is a wifi packet sniffer, which is an essential step in actually breaking into someone's wireless system. Of course, this is illegal, so make sure you're only doing it to test a network's security, or for your own educational purposes. Check out the video, follow the steps and see how secure network is. Hack, hack, hack!