
In an effort to get more folks to use the company's check-in service, Facebook is now offering access to free Wi-Fi hotspots in local businesses. It's only in beta right now, but they are looking to expand if they decide to continue the program. Users who check-in on Facebook while at one of the partnered businesses will be automatically directed to the business's Facebook page. Some of the businesses give deals or special offers to customers who check-in. Facebook provides these businesses w...
Ever found yourself not able to connect to a Wi-Fi network on your Android device that you know damn well was there? The worst part is that you know it's your device, because you can see everyone else around you on that network! WHAT GIVES?!? Well, maybe it has something to do with your phone’s Wi-Fi country code!

For some, Halloween is all about the candy. For others, it's more about causing trouble. There's nothing wrong with a good laugh, but no one wants to be the target of a prank that will entail lots of cleaning later.

The team behind the Pwn Plug, a little white box that can plug into any network and access it remotely, is at it again. This time, Pwnie Express is working for DARPA to create a hacking machine that looks like a power strip, cleverly called the Power Pwn. The device has wireless, ethernet and Bluetooth capabilities and can do a full-scale penetration test as well as bypass NAC and other security measures automatically. It has three modes: Evil AP, stealth mode and passive recon. In stealth mo...

It's no secret that water and electronics don't mix well, but somehow, people always manage to combine the two. I've had my fair share of water-damaged electronics, everything from cheap headphones to a desktop computer. My devices are getting dunked in water so much, it's like doughnuts in coffee. And I know I'm not the only one. That jam session with your favorite song will end really quick when your iTouch is chilling in the toilet bowl.
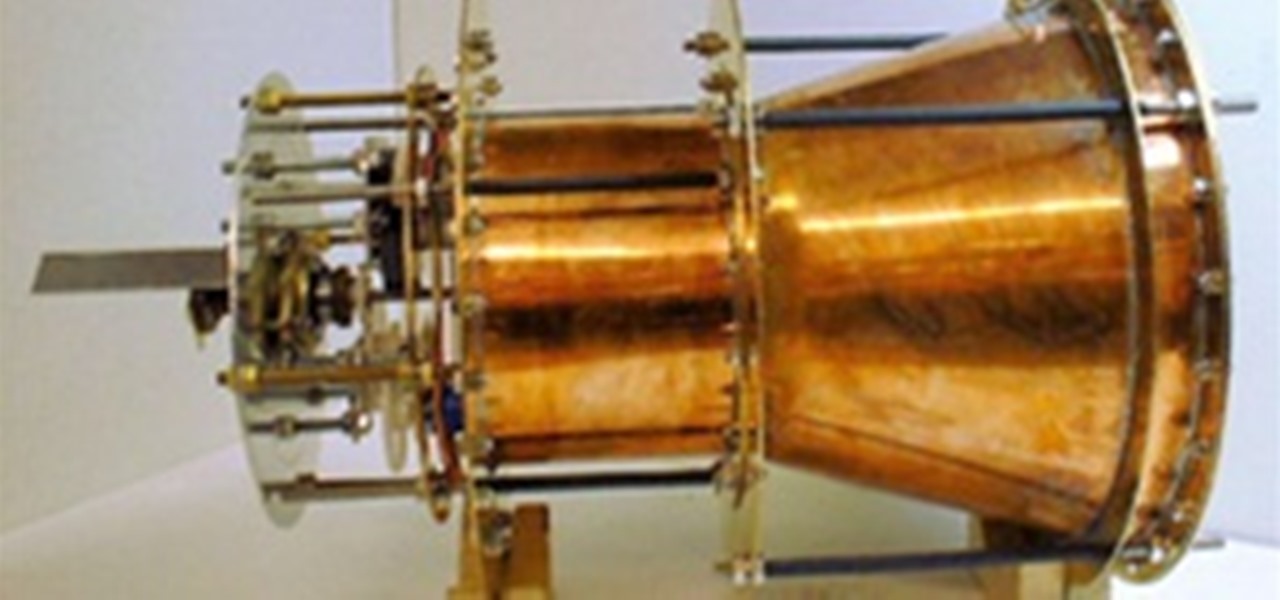
Welcome to Microwave Energy—the next part of my Making Electromagnetic Weapons series. For the Electromagnetic Pulse Generator, check out the last three articles (One, Two and Three).

As I was listening to Apple's WWDC conference today, what ran through my mind the most is if there were ever a time to switch to the world of Apple computing now is it. Today's WWDC keynote presentation was chock-full of new and updated iOS mobile software—too much to cover in this one article. But the most "new thing" coming from Apple this Fall is iCloud, a file sharing and streaming service that requires no wired connections.

Android's answer to the BlackBerry is here, and it's called the DROID Pro. Verizon Wireless officially starts selling the Motorola DROID Pro in stores today, November 18th, and you can get your DROID Pro online, too. Verizon states the full retail price at $479.99 with a final price of $179.99 with a two-year contract (after a $100 mail-in-rebate).

UPDATE: New York Giants WON! Super Bowl XLVI has concluded. The New York Giants beat the New England Patriots 21 to 17. If you missed the big game, there doesn't seem to be a full replay of all the action, but you can visit NBC.com or NFL.com to get information and video highlights on the game and player interviews, as well as a list of all of the records broken and tied.

Remember the good ol' days when you actually had to swipe your credit or debit card to make a payment at the store? Now all it takes is a flick of the wrist to purchase goods with your card, thanks to RFID (radio-frequency identification) technology from Chase (blink), Visa (payWave) and MasterCard (PayPass). But soon "contactless" payments will be made by an entirely different beast—NFC, which stands for near field communication.

Earlier this month, game developer David Braben and his Rasberry Pi nonprofit foundation revealed a $25 USB PC. The computer can connect to an HDMI monitor on one end, and a USB peripheral on the other (such as a keyboard or a USB hub). You can use the USB hub to connect multiple items, such as a keyboard, mouse, printer, USB ethernet/wireless, creating a fully functional computer.

By now, many of you may have heard about iPhone tracking and recording your location data, but is there anything else being extracted from cell phones without our knowledge? If you're a Michigan state resident, the answer is an alarming "maybe".

The Motorola XOOM was just released last week to Android-hungry fans waiting the next best thing to Apple's iPad. But should it have been released, considering Verizon's switching to the 4G LTE network soon?

Join the Pilot program and learn how to fly! But you're not going to be flying airplanes in this Pilot program, you'll be trying your hands at Google's first laptop computer.

Giveaway Tuesdays has officially ended! But don't sweat it, WonderHowTo has another World that's taken its place. Every Tuesday, Phone Snap! invites you to show off your cell phone photography skills.

A practice amplifier can be just about anything, but by definition it’s probably not something you are going to gig with.

This is my fourth (and final) installment on SCRABBLE adverts. I'm sure there's a lot I haven't found, but that's for another day. But this post features all of the remaining SCRABBLE advertisements (prints and posters) that haven't already been listed in my previous posts:

Before you go running off to the Apple store, you may want to educate yourself. DVICE is kind enough to compile the 20 biggest complaints about the iPad from a whole slew of reviewers.

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

Grab your thinking caps and get your hack on. Null Byte is officially seeking contributors on a weekly basis who are willing to take the time to educate the Null Byte community on anything, from hardware hacks to life hacks. Contributors that write tutorials will be featured on the Null Byte blog, as well as the front page of WonderHowTo (providing it's up to par, of course).

WonderHowTo is made up of niche communities called Worlds. If you've yet to join one (or create your own), get a taste below of what's going on in the community. Check in every Wednesday for a roundup of new activities and projects.

We're officially seeking Null Byters on a weekly basis who are willing to take the time to educate the community. Contributors will write tutorials, which will be featured on the Null Byte blog, as well as the front page of WonderHowTo (IF up to par, of course). There is no need to be intimidated if you fear you lack the writing skills. I will edit your drafts if necessary and get them looking top-notch! You can write tutorials on any skill level, and about anything you feel like sharing that...

How did it happen? How did your ultra-secure WPA password on your wireless network get broken into? Well, you might have just found yourself at the mercy of a cracker.

Paying for web hosting isn't ideal in most situations. If you have your own website, hosting it yourself is very acceptable and easy to do, assuming your internet bandwidth permits. Most people want to run a personal site, nothing crazy, so hosting from home on low-bandwidth internet is actually a better solution in most cases.

I've seen numerous tutorials on how to create a "strong" password. This makes me laugh. These titles imply "one" password, which is wrong in and of itself. A person should have many passwords, all different, and all extremely long. People may ask how they're supposed to remember lengthy passwords and why their current password isn't good enough. Well, I'm going to show you.

The HP Touchpad 64 GB is out in action with a robust processor and additional applications in the market. Using the best technology on earth, it is looking forward to give a tough fight to the Apple’s iPad 2. The 64 GB HP TouchPad sound more promising to its predecessors. The experts feel that the two device, HP TouchPad 64 and Apple’s iPad-2 is more or less the same. Let’s have a glance over the device by discussing the various features it encompasses.

For Windows laptops and PCs it's easy to install Linux. However for Macs, it's a different story. There are people installing Ubuntu on Macbooks and so far I've noticed that they are using 9.10. I've remastered my own Ubuntu 10.04 complete with playing flash videos and other applications already pre-installed on a DVD. Plus, it can boot on laptops with Nvidia graphic cards. If you'd like to see my workaround for Nvidia check out my article on remastering Ubuntu.

Our hacked Kinect series has demonstrated amply how the Kinect is changing the worlds of business, art, medicine and robotics. But where does it go from here? That will be determined by the thousands of dedicated DIYers out there doing work like you've seen here over the last week.

Sure, you go online to email and shop and do research. But have you ever been curious about how the internet actually works? Don't worry, you don't need a degree in computer science to get a handle on how your info gets from point A to point B. Learning the basics of the internet will give you a whole new appreciation for all those emails and chat messages that seem to magically appear. Get ready, because we're about to enter the wonderful world of digital data!

This German video is amazing. A joyously analog interpretation and deconstruction of the digital gaming experience. Malte Jehmlich is as primitive and inspiring as the the Vanuatu natives who devoted themselves to cargo worship after World War II!

Oh, LifeHacker, we love you. You've brought us so many handy HowTo's: Hack Wireless Internet, Bypass Blocked Websites, Convert a Laptop Into a Projector, Watch TV & Movies on the Web For Free, 10 Must-Know Google Privacy Settings, and more.

As 2009 comes to a close, the Telegraph presents a compilation of this past year's wackiest inventions. As always, here at WonderHowTo, we are inspired and impressed by ingenuity. The contraptions below range from utter silliness (engagement ring bra) to downright amazing (see-through concrete). Check it out.

Did you know that you can use Gmail to make free phone calls to anywhere in North America? We're not talking computer to computer, but actual free phone calls to cell phones and home phones. All you need is a Gmail account, a microphone, and speakers plugged into your computer.

A Self-Protection Guide 1) You can help protect yourself from violent crimes.

The DROID 2 from Motorola came out last August, but it's just now exploding— literally. The 33 News reported yesterday that a Motorola DROID 2 smartphone exploded in the hands of Aron Embry from Cedar Hills, Texas. He was making a phone call outside his home when he heard a POP sound— blood was dripping down his face and the glass was broken around the phone's speaker— his DROID 2 cell phone actually exploded against his ear. He ended up getting 4 stitches and a CAT scan, but thankfully, he d...

At $349, you won't find many smartphones that provide a better deal than the Google Pixel 4a. It has flagship-level performance, a headphone jack, and one of the best smartphone cameras on the market, all for less than $400. But if you act now, you can save even more.

This prank has to be where people walk all the time.... You start off by putting portable or wireless speakers that would play a playback of car tires skidding on the ground, in cylinder shaped trash cans right by a busy street full of cars and where a lot of spectators would walk or cross. Then step away and wait for a group of people or an individual to walk by the trash cans, then play the sound and watch everybody suddenly run or jump, expecting a car to crash somewhere....It's funny beca...

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

In my Wireshark article, we talked a little bit about packet sniffing, but we focused more on the underlying protocols and models. Now, I'd like to dive right back into Wireshark and start stealing packets.








































