Welcome back, my nascent hackers! Like anything in life, there are multiple ways of getting a hack done. In fact, good hackers usually have many tricks up their sleeve to hack into a system. If they didn't, they would not usually be successful. No hack works on every system and no hack works all of the time.

Welcome back, my greenhorn hackers! Continuing with my Wi-Fi hacking series, this article will focus on creating an invisible rogue access point, which is an access point that's not authorized by the information technology staff and may be a significant security vulnerability for any particular firm.

If you plan on listening to music or making phone calls, you're going to have to get some headphones or a headset with mic (in lieu of Bluetooth headsets). Using them might just be the simplest thing to do on the Samsung Galaxy Tab, but just in case, this video will show you how to plug in your headset cable. It's just like any other Android device.

This video is about how to get free ringtones for a Verizon wireless phone. First you need a Verizon wireless phone with Vcast. You can either have or not have a micro SD card. You need a phone with Bluetooth. First go to your email, then where it says to put vzwpix.com you don't need a subject on the email but you need to type in your phone number. You have to also be able to get picture txt. Then next you need to open a new window and go to MyTinyPhone and enter in the ringtone you want. Fi...

On May 17, Apple announced that Lossless Audio playback for Apple Music was finally coming to subscribers in June. The long-awaited option will let users stream songs at a much higher quality than ever before. Still, in the fine print, Apple noted that you wouldn't be able to listen to the best sound quality — Hi-Resolution Lossless — on your iPhone without a DAC.
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Your home has walls for privacy, but Wi-Fi signals passing through them and can be detected up to a mile away with a directional Wi-Fi antenna and a direct line of sight. An amazing amount of information can be learned from this data, including when residents come and go, the manufacturer of all nearby wireless devices, and what on the network is in use at any given time.

A man-in-the-middle attack places you between your target and the internet, pretending to be a Wi-Fi network while secretly inspecting every packet that flows through the connection. The WiFi-Pumpkin is a rogue AP framework to easily create these fake networks, all while forwarding legitimate traffic to and from the unsuspecting target.

It's Monday, and what's a Monday at Gadget Hacks without a new leak to ponder over? Thanks to known leaker Benjamin Geskin, we have a dummy iPhone 8 without one of its most-anticipated features.

Yes, I understand some people may consider this a repost. However, I have been searching for this answer for 3 weeks and after reading numerous reddit post, Kali Forums post and Null byte post I finally have gotten it to work for me. I would like to compile and share this information with you guys.

Hello there learners and readers! I figured I'd show you guys my problem and how I solved it, hoping that it would help people who are facing the same issue. Today, we'll be talking about the solution of

Whether I'm in my car or making dinner, I always have music playing. And since I don't like to keep my headphones on me at all times, I end up using my Android's built-in speakers a good portion of the time.

Welcome back, my nascent hackers! In previous tutorials for my Wi-Fi Hacking series, I have shown you how to crack WEP and WPA2 passwords, break a WPS PIN, and create Evil Twin and Rogue access points. In this continuation of the series, let's look at slightly different approach to attacking wireless.

Video: . At a certain moment in our lives all of us wanted to be a fire fighter. To simulate that effect, we created a super-awesome siren. With two 555-timer chips and lots of trail and error, we were able to create this awful noise.

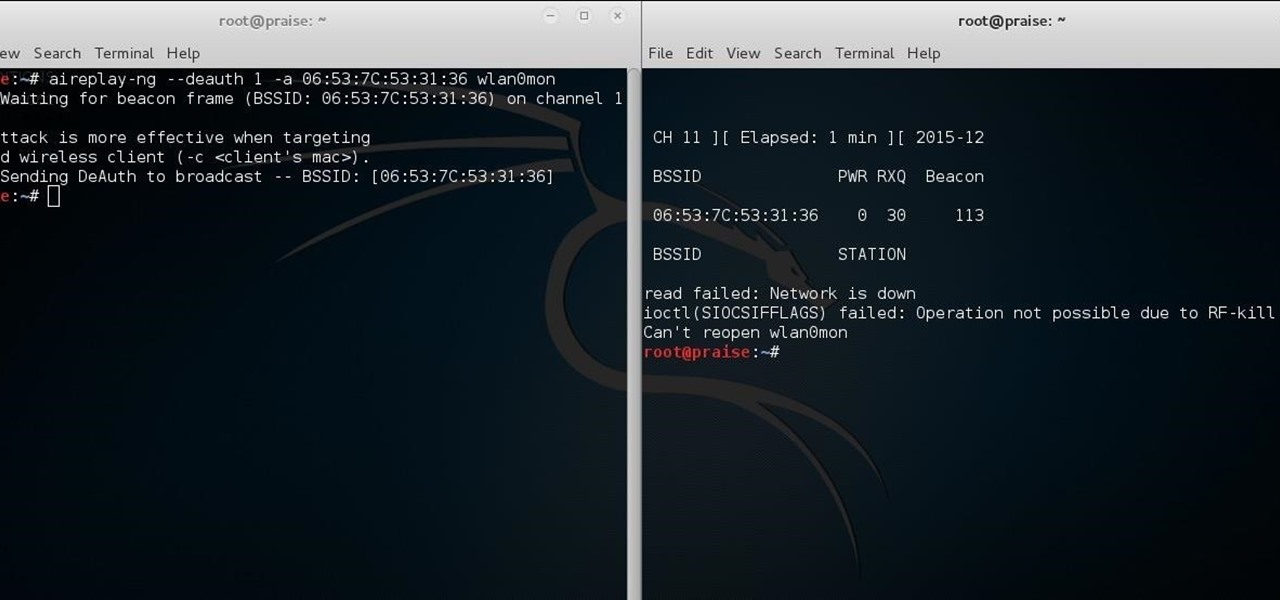
Welcome back, my greenhorn hackers! Now that we're familiar with the technologies, terminology, and the aircrack-ng suite, we can finally start hacking Wi-Fi. Our first task will be to creating an evil twin access point. Many new hackers are anxious to crack Wi-Fi passwords to gain some free bandwidth (don't worry, we'll get to that), but there are so many other Wi-Fi hacks that are far more powerful and put so much more at risk than a bit of bandwidth.

Nikola Tesla is one of the most tragic figures in the history of science, a history that is practically filled to the brim with tragic figures. Francis Bacon, a 16th century philosopher and scientist, caught pneumonia and died because he was trying to stuff snow into a dead chicken. Marie Curie died as a result of her long-term exposure to radioactivity, and her papers from the 1890s are too radioactive to touch without protective gear to this day.

The original NES controller has become one of the most recognizable symbols of the Nintendo gaming culture, thanks to its perfectly rectangular shape and simple button design. But despite its popular appeal, people just don't game with them anymore. So, what do they do with them? They savor the memories and turn it into something more useful, like a light switch.

We will be setting up a portable radio in the mountains. It will be established in a clearing with available rocks for setup. The equipment we will be using is a Yaso radio with microphone and headphone, coaxial cable, slight line and weight, 13.5 battery pack, 2o and 40 meter antenna, pen and paper to record contacts.

If you need to replace or remove the battery, sim card, or SD card from your new Droid Bionic by Motorola, take a look at this walkthrough on how to remove the back of the case and gain access to all three pieces of the Android smartphone. Yes, you heard right. The Verizon Wireless phone does use a sim card because of its 4G connection.

This video shows you how to set up and hide mini wireless spy camera. Where you put it is up to you. Who you spy on is up to you. If you're wanting to keep an extra set of eyes on someone, watch and learn. Whether it's your bathroom or kitchen, put your eyes on the prize.

In this clip, you'll learn how to jailbreak and unlock an iPhone 3G running iOS 4 for use on the T-Mobile wireless network. For more information, including detailed, step-by-step instructions, and to get started jailbreaking and unlocking your own iOS 4 iPhone 3G, watch this hacker's how-to from Zedomax.

The Droid Incredible cell phone by HTC brings the newest Google application right to your fingertips. With "Near me now" Google Search uses your current location to let you search for restaurants, ATMs, gas stations, and more! Verizon Wireless gives you tips on how to search Google on the Incredible Android device.

The Google Android Market offers you thousands of free and for purchase applications to download to the HTC Droid Incredible cell phone. In this video, Verizon Wireless shows you how to navigate the Android Marketplace and download the newest and coolest Android apps.

You can customize the seven home screens on the HTC Droid Incredible cell phone by adding widgets, changing the live wallpaper, and creating scenes to fit your lifestyle. Live wallpapers move and respond to your touch and changing scenes is a quick way to match the Incredible to your current status. Verizon Wireless shows you how to personalize your phone.

Getting to know your HTC Droid Incredible cell phone will help you fully experience its benefits. In this video tutorial, Verizon Wireless shows you some basic navigation tips for the home screen for getting started with your Android device.

Watch and learn how to stay in touch with your friends and family on the HTC Droid Incredible cell phone. Verizon Wireless shows you around the Android platform on the Incredible, highlighting the "People" widget and "Friend Stream" icon to work with your contacts and social networks (Twitter, Facebook, Flickr).

Just because you have more than one Gmail account doesn't mean you can't view them all on your HTC Droid Incredible cell phone. Verizon Wireless teaches you how to add multiple Gmail accounts to the Incredible's Android platform, making it easy to get all your emails as soon as they arrive.

One of the coolest new features available on HTC's new EVO 4G cell phone is the ability to create Sprint Hot Spots with your phone and tether other devices to it. In this clip, you will receive a great step by step tutorial on how to set up your Hot Spots and use it to tether up to 8 other devices. Begin using your cell phone as a wireless modem anywhere you may be with this instructional clip from Fommy.

Looking a way to share a wired Internet connection? With an Apple computer, it's easy! So easy, in fact, that this home computing how-to from the folks at CNET TV can present a complete (and somewhat talky) overview of the process in just under a minute's time. For the specifics, and to get started creating your own WiFi hotspots, just watch this handy how-to.

The beauty of the iPod Touch is that it is not only for music. With the iTouch, you can access the Internet as well. You can use this Internet capability to download from iTunes, get e-mail, surf the web and many more options. In this tutorial, learn exactly how to turn your iPod on to a WiFi network so that you can take advantage of all the features your new device has to offer.

The XBee is a wireless radio module that allows you to implement a cheap and easy wirelss interface between two kinds of devices. This video will walk you through each step of configuration for your XBee. Modify it and add it to your next creation, whether it's a robot, machine, or something else from your imagination. The possibilities are endless!

This video shows how to setup and use your DynaSpy wireless video surveillance camera.

From booting into Fastboot mode with a single command to installing mods without root access, there's no shortage of reasons to use ADB. The catch, though, you had to be tied to a computer with a USB connection. However, a new feature in Android 11 finally allows you to run ADB commands over Wi-Fi instead of being tethered.

The entire wireless industry is working overtime to convince the world that 5G, and the higher prices associated with the faster speeds it affords, will not only be worth it but will deliver never-before-seen wonders. But few companies have produced such a stunningly well-done sales job as Three, one of the leading wireless giants in the UK.

As Magic Leap continues to spread its influence in the US with the help of wireless carrier AT&T, the augmented reality startup is also working its way into East Asia.

After delaying its launch by four months, LG revealed its 2018 entry to the flagship market on Wednesday, May 2. After years of an underperforming mobile division, the LG G7 ThinQ is the first product since a shakeup within the division to get things back on track, and it brings a number of upgrades over its G6 predecessor.

Google and Samsung are the biggest players in the Android world. Despite a rocky launch, Google's Pixel 2 XL became one of the premier Android devices of 2017, headlined by fast performance and a pure version of Android. Still, many users prefer Samsung's offerings, and their Galaxy S9+ is poised to be the phone to beat in terms of specs.

Welcome, my hacker novitiates! As part of my series on hacking Wi-Fi, I want to demonstrate another excellent piece of hacking software for cracking WPA2-PSK passwords. In my last post, we cracked WPA2 using aircrack-ng. In this tutorial, we'll use a piece of software developed by wireless security researcher Joshua Wright called cowpatty (often stylized as coWPAtty). This app simplifies and speeds up the dictionary/hybrid attack against WPA2 passwords, so let's get to it!

Welcome back, my rookie hackers! When Wi-Fi was first developed and popularized in the late '90s, security was not a major concern. Unlike wired connections, anyone could simply connect to a Wi-Fi access point (AP) and steal bandwidth, or worse—sniff the traffic.

Why do we still need to plug in our phones to charge them? Wireless charging exists, and has for quite some time, but most manufacturers don't include it in their devices. When it comes to the Samsung Galaxy S4, you can buy a QI-compatible wireless charging kit, but between the charging pad and the battery cover, you're looking at around $90 or more.