In this Null Byte, we are going to be installing Packet Injection capable drivers in Linux. These are the open-source drivers required to sniff wireless traffic, inject packets to crack a wireless access point, and go into "monitor-mode". These drivers are superior because they are the fastest available drivers.

In this Computers & Programming video tutorial you will learn how to encrypt a D-Link router with WEP password protection. First you connect to your wireless network. Open your browser and type in http://192.168.0.1. Type in your base station username and password and press OK. Under the SETUP tab, select WIRELESS SETTINGS, scroll down to 'Wireless Security Mode' and select 'Enable WEP Wireless Security'. Scroll down to WEP. Under WEP Encryption pull down menu select 128Bit. Now create a pass...

Ever since kernel 2.6.xx in Linux, a lot of the internet kernel modules for wireless interfaces ended up becoming broken when trying to use monitor mode. What happens commonly (to myself included) is a forced channel that your card sits on. No good! For users of airodump and the aircrack-ng software suite, the software has become unusable.
In this video tutorial, viewers learn how to set and encrypt the wireless password using WEP Apple Airport. Begin by opening the Apple Airport utility program. Then find the network's name and double-click on it. The Configure "Apple Airport Express" opens, click on the Airport tab. Then click on the Wireless Security button. Now click on the Wireless Security drop-down menu and select 128-bit. Click on the Set WEP Password button, type in the password and verify it. Finish by clicking on Upd...

In this video tutorial, viewers learn how to disable SSID broadcast on a NETGEAR router. Begin by opening your browser and go to the site: Router Login. Then type in your user name and password. Click OK. In the sidebar under Setup, click on Wireless Settings. In Name (SSID), type in a new network name and click on Apply. In the sidebar under the Advanced, click on Wireless Settings. Type in your user name and password once again, and click OK. Under Wireless Router Settings, uncheck Enable S...

Watch this video to learn how to encrypt Wi-Fi using WEP password on Linksys in 4 simple steps. Connect to your wireless network. Open your Web browser and type in the web address http://192.168.1.1. Press enter key. Type in the User Name for your network. Type in the Password, press OK button. Select the Wireless text tab, select the Wireless Security text item. Pull down and select the WEP menu item. Type in a good password. Click the Generate button. Click the Save Settings button. Encrypt...

Jeremy at GamerTell shows us how to connect our X-Box 360 to the internet VIA Windows Vista and a Laptop Computer that is already connected to a wireless network. First we have to connect your laptop to your X-Box 360 using an Ethernet cable. Now we will turn on the Xbox 360. Make sure you are on the correct TV Input or channel. Now go to your laptop and Click on the start button on your laptop and find control panel. Once your in control panel select Network and Internet. Now we will select ...

In this video tutorial, viewers learn how to set and encrypt your Wi-Fi password using WPA on a Linskys router. Begin by opening your web browser and type in the address: Click Enter. Now type in your user name and password, and click OK. Then click on the Wireless tab and select Wireless Security. In the Security Mode drop-down menu, select WPA Pre-Shared Key and then type in a password under WPA Shared Key. Finish by clicking on Save Changes. This video will benefit th...

In this video tutorial, viewers learn how to disable their Wi-Fi SSID broadcast on a Linksys's router. Begin by opening your web browser and type in this address: Press Enter to access the page. Then type in your user name and password. Click OK. Now click on the Wireless tab and check Disable under "Wireless SSID Broadcast". Finish by clicking on Save Changes. This video will benefit hose viewers who use a Linksys's router, and would like to learn how disable their broa...

I have had a lot of people ask me, "How does my neighbor keep getting into my wireless?!". Chances are, these people are all using WEP, a deprecated wireless encryption protocol. Either that, or you are using one weak WPA passphrase.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Consumer Electronics for Dummies. Just watch this video tutorial to learn how to position home theater surround-sound speakers, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. This is Mac for Dummies. Just watch this video tutorial to learn how to set up a WiFi network on a mac, For Dummies.

DD-WRT is a Linux firmware available for many Linksys, NetGear, Belkin, D-Link, Fon, Dell, Asus and other vendor's wireless routers. DD-WRT is far more feature rich than the stock firmware that comes with most routers. This video covers the basics of installing and configuring DD-WRT. Install and configure DD-WRT firmware on your router.

10 conversational Spanish phrases that you can use in a coffee shop. Includes ordering drinks and asking about wireless Internet. Subtitles are included for help with pronunciation. Speak Spanish at a coffee shop.

In this video tutorial, viewers learn how to find their computer's MAC (or physical) address in a Windows computer. This task is very easy, simple and fast to do. Begin by clicking on the Start menu and open the Run program. Then type "cmd" in the Run box and press OK. When the black command prompt opens, type in "ipconfig /all" and press Enter. The computer's MAC address will be listed as Physical Address under Wireless Network Connection. This video will benefit those viewers who use a Wind...

In this tutorial, we learn how to set and encrypt a Wi-Fi password using WPA in Netgear. First, type "www.routerlogin.net" into your internet browser. Next, a pop-up window will appear, type your user name and password into this dialog box. A new window will pop up, click on the tab on the left hand side of the screen that says "wireless settings". Type in your user name and password once more, then find where it says "security settings", and click on the "WPA-PSK" radio button. Now, make a p...

In this video tutorial, viewers learn how to set and encrypt a NET-Gear router with WEP password protection. Begin by opening your web browser and go to the router website: Router Login.. When the Prompt window appears, type in your router user name and password, and click OK. In the sidebar, under Setup, click on Wireless Settings. Once again, type in your user name and password, and click OK. In the Security Options, check WEP (Wired Equivalent Privacy). Then select the Pass-phrase box, typ...

This video demonstrates how to connect a Mac to an ethernet network. From the people who brought you the Dummies instructional book series, brings you the same non-intimidating guides in video form. Watch this video tutorial to learn how to connect a Mac to an ethernet network, For Dummies.

In this video tutorial, viewers learn how to set and encrypt their Wi-Fi password using WPA in Apple Airport. Begin by opening the Airport Admin Utility application from the CD. Then locate your the name of your network and double-click it or press the Configure button at the bottom right of the screen. Now enter your password and click OK. The network should be opened now. Then click on the Airport tab and click on Wireless Security. In the pull-down menu, select WPA2 Personal. Then click on...

Watch this video from This Old House to learn how to create zones in a hot water system. Steps:

Wireless contracts and phone-buying programs continue to become more and more confusing. As if you didn't have enough to worry about with regards to the rising costs of services and the elimination of contracts with mobile providers, Verizon Wireless will soon institute a new charge that puts the grub in "money-grubbing." Sadly, this isn't one of those April's Fools pranks that are running rampant on the web today. Starting next week, the largest mobile phone provider in the United States wil...

Often times when staying at a hotel or anywhere for that matter, you'll whip out your laptop and check the local area for Wi-Fi. I know you've all been in my shoes when you find an unsecured network that appears to be public Wi-Fi belonging to the hotel or airport, and you connect to it. You connect fast and perfectly, only to find that when you open your browser, it says you don't have an account, and are filtered from accessing the web. This is because the owners of the network want to keep...

UPDATE: Verizon has posted their support document, with everything you need to know about this update. Last week it was Sprint's turn to push out Android 4.4 KitKat for the HTC One, and today it's Verizon Wireless who's up to bat.

It seems like Apple is always releasing something new, so there must be a lot of lonely iDevices out there going unused, right? With Seedio, you can make the most of your Apple products by connecting them to make one synchronized loudspeaker. As long as all the devices have the Seedio app installed, you can connect as many iPads, iPhones, and iPod touches as you want. All you need is a wireless connection. You can play music from anywhere: your library, YouTube, or the Web. It also works as a...

Welcome to the second part of the Arch Linux installation tutorial! We are installing Arch because of the amount of users who want to learn how to get into Linux. Arch is a simple, minimalistic distro, designed not to hold the users hand, but to push them to know their system and customize it to the core. This will make you feel accomplished, as well as give you the extra edge of being knowledgeable of the GNU/Linux operating systems.

SSL stands for Secure Socket Layer. It's an encryption standard used on most sites' login pages to avoid their users' passwords being packet sniffed in simple plain-text format. This keeps the users safe by having all of that traffic encrypted over an "https" connection. So, whenever you see "https://" in front of the URL in your browser, you know you're safe... or are you?

Here at Null Byte, we've spoken a lot about securing and anonymizing traffic. This is a big deal. With all of today's business taking place electronically via computers, we need to be secure when on-the-go. A lot of businesses don't even train their employees to secure their computers to protect from various threats. Here are a few things that should always happen when doing business on computers:

An amazing price for a full featured wireless micro-remote, using the iphone or ipod touch as its brains.

Bluetooth capability allows your mobile phone to connect to a computer, lap top, a wireless head set, or even your car. With most states rushing to pass no cell phones while driving laws, a Bluetooth device keeps you connected. Watch this video cell phone tutorial and learn how to hook up and use the Bluetooth features on your Blackberry Curve. Use the Bluetooth capability on a Blackberry Curve.

Apple shipped their first batch of iPhone X's with an outdated and unpatched version of iOS. Be sure to check for updates and install iOS 11.1 first thing after you open your new iPhone or it'll be susceptible to the KRACK vulnerability for wireless connectivity.

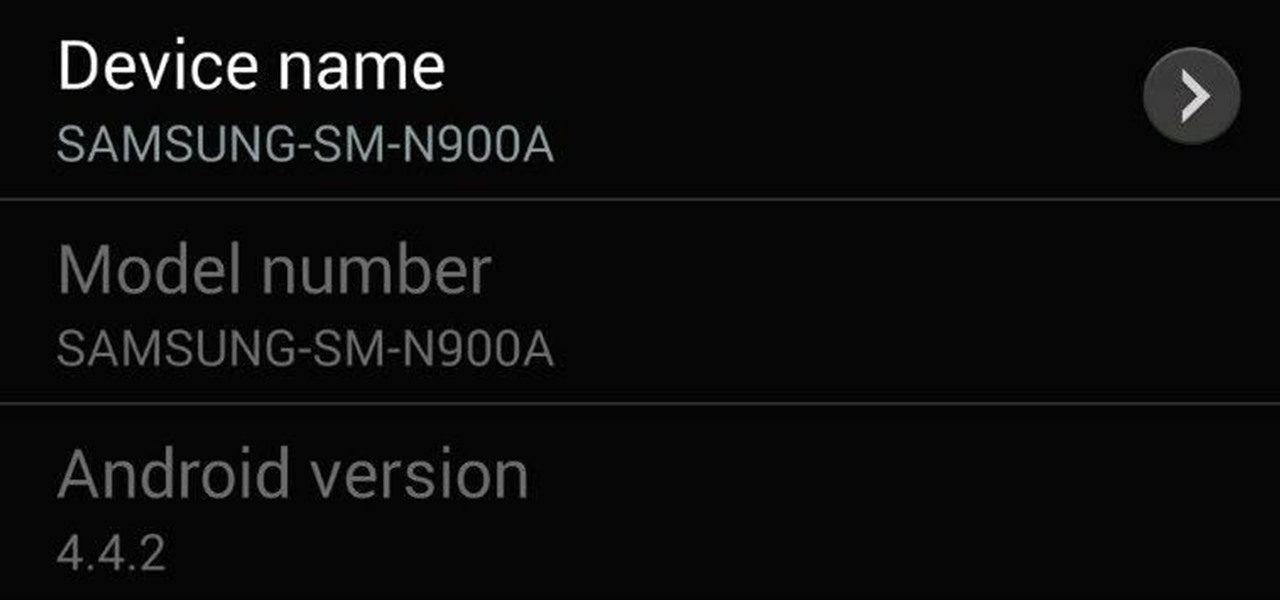
After leaks and rollouts from rival carriers, AT&T has finally released their official Android 4.4.2 KitKat update for the Galaxy Note 3. If you haven't received your update notification, force a manual check by going to Settings -> More -> About Device -> Software Update -> Check for Updates. Make sure you're connected to Wifi and have at least 50% battery remaining. This update includes:

Remember what life was like before your iPhone? Before there were palm-sized smartphones with seemingly endless features, there were phones like Motorola's RAZR that peaked with its embedded camera. Before that, there were simple flip phones with texting capabilities, bulky two-pound Gordon Gekkos—even briefcase phones.

Last year, Hasbro unveiled Scrabble Flash, an electronic version of the popular word game which consists of five SmartLink letter tiles that can communicate with one another using near field communication (NFC) to spell and score words. It's an interesting (and fun) way to build your Scrabble vocabulary for words ranging from two to five letters, but that's about it.

With so many wireless iOS networking apps for the iPhone, iPad, and iPod touch available, there’s very little reason to connect any of these devices to iTunes, except to update the software. Besides, importing and exporting photos using iTunes has never been one of the best features of Apple‘s mobile device process. Let me introduce you to 5 useful apps for importing and exporting photos to and from your iOS device(s).

Wouldn't it be nice to just sit at your buddy's house, plug into his network, and see exactly what he's doing? What if it was as easy as that? What makes packet sniffers like Wireshark such potent tools is that a majority of local area networks (LANs) are based on the shared Ethernet notion.

Julian Oliver created the Transparency Grenade in January 2012 for the Studio Weise7 exhibition at Labor 8. It's a transparent device with a "payload" built from an ARM Chip, an Arduino Nano, a mic, and a strong Wi-Fi antenna. It taps into wireless networks and logs emails, webpages, images, and voice to a publicly available online map showing its "detonation" location. Apparently, development for an Android version (sans the pretty plastic shell) is under way thanks to interested donors. See...

Welcome to Microwave Energy—the next part of my Making Electromagnetic Weapons series. For the Electromagnetic Pulse Generator, check out the last three articles (One, Two and Three).

As I was listening to Apple's WWDC conference today, what ran through my mind the most is if there were ever a time to switch to the world of Apple computing now is it. Today's WWDC keynote presentation was chock-full of new and updated iOS mobile software—too much to cover in this one article. But the most "new thing" coming from Apple this Fall is iCloud, a file sharing and streaming service that requires no wired connections.