Last year, the Washington Post's Ashley Halsey wrote an article on what really happens to your luggage at airports. In it, they unwittingly published a photo of the master keys the TSA uses for TSA-approved baggage locks. Now, thanks to that picture and a French lock-picking enthusiast, anyone with a 3D printer can make their own master keys to unlock any TSA-recognized locks.

Historically, battery life has not been a strong suit for machines running Windows. Poor decisions by hardware manufacturers combined with the resource-hogging behavior of Windows are to blame. However, Microsoft is trying to resolve this issue, once again, with the release of Windows 10.

Dropping upwards of $60 on a new game can really break the bank, and being a struggling college student leaves me having to decide whether to pick up the latest title or, you know, eat. But often my more primitive urges win out, meaning the only way to enjoy the latest and greatest games are vicariously, using increasingly-popular live streams.

People like to cite the iPhone as the device that started the smartphone craze, but the truth is, smartphones had existed for years by the time Apple got into the game. The real groundbreaking feature that this device brought to the table was a multi-touch screen to go along with its "smart" functionality, and this is still the main method we use to interact with our devices today.

Often, despite your favorite makeup mecca's rows and rows of endless colors, applicators, and brands, it's hard to find the perfect shade of lipstick—especially one at the price you want. Rather than resorting to what's available in stores, turn to your stovetop and a box of crayons.

Depending on your child's age, their first smartphone may be a little too open for them, or you, to handle. With essentially a world of information—both good and bad—available at their fingertips, it can seem like a huge hurdle to instill parental controls on their device.

If your Android device wasn't manufactured by Samsung, chances are it uses on-screen navigation buttons. Colloquially referred to as "Soft keys," these have become commonplace due to their flexibility, as well as the fact that manufacturers don't have to include extra hardware buttons with a propensity to fail.

Welcome back, my rookie hackers! As most of you know, Mr. Robot is probably the best hacker TV show ever! This is a great show about a cyber security engineer who is being enticed to hack the very corporation he's being paid to protect. This show is so good, I began a series to demonstrate how to do the hacks he uses in the show.

Researchers at the cyber security firm Zimperium have recently uncovered a vulnerability in roughly 95% of Android devices that has the potential to allow hackers to take total control over your phone with a simple picture message (MMS). The gritty details of this exploit have not been made public yet, but hackers now know the general framework for this type of attack, so you can be certain that they'll hammer out the details in no time.

When I first heard about the Thermomix, an all-in-one kitchen appliance from Australia, it sounded like an old SNL commercial parody: It slices! It dices! It heats! It kneads! Is there ANYTHING this machine CAN'T do?

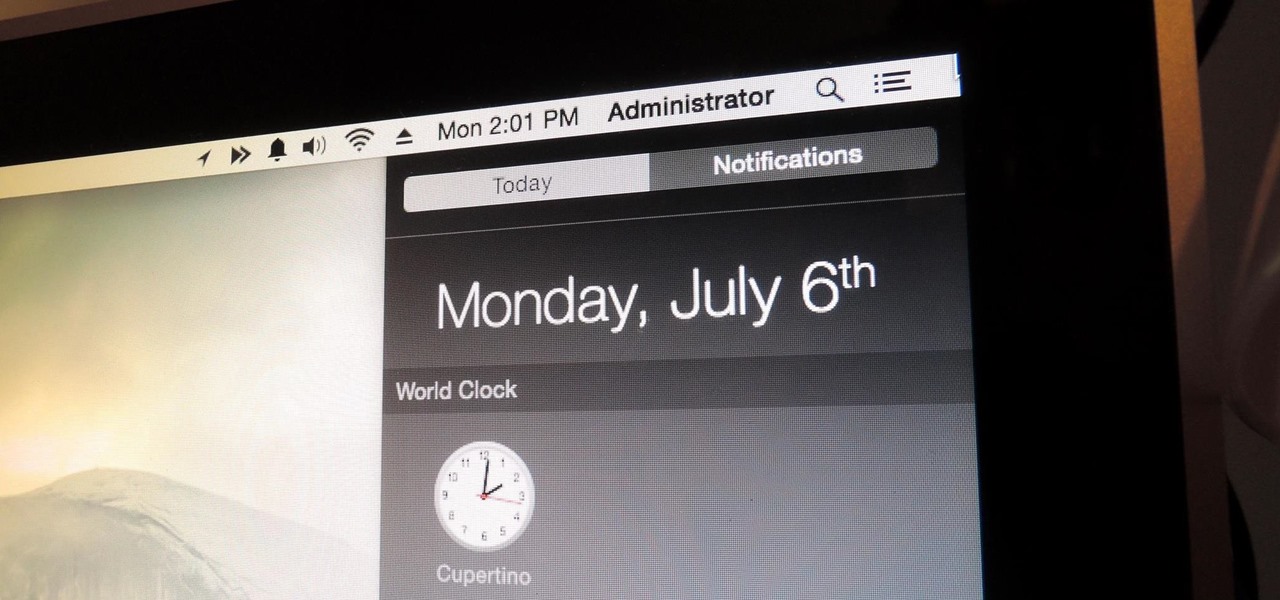
You can check stock quotes, make quick calculations, see the weather forecast, get reminders, and view upcoming calendar events all from the Notification Center on your Mac. But if that's all your using it for, you're just barely scratching the surface.

When the Galaxy S6 hype-train was building momentum ahead of the phone's release, many reports had Samsung cutting back on its much-maligned TouchWiz skin. In the end, these reports were either highly exaggerated or entirely fabricated, because while not as egregious as previous devices, Samsung's signature bloated UI and duplicate apps are definitely present on the Galaxy S6.

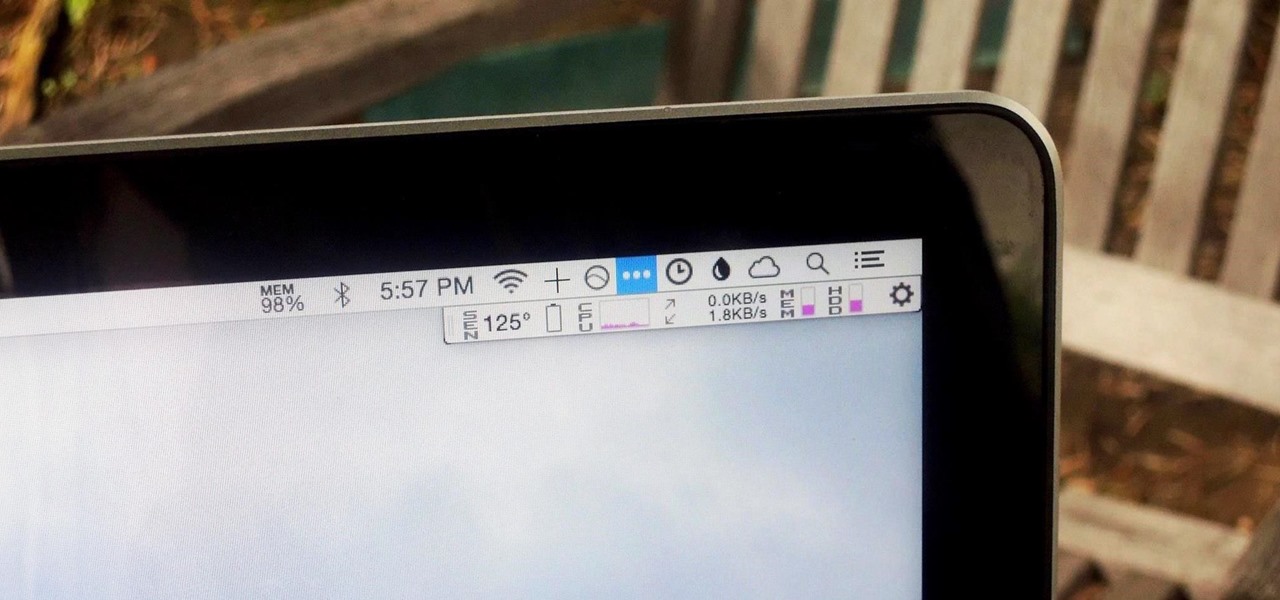
We recently showed you 8 menu bar apps that ever Mac power user should have, covering apps that allow you to control iTunes, eject drives, organize screenshots, and more—all from that tiny strip at the top of your screen.

If you remember last time, we successfully uploaded picture with a small hidden PHP command executer embedded in it onto a server. Now, our goal is to take this a step further and get an interactive shell. To do this, we need to upload another file that either binds a port for us, or connects back. For this tutorial, we will use a Python reverse Meterpreter shell.

If you updated to iOS 8.4 already to try out the new Apple Music service, there's one important change you need to know about—there's no longer a "Shuffle" option for all songs in your library.

Welcome back, my tenderfoot hackers! One of the issues we often encounter with Metasploit is how to add new modules. Although Rapid7 (Metasploit's owner and developer) periodically updates Metasploit with new exploits, payloads, and other modules, at times, new modules appear that are not added to the Metasploit repository.

When it comes to smartphones, the biggest complaint voiced by most users is battery life. Sure, it's unrealistic to expect your Android device to run for weeks without a recharge, but many folks struggle to even make it through the day without having to top off their battery.

Most mobile games have moved to an online-only format, meaning you need to be connected to the Internet in order to get any kind of multiplayer action going. This is great when you're at home on Wi-Fi, but when you're out and about, slow and inconsistent data speeds can cause serious lag. Or worse yet, you may be nearing your monthly data cap!

Catching up with Windows 8, Apple has finally included a way in Mac OS X to use two apps side by side in full screen view. In the 10.11 El Capitan update, it's called Split View, and it works fairly well for the most part. It's not quite as intuitive as it should be, but easy enough once you get the hang of it.

Hello there, 'Flashers'! Welcome to my 8th Post. This tutorial will explain how to flash Kali NetHunter on OnePlus (Tested) and Nexus Devices (Not Tested-Should work) as a secondary ROM, so that none of your personnel data/ROM gets affected.

Apple just showed off iOS 9 and its new features at WWDC 2015, including multitasking support for iPads (finally!), a new Low Power Mode to save battery, local area search and transit directions in Maps, a highly improved "Proactive" Siri, a better Spotlight search, new apps, and so much more.

Amazon makes it exceptionally easy to purchase anything you want in just a few minutes. From textbooks for school to live ladybugs, its more surprising when you can't have something delivered to your doorstep in a few day's time.

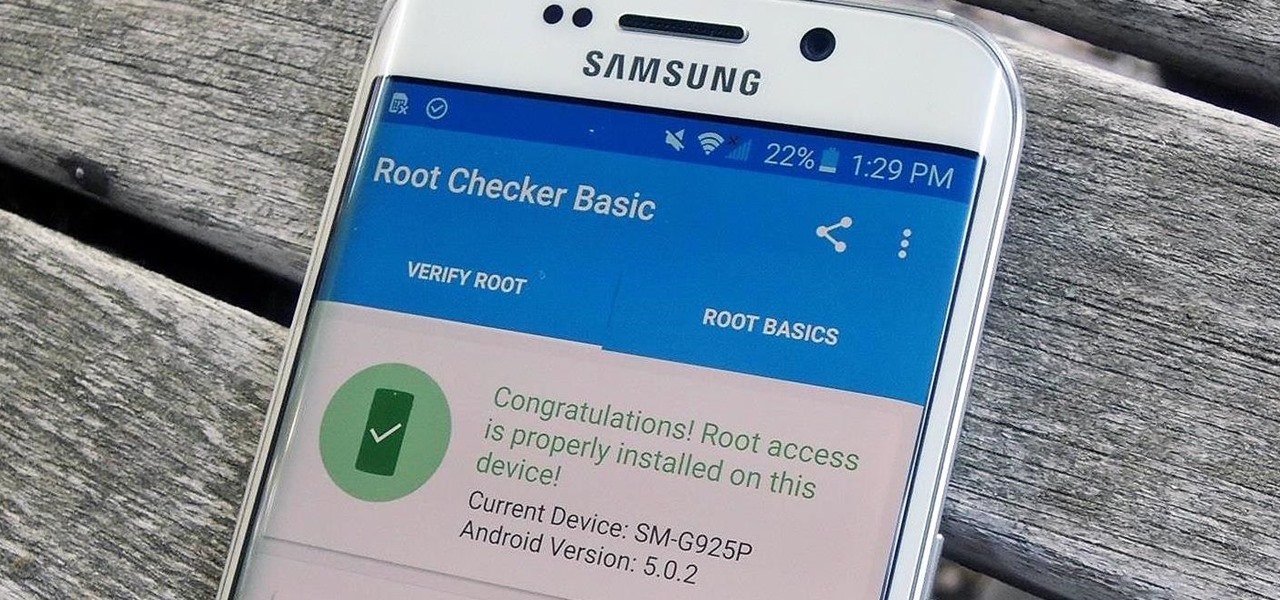
Thanks to leaks and hard working developers, rooting tools for brand new Android devices are usually available right around the time of the smartphone's release, if not earlier. The Samsung Galaxy S6 and S6 Edge are no exception.

Welcome back, my tenderfoot hackers! As hackers, we often are required to get past antivirus (AV) software or other security measures. To do so effectively, we need to have some understanding of how AV software works. In this tutorial, we will take a cursory view of how AV software works so that you can better strategize on how to evade detection by it.

Welcome back, my rookie hackers! As hackers, we are often faced with the hurdle of cryptography and encryption. In some cases, we use it to hide our actions and messages. Many applications and protocols use encryption to maintain confidentiality and integrity of data. To be able to crack passwords and encrypted protocols such as SSL and wireless, you need to at least be familiar with the concepts and terminology of cryptography and encryption.

What Is IPython? IPython is a richly featured replacement for the standard python interpreter. It offers a wider range of functionality, that the standard

From time immemorial, human beings seem to be at odds with one another. When these differences become so heated and unresolvable, it eventually erodes into physical violence. This violence has manifested into some of the most horrific exercises in human history, things which every school child is aware of and none of which we have to recount here. Although humans have been cruel and violent for a very long time, the 20th century may have epitomized that behavior. With two World Wars and many,...

Big box stores love to sell gift cards, and as consumers, we snap them up almost as quickly as they can be printed. This industry has become rather profitable, though, because portions of the gift card balances often go unused.

While Kobe beef cows get massaged, American dairy cows are taking a real beating. Many people are cutting back on dairy while a growing number of people are discovering that they're lactose intolerant. As the public's disdain of cow's milk grows, milk sales themselves are at a forty-year low.

The gag reflex: it can interfere while in the dentist's chair, upon seeing another person throw up, or even just getting a whiff of a disgusting, stomach-twisting scent. Every time this reflex kicks in, it stops us immediately, inducing a choking, gagging, coughing fit.

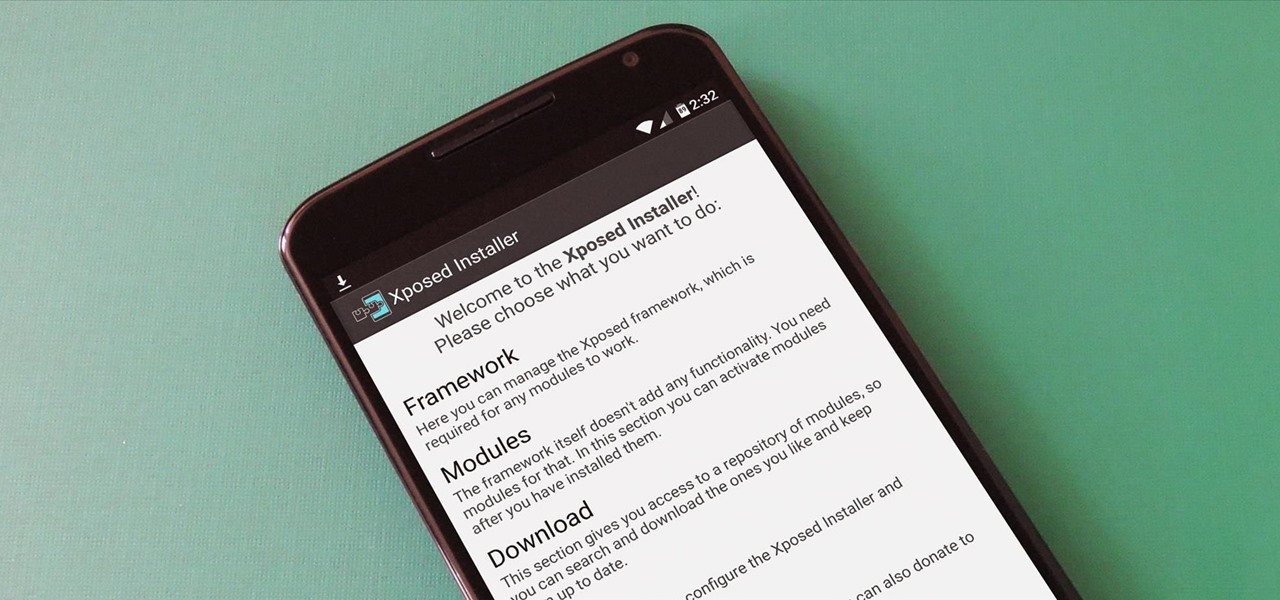
UPDATE 11/17/15 The Xposed Framework now officially supports Android 5.1 through 5.1.1 Lollipop devices as well. Everything will still work the way it has with Android 5.0 through 5.0.2, but there are a separate set of files for the newer Android version. I'll cover both below, but make sure to download the proper file for your particular version of Android.

Valentine's Day can seem like Singles Awareness Day if you're newly broken up, but that's all the more reason to treat yourself on this pink-and-red consumerist holiday. Whether you're happily single or bitter and bitchy, there's definitely something on this list of Anti-Valentine's Day treats to fit your mood. Remember: cake is still cake!

Among the many gifts that Italy has bestowed upon the world, culinary and otherwise, pesto stands alone. The exact birthplace of pesto, that herby sauce made of pine nuts and olive oil, is an area of Italy called Liguria, whose microclimate is particularly kind to basil, one of pesto's key ingredients.

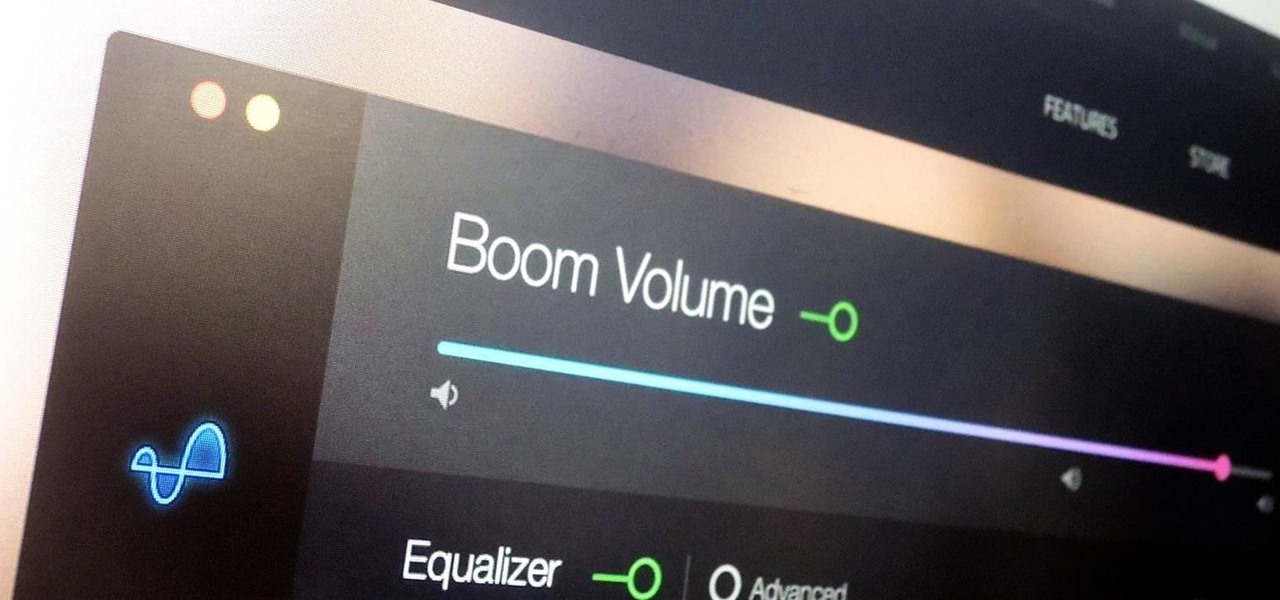
During a power outage at my apartment this year, I watched movies on my MacBook Pro instead of on my television. While I had no complaints about the screen size, I did have an issue with how low the audio coming from my speakers was. External speakers would help, but I don't want to buy them or lug them around every time I want to watch a movie.

Oops... did you forget to connect to a Wi-Fi network before streaming HBO GO on your iPhone? While those episodes of The Wire may have been absolutely life-changing, your three-digit cellular bill is definitely going to hit you a little harder.

Sweaty palms, stuttered speech, and terror blackouts: if you're someone who absolutely despises speaking before audiences, you've probably experienced side effects like these. No matter how well prepared we are, or how familiar our audience is, giving a presentation can be an experience more terrifying than death, according to psychologists. Unfortunately, it's impossible to avoid public speeches, but you can make these events less frightening with a few simple hacks.

Welcome back, my fledgling hackers! With this first article, I am initiating a new series intended to convey to my readers the skills necessary to develop your own exploits.

I'll admit it: I've spent many eight-hour workdays stuck at my desk, staring at my computer as my breaks slip past unnoticed. I frequently tell myself I'll take one in a few more minutes—but somehow, the entire day will pass and I won't have taken a single break.

Welcome back, my fledgling hackers! Sometimes, for a variety of reasons, we can only get a command shell on our target system. For instance, with Metasploit, it's not always possible to get the all powerful Meterpreter on our target system. In other cases, we may be able to connect to a command shell via Netcat or Cryptcat.

The release of iOS version 8.1.1 brought some much needed bug fixes to Apple's mobile operating system, but with it came a patch for Pangu's jailbreak method, which worked on iOS 8.0 to iOS 8.1 using a Mac or Windows computer. Luckily, it didn't take very long for a new team of developers to come up with a method for jailbreaking iOS 8.1.1 devices, and much like its predecessor, the process is a cinch.