The threat of an evil access point has been around for a long time, and with the rise of open public Wi-Fi, that threat is often overshadowed by how comfortable we are using third-party Wi-Fi hotspots at coffee shops and public spaces. While we've shown an evil twin attack using the Aircrack-ng suite of tools, MitmAP is a Python tool to configure custom APs for many types of wireless attacks.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

Despite concerns with SafetyNet, Google actually cares about root. Every phone they sell has an unlockable bootloader, so you can toggle a setting and send a Fastboot command, then start flashing custom firmware right away. The Pixel 2 and Pixel 2 XL continue this tradition, and now they have an official root method.

With their first attempt at the mobile market, Razer introduced a device that looks at the smartphone differently. Instead of focusing on minimal bezels or an amazing camera, Razer decided to make a phone for gamers. So how could Razer target the growing mobile gaming market, which is projected to generate $40.6 billion in global revenue in 2017? It starts with the IGZO LCD Display.

If you need to scan a large number of domains for a specific web app vulnerability, Dorkbot may be the tool for you. Dorkbot uses search engines to locate dorks and then scan potentially vulnerable apps with a scanner module.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Bluetooth Low Energy (BLE) is the de facto wireless protocol choice by many wearables developers, and much of the emerging internet of things (IoT) market. Thanks to it's near ubiquity in modern smartphones, tablets, and computers, BLE represents a large and frequently insecure attack surface. This surface can now be mapped with the use of Blue Hydra.

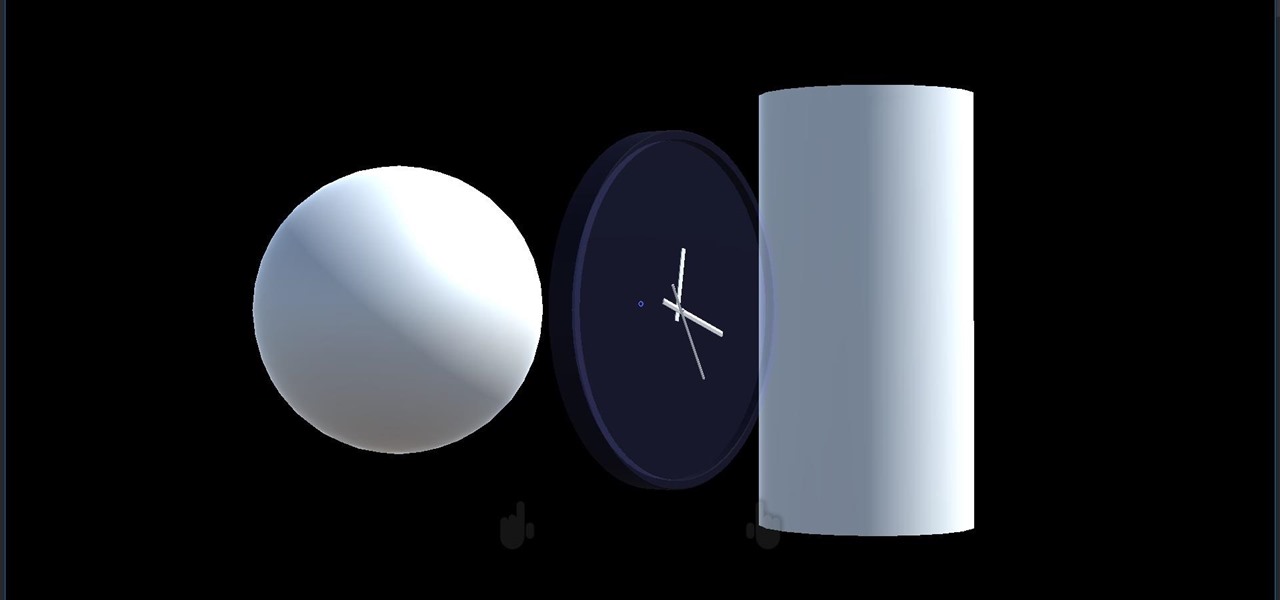
In this chapter, we want to start seeing some real progress in our dynamic user interface. To do that, we will have our newly crafted toolset from the previous chapter appear where we are looking when we are looking at an object. To accomplish this we will be using a very useful part of the C# language: delegates and events.

We started with our system manager in the previous lesson in our series on building dynamic user interfaces, but to get there, aside from the actual transform, rotation, and scaling objects, we need to make objects out of code in multiple ways, establish delegates and events, and use the surface of an object to inform our toolset placement.

One of the best things about Android is the ability to customize your phone to your liking. From changing the layout of icons to finding the perfect wallpaper to reflect your current mood, there's a wide range of tools to make your phone yours.

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

On July 20, 1969, humans set foot on the moon for the first time. But some say our microbes beat us there. With the Space Age came new questions about microscopic invaders from outer space and concern about where we are leaving our microbial footprints. The questions are even more relevant today.

A router is the core of anyone's internet experience, but most people don't spend much time setting up this critical piece of hardware. Old firmware, default passwords, and other configuration issues continue to haunt many organizations. Exploiting the poor, neglected computer inside these routers has become so popular and easy that automated tools have been created to make the process a breeze.

The world is full of vulnerable computers. As you learn how to interact with them, it will be both tempting and necessary to test out these newfound skills on a real target. To help you get to that goal, we have a deliberately vulnerable Raspberry Pi image designed for practicing and taking your hacking skills to the next level.

Social engineering makes headlines because human behavior is often the weakest link of even well-defended targets. Automated social engineering tools can help reclusive hackers touch these techniques, but the study of how to hack human interactions in person is often ignored. Today, we will examine how to use subtle, hard to detect persuasion techniques to compromise a human target.

Full disclosure: I really like Apple's stock ringtones on the iPhone. After all, there are over 50 to choose from if you include the classic ones. With all that choice, why would you ever need more? Personally, I get bored easily, and I'd like my music to play when people call. Apple doesn't let us pick a song from our music libraries, but there is still a way to use our favorite tunes as tones.

One major component of Level 4 and Level 5 driverless cars is in very short supply. Venture capitalists and engineers from around the world are racing to fill the LiDAR production, price, and performance void.

After months of leaks and rumors, Google has finally unveiled the Pixel 2 and Pixel 2 XL. If there were such a thing, the Pixel would be the one "true" Android flagship — so even if you don't plan on buying a Pixel 2, you'll want you learn more about this milestone device.

In the past, to see a pre-constructed state of the house that you would one day live in, you had to be able to read blueprints or hire an artist to sketch it out. Later came the ability to have a 3D rendering of that house on a screen, but you'd still have to work hard to envision it in real life.

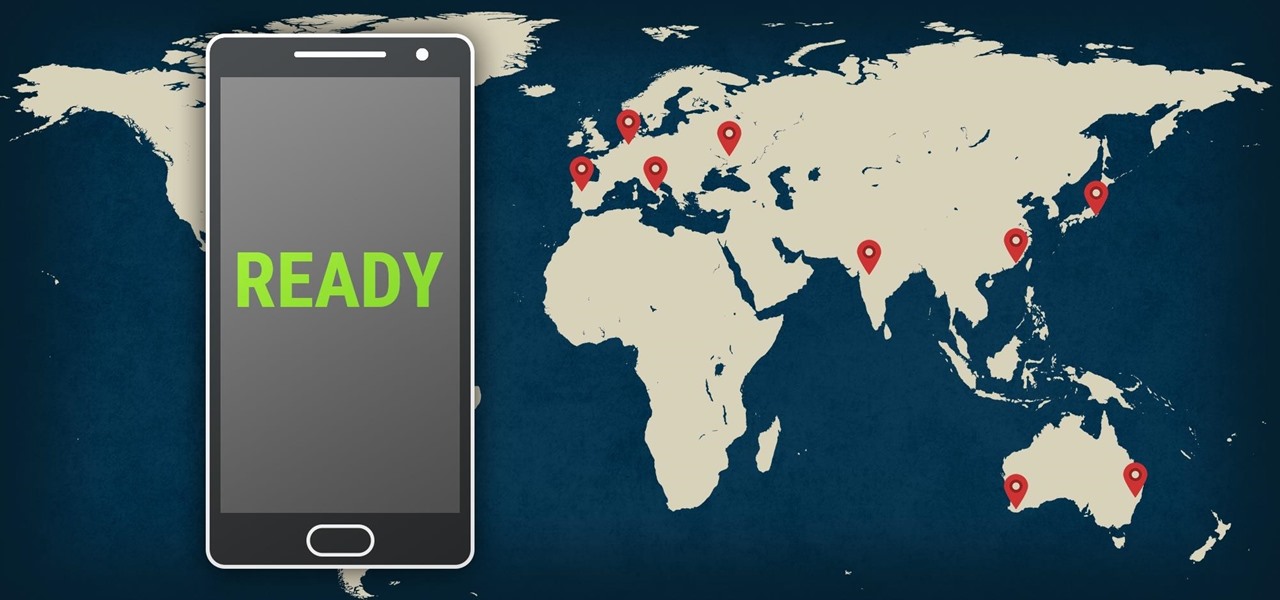
At a global security conference in Munich, philanthropist and businessman Bill Gates spoke about the next pandemic and a dire lack of global readiness. Here's how his statement could come true—and how to be ready when it does.

There are all kinds of theories—many supported by science—about what causes Alzheimer's disease. Tangles of protein called ß-amyloid (pronounced beta amyloid) plaques are prominently on the list of possible causes or, at least, contributors. An emerging theory of the disease suggests that those plaques aren't the problem, but are actually our brains' defenders. They show up to help fight an infection, and decades later, they become the problem.

Beginners luck is a phrase I have always hated. But really, beginners luck comes down to not letting your experience in something get in the way of the idea.

The new Google Assistant is only officially available on three platforms—newer Android phones (Pixels and those running Marshmallow and Nougat), the Google Allo app, and Google Home. However, most of the Assistant's basic functionality is also bundled into the Google app for Android and iOS, which used to go by the name Google Now, but is now referred to only as Screen Search or your Google app's Feed.

After enabling disk encryption, creating encrypted disk images, installing KeePassX and iTerm2, and using Git with local repositories, the next step to getting your Mac computer ready for hacking is setting up a package manager that can install and update open-source hacking tools. There are multiple options to choose from, but Homebrew has a slight advantage.

The 12.9-inch iPad Pro was released in stores on November 11, 2015, and a couple days later I went to an Apple Store and to check it out in person. I had mixed feelings about the tablet, but was intrigued overall—so much so that over the next few weeks, as I found myself hearing more and more about the device, a thought began to take hold in the back of my mind—I really want one. At the same time, I was hesitant about dropping roughly 10 Benjamins for a tablet!

Samsung's Note series is directly responsible for some of the biggest innovations in smartphones. As the first "phablet," it sparked the current craze for bigger screens, and the S Pen stylus has been mimicked numerous times. Even the curved display made famous by the Galaxy S6 edge made its debut on the Note 4, so this is the one smartphone line you want to keep track of if you like to stay on the bleeding edge.

So you're finally ready to head out on that big trip you've been planning for months, huh? It's an exciting time, but there are plenty of things you'll need to prepare before you head out. For instance, it's hard to imagine life without a smartphone these days, and with useful traveling apps like Google Translate and maps, you'll almost have to make sure that you have a working smartphone when you arrive at your destination.

When a headache strikes, I reach for the nearest painkiller. Forget closing my eyes, laying down, or even applying an ice pack—I seek the quickest and most immediate relief possible, and normally that comes in the form of pills. However, fast relief can be found from another, more natural source: herbal beverages. So if you're tired of popping pills when you have aches and pains, try some of these herbal drinks out instead.

Welcome to the final tutorial of the series on standard C. This article will cover the linked list abstract data type (ADT). There will be a lot of abstraction to try to deliver the understanding in the most basic way for easiest interpretation of what they are and how they work, then we will get into the guts of it and learn the technical code underneath. For those who have yet to grasp the concept of pointers, it's advisable that you do that first before approaching this. Having learned thi...

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

When you hand your unlocked iPhone to somebody so they can use the internet real quick, check out some cool photos, or do whatever, there's a possibility that they could snoop around where they don't belong. If you have some secret recipes, login credentials, intellectual property, or other sensitive information in your notes, you'll want to add some protection to them.

Since Android is an open source operating system, that means anyone with a little know-how can download, view, and even alter its underlying code base. Manufacturers do it all the time, which is how we end up with skins like TouchWiz and Sense. But when Android's awesome third-party development community gets their hands on this code, we end up with custom ROMs like LineageOS and MIUI.

Most of us lead busy, work-filled lives, often clocking in a 9-to-5 five days a week. And when that clock signifies the hour to leave, the last thing on anyone's mind is: "Time to go to the grocery store to pick up more fresh produce!" (Well, to be fair... maybe more people are psyched about this, but I know with certainty that I am not one of them.)

Hello partners, first of all I would like to thank all those who have sent me positive feedback about my posts, to say that I'm always willing to learn and teach. I'm also open to answer the appropriate questions.

Considering that nearly half a million brand new apps were published to the Google Play Store in 2015, you can definitely call it a banner year for Android development. In fact, it's getting to the point where we're a bit spoiled as end users, since we've grown to expect something new and exciting practically every week.

Upon reading the title for this article, I bet you secretly thought to yourself, "Yeah, I've got the perfect way to 'make' roast chicken: I go to the store, and I buy one!" Well, there's no question that there are some really tasty, convenient rotisserie chickens out there, already made and ready for eating or using in recipes.

This year, Google released two Nexus phones to glowing reviews, and as we've grown to expect, the Android community wasted no time in coming up with a root method for both. In fact, legendary root developer Chainfire even devised an entirely new "systemless" method for rooting that should make updating a bit less complicated, along with a few other benefits.

Hello my anxious hackers, the week has started and here we begin a new series that I think will help many here and not only, for those that have the opportunity to follow our tutorials but they are not yet part of the community.

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

It would only make sense that Google is one of the most active app developers on the Android platform, particularly when you consider that they develop the platform itself. From my count, there are an astounding 117 unique apps that the search giant and its subsidiaries have published on the Google Play Store.