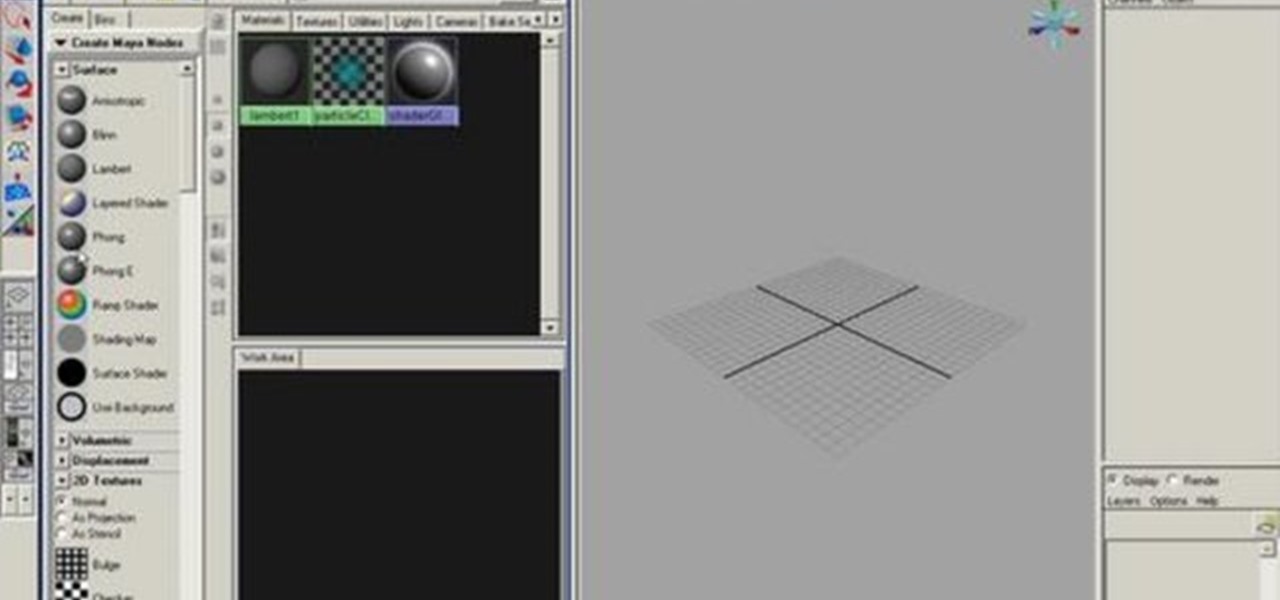
First off, a bit of explanation. The hypershade in Maya is a quick way to create and connect rendering nodes, which include textures, materials, lights, and special effects. Hypershade is one of the most important features in Maya to learn and master.
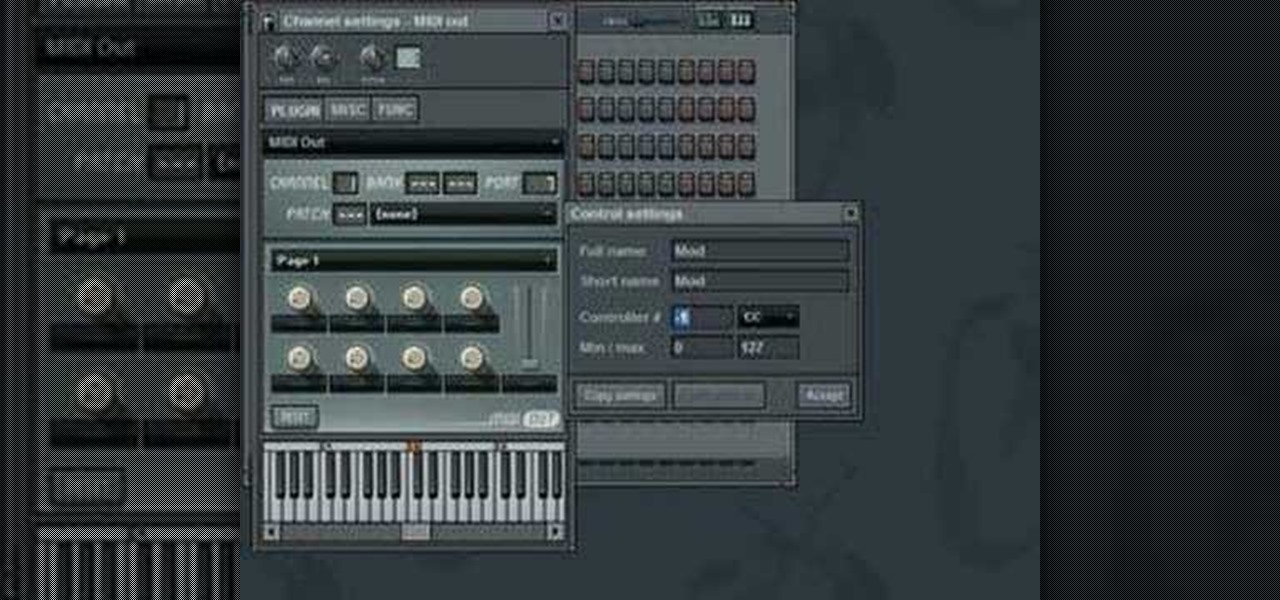
NFX shows you how to connect the MOD wheel on the MIDI controller to a channel plugin in FL Studio. Fruity Loops doesn't do this for you automatically so it's a good skill to learn.

In this English tutorial we look at fame and words connected with it. There are many words to describe a person who is famous or a "star." This ESL video lesson teaches you how to talk about well known people in the English language.

I explain how to view and control your computer from your iPhone/iPod Touch. This works over Edge and Wifi connection, but obviously the better your connection the faster it will go. If you are having problems connecting try going to control panel then security center then turn your firewall off. Also try turning off anything like virus protection.
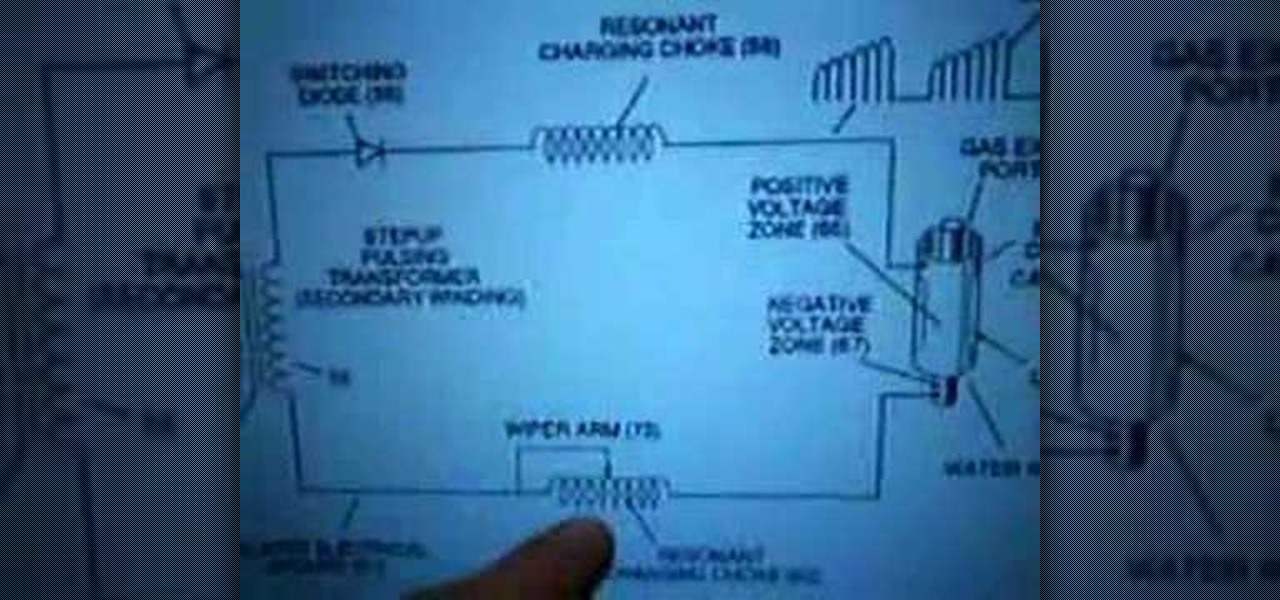
Here are some concepts that Stanley Meyers had related to his patents regarding the Resonant Charging Choke, which is basically Telsa's BiFiler Coil Design, which basically is how to connect the WFC to the bifilar coil for maximum efficiency and if you have higher resistance and impedance than the WFC you can inhibit amp flow and allow voltage to go to the maximum.

This is a chemical demonstration of the excitation of sodium atoms in a dill pickle by connecting it to 120 volts. Watch to learn how to electrify a pickle yourself.

Watch this video to learn how to pick a trie circle lock with a woman's electric shaver. This lock pick technique only takes seconds.

This video shows how to perform a pelvic exam of a pregnant woman in labor.

This is an in depth tutorial on how to use the Motif XS vocoder. Subjects covered are: which microphone to use for vocoding, how to connect the mic, how to set up the parameters from utility mode and a short demo of the 4 basic vocoder voices from the Motif XS ROM.

An explanation of how to get access to your Linux desktop from any other computer connected to the Internet.

Dr. Coyle Connolly, D.O., board-certified dermatologist and skin cancer expert removes a wart from a woman's leg for a skin cancer biopsy.

Learn the names of some common jobs women can hold.

This video is shows you how to conjugate Japanese verbs into the te-form. The te-form is useful for connecting sentences, watch and learn.

If you want to pull a small trailer with the Chevy Aveo, you are going to need some wiring for the trailer lights. This video will demonstrate how easy it is to connect a modulite circuit protected wiring harness. Now, even though you don't have a truck, you can run to the hardware store to pick up supplies and it will be safe, convenient, and legal.

In this video you will see how to create a primary menu in Drupal and connect URLs (paths) to it.

What to say on the mic to keep the crowd interested. When you are DJing, you need to have a confident entertainer persona so that you can connect with the audience.

This video shows you the benefits of the pilates workout for pregnant women.

This section of "Final Assembly" of an engine covers installing your distributor. This can be tricky. The distributor gear has to meet the cam gear and connect with the oil pump drive shaft. Take your time and you'll get it.

When you're ready to remove the pistons, start with the rod caps. You'll also get to see the crankshaft, rod bearings and journals for the first time and inspect them for damage as they come out. Great tips on protecting the cylinder bore while removing the pistons and connecting rods.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program the buttons and directional pad on your Wiimote using GlovePie's GUI interface.

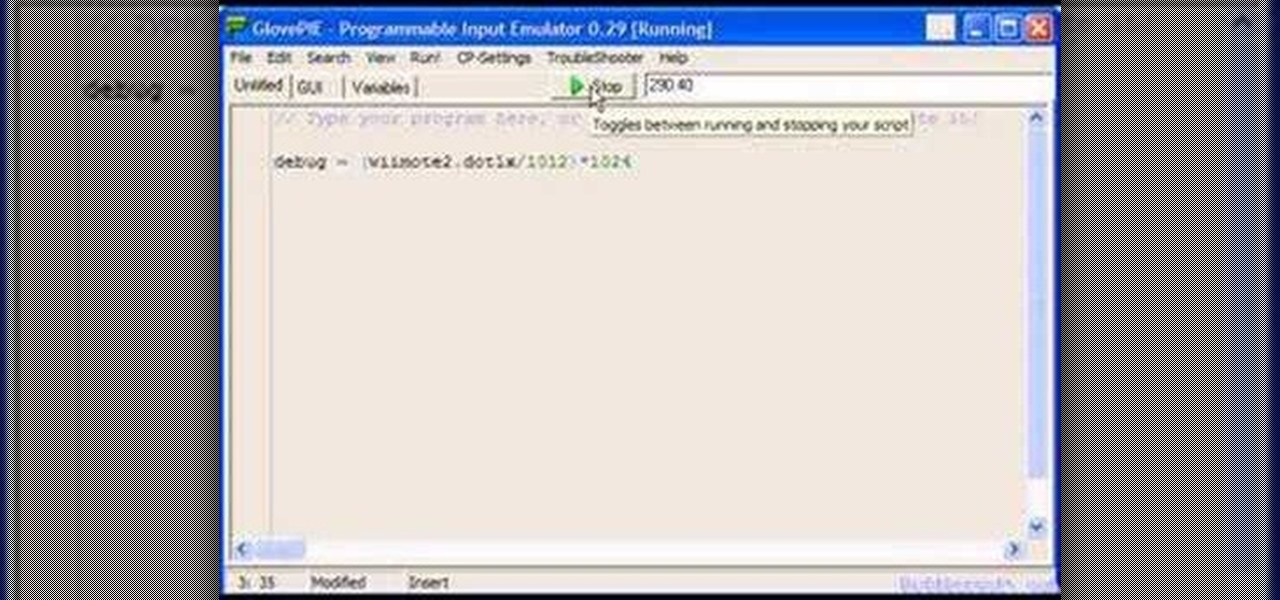
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to detect motion from the Wiimote using GlovePie.

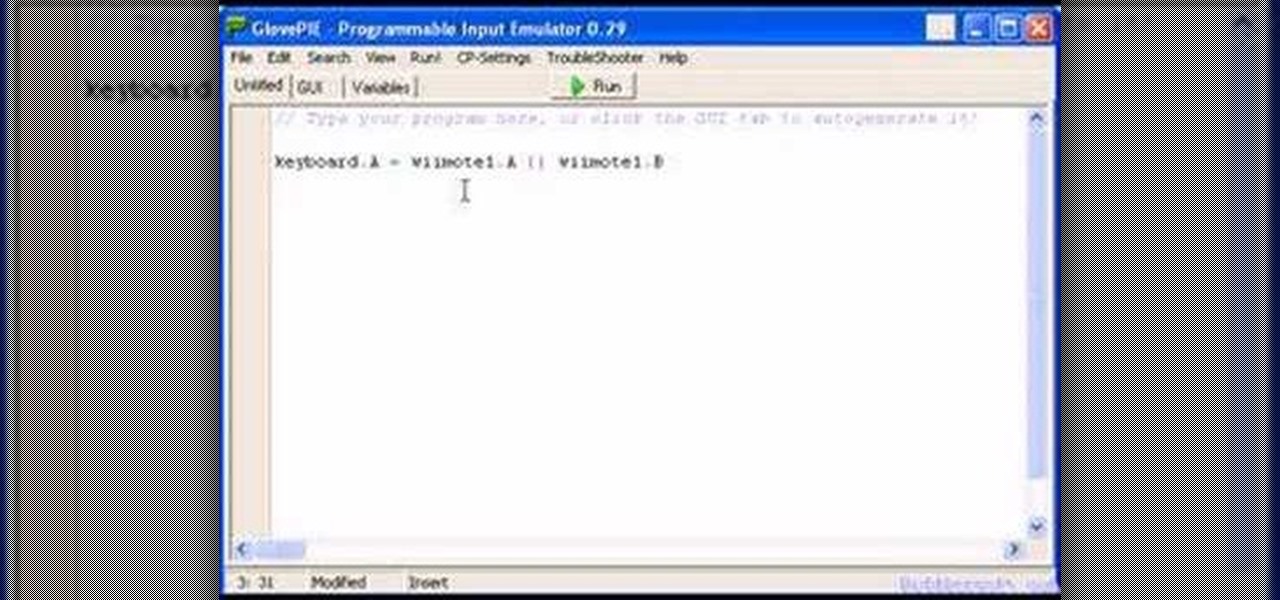
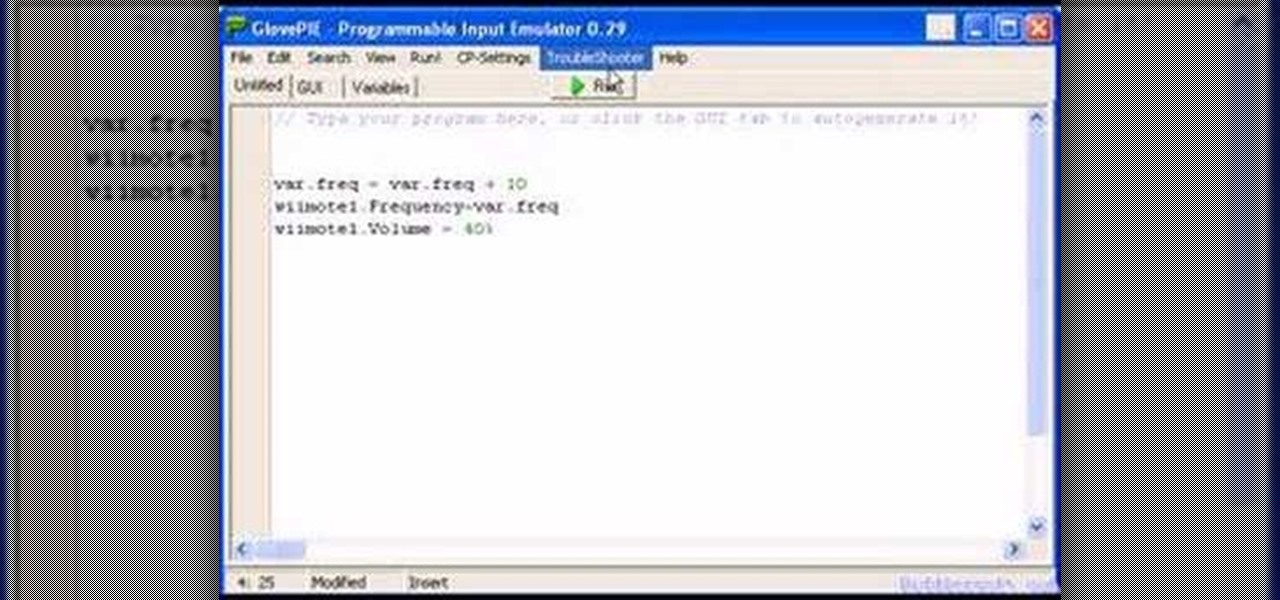
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to create scripts in GlovePie to program your PC to respond to simultaneous button presses and button combinations from a Wiimote.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how you can program GlovePie scripts that will emit sounds from the Wiimote's built in speaker.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program conditionals - if, if/then, and if/else statements - in GlovePie.

You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. See how to program scripts in Glovepie to use the infra-red sensor on the Wiimote to move the mouse cursor.

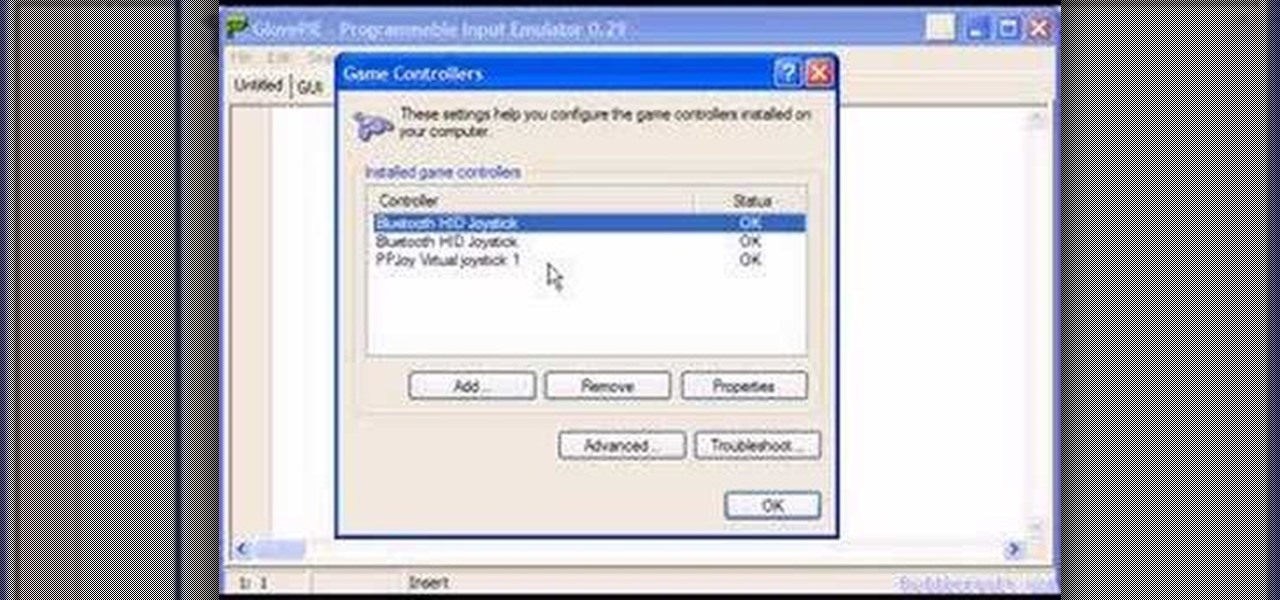
You can connect your Nintendo Wii Wiimote to your PC using GlovePie input emulation software and a bluetooth connection. Learn how to program your PC to recognize analog input or joystick/joypad input from a Wiimote using GlovePie and another piece of software called PPJOY

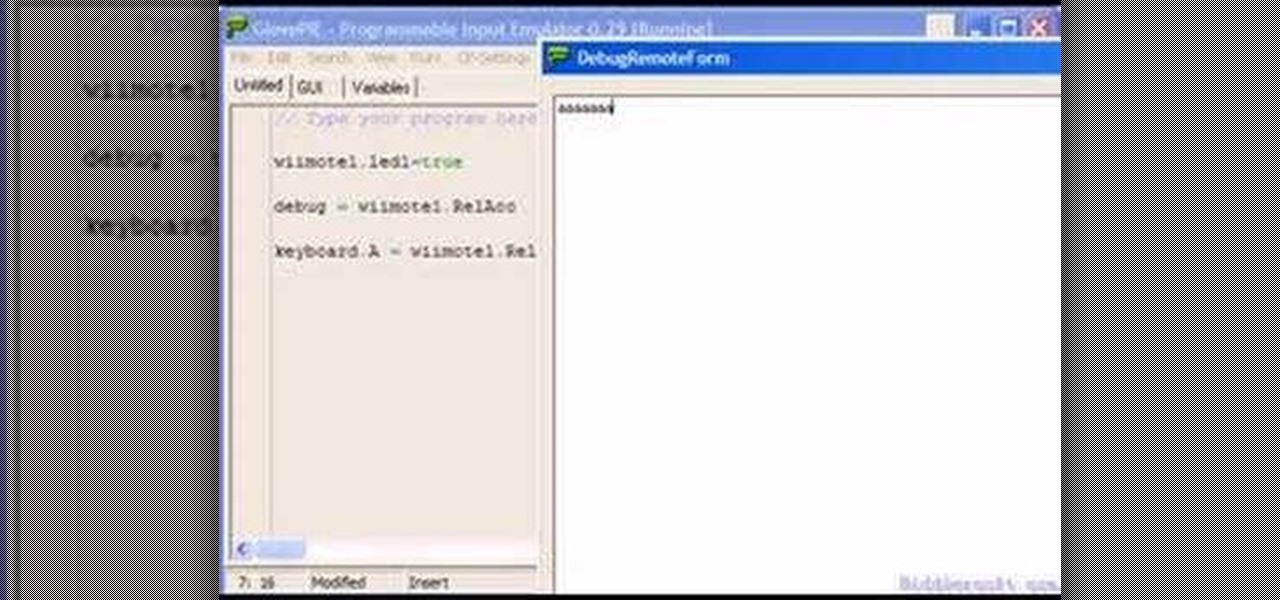
If you're trying to get your Nintendo Wii Wiimote to connect to your PC via a bluetooth connection, you'll need to sycronize it before you can start using it as an input device. Learn some basic scripting and programming in GlovePie, input emulation software, to get your Wiimote up and running.

Learn how to program basic script in GlovePie to allow your Nintendo Wii Wiimote to function as an input device on your PC. Using GlovePie input emulation software and a bluetooth connection you can connect your Wiimote to your PC.

It is argued that sun exposure and warm weather helps people cope with and fight multiple sclerosis. Sun is important to produce vitamin D. There are arguments that vitamin D deficiency is connected with cases of multiple sclerosis. Get a blood test to make sure your vitamin levels are optimum and you are suffering from no mineral or vitamin toxicity.

The perfection loop is used for attaching lures or sinkers to a heavy monofilament leader. The Perfection Loop knot is designed to easily create a loop at the end of the fishing line. The perfection loop is also often used by fly fisher men use the perfection loop to connect the fly fishing line and leader in a loop to loop connection.

Learn this exciting swing dance from the 30s. Sosh and Gina will start at the very beginning, no experience necessary. Learn how to dance from our instructional dance video clips (it's like a virtual dance lesson). Each? week we will post a new video clip here on our video podcast. If you're interested in more check out our site www.iDance.net.

Want to watch movies from your computer on a TV? What about just using your television as another monitor? Find out how to connect you TV to your computer and convert it into a monitor.

You can learn how to make a magical magnetic toilet roll. To do this, you need a paper roll, a piece of paper, glue, and scissors. You cut the roll into two pieces, connect the roll to the piece of paper, and mark the middle gap to make inserting the third stripe more accurate.

You're out and about, and nothing on your iPhone will load. A glance at the settings shows a saved Wi-Fi network with full bars that your iPhone had connected to automatically, but you're not getting any internet. If you've experienced this, you're not alone, and there's something you can do about it. You'll even increase privacy and security on your iPhone in the process.

Arduino is a language that's easy to learn and supported on many incredibly low-cost devices, two of which are the $2 Digispark and a $3 ESP8266-based board. We can program these devices in Arduino to hijack the Wi-Fi data connection of any unlocked macOS computer in seconds, and we can even have it send data from the target device to our low-cost evil access point.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

Smartphone hardware surpassed the most popular portable game devices long ago in all but one category — control. Your iPhone is more than capable of running impressive, fully-realized games, but touch controls only go so far. That's why it's so exciting that Apple has added support for PS4 and Xbox controllers with iOS 13.

Spotify integration in Bumble has been around for a few years now, allowing prospective matches to view the artists you listen to the most on the popular music streaming service. It definitely helps people connect, but sadly, it doesn't work as well as it should because it rarely updates to show what you're listening to now.

Having a dropped call can be incredibly frustrating, especially when you look down and see that your iPhone has full reception. While there's any number of issues that can cause this, one common and often overlooked issue is your iPhone failing to switch cell towers as appropriately needed.

Hacking Wi-Fi is a lot easier than most people think, but the ways of doing so are clustered around a few common techniques most hackers use. With a few simple actions, the average user can go a long way toward defending against the five most common methods of Wi-Fi hacking, which include password cracking, social engineering, WPS attacks, remote access, and rogue access points.