Before you start a paint job you will need to prime the surface of the wall. Priming is necessary if the wall is a dark color or stained or bumpy at all. Once you've decided to prime and paint, check out this tutorial for advice on how to go about it.

Your IP address is what identifies your personal computer while you are online. You may want to change your IP address for privacy, to bypass website settings, to download, or for various other reasons. This tutorial will take you through the steps you need to start surfing more anonymously.

In this video you are shown how to use proxies and why they are important. Proxies are useful because they shield you and make you anonymous over the internet, it also prevents websites from logging your IP address. To see how important it is to prevent this go to whatismyip.com. It will show you your IP, click on it and go to 'look up'. It will show you all the personal information that can determined from your IP address. The easiest way to proxy are VPN's, which stands for virtual private ...
In this video the instructor shows how to set parental controls for a user ID account in Windows 7. To do this go to the 'Start Menu' and go to 'Control Panel'. In the Control Panel window select the 'User accounts and Family Safety' link. There is an option called 'Set up parental controls for any user'. Select that link and it opens a window where it asks you to Choose a user and set up parental controls. There you are presented with some user accounts that are currently active on that syst...

If you’re into cinematography try creating your own dolly camera platform to get those seamless tracking shots. This is a fun project that will allow you to take your film to the next level, or at least get the shot you want.
This video tutorial instructs you on what a key logger is and how to make a key logger which records your computers key strokes for later review. There are software or hardware based key loggers that intercept the connection between the keyboard and computer. Hardware key loggers consists of a micro controller for data logging. Software key logger is a script that runs in the background then processes and saves the key strokes to a text file. To make a key logger you'll need to know a program...

This video shows that how you can make plenty of delicious waffles anytime you desire. To make waffles you would require a waffle maker. First, Separate 2 eggs (yolks from the whites) and keep the same in small bowls. Put 2 cups of flour (you can use 1 cup of white flour and 1 wheat flour for more fiber and flavor) in a large bowl. Add 1 tablespoon of baking powder and 1/2 teaspoon of salt in the flour bowl. Put the egg whites in another bowl and beat the eggs for about 2 minutes. Put 2 cups ...

Love kalamata olives? Love butter? Are you thinking what I'm thinking? In this cooking lesson from chef Jason Hill, you'll learn how to prepare a simple kalamata olive butter spread perfect for entertaining.

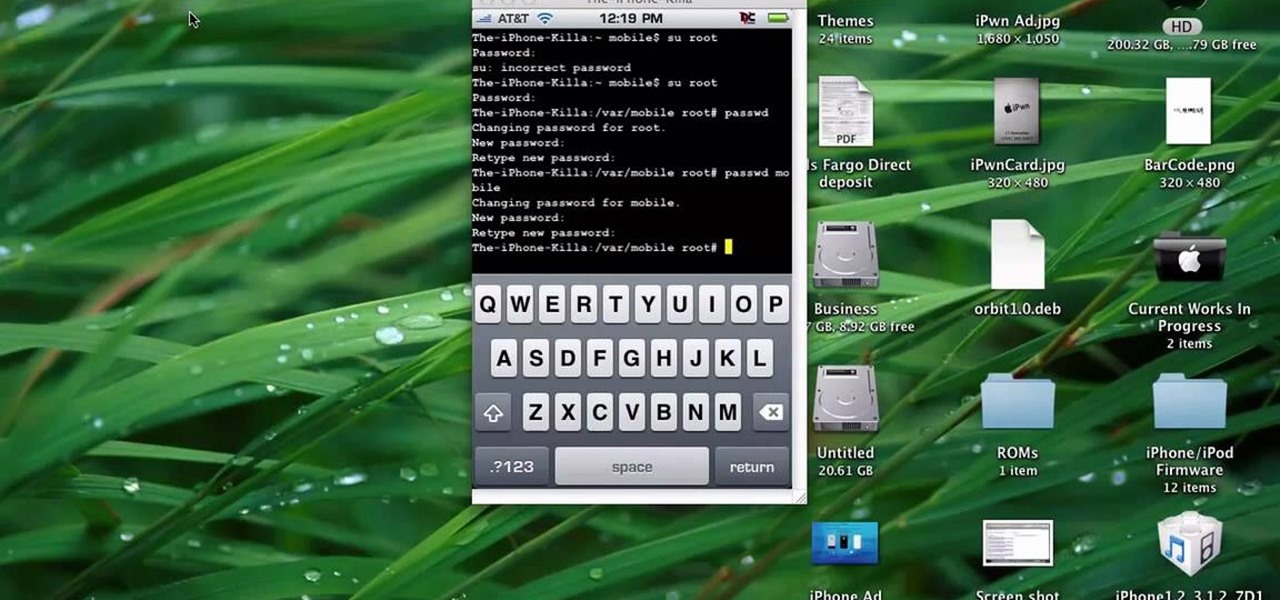
This quick tutorial runs you through a fast and easy way to make your iPhone or iPod Touch more secure. However the best security is abstinence. Just don't run the programs that leave your devices vulnerable unless you need them.

Systm is the Do-It-Yourself show designed for the common geek who wants to quickly and easily learn how to dive into the latest and hottest tech projects. They will help you avoid pitfalls and get your project up and running fast. In this DIY episode, see how to broadcast live online.

It Really Sounds Like a Chicken! Have fun with your friends and family when you build this little device that sounds just like a chicken. This is also a great example of how sounding boards work. The cup makes the vibrations louder while the wet paper towel provides friction to create the sound.

How to use a jack or bench plane; get professional tips and advice from an expert carpenter on using tools for rough finishing and smoothing edges of wood in this free woodworking video.

How to use a power planer; get professional tips and advice from an expert carpenter on using tools for leveling, shaving and shaping wood in this free woodworking video series.

How to use a block plane to cut off small portions of wood for your carpentry project; get professional tips and advice from an expert on carpentry tools in this free home improvement video series.

Knowing how to cut a straight line is essential for most projects. AsktheBuilder.com host Tim Carter demonstrates one technique for cutting a straight line. With his tips, you'll have no problem getting perfect cuts every time.

The tools required for this project are: an electric hand drill, a drill bit of the appropriate size and goggles to protect the eyes from falling debris. You will also need a ceiling hook kit, available in most major home stores. In the kit, there is a hook; a spring-loaded anchor; a threaded shank or screw, which is threaded on both ends; and another threaded shank or screw, which is threaded on one side and has screw thread on the other side for wood installation. To install in a sheetrock ...

Web applications are a prime target for hackers, but sometimes it's not just the web apps themselves that are vulnerable. Web management interfaces should be scrutinized just as hard as the apps they manage, especially when they contain some sort of upload functionality. By exploiting a vulnerability in Apache Tomcat, a hacker can upload a backdoor and get a shell.

The idea of a world without passwords used to be a pipe dream. But as we inch closer to making that a reality, we have services now that securely store all of our passwords under a single master password. It's a convenient way to keep our accounts safe and sound without having to remember all of their credentials. And there's no reason to be afraid — I'll explain why.

If you're worried about the security of your Mac, there are easy measures to prevent the most dangerous attacks. Named after the tactic of accessing an unattended computer in a hotel room, we can thwart "evil maid" attacks with Do Not Disturb and LuLu, free macOS tools by Objective-See that keep an eye on unattended computers and flag suspicious network connections that indicate a malware infection.

Many of our online accounts now come with an added two-factor authentication (2FA) functionality to help keep our data safe. This essentially means no one would be able to access the account until a specific set of requirements were met. It could be a combination of a password with a security key or even a passcode with some form of biometrics, like a fingerprint or face scan.

When your iPhone goes missing, it's serious business. Depending on your usage, your whole life might be connected to your iPhone, not the least of which includes debit cards, credit cards, and Apple Pay Cash stored in Apple Pay. While it's nearly impossible for someone to use your money with Apple Pay, it's still a good idea to disable it until you find your iPhone, just in case.

While iPhones may be more expensive than ever, it won't stop us from losing them or having them stolen. Whether you have an iPhone 5S or an iPhone XS Max, there's a good chance it'll go missing at some time during your ownership. It could end up in a couch cushion or in the hands of a pickpocket, but no matter what happens to it, you need to prepare it beforehand for the inevitable.

The key to becoming a competent white hat is knowing how the technology that you are trying to exploit actually works. SQL injection is one of the most common methods of attack used today and also one of the easiest to learn. In order to understand how this attack works, you need to have a solid grasp of ... you've guessed it ... SQL.

There are more ways to finding your missing iPhone than using Apple's own "Find My iPhone" tool in iCloud. If you just need help tracking down your iPhone in your home or at a friend's house, Find My iPhone isn't necessarily the most convenient thing to do when you've got these other options to try out first.

With the Masters, one of professional golfing's four most prestigious annual tournaments, now in full swing, Snapchat is giving users the ability to commemorate the moment in augmented reality.

Using a keylogger to intercept keys pressed on an infected computer can circumvent encryption used by email and secure chat clients. The collected data can often reveal usernames, passwords, and potentially compromising and private information which hackers abuse for financial gain.

Between the Cambridge Analytica scandal and the revelation that Facebook logs your calls and text history on Android, many are considering joining the #DeleteFacebook movement. But it can be difficult to leave the site, because so much of its content is only available to active users. If you want to keep in the loop without sacrificing your privacy, you'll want to follow the steps below.

Since starting as a simple messenger with self-destructing pictures, Snapchat has grown into a full-fledged social media platform. As features were added, new permissions were requested, and we're all probably guilty of just tapping "OK" to try out the latest and greatest. But at some point, it's a good idea to review your settings to see what personal data you're putting out there for all to see.

Local port forwarding is good when you want to use SSH to pivot into a non-routable network. But if you want to access services on a network when you can't configure port-forwarding on a router and don't have VPN access to the network, remote port forwarding is the way to go.

After pouring out $10 million for 60 seconds of Super Bowl advertising time, Doritos and Mountain Dew continued their Sunday marketing binge on Snapchat.

While Animal Crossing's emphasis has always been on making friends with the animals that populate your world, each subsequent game following its initial release has stressed relationships with human players more and more. In Animal Crossing: Pocket Camp, making human friends is a crucial part of the process with the inclusion of market boxes, Shovelstrike Quarry, and giving "kudos."

Proxies can be quicker to use than a VPN for specific applications, like web browsers or torrent clients. Both services will hide your true IP address, but a VPN is slowed down because it encrypts all data through a VPN network, while a proxy just acts as a middleman for fetching and returning requests from a server on your behalf. When speed is needed, go proxy.

Sharing your Wi-Fi password is like giving an unlimited pass to snoop around your network, allowing direct access even to LAN-connected devices like printers, routers, and security cameras. Most networks allow users to scan and attempt to log in to these connected devices. And if you haven't changed the default password on these devices, an attacker can simply try plugging them in.

Tossing an old Android smartphone with a decent battery into your hacking kit can let you quickly map hundreds of vulnerable networks in your area just by walking or driving by them. The practice of wardriving uses a Wi-Fi network card and GPS receiver to stealthily discover and record the location and settings of any nearby routers, and your phone allows you to easily discover those with security issues.

It's no secret that devices leak data, but sometimes they do so in ways you may not expect. Your phone, laptop, printer, and IOT devices leak Wi-Fi information that can (and is) used to track you.

As much as you try to safeguard your personal information, you may have made a small mistake by giving your phone number to the wrong entity, and now you're being bombarded with dozens of spam calls every day. To help parse your call log and reject the proper numbers without answering or trudging through voicemail, a good reverse phone lookup app is needed.

Android is Google's project, so of course you can see the search giant's fingerprints all over the operating system. Aside from the obvious user-facing apps, there's Google Cloud Messaging, Google Connectivity Services, and the much-maligned Google Play Services running in the background, to name a few.

If you're looking to mix up your home décor with something a little bit outside the traditional cabinet box set, check out the amazing Wave cabinet from NYC-based, Chilean designer Sebastian Errazuriz. This revolutionary design will change the way you think about interior decoration and furniture functionality.

Sushi rolls, known as makizushi in Japanese, are only limited by your imagination—and your ability to roll them neatly, of course. While it may seem like a lot of effort, rolling sushi is a snap if you have the right tools.

One of the first orders of business after purchasing a new smartphone is to load up your shiny new toy with phone numbers, email addresses, and general contact information for all the important people in your life.