Hackers often rely on lazy system admins and unpatched vulnerabilities to get access to a host. Keeping intruders off of our machines requires us to update daily, only run the services we need, and read the code, among other things, but we can still make mistakes. Luckily for us, we can limit the damage caused by those mistakes by running SELinux.

Before you read further, you may want to make sure you're wearing brown pants if you scare easily. Developer Abhishek Singh conjured an augmented reality experience that recreates the spine-tingling scene from The Ring where (spoiler alert) the ghost of Samara (or Sadako, from the original Ringu) emerges from the television.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

After numerous scandals like the Equifax data breach and the 2016 US election, cybersecurity has become a significant issue for Americans. Unfortunately, anytime we use our devices, we're open to a cyber attack — especially when we browse the web. However, there are ways that we can make it harder for hackers and data miners.

Tor is an excellent obfuscation network for web traffic, and while instant messaging over the network is very useful, it can be relatively difficult to configure. In this guide, we'll look at two synchronous communications platforms (instant messengers) which can be routed over the Tor network, Ricochet and XMPP.

In my previous article, I discussed installing and configuring OpenVAS on Kali Linux. Now it's time to start using OpenVAS with the Greenbone Security Assistant to audit networks for security issues. This can be extremely helpful when you are looking for vulnerabilities or misconfigurations in a large number of hosts.

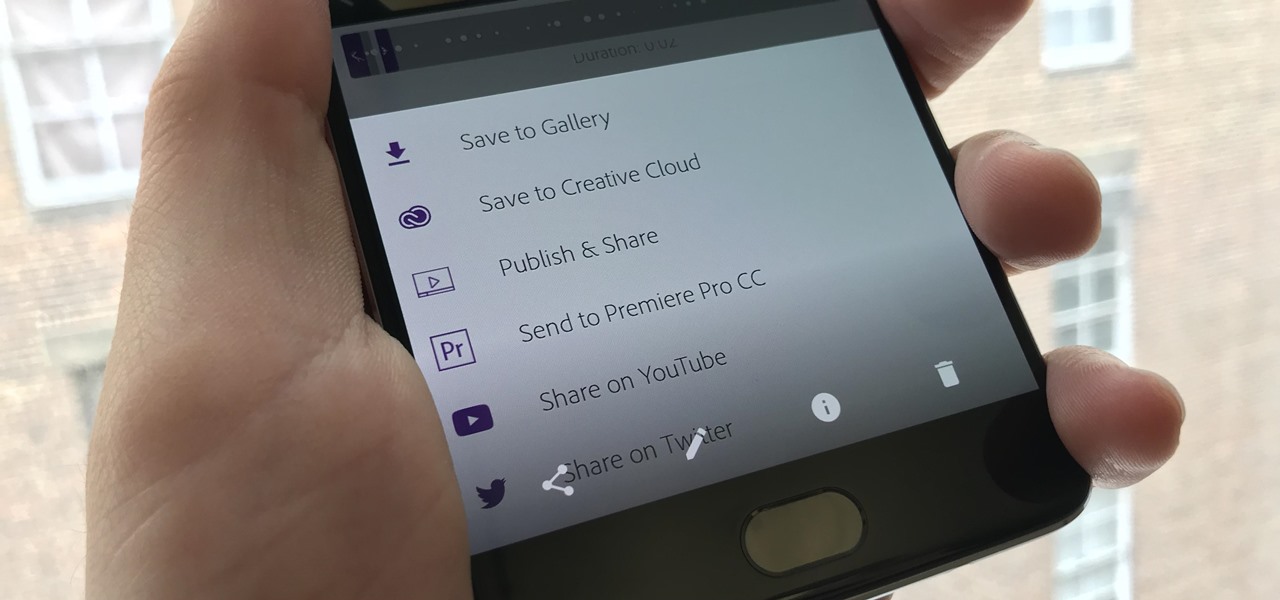
If you've taken the time to edit a video on your iPhone or Android phone, you probably have a purpose for it. Maybe you want to share it to YouTube in hopes of making the next viral sensation. Maybe you just want to save the video to your phone to show off to friends and family when you can.

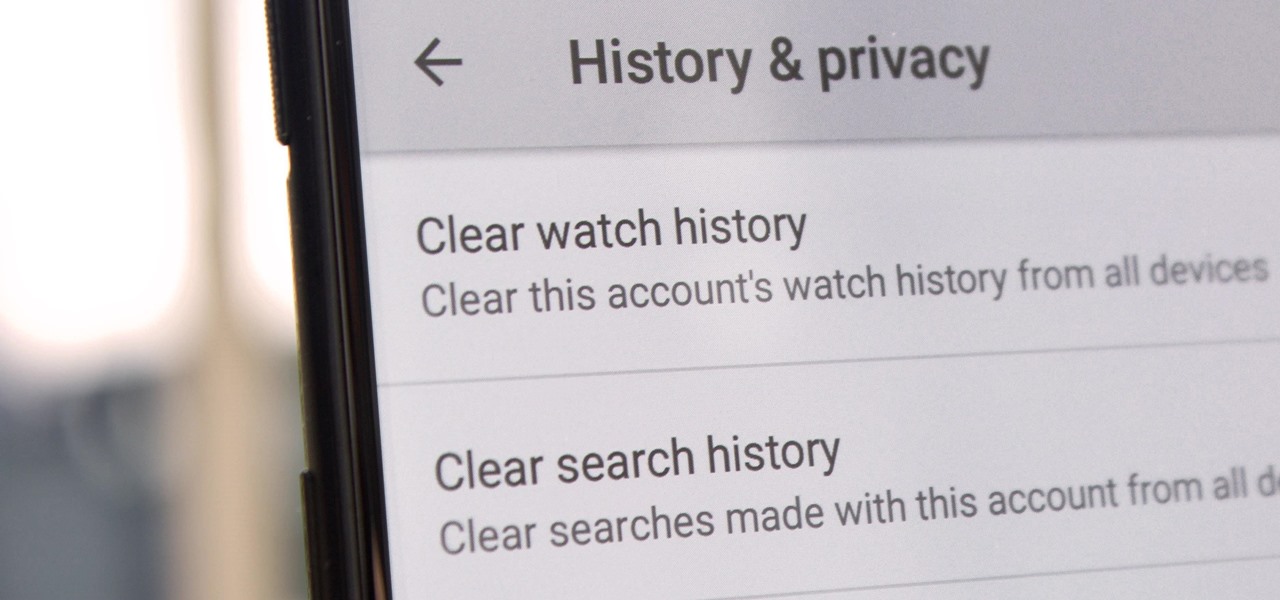
Yeah, yeah, yeah. Get your mind out of the gutter. Search histories can and should be managed. Many folks are uncomfortable knowing that every video they click and every phrase they search is being recorded and saved, and YouTube is no exception.

WordPress did not become what is arguably the most popular blogging and CMS platform on the planet because it was difficult to use. Rather, its user-friendly and rich feature set led to it finding a home on somewhere north of 70 million websites—and that's just counting blogs hosted on WordPress.com.

The most genius summertime snack hack that we've come across recently is, without a doubt, the campfire cone. Astounding in its simplicity and ease of preparation, yet brilliant in its execution, the campfire cone has something for everyone: parents and children, expert and novice campers, backyard barbecuers, and oven lovers alike.

This is a familiar scenario: you light up the grill, get cooking, eat the fruits of your labor, then clean up every trace of your barbecuing once you're finished — except maybe the hot charcoal, which usually gets dumped right before the next cookout.

Welcome back, my hacker novitiates! If you have been following this new Snort series, you know that Snort is the world's most widely used intrusion detection/protection system. Now a part of the world's largest network equipment company, Cisco, it is likely to be found everywhere in one form or another. This makes a compelling argument for learning how to use it, as it will likely be a necessity in any security-related position.

Near Field Communication, or NFC for short, is a feature that allows our smartphones to wirelessly communicate with other devices over a short distance while using almost no power at all. Think of it like a slimmed-down version of Wi-Fi or Bluetooth that can send a small burst of data two inches away without having any measurable impact on your battery life.

As one of the most powerful Android apps for connecting your phone or tablet to your other devices in various ways, Pushbullet had always been a fan—and Gadget Hacks—favorite.

As we're all aware, recon is vital to a successful hack. We need to know everything we can about the target in order to perform the best possible attack. Port scanning is a basic recon concept that is introduced very early in learning proper reconnoissance. The issue with port scanning is that is makes a lot of noise. Every connection to every port will be logged. This is where stealth scanning comes in. Also known as SYN or half-open scanning, stealth port scanning is a bit quieter, and is l...

Welcome back, my hacker novitiates! In an earlier Linux Basics tutorial, I had demonstrated the basics of the Apache web server. Since Apache is the world's most widely used web server on the Internet (as of July 2015, Apache was 38%, IIS was 26%, and Nginx is 15%), the more you know about it and understand it, the more success you are likely to have hacking it.

Welcome back, my greenhorn hackers! As all you know by now, I'm loving this new show, Mr. Robot. Among the many things going for this innovative and captivating program is the realism of the hacking. I am using this series titled "The Hacks of Mr. Robot" to demonstrate the hacks that are used on this program.

Welcome back, my fledgling hackers! Let's continue to expand our knowledge of digital forensics, to provide you the skills necessary to be a digital forensic analyst or investigator, as well make you a better hacker overall. In your attempts to enter a system or network undetected, it is key to understand what a skilled forensic investigator can learn about you, the alleged hacker.

At first glance, the Big Green Egg looks like it was created by Dr. Seuss or some other whimsy-driven being, like Zooey Deschanel. And while this earthenware cooker may look cute, it produces serious results that can rival the best barbecue or grill. In fact, it's got quite a large cult following. Entrepreneur and former Navy serviceman Ed Fisher fell in love with the taste of food cooked in kamodos (traditional domed, covered earthenware vessels in Japan) and began to import them for sale in...

If a tree falls in the woods and nobody is there to hear it, does it make a sound? If a person makes calls but doesn't have a Facebook account, are they even really a person? Yes, of course they are, but it just makes life easier when you're part of the world's biggest social network, as proven with Facebook's latest application, Hello - Caller ID & Blocking.

Salt is a miraculous substance. From the Ancient Egyptians to the Christian Bible, many cultures believe it to have mystical powers that can ward off evil, among other things.

You've undoubtedly seen this trick on the internet or from your beloved Italian nonna: balance a wooden spoon across a pot of cooking pasta to prevent the water from boiling over and creating an unsightly, sticky mess all over your stovetop. It's almost magical, that's how easy it is. The most popularly held belief is that the wooden spoon prevents heat from building up too much at the center of the pot, thus preventing the liquid from boiling too high—but this is not true.

Knowing how to cut and slice raw meat is a skill all omnivorous cooks need in their arsenal. However, raw meat's limp and gelatinous character can be challenging to work with, especially when you're trying to slice it into symmetrical, attractive sections for a stir-fry or a stew.

A new coat of paint is an easy, cheap way to make your home look instantly better, but dealing with paint fumes for days afterward isn't so fun, especially if you have kids or pets.

If you're like me (and everybody else probably), you probably have a few nights of reckless drinking that you wish your could take back, or at least turn down a notch.

I hate being cold. That's why I live in Los Angeles. But, there are plenty of folks who are experiencing some pretty chilly temperatures this year, despite global warming, and one of the worst places affected is the garage. C'mon, who has a freakin' heater in their garage?

Not many people fly kites anymore. Most of us don't have the patience or attention span because, let's face it, we're used to smartphones and other gadgets that have games and apps galore to entertain us. Heck, you can even fly a kite on them if you really want.

You may remember string art from your elementary school days. If so, it probably makes you think of the 2D geometrical designs that took every ounce of patience you had as a kid. Or those laborious curve stitch drawings, which string art was actually birthed from. But thanks to some innovative modern artists, string art has gotten a lot more interesting. Here are some of the most creative applications so far.

Have you ever wondered what sort of microscopic critters are floating around in your water? Well, you can find out with just a few bucks worth of materials and a laser pointer. Really. That's all it takes to build your very own homemade laser projection microscope, aka a water drop projector.

Welcome! Today I would like to share a few hints about picking the right color. So, if you do not know what color your today's outfit should be or your or which color you should choose for your room walls, please follow my suggestions.

How a Hovercraft can be build.Brittany is demonstrating how to make a Hovercraft. Since hovercraft needs a base she is using plywood for it. She takes square plywood of 48*48 and finds out its center to cut plywood in circle. Don’t forget to wear safety goggle while cutting the plywood. Then she takes a square plastic to make it an air cushion so that the hovercraft should float. In order to secure plastic to the wood she used screws and a plastic top. Then cut the vent hole and plastic by si...

Ho to remove your call log/history from Skype to protect your privacy.

In this Webcast, Password Management for Windows and Beyond, you will learn how to: Increase security standards cross-organization by easily customizing and enforcing password policies for Windows, Unix, Linux, and Java users.

In this expert video series, you’ll learn more about the history and general practice of wood burning. Get expert tips on wood burning pens and other equipment needed to practice the art of pyrography.

In this do-it-yourself video series, learn how to use a belt sander. This power tool allows you to complete large woodworking projects in minutes instead of hours, saving you the back-breaking effort of smoothing out large areas of rough wood by hand. Our expert will give you easy-to-follow shop safety tips, as well as how to care for and maintain your sander, how to operate the trigger system, and what types of wood to use.

In this instructional video series, learn the proper, safe way to use a reciprocating saw. Our expert will give you tips and techniques for doing metal and wood cutting work in a variety of settings. Demonstrations include important safety guidelines for saw use, choosing the reciprocating saw blade that is right for the job, ripping, how to replace a blade, and how to cut wood and metal.

This video shows various experiments with circular motion. In Dr. Carlson's Science theater he uses water, a lit candle, and a piece of paper to show the ways that circular motion causes gravitational pull. The water in a glass doesn't spill as it is spun around 360 degrees in a circle, even upside down. The flame on the candle was pulled toward the center when spun around. The piece of paper becomes a paper saw and was able to cut wood when spun. He not only demonstrates centrifugal force wi...

Making a wooden spear requires a between medium and small thick stick, a rectangular piece of board, a hatchet and a wood clipper. The branches off the stick is removed and thrown away. The stick is clipped at the smaller end. It is then placed on the board and the larger end is cut off with the hatchet, while the stick rotates in a circular motion on the board to remove the outer skin. Closer attention is paid the shaping and cutting of the point of that larger side to get it in formation. T...