When you need a file on your Mac as soon as possible, you usually have to get your MacBook or hop on your iMac, Mac mini, Mac Pro, or Mac Studio. But that's too much work if you're in bed, lying on the couch, or outside in the fresh air. Why even bother when you can access that file directly on your iPhone or iPad — without moving an inch?
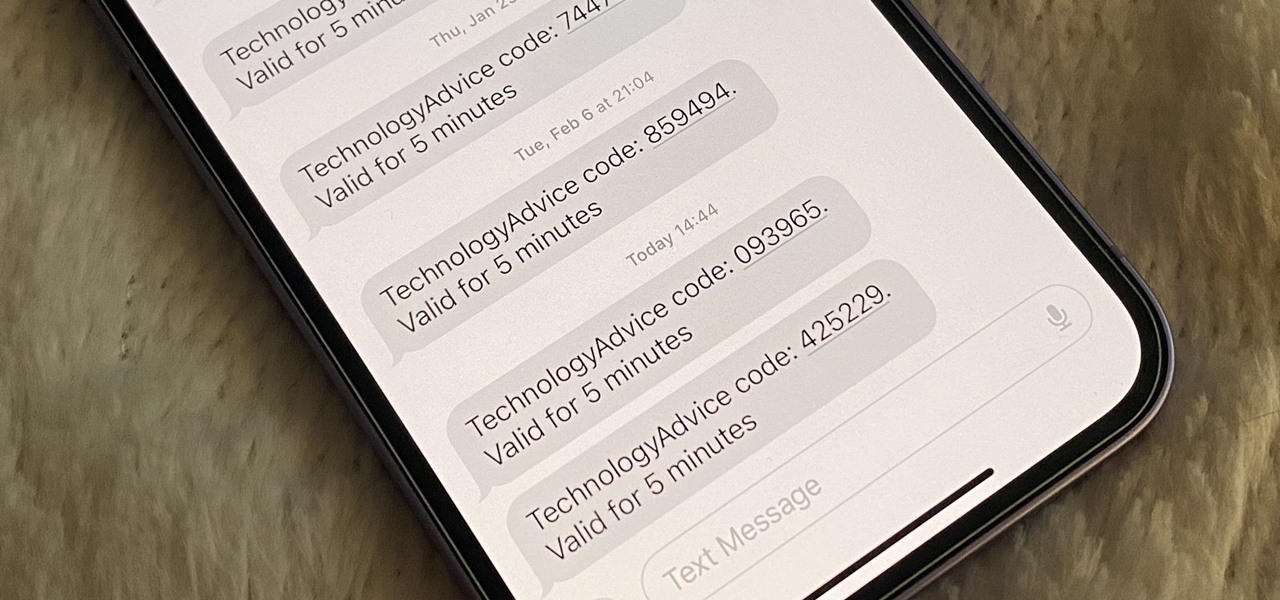
Many of your accounts online likely require two-factor authentication (2FA) or two-step verification (2SV) to confirm your identity when logging in, and there's a good chance the second factor or step for each is a one-time email or SMS verification code. If you get a lot of email and SMS codes, it can clutter your Mail and Messages apps with junk if you don't delete the messages after signing in.

When setting up your home office or giving it a makeover, the desk is the key to making the room a functional workspace. And if you're in there all day, it also has a significant impact on your health. Standing desks can help offset some of the adverse health risks associated with sitting all day, but it's hard to find a decent standing desk that won't break the bank. That's where Flexispot comes in.

Downloading content from TikTok is relatively easy, even if the video is protected, but the same can't be said of Reels, Instagram's version of short-form videos. Instagram doesn't make it easy to download content unless it's your own, and that's especially true with Reels. However, there is a way to bypass Instagram's restrictions on your iPhone and save videos locally without ever leaving the app.

Since iOS 13, your iPhone's come equipped with a fonts manager that lets you install custom fonts for use in Apple apps and supported third-party apps. To add fonts, you need to use a font provider app that'll load them on your device and register them system-wide, and one of these apps shines above all else.

The ability to browse the web in coffee shops, libraries, airports, and practically anywhere else you can imagine is more than convenient, but convenience has risks. Using public Wi-Fi allows others to spy on you easily. Even your own internet service provider can see every website you've ever visited. Don't fall into the trap of protecting your identity, data, and devices after it's too late.

Web applications are ubiquitous in the modern online world, and knowing how to attack them is an increasingly valuable skill. But the key to a successful attack is good recon since it's easier to be focused and efficient with the more information you have. There are many fingerprinting tools available, such as httprint and WebTech, but there are even more that can aid us in reconnaissance.

Your Apple Music subscription is tied to the Apple ID that subscribed, so you can stream content from any iOS, iPadOS, macOS, tvOS, or watchOS device that your Apple ID is signed in to. However, things get slightly more complicated when you want to listen to Apple Music on another device you use with a different Apple ID, such as a work iPhone. Complicated, but not impossible.

Now that more people are working from home on unsecured networks and personal devices, hackers are having a field day accessing everything from private browsing histories to personal banking information. A virtual private network (VPN) is the first and most important line of defense when it comes to protecting all of your devices from digital intrusions, but not all VPNs are created equal.

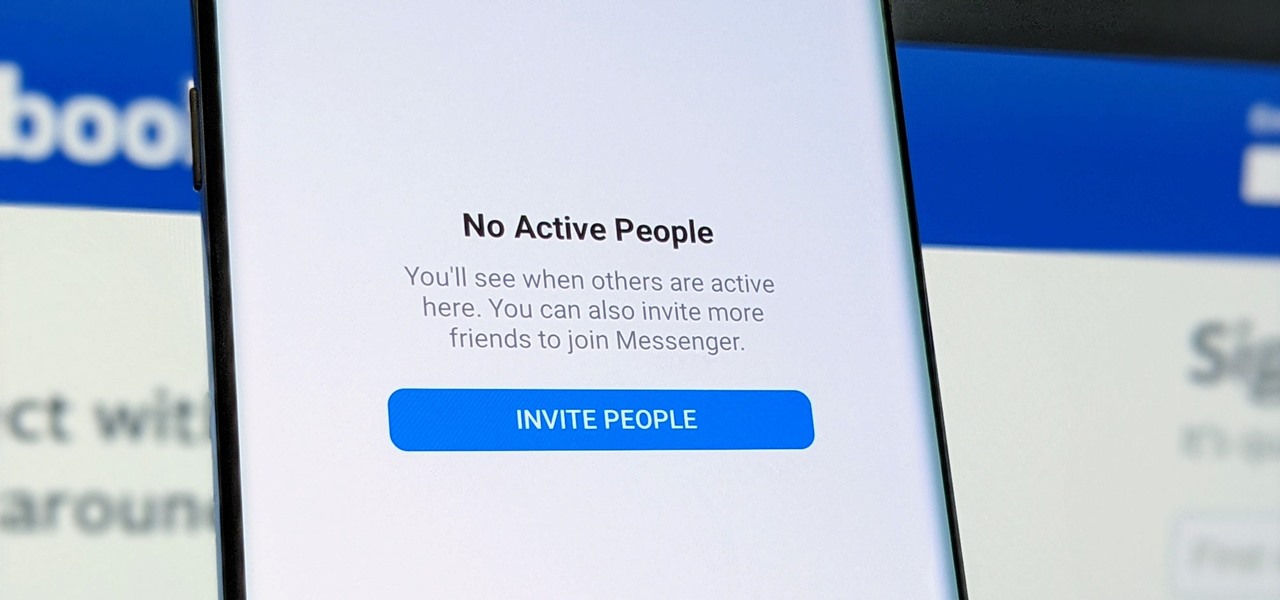
Facebook Messenger's user base has grown so much that it has taken over text messaging as the primary contact method for many people. However, sometimes you might want to hide your online status from specific contacts and appear offline to others. There's a neat little trick you should know that can help you achieve this.

Post-exploitation is often not quite as exciting as popping the initial shell, but it's a crucial phase for gathering data and further privilege escalation. Once a target is compromised, there's a lot of information to find and sift through. Luckily, there are tools available that can make the process easy. One such tool is Postenum.

As protests surge in the wake of George Floyd's murder by a Minneapolis police officer, powerful photographs and videos from the demonstrations have gripped the world, putting our nation's very real and very justifiable widespread civil unrest out into the digital world. Unfortunately, these pictures could put you or others in danger if precautions aren't taken before uploading them online.

Everything you post on social media lives there forever — even if you delete it. Just ask anyone that's ever posted something stupid. Instagram does not provide built-in tools to save or download images and videos from other users, but there are workarounds. Third-party tools make saving other people's photos and videos easy, and there are always screenshots.

Even under normal circumstances, it's almost impossible to speak to a representative for a government agency or company in just one try. Many systems will put you on hold for long periods or ask to call you back when someone is available, but there are still some out there that just give you the busy signal over and over again. In those cases, there's a jailbreak tweak that can help.

With more digital content than ever, the search feature on smart TVs is essential. But typing is such a terrible experience when you're forced to use voice dictation or peck around with the remote control. Thankfully, there's a better way.

Attacks against databases have become one of the most popular and lucrative activities for hackers recently. New data breaches seem to be popping up every week, but even with all of that attention, databases continue to be a prime target. All of these attacks have to start somewhere, and we'll be exploring a variety of methods to gather information on PostgreSQL databases with Metasploit.

The 2020 iPhone SE had been through the rumor mill for a long time, but Apple finally unveiled the second-generation iPhone SE on Wednesday, April 15. While it doesn't sport the 4-inch design of the original SE, it combines a small form-factor with modern specs. The big question, of course, is when and how you can get your hands on one.

The response to the COVID-19 pandemic means that social distancing has become the new normal. It also means that more Americans are using video conferencing to connect with colleagues working from home or friends and family in quarantine because of the new coronavirus.

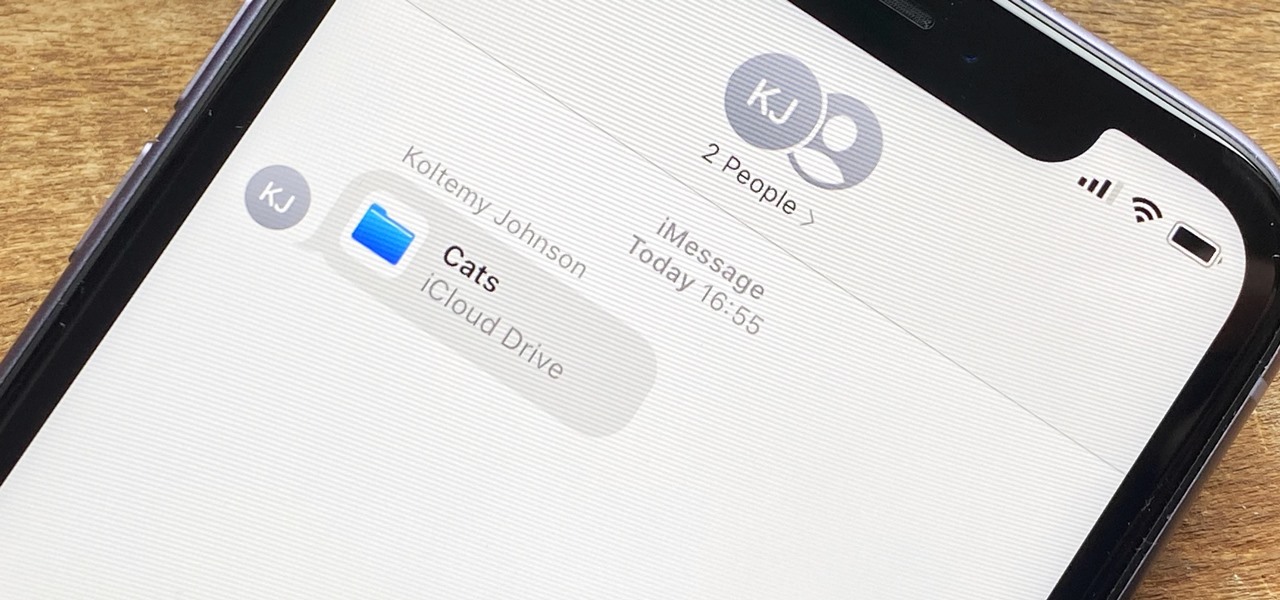
In the iOS 13.4 update, Apple added folder-sharing capabilities in the Files app. That means you can share multiple documents at the same time instead of doing it one by one. But that's not all — you can share folders with numerous contacts and even enforce access and permission settings.

In the last decade, the number of people working remotely in the US has increased dramatically, and so has their need for technology and software to supplement that remote work. Whether you work from home or a coworking office space, the requirement for highly compatible and helpful productivity apps is a must if you want to get things done successfully.

Smartphones are more like computers than actual telephones. Unfortunately, thieves, hackers, and other bad actors know this and are always looking to make money off your personal data. Thankfully, your Galaxy S20, S20+, or S20 Ultra has tools to combat these threats — as long as you know where to look.

Whether you've made a resolution to try and read more books this year or are just looking to set time aside to listen to an audiobook a little bit each day, building good reading habits can be tough with a busy life. However, with iOS 13, Apple Books includes reading goals, which might give you that little extra bit of encouragement and accountability to help you reach your goals.

As fun as Twitter is, it can also quickly turn scary. Anonymous, aggressive, and troll accounts can attack you for your tweets and stalk your every move. While you could make your profile private and block users, there are lesser-known privacy and security features that you can switch to improve your safety online.

As long as you're on the internet, you can be hacked. With an estimated 2.65 billion social media users, these apps are prime targets for hackers.

Brute-forcing is an easy way of discovering weak login credentials and is often one of the first steps when a hacker finds network services running on a network they gain access to. For beginners and experienced hackers alike, it's useful to have access to the right tools to discover, classify, and then launch customized brute-force attacks against a target. BruteDum does it all from a single framework.

Along with rebranding Magic Leap 1 for enterprise customers, Magic Leap has gifted its developer community with some new toys with a tease of more to come in 2020.

With EA chief executive Andrew Wilson stating the official mobile version of Apex Legends won't arrive until the 2021 fiscal year, fans have to wait at least another year to enjoy their favorite battle royale game on the go. But for those who can't wait, there are ways to play the game on iPhone and Android right now.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

|Choose Your View: Quick Bullet Points | Detailed Descriptions Android's newest major update is a special one — it's the tenth full version of the world's most commonly used operating system. The latest release, dubbed simply Android 10 (codename Android Q), was first showcased as a beta back in March 2019, so we've been digging around in it for several months. There's one dramatic visual change, plus there are a lot of goodies in general.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

Many popular apps automatically share your personal data. While I have accepted a certain amount of data collection from Google, to know companies such as Facebook perform this without my consent bothers me. After some researching, I've found a great solution, and it doesn't require root.

Passwords on Windows are stored as hashes, and sometimes they can be tough to crack. In certain situations, though, we can get around that by using the hash as is, with no need to know the plaintext password. It's especially interesting if we can manage to get the hash of an administrative user since we can then authenticate with higher privileges by performing an attack known as pass the hash.

KeePassX, 1Password, and LastPass are effective against keyloggers, phishing, and database breaches, but passwords managers rely on the operating system's clipboard to securely move credentials from the password vault to the web browser. It's within these few seconds that an attacker can dump the clipboard contents and exfiltrate passwords.

MouseJack vulnerabilities were disclosed over three years ago. Some wireless keyboard manufacturers have since issued firmware updates, but millions (if not billions) of keyboards remain unpatched worldwide, either because they can't be updated or because the manufacturer never bothered to issue one.

When you can't think of a way to respond in Messenger with words, emojis and stickers will do the trick. Since Facebook is all about the "likes," which use a thumbs-up icon, there's a shortcut to the symbol just to the right of the chat field. It's always there to send a quick like in response to something. But it doesn't have to be the standard Facebook thumbs-up sign — it can be any emoji you want.

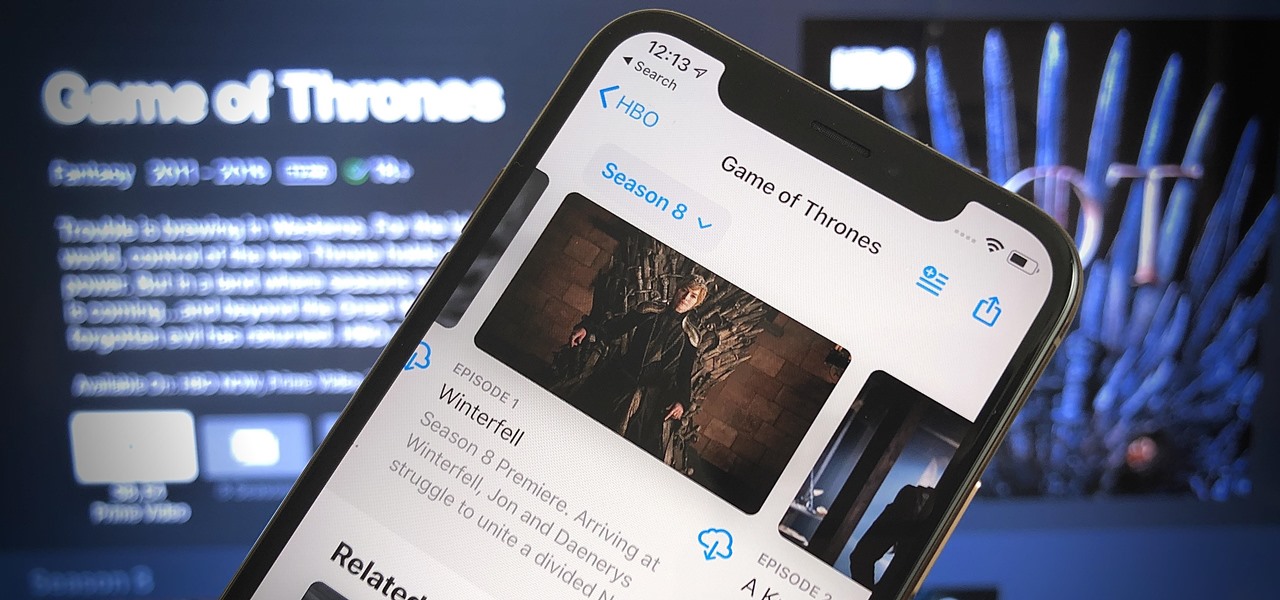
If you're a Game of Thrones fan and would like to watch the latest season offline on your iPhone, or if you need to catch up on previous seasons, there is no current support on HBO Go or HBO Now to download episodes for offline viewing. But that's only halfway true because there is a legal, official way to download HBO content on your iPhone, it's just not obvious at all.

The price of hacking Wi-Fi has fallen dramatically, and low-cost microcontrollers are increasingly being turned into cheap yet powerful hacking tools. One of the most popular is the ESP8266, an Arduino-programmable chip on which the Wi-Fi Deauther project is based. On this inexpensive board, a hacker can create fake networks, clone real ones, or disable all Wi-Fi in an area from a slick web interface.

Information gathering is one of the most important steps in pentesting or hacking, and it can often be more rewarding to run things on the target itself as opposed to just running scripts against it remotely. With an SQL injection, a hacker can compromise a server and, ultimately, upload and run the "unix-privesc-check" script locally in order to further identify possible attack vectors.

When it comes to digital security, one of the best ways to protect yourself is to use two-factor authentication. Most apps these days support it, including Facebook, a site where the more privacy you can muster, the better. However, of the two 2FA options available for Facebook, only one should be used as the other will share your phone number with the world, a huge privacy concern.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.