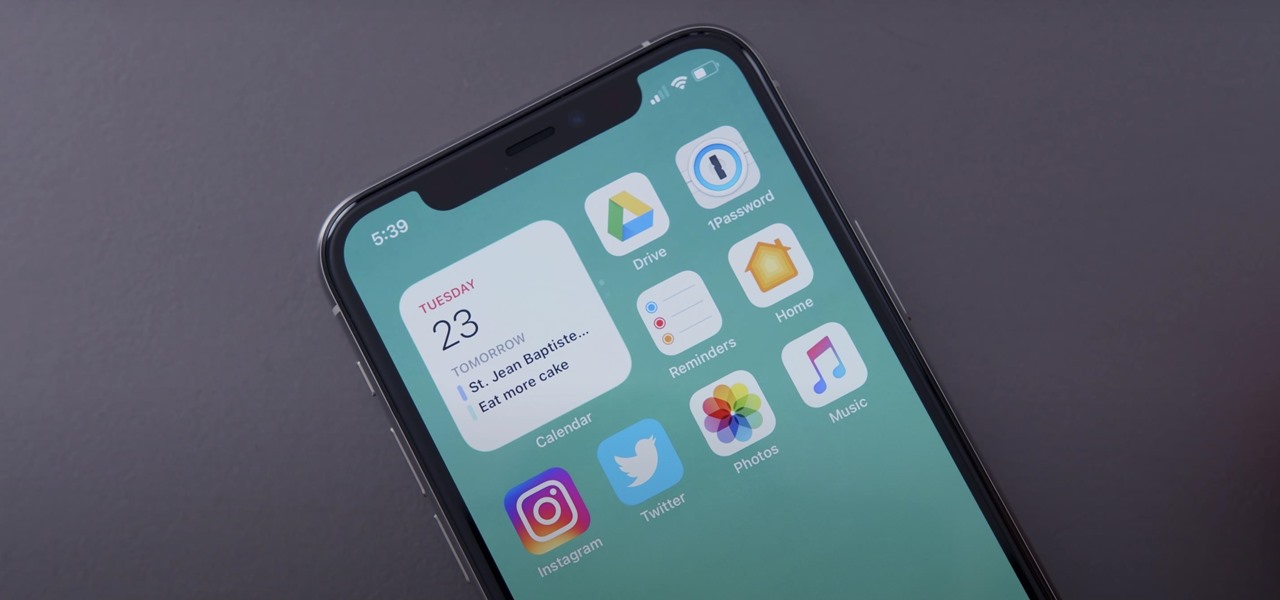
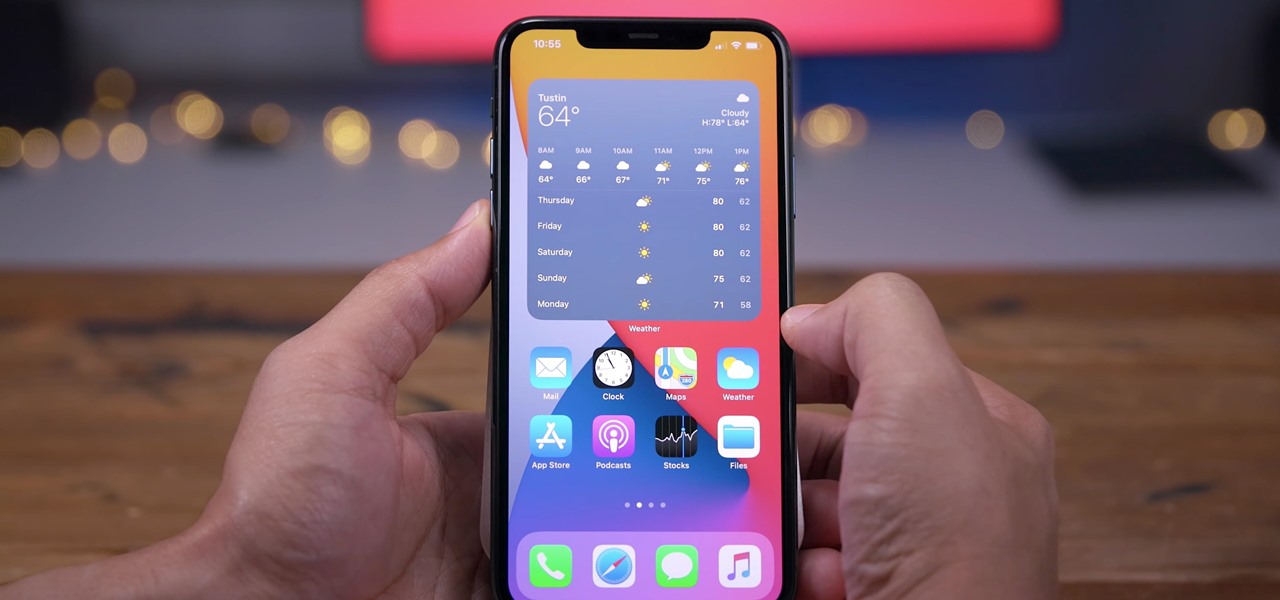
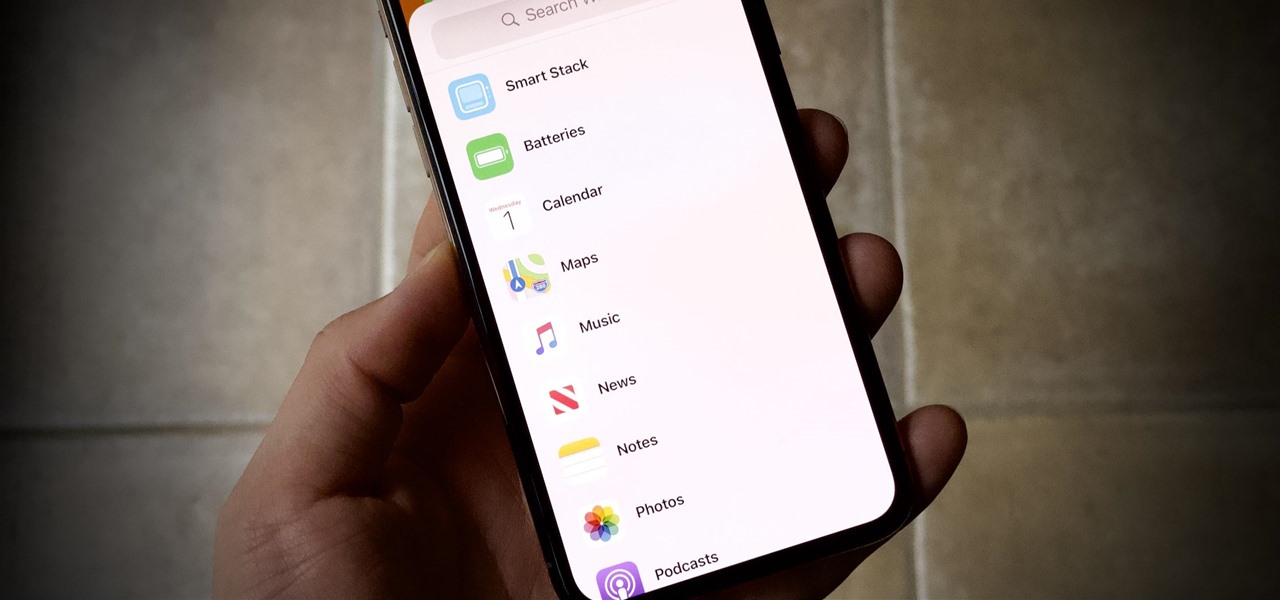
Streaming media companies like Netflix and Hulu make deals with Roku to have their apps featured on Roku's remote controls, but there's an inherent flaw with this model: the buttons become useless if the app no longer exists. So, is there anything you can do to change those defunct buttons on your Roke remote?

You should feel relatively safe to watch and post videos on TikTok, but like with any online service, you're always at the mercy of hackers.

Night mode, which helps you snap great photographs in low-light environments, is a feature available only on the iPhone 11 and iPhone 12 lineups. It's a useful tool to have in your arsenal, especially if you're fond of nightlife photography. Still, you don't have to purchase a newer iPhone to get Night mode shooting capabilities.
Outside of iPhone releases, software updates are arguably the most exciting aspects of iOS life. It's like Christmas morning when your iPhone installs an update, as you dive through your device to find all the new features and changes Apple thought to include. With iOS 14.4, there are at least 10 such new additions just waiting for you to explore.
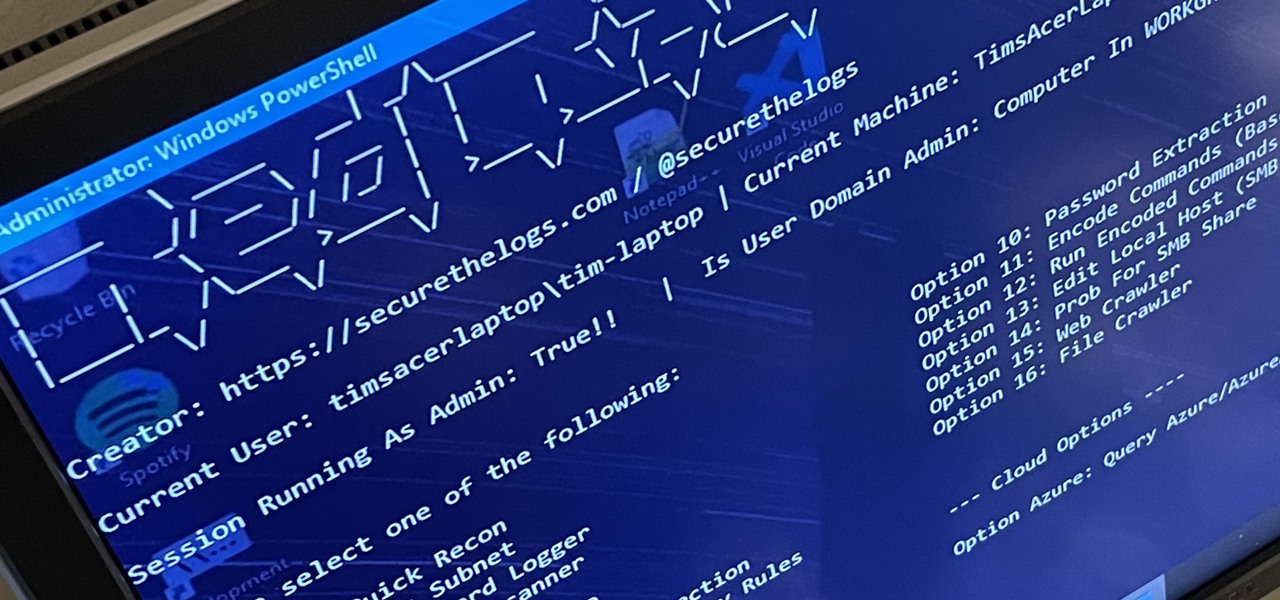
RedRabbit is an ethical hacking toolkit built for pen-testing and reconnaissance. It can be used to identify attack vectors, brute-force protected files, extract saved network passwords, and obfuscate code. RedRabbit, which is made specifically for red teams, is the evil twin of its brother, BlueRabbit, and is the offensive half of the "Rabbit Suite."

The year 2020 was a pivotal span of time during which the word "virtual" took on a brand new meaning. Instead of referring to VR or augmented reality, the term was hijacked to describe meeting across long distances through a variety of software tools, most often through video.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

The Pixel 5 is a great value proposition in this era of $1,500 phones. With its reasonable price tag, fully open-sourced software, and unlockable bootloader, it's also an ideal phone for rooting.

As we've seen with other tools and utilities, administrators typically use certain things to do their job more efficiently, and those things are often abused by attackers for exploitation. After all, hacking is just the process of getting a computer to do things in unexpected ways. Today, we will be covering various methods to perform banner grabbing to learn more about the target system.

Nearly every native app on the iPhone received an upgrade or new features in iOS 14 — and Safari is no exception. The web browser now has better password protection, faster performance, privacy reports, and built-in translations, just to name a few. Some of the Safari updates went unnoticed by many, but they're there and ready to use in iOS 14.

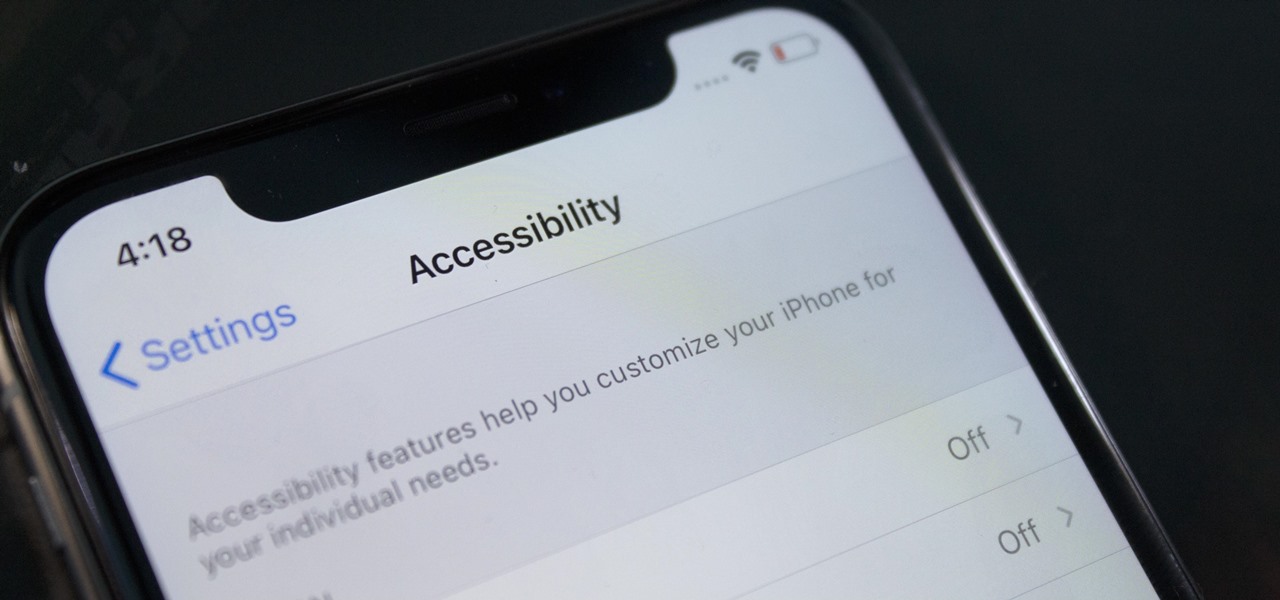
According to the CDC, one in four U.S. adults has a disability, where limitations can involve vision, cognitive function, hearing, motor skills, and more. That's why the iPhone has accessibility features; so that everyone can use an iPhone, not just those without any impairments. Apple's iOS 14 has only made the iPhone even more accessible, and the new tools benefit everyone, not just those that need them.

Widgets have been available on the iPhone for a while now, but they were tucked away in the Today View or hidden in the quick actions menu for app icons on the home screen. Android had always had a leg up on Apple in the widget department because they were so much more versatile, but that changed with the introduction of iOS 14.

If it has an internet connection, it's got a huge attack surface for hackers. But what makes your phone even more dangerous is its portability and the collection of sensors it houses that can be just as good at tracking you as the camera and mic.

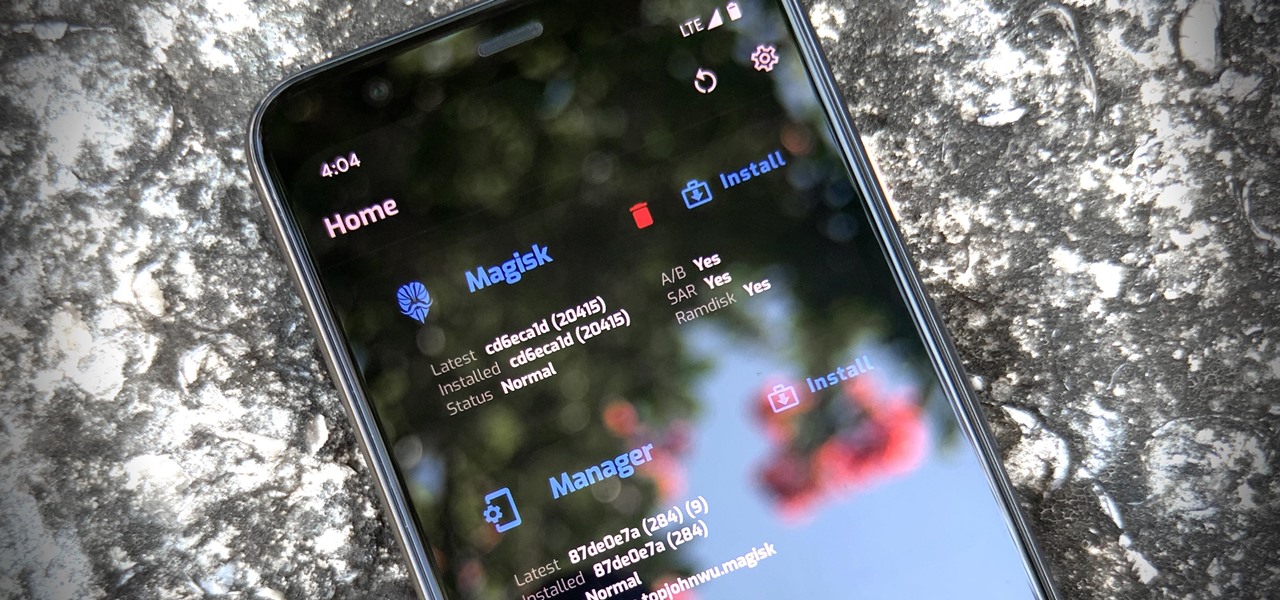
Thanks to Magisk, you don't have to lose root when updating to Android 11. The popular systemless rooting tool already achieved superuser access on Google's latest OS, even before the official release. It's currently in its experimental stages so the process is trickier than usual, but it does work.

Microsoft's built-in antimalware solution does its best to prevent common attacks. Unfortunately for Windows 10 users, evading detection requires almost no effort at all. An attacker armed with this knowledge will easily bypass security software using any number of tools.

There are countless tutorials online that show how to use Netstat and Tasklist to find an intruder on your computer. But with a few PowerShell functions, it's possible for a hacker to evade detection from the almighty command line.

Your iPhone and Mac can speak to each other in many ways, allowing you to start work on one device and seamlessly switch to the other, share clipboards between the two, and pick up phone calls and answer text messages on both. The compatibility is incredible, but there's even more you can do by incorporating third-party software into the mix.

Apple just released the fifth public beta for iOS 14 today, Wednesday, Aug. 19. This update comes one day after Apple released iOS 14 developer beta 5. It follows iOS 14 developer beta 4 by 15 days, and iOS 14 public beta 4 by 13 days.

Apple just released the fifth developer beta for iOS 14 today, Tuesday, Aug. 18. This update comes two weeks after Apple released iOS 14 developer beta 4, and 12 days after the release of iOS 14 public beta 4.

Apple just released the fourth public beta for iOS 14 today, Thursday, Aug. 6. This update comes two days after the company released iOS 14 developer beta 4, 15 days after Apple seeded developers the third dev beta, and two weeks after the release of public beta 3.

Apple just released the fourth developer beta for iOS 14 today, Tuesday, Aug. 4. This update comes 13 days after Apple seeded developers the third dev beta, and 12 days after public testers got their hands on public beta 3.

Apple just released the third public beta for iOS 14 today, Thursday, July 23. This update comes one day after the company released iOS 14 developer beta 3, and two weeks after the release of iOS 14 public beta 2.

Apple just released iOS 14 developer beta 3 for iPhone today, Wednesday, July 22. The update comes 15 days after Apple released the second developer beta for iOS 14, and 13 days after the release of iOS 14 public beta 2.

Apple just released public beta 2 for iOS 14 today, Thursday, July 9. The good news comes two days after Apple released the second iOS 14 developer beta, and 17 days after the release of the first developer beta. While this is the first public beta for iOS 14, it's called "public beta 2" to keep in line with developer beta numbering.

Apple just released the second developer beta for iOS 14 today, Tuesday, July 7. The update comes 15 days after Apple seeded developers the first iOS 14 beta, which introduced home screen widgets, picture-in-picture, and 4K YouTube support, among more than 200 other features.

Hackers often find fascinating files in the most ordinary of places, one of those being FTP servers. Sometimes, luck will prevail, and anonymous logins will be enabled, meaning anyone can just log in. But more often than not, a valid username and password will be required. But there are several methods to brute-force FTP credentials and gain server access.

Using a strong password is critical to the security of your online accounts. However, according to Dashlane, US users hold an average of 130 different accounts. Memorizing strong passwords for that many accounts is impractical. Fortunately, password managers solve the problem.

What appears to be an ordinary MP4 may have been designed by an attacker to compromise your Linux Mint operating system. Opening the file will indeed play the intended video, but it will also silently create a connection to the attacker's system.

Trying to figure out which music streaming service to subscribe to can be a difficult task when the playing field is so crowded. Each has its benefits, as well as downsides, so finding the right one for your needs and wants can take a lot of overwhelming research. But we've done all the research for you to help you find the best music subscription your money can buy.

Data can be injected into images quickly without the use of metadata tools. Attackers may use this knowledge to exfiltrate sensitive information from a MacBook by sending the pictures to ordinary file-sharing websites.

SSH is one of the most common protocols in use in modern IT infrastructures, and because of this, it can be a valuable attack vector for hackers. One of the most reliable ways to gain SSH access to servers is by brute-forcing credentials. There are a few methods of performing an SSH brute-force attack that will ultimately lead to the discovery of valid login credentials.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

After installing Ubuntu as your primary OS, you should have protected against USB Rubber Ducky payloads, defended against hard drive forensics, and reduced the overall attack surface against physical strikes. When defending against network-based attacks, you'll want to minimize hardware disclosures, prevent packet sniffers, harden firewall rules, and much more.

To name just a few companies, VK, µTorrent, and ClixSense all suffered significant data breaches at some point in the past. The leaked password databases from those and other online sites can be used to understand better how human-passwords are created and increase a hacker's success when performing brute-force attacks.

A mention of the deep web can bring to mind images of drugs, hackers, and other criminal activity. Despite the presence of these elements, the Tor network is a valuable tool for preserving privacy and anonymity. And browsing the deep web and any hidden services can be as simple as downloading the Tor Browser.

Sometimes I forget that I'm also a fiction writer, so I thought it might be a nice change of pace to share one of my stories with you. I wrote this piece awhile ago for an anthology that never came together and I'm tired of just sitting on it.

I am not trying to ruin anyones hopes and dreams...BUT... Look, say you go to Graduate school in fine art. You graduate 3 years later, $100,000 in dept. You go into a workforce which is so over saturated, you can't get a job making copies at kinkos.

Today's digital cameras record not only the images themselves, but also the metadata behind the scenes, like camera settings, location, date, time, etc. But there's a lot more to say about a photograph. What's the subject? Is it night or day? Outside or inside? Person, place or thing?

Sending and receiving email on the go is made easy with the Apple's "Mail" app on the iPhone. However, up until the release of iOS 5, plain text was the only option for sending emails (even though well-formatted messages could still be received). The information below, coupled with unlocking the emoji keyboard will make you an unstoppable force of communicating accurately.

A full QWERTY keyboard makes typing out a text message simple on the Blackberry Curve. Short cut keys may take some time to get used to, but once mastered, texting will only take a second. Watch this video cell phone tutorial and learn how to send an SMS text message on a Blackberry Curve. Send a text message from a Blackberry Curve cell phone.