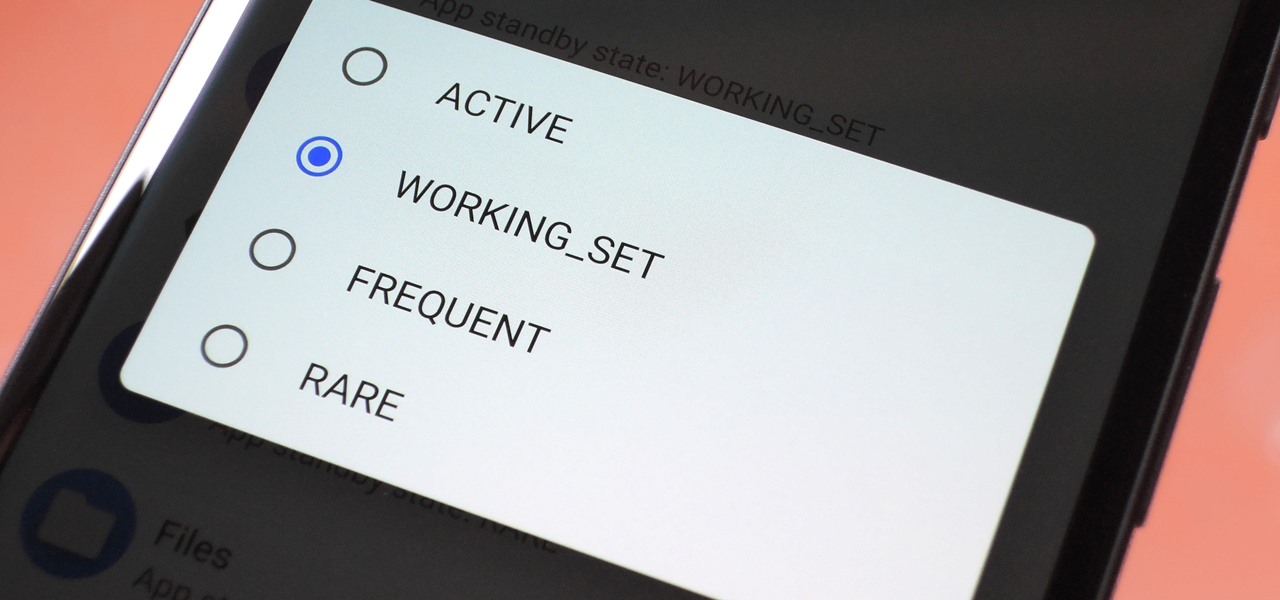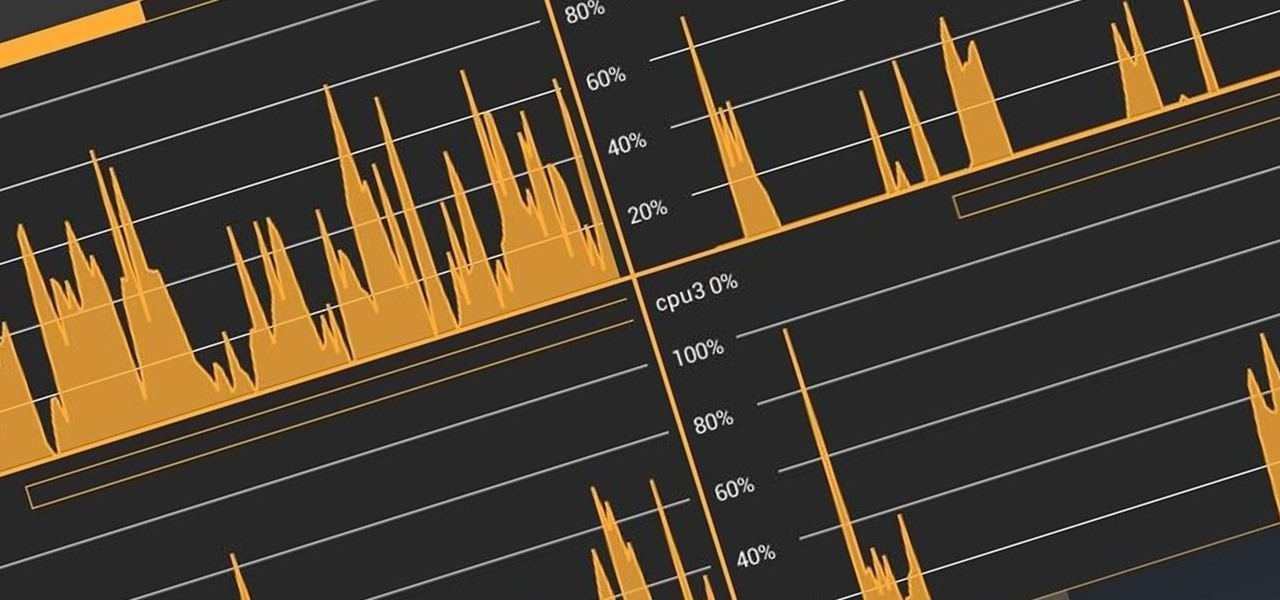
I remember how fast my Nexus 7 was the first time I turned it on. Boy, do I miss it. Now my tablet is pretty buggy and crashes happen frequently, and I'm sure that goes for many of your Nexus 7s as well. Even if you upgrade to the new Nexus 7 next week, it will eventually develop similar issues.
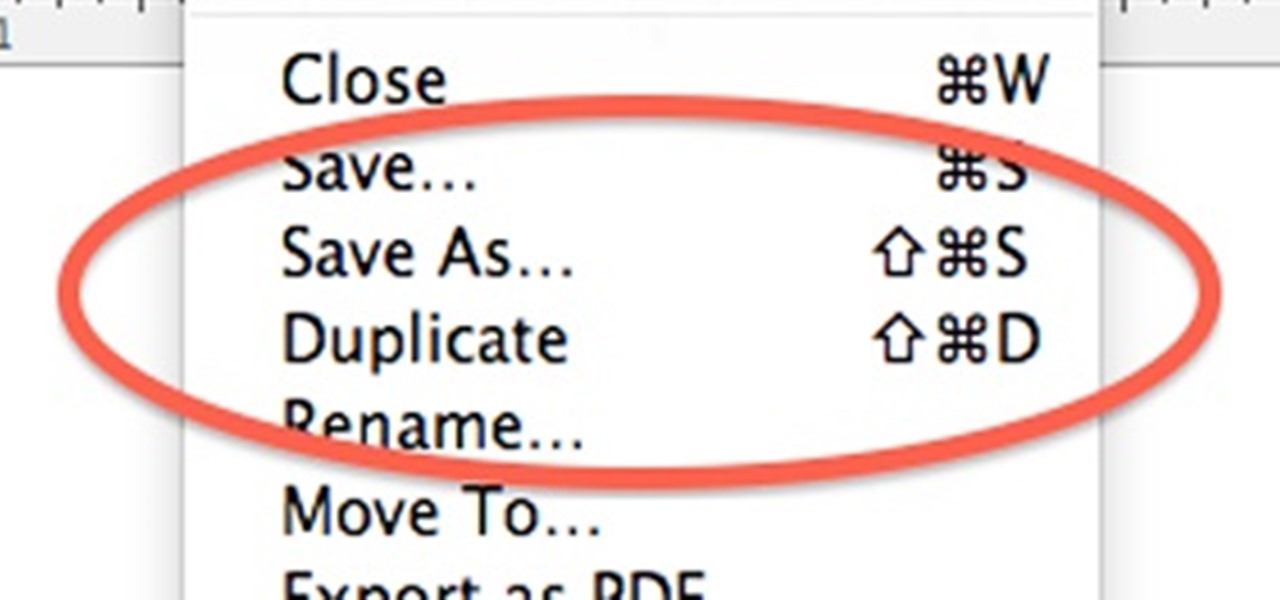
When OS X Lion (10.7) debuted last year, a lot of Apple users were dismayed that the "Save As" option had disappeared, replaced by the "Duplicate" function. Most felt that it just wasn't the same, so when Mountain Lion was released, the "Save As" option was brought back… sort of.

In a stunning end-of-year twist to the Magic Leap versus Nreal legal saga, the China-based startup is now filing a motion against Magic Leap.

It wouldn't be iPhone season without a new controversy. Chargegate, Apple's latest PR nightmare, is the name being used for charging issues on some iPhone XS and XS Max devices. If you plug in your iPhone at night — or whenever — then wake up or come back later and see that your iPhone has even less battery power, you're affected. But there is a fix you can implement right now.
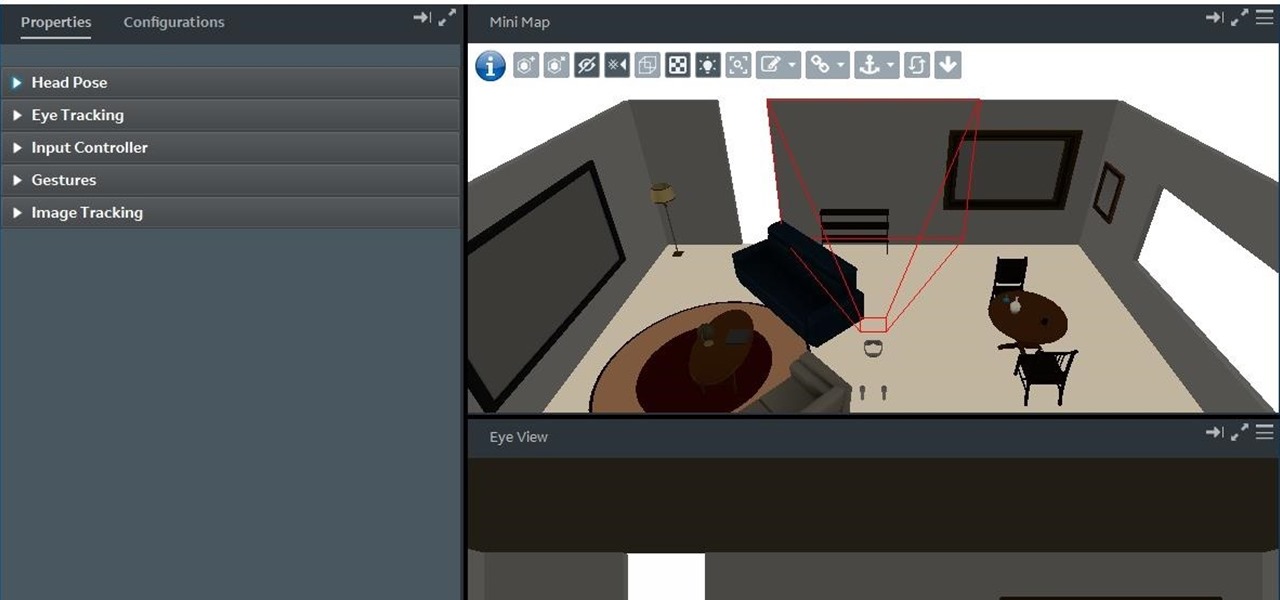
With the reveal of Magic Leap's developer documentation last week, many questions have been answered—and several new ones have been raised as well. But since the Magic Leap One (ML1) isn't simply called the "Leap One," these are questions that the company probably has no interest (at least for now) in answering. Understandably, Magic Leap wants to keep some of the "magic" under wraps.

Welcome back, my novice hackers! You have probably heard of the Panama Papers hack by now. This was a hack of the servers at Mossack Fonseca, a major law firm in Panama. This law firm specializes in assisting the rich and powerful to hide their wealth from taxes and scrutiny by creating tax havens overseas.

Very often we have processes in Linux that we want to always run in the background at startup. These would be processes that we need to start at bootup and always be available to us.

Welcome back, my aspiring hackers! In this series, we continue to examine digital forensics, both to develop your skills as a forensic investigator and to avoid the pitfalls of being tracked by a forensic investigator.

Welcome back, my greenhorn hackers! Throughout this series on Metasploit, and in most of my hacking tutorials here on Null Byte that use Metasploit (there are many; type "metasploit" into the search bar and you will find dozens), I have focused primarily on just two types of modules: exploits and payloads. Remember, Metasploit has six types of modules:

Welcome back, my rookie hackers! In my ongoing attempts to familiarize aspiring hackers with Linux (nearly all hacking is done with Linux, and here's why every hacker should know and use it), I want to address a rather obscure, but powerful process. There is one super process that is called inetd or xinetd or rlinetd. I know, I know... that's confusing, but bear with me.

Welcome back, my novice hackers! In this continuing series on Metasploit basics, let's next look at a module that many aspiring hackers find useful—autopwn.

One of the best things about the Samsung Galaxy S3 is the ability to modify the device in countless ways, as with any other Android device.

Battery drain is a major pain point for Android users, though that promises to change thanks to Android Pie's new Adaptive Battery feature. But Google hasn't said much about the inner workings of this feature, only publicly stating that it uses AI to boost battery life. So we dug in to find out what's really going on under the hood.

While some researchers look for drugs to treat HIV, other scientists delve deep into the virus itself for answers on how it causes infections.

It seems like whenever someone sees my phone, they ask me two questions right off the bat; "What phone is that?" and "How did you get your Android to look like that?"

No matter what device you have, Android lag will get you down. It's our little green robot's only major downside, and you've probably noticed it quite a bit on your Nexus 7 tablet. Apps open slowly, actions stutter or pause, and loading files takes forever.

Does TikTok scare you? Trust me, I get it. It's a strange, unfamiliar place to those of us not accustomed to its ways, populated by teenagers and college students with their own subcultures, memes, and humor. But here's the thing: TikTok has something for everyone, you included.

YouTube's massive user base comprises almost one third of all people on the internet, and collectively, users spend well over 100 million hours on the site watching billions of videos each day. Add it all up, and this means that YouTube is viewed by more people than any U.S. cable network—making it by far the favorite "TV station" of the internet generation.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

If you haven't read the last article, feel free to stop by and give it a read, but abstaining from reading it will not, for the most part, be detrimental to your understanding.

Welcome back, my hacker novitiates! In the previous two posts in this series, we looked at the basics of buffer overflows. In this post, we will look at one technique for finding buffer overflows. We will try to send random, oversized, and invalid data at a variable to see whether we can make it crash or overflow. This process is known as fuzzing. It is often the first step to developing an exploit, as we need to find some variable that is susceptible to overflowing.

Welcome back, my aspiring hackers! In many of my earlier tutorials, I mentioned the complementary nature of hacking and forensics. Both disciplines, hacking and forensics, benefit from a knowledge of the other. In many cases, both disciplines will use the same tool. In this tutorial, we will use another tool that can be used in either discipline—Sysinternals—a suite of tools developed by Mark Russinovich.

Welcome back, my greenhorn hackers, and happy New Year! Now that your heads have recovered from your New Year's Eve regaling, I'd like to grab your attention for just a moment to preview 2015 here at Null Byte. I hope you will add your comments as to what you would like to see, and I'll try to honor as many requests as I can.

Influencers of augmented reality demonstrate expertise in their fields and outline a strong vision for the future that they evangelize to others. They help define the direction of the industry and identify others who foster and create innovation in the field.

Puzzle games are great at giving your brain a workout while keeping things fun and killing time. They stimulate your noggin as you strategize and plan your next move, whether it's to keep your character from getting killed, or to get that special item to finally complete your collection and unlock a new feature within the game.

If your phone has an unlocked bootloader, you can use Fastboot commands to flash factory images. That may sound like a bunch of technical jargon, but when it comes down to it, this is the best method for updating a rooted device, fixing a bricked phone, reverting to stock, or even getting new Android updates before everyone else.

Kali Linux is probably the most well-known hacking distribution among penetration testers. However, there are alternative distros which offer versatility and advanced package management systems that are absolutely worth considering.

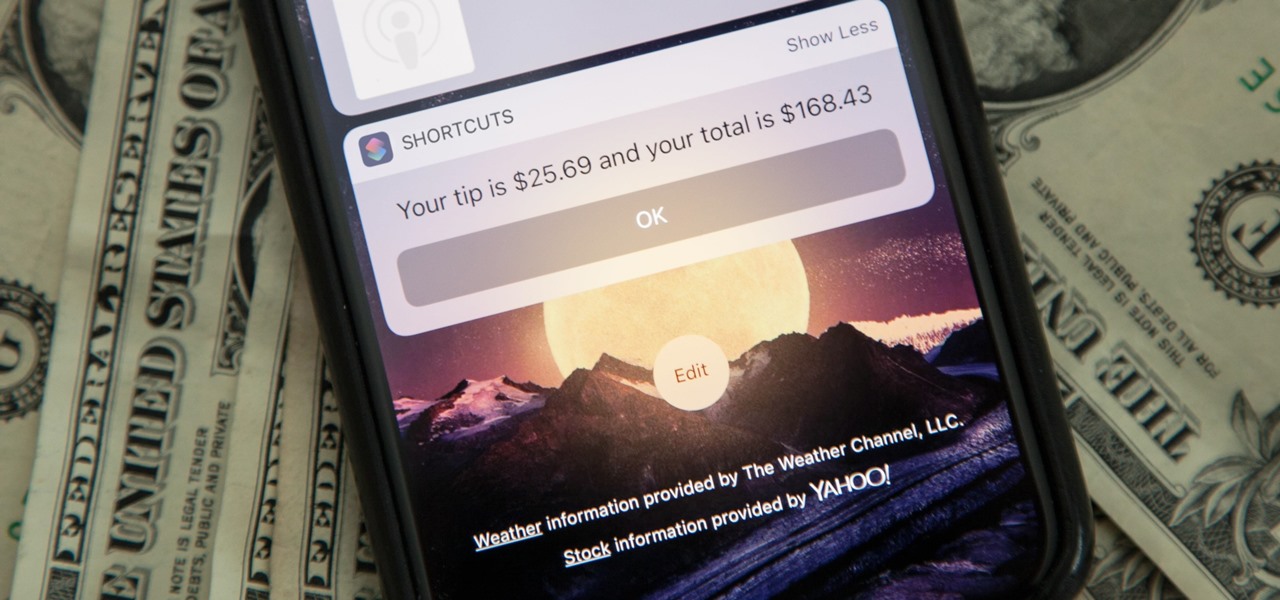
When it's time to calculate a tip at a restaurant or bar, I usually try some mental math at first, but sometimes I resort to opening the Calculator quickly from the Control Center on my iPhone and doing a quick calculation. But with Apple's Shortcuts app, there's an even easier way, and you don't even have to leave your lock screen to get the results.

You've protected your Ubuntu system from physical attacks, annoyed network hackers, and sandboxed potentially malicious applications. Great! Now, the next logical steps to locking down your OS include thoroughly auditing Ubuntu for weak points, using antivirus software that respects your privacy, and monitoring system logs like a boss.

Haven't quite appreciated the beauty of a digital camera yet, but still don't know all about that manual SLR of yours. This video serves as a manual to the workings of your SLR 35mm camera.

Music theory is a field of study that focuses on the intricate workings and mechanics of music. Learn about guitar music theory and intervals from a professional musician in this free guitar video.

In this series of expert video clips, learn more about the theremin. Our expert goes into detail about what makes up the complicated workings of the theremin including the coils and other components. Get a full history on the musical instrument and learn about the many uses of a theremin. What makes a theremin sound so special? Get answers to this question and many more in our expert instructional videos.

Jim Koch has worked as a repo man and a locksmith. He gives you an insider's perspective on how to theft-proof your home by setting up surveillance systems and engraving your possessions. He also explains the basic workings of several kinds of locks and how to pick them. So next time you like lose your keys, you'll know exactly how to get in. And how to keep Big and his friends out.

Chris Chianelli talks a bit about nitro engines and using the main needle valve. Without knowledge of the vehicle's engine, you won't be able to use the RC vehicle to the max. Watch this video tutorial and learn the inner-workings of an RC vehicle engine.

Some of you may stick with your iPads, but for those looking for a similar Android version, you finally have a winner.

The brush engine was developed back in Photoshop 7 (before CS) and is what makes Photoshop a true painting program and revolutionized the way Photoshop works. In the longest episode of PixelPerfect yet, Bert explains and demonstrates the inner workings of the brush engine. This is a great tutorial for those that are new to Photoshop. Use the brush engine in Photoshop.

Chain locks are hardly highly secure to begin with, but a fun MacGyver-style trick nonetheless. Add it to the lock picking vault. Crack a Master Lock - Mathematically, No Shim.

Animatronics: the use of electronics and robotics in mechanized puppets to simulate life, mainly used in moviemaking, but also in theme parks and other forms of entertainment. (wikipedia)
Monday 27 February, WikiLeaks began publishing The Global Intelligence Files – more than five million emails from the Texas-headquartered "global intelligence" company Stratfor. The emails date from between July 2004 and late December 2011. They reveal the inner workings of a company that fronts as an intelligence publisher, but provides confidential intelligence services to large corporations, such as Bhopal’s Dow Chemical Co., Lockheed Martin, Northrop Grumman, Raytheon and government agenc...

chrof Instructables boasts: "This is the most comprehensive step-by-step guide to build an 8x8x8 Led Cube ever published on the intertubes. It will teach you everything from theory of operation, how to build the cube, to the inner workings of the software."