Reddit user craigyboy2601 knows a thing or two about airline baggage handlers. After all, he is one. So, when he offers some tips on how to protect your luggage from loss or damage, you should probably pay attention! Here are the highlights from his post.

In this video, Jeff Cavalier demonstrates how the viewer can obtain six pack abs in just twelve weeks while training at home. He begins by explaining that he will show the viewer five separate work outs techniques. The first exercise is called a X-man crunch. To complete this exercise you must lay on your back, with your body in an "X" shape. You then tighten your stomach muscles and bring your legs and your arms together towards the middle. The second exercise is called Heels to the Heavens....

In this Education video tutorial you will learn how to know if matrices can be multiplied. If the column of the first and the row of the second match, you can multiply them. For example if, matrix A has 2 rows and 3 columns (A: 2x3) and matrix B has 3 rows and 4 columns (B: 3x4), then you can multiply them. But, if A: 3x2 and B: 3x4, you cannot multiply them. The shape of the resultant matrix will be the shape of the outer numbers. For example, we saw that if A:2x3 and B :3x2, then they can b...

Mudtokens of YouTube found a way to quickly level up in Modern Warfare 2 and wants to share. His method of doing this is to get 12 of your friends into a ranked lobby, making it a full game. After this, you get one person from each team, who will be the one getting ranked up. For this to work, however, you need 2 load outs, both of which need to have One Man Army and Stopping power, one with a light machine gun, and the other with a riot shield. The two meet up in the game, and take turns blo...

Rubik’s UFO is an out-of-this-world puzzle experience from the inventors of the world famous Rubik’s Cube! A few twists and turns completely scrambles the UFO. The challenge is to put the UFO back in working order with all the colors matching up.
So, you've just plugged in your new Chromecast with Google TV. You lean back to watch a TV show or movie and you notice that people look kind of ... odd.

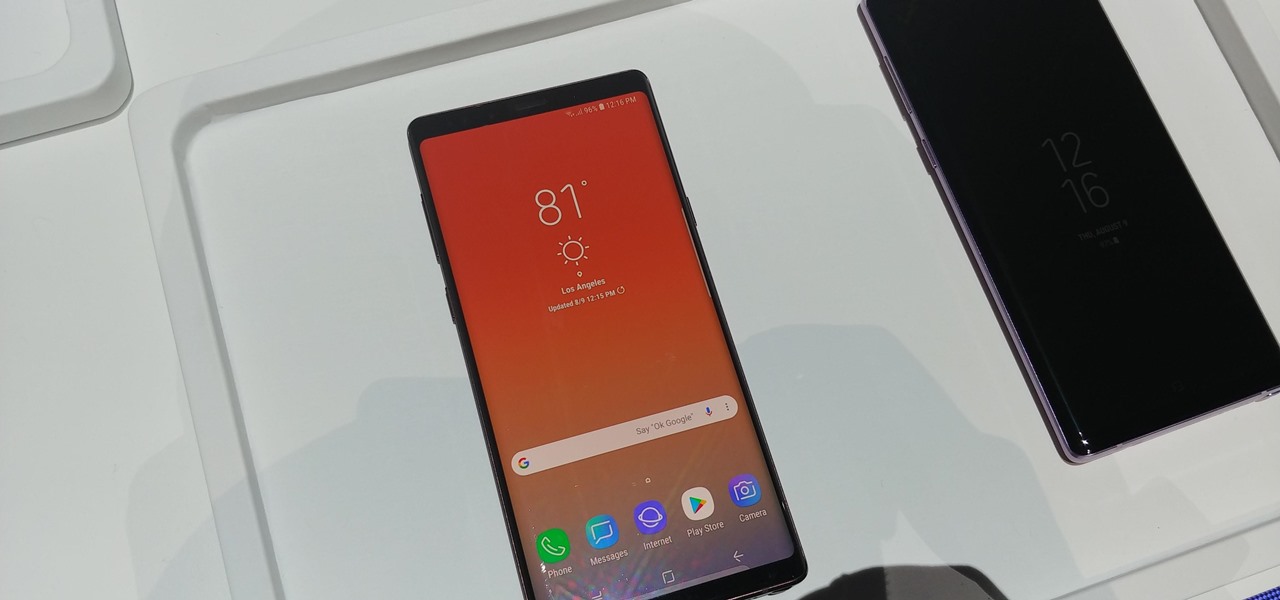
iPhones with Face ID all retail for at least $999, which many still believe is just too much for a smartphone. But that's okay, because Apple just introduced the iPhone 11 for roughly $700. It's not necessarily the best value, though, because the iPhone 11 already has some stiff competition in this price range.

We've already shown you our favorite new action games that have come out this year, but now it's time to share our all-time top ten list. These games are available for both Android and iPhone, they don't have intrusive ads or freemium schemes, and most importantly, they're all completely free to play.

It was only a few years ago when the idea of a 5+ inch display on a smartphone was unreal. With most hovering around four inches at the time, a phone that big seemed impossible to hold. We've come a long way since then, but it appears another wave of large displays will soon hit us, and they are all at least six inches.

Networking is built largely on trust. Most devices do not verify that another device is what it identifies itself to be, so long as it functions as expected. In the case of a man-in-the-middle attack, we can abuse this trust by impersonating a wireless access point, allowing us to intercept and modify network data. This can be dangerous for private data, but also be fun for pranking your friends.

The sheer variety of Android devices on the market is staggering—one report suggests there are well over 24,000 distinct phones and tablets floating around out there. When you consider that each manufacturer adds a few tweaks to the Android code base here and there, that makes for a lot of software variations, which in turn means there needs to be many different root methods to match this variety.

Welcome finally, to a tutorial on buffer overflows! At last we have reached an exciting part of this series where I will dedicate the entire article on explaining and exploiting the notorious vulnerability. Grab some popcorn, sit back and enjoy the show.

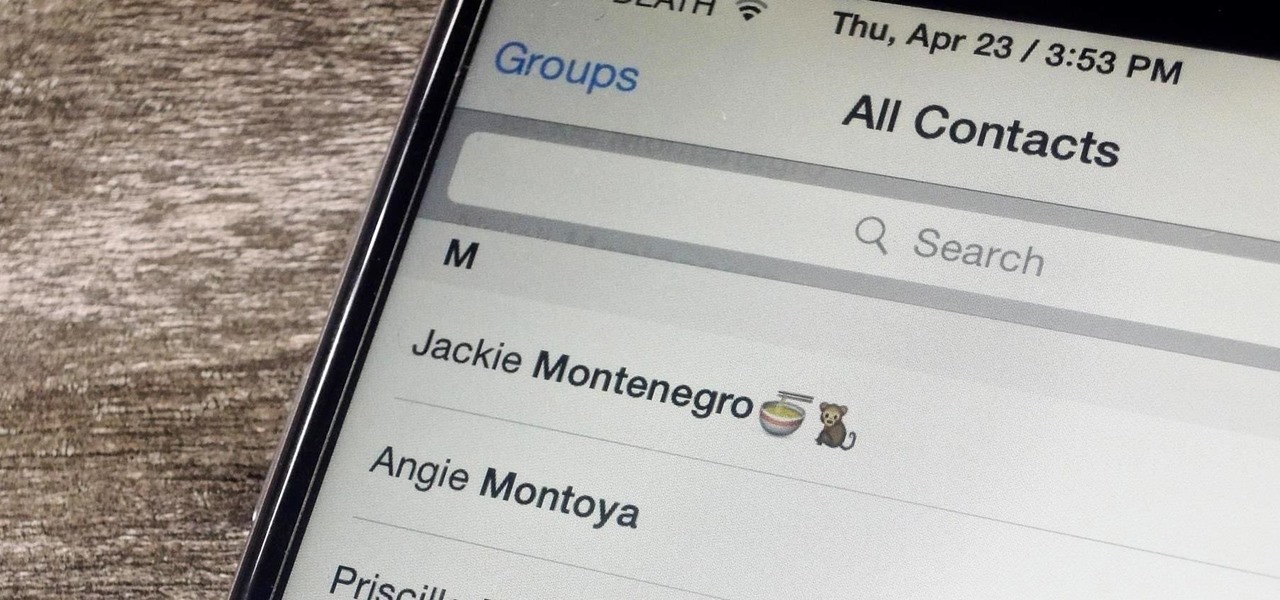
Organizing contacts is a bitch, especially on the iPhone. Some contacts will have multiple entries, you can only delete contacts one by one, and certain types of contacts can't be deleted at all. If that isn't enough to make you pull your hair out, then I don't know what will.

Disney's animated film Toy Story 3 beat all expectations at the box office, and is now the highest-grossing movie of 2010 in North America and second worldwide. Can Disney Interactive Studio's Toy Story 3: The Video Game match the success? Who knows, but no matter how successful it is, it's still a fun game full of animated delight, and this Mahalo video walkthrough series will show you the entire gameplay for the game on the Xbox 360.

In order to set up your email in Outlook Express IMAP, you will need open Outlook. In accounts, enter your user name in the box above: "for example John Smith". Switch the incoming mail server to IMAP. Fill in your server and outgoing mail SMTP.

When holding a belly putter in golf, a longer grip should be used than the type of grip used for a normal putter. In this tutorial, learn how to use that belly putter effectively and win every match. In this video, you will discover methods for keeping a belly putter centered. Staying centered is the key to excelling at this type of swing. So, if you are ready to master that putter.. follow along and you'll be ready to hit the course!

Accents are not only fun but attractive too, when done properly, at least. Work on your Irish accent, practicing the inflection and sound of consonants and vowels. Impress your friends with your new accent.

Make sure to get a complete upper body workout and add cable crossovers to your exercise routine. These crossovers can be done at varying angles to work a variety of chest and arm muscles without changing machines. Your pecs will thank you.

Staying in shape will give tennis players an edge over their opponents. Learn how exercises and increasing strength and agility will make you a better tennis player in this free workout video.

Boxing workouts to do with a medicine ball. Learn about training to be a better boxer with these medicine ball exercises in this free video series.

Ease your aching back! Learn exercises and stretches to reduce back aches and pains in this free back pain workout from our health and fitness expert.

This video tutorial shows how to mix your own clay body. Covered are the basic types of clay, fluxes, and fillers. When testing clay body mixtures, make 1000 gram batches dry, then add water to that. This way a percentage recipe can be taken and just by moving the decimal point can convert it to grams (25% = 25 grams or 250 grams, etc). Here is a clay-body recipe is as follows for those of who might care. Also, much of the mixture of a clay body is designed to match the glazes. It needs to me...

Apple's first release candidate for the iOS 14.3 beta came out on Dec. 8, but there must have been a serious bug in the system because iOS 14.3 RC 2 followed it just two days later on Dec. 10. These builds highlight everything that you should expect to see on the stable version very soon.

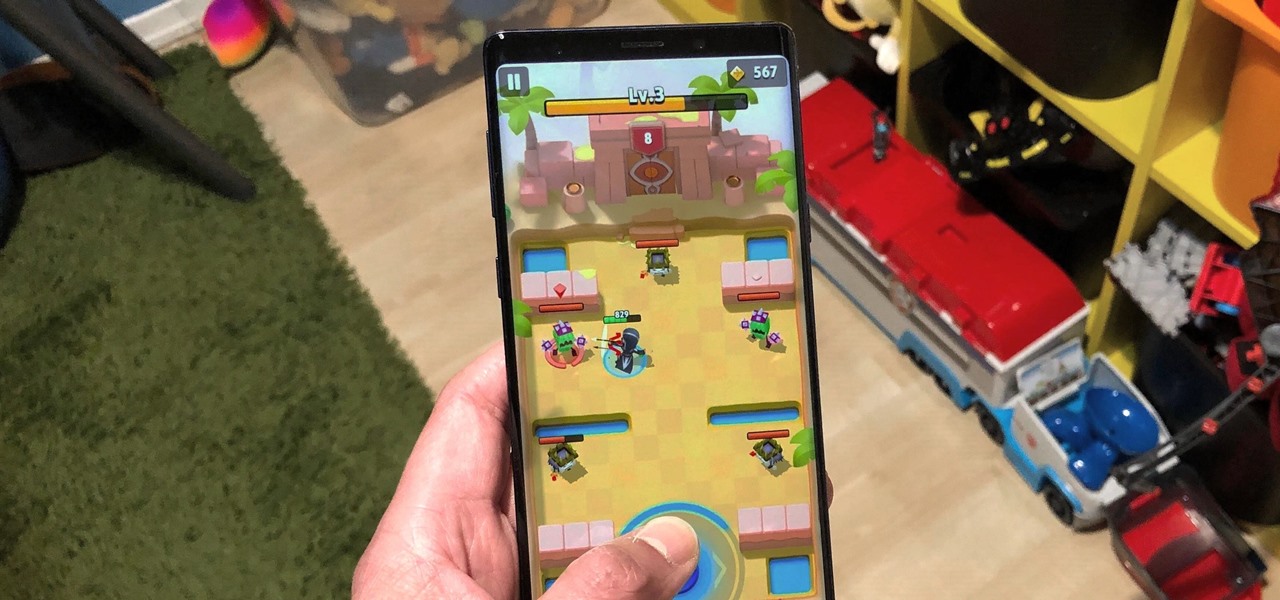
The COVID-19 pandemic has practically shut down all sports except for World Wrestling Entertainment, which has continued staging matches without an audience, leaving us sports fans with nothing much to cheer for. While they can't replace live games, smartphone games provide an alternate reality to live out our competitive entertainment in the absence of the real thing.

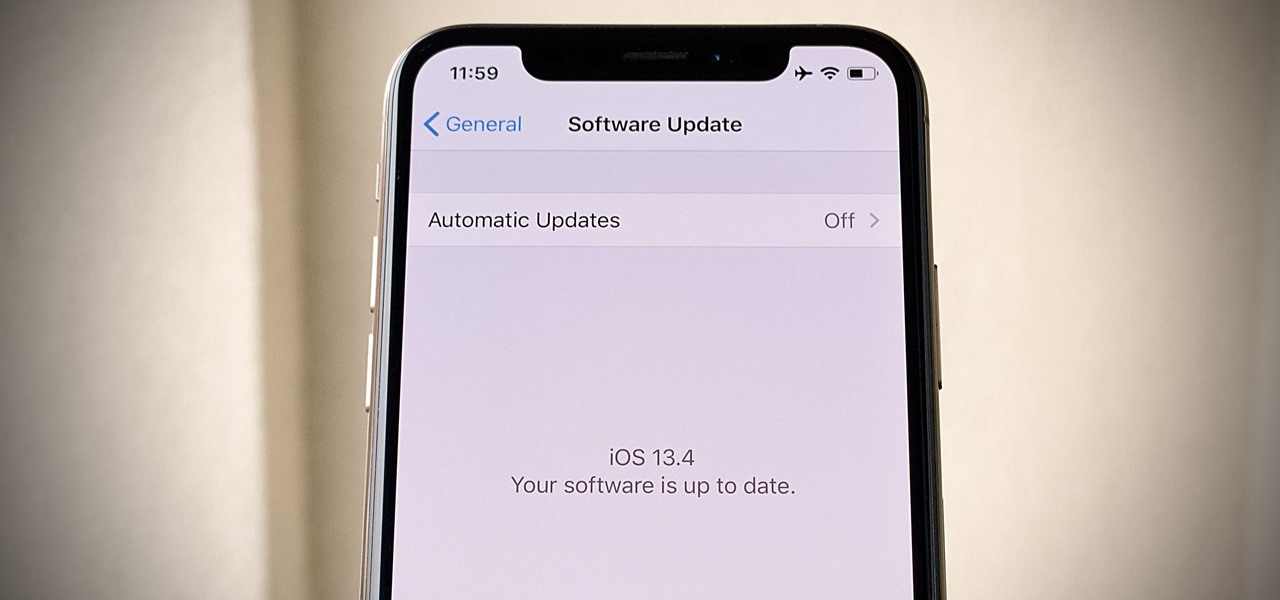
Last week, Apple released the first iOS 13.4 beta with fun and useful new features, such as new Memoji, an upgrade Mail toolbar, and the ability to control your NFC-compatible car via CarKey. To add to that, Apple just released iOS 13.4 developer beta 2, but does the update have any more new changes to be excited about?

Are you thinking about upgrading your iPhone this year? Apple sure wants you to. Of course, that's no different than any other year, but Apple really wants you to upgrade this year. How do we know this? The rumors point to not three, not four, but five brand new iPhones in 2020, with two very different release schedules. All this begs the question what the hell is Apple thinking?

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Continuing our NR30 series this week, we focused on the leaders of the software development industry that make augmented reality experiences possible. In other news, two of the current leaders in making AR headsets, Microsoft and Magic Leap, are pursuing multiple verticals with their products, as both now appear to be interested in making AR headsets for the military.

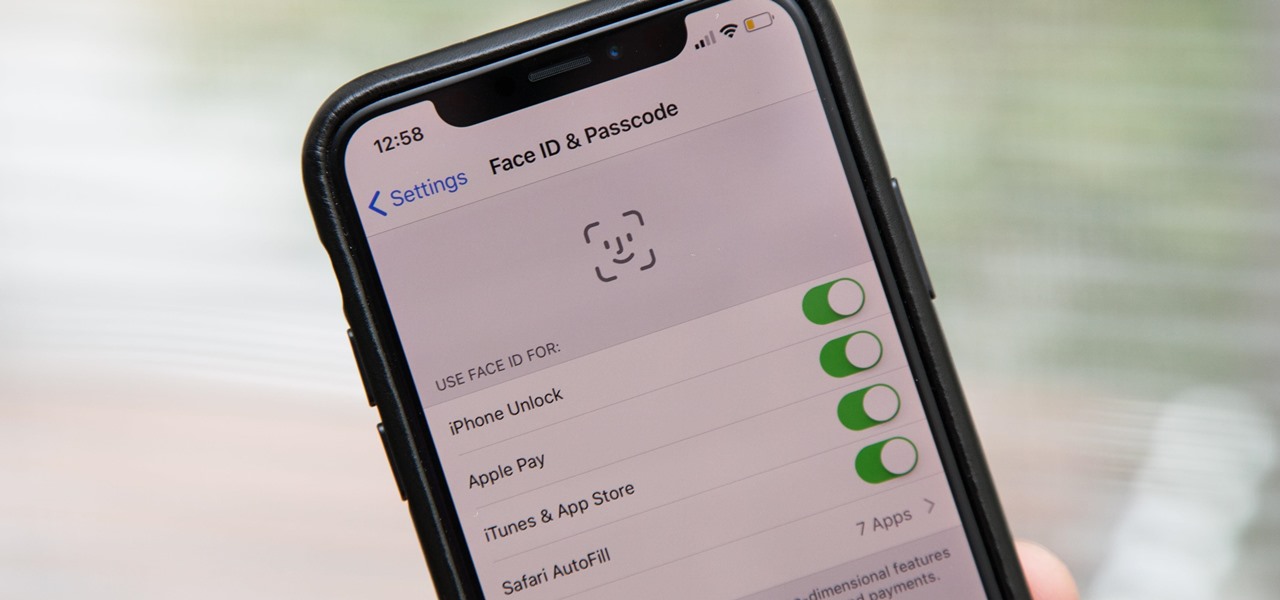
Aside from the second-generation iPhone SE, all new iPhone models since the iPhone X have had Face ID instead of Touch ID as the biometric authentication technology. While Touch ID can be touchy, Face ID is not without its own issues. If you can't get Face ID on your iPhone to recognize your face and unlock your iPhone, there are plenty of things you can try to get it working again.

The Pixel 2 is a solid upgrade when compared to the 2016 model, but we've reached a point where the latest generation of a smartphone is never leaps and bounds better than the last. It's hard to justify dropping nearly a grand on a phone when it doesn't improve your situation much — especially when a few software tweaks will give you most of the upgrade for free.

Cross-compilation allows you to develop for one platform (like Kali) and compile to run on a different platform (such as Windows). For developers, it means that they can work on their platform of choice and compile their code for their target platform. For hackers, it means we can compile exploit code for Windows from Kali.

Running diagnostics on your Android phone can be a very tedious process. More often than not, you need to key in dialer codes to see if your device's hardware is functioning properly, though you can also download apps — but these are often hard to understand for a layperson. When a smaller component like a proximity sensor fails, you're often left with no other choice but to take it to a professional.

Containers are isolated software instances representing applications, servers, and even operating systems—complete with all of their dependencies, libraries configuration files, etc.—and they're taking over the corporate world. The ephemeral, portable nature of containers help them stay current and speedy, and they can work on pretty much any computer, virtual machine, and cloud.

We already know that Samsung's Galaxy S7 is one of the most versatile smartphones ever made, complete with edge-to-edge displays, water resistance, and a huge battery. But what's versatility without durability? How much punishment can the Galaxy S7 take? Let's play a game of Samsung Galaxy S7 Punch-Out!! and see what happens.

Running out of any shower necessity is just a temporary annoyance, but it always seems worse when it's an empty can of shaving cream or gel. Sure, you could dry shave or use whatever liquid toiletry item is in hands reach, but if you want a truly smooth shave without irritation, you'll want to try one of the following alternatives. Some of them might even work better than your can of Barbasol or Skintimate.
Have you ever used an open wifi, which after you connect displays a website to enter your credentials to get internet? That website is called captive portal and widely used in airports, hotels, universities etc. Have you ever wondered what would happen if someone would set up an open wifi with the same name displaying a very similar web page asking for credentials? Usually if there are multiple wifi networks with the same name and encryption, devices only display the one with the highest sign...

Throwing a party means making sure everyone has fun, but that pursuit can quickly get out-of-hand. Before you know it, you're once laid back get-together has received so many RSVPs that it becomes obvious you're throwing the party of the century. With an over-abundance of beer and an inflated guest list, your newly-formed epic reputation must live up to the hype.

Staying healthy is a progressive challenge we all face throughout our lives, and figuring out just how to do that can be a challenge when it's not your job. For doctors, however, it is. Here's how they keep themselves healthy day to day.

It may not be as large as the Samsung Galaxy Note 2, but the Galaxy S3's screen size is still big enough to make iPhone owners cry themselves to sleep. The 4.8-inch AMOLED display with 720 x 1280 pixels makes the GS3 a great mobile companion—and an even better portable gaming device.