
How To: Use the Left, Mid, and find function in Excel 2007
This video demonstrates uses of the left, mid, and find function in Excel 2007 to pull out specific pieces of text from a longer text string.


This video demonstrates uses of the left, mid, and find function in Excel 2007 to pull out specific pieces of text from a longer text string.

YouTube Hack! Youtube now uses a new gdata format and doesn't require a developer key. It also added a whole bunch more variables you can attach to the query string making things possible that weren't before.

Make a prank ketchup bottle that will squirt out string that looks like fake ketchup. Use this as inspiration for one of your April Fools Day pranks!

Learn how to do basic bead stringing with this demonstration on how to make a bracelet.

You don't have to wait until Halloween to get your fill of creepy critters—fold a whole colony of bats and string them into a spooky mobile.

You need wooly nylon string and a candle. This is pretty easy and you can get these things at any fabric store.

So you're getting pretty good now, and if you've been following Justin's progressional tutorials you know your major and minor chords and can strum. Now it's time to learn the dreaded F chord. Don't be alarmed, even though you have to hold down two strings with one finger, it is a very nice chord and leads later to playing barre chords.

Brad Davis explains why he sometimes uses two capos on a guitar. The effect is similar to that of using a drop tuning on the B string. The technique and effect are discussed in detail. He then performs an original tune (demonstrating the use of two capos), "Love You Don't Know".

In order to build a trip wire, you will need the following: a knife, fishing line, a rope/string, sticks, and a large stone.

As per Alex's request, I am posting about generating word-lists in Python. However, this is my FIRST attempt with Python, so please provide me with critiques and any and all comments. I really want to know what you think as there was a little bump here and there seeing as I am transitioning from C#.

For SQL injection, the next step after performing reconnaissance and gathering information about a database is launching an attack. But something seems off .. in the real world, it's usually not quite as simple as passing in a few fragments of SQL code to an input field and seeing all that glorious data displayed right in the browser. This is when more advanced techniques are needed.

Video: . ?The following are 5 practical jokes you can set up on your friends and family, All these pranks involve sodas so make sure you have a few handy if you want to try out these pranks. Just a little warning, 4 out of the 5 pranks showcased in this intractable are pretty messy so prank at your own risk.

Henry Goodelman we commend you, sir. You have stunned and baffled us ... more than any of the other 1000+ submitters to the Jackass 3D Prank Contest.

The city of London is getting a holiday gift this season, but it's not the kind you unwrap, since it's completely delivered in augmented reality.

Cross-site scripting can be one of the easiest vulnerabilities to discover, but to be successful with this type of attack, it is essential to learn how to get past filters. In the previous guide, we explored some ways to do this, such as abusing attributes and event handlers and tricking the application into accepting unusual characters. Now, let's take a look at more techniques used to defeat filters.
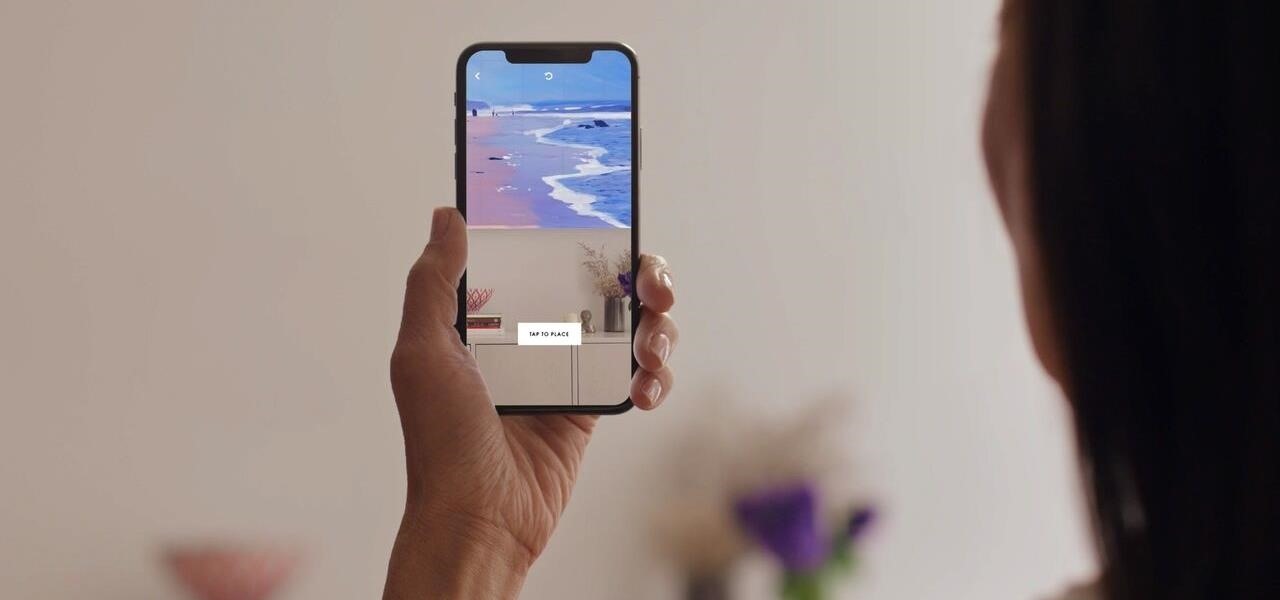
Less than a week after ARKit 1.5 became available to the public through the iOS 11.3 update, the App Store has its first app with AR features (Artsy) to leverage Apple's AR toolkit update.
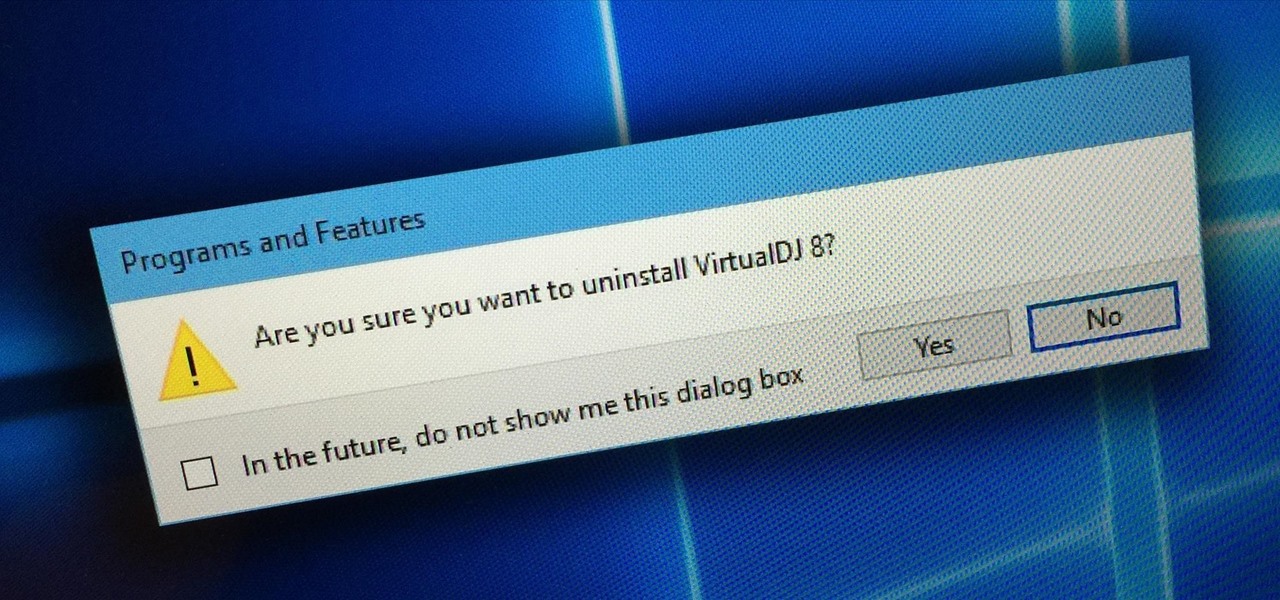
Uninstalling programs in Windows is not the nicest procedure. Some programs bundle a nice uninstaller with them which helps to ease the process. Other programs, mainly those that utilize the Windows Installer technology, begin the uninstall process right away. This can potentially be problematic for users who are trigger-happy with the mouse.

Video: . IF function

Attention jewelry makers! When making your own unique jewelry designs, one must learn how to secure the end crimp beads with crimping or chain-nose pliers. Crimp beads can be used for finishing off your strung jewelry or as "stoppers". In this tutorial, learn how to hone your jewelry-making skills!

In this article, I'll be exploring the basics of Python, i.e. variables, input and output. You'll need Python (2.7+), a computer, and some free time.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

K'NEX is the world's most famous constructive toy, which means you can build just about anything. You can take the K'NEX plastic pieces and build all kinds of contraptions, everything from boats to airplanes to robots to weapons.

Nauto, which develops driver-monitor cameras and algorithms for autonomous vehicles, is among a growing list of driverless startups able to attract tens of millions of dollars in funding after raising $159 million in its latest round of financing.

Welcome back! In the last training session we covered how to write and execute scripts. But today we'll be getting back to the code!

This is my first ever how-to so I apologize in advance for any grammar mistakes or spelling errors. Introduction

Greetings null-bytians. Firstly, I would like to apologize for the no images thing. I guess I can't upload them.

Well, first things firsts, it's been awhile! I'm sorry the series has been dead for a little bit, but I recently hit some personal relationship issues and needed to take some time to think. But, now that it's all said and done, the dust can settle and we can start training again!
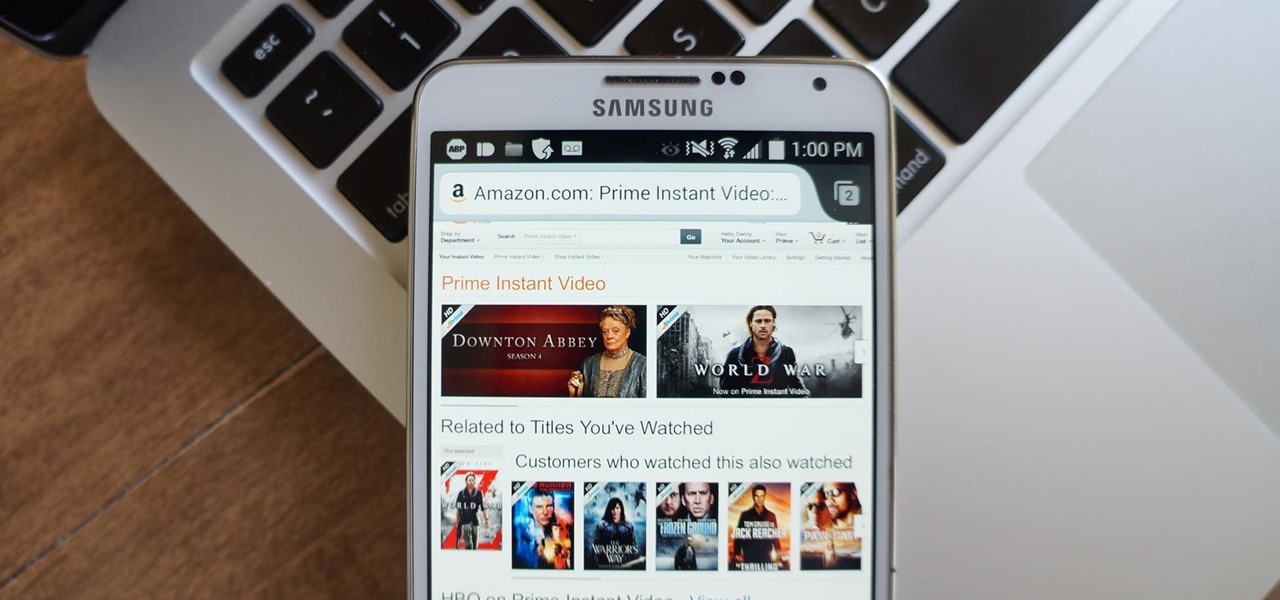
While Google would like you to believe that Flash is incompatible on Android KitKat, there is a functional workaround that will get it up and running on your Samsung Galaxy Note 3's gorgeous screen in no time.

Welcome back, my rookie hackers! The more we know about a system or network, the better our chances of owning it and not leaving a trace for investigators to follow. One of the often overlooked sources for information is the Simple Network Management Protocol (SNMP). Many rookie hackers are not even aware of it, but it can prove to be a treasure trove of information, if you understand how it works and how to hack it.

United Arab Emirates is the cosmopolitan country that offers various attractions for tourists across the world. This country has buildup its image as one the fastest growing country of this region. Besides visiting worth seeing places, travelers can also enjoy tasty traditional food of UAE across the country. Whether you have chosen Dubai, Abu Dhabi, Ajman or Ras Al Khaimah, you will get the chance to enjoy best traditional food everywhere.

You knew it was only a matter of time. China is now producing the iClone, a phone which looks very similar to the famous iPhone. The bonus with this phone is that you have the ability to install Java, and run Java based applications on the device. This tutorial shows you how to download and install Java on your new China phone.

We can bet that the first time you tasted a thick, chocolatey Mississippi mud pie certainly wasn't your last. Made with Paula Deen-approved portions of chocolate chunks, marshmallows, candied pecans, and even more chocoalte, Mississippi mud pie is famous for its utter decadence.

Love Mickey Mouse? Then show your love for the famous Walt Disney character by drawing him. But don't worry, you need not be an artist to make a great Mickey drawing. It's really just a bunch of circles. Follow along with this video to sketch Mickey out the easiest way possible!
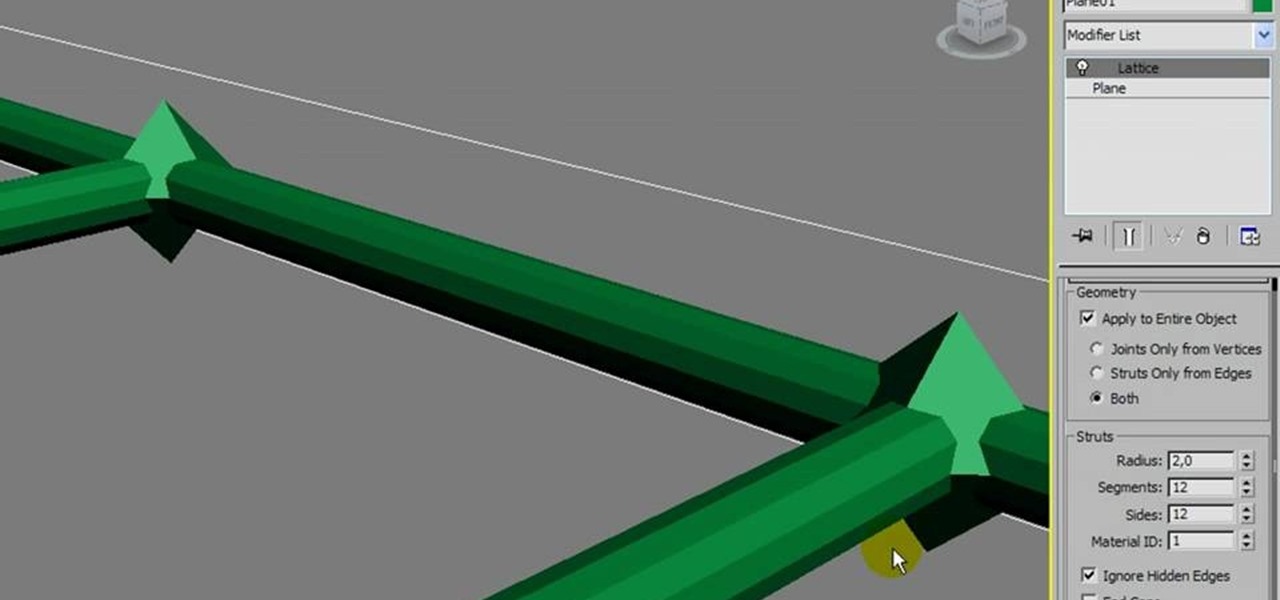
Replicate the famous double helix structure of DNA using the 3-D modeler Autodesk. This tutorial shows you how you can create your own 3-D model of a strand of DNA by applying the lattice modifier and then twisting and coloring it.

Square lashing is a knot-making technique that has been made famous by the Boy Scouts of America's massive pioneering projects, and is really integral to any structure made out of poles like the one you see in the thumbnail. This video will teach you how to use square lashing to bind two poles together perpendicular to one another. You will need to know how to tie a clove hitch to make this work.

What could be more perfect for a summertime barbecue than an All-American flag cake? This sponge cake is easy to make and covered in berries to give it a fresh, warm-weather flavor. If you need a dessert for Memorial Day or the Fourth of July, this is the perfect one for you. Start from scratch with the Food Network's Ina Garten, aka the famous Barefoot Contessa, in this clip.