No matter how many camera improvements a phone adds, you're always better off using manual mode. Known as "Pro Mode" on the Galaxy S20, this feature can remove Samsung's pre- and post-processing from photos, putting you in total control.

Wi-Fi networks come in two flavors: the more common 2.4 GHz used by most routers and IoT devices, and the 5 GHz one offered as an alternative by newer routers. While it can be frustrating to attack a device that moves out of reach to a 5 GHz Wi-Fi network, we can use an Alfa dual-band adapter to hack Wi-Fi devices on either type of network.
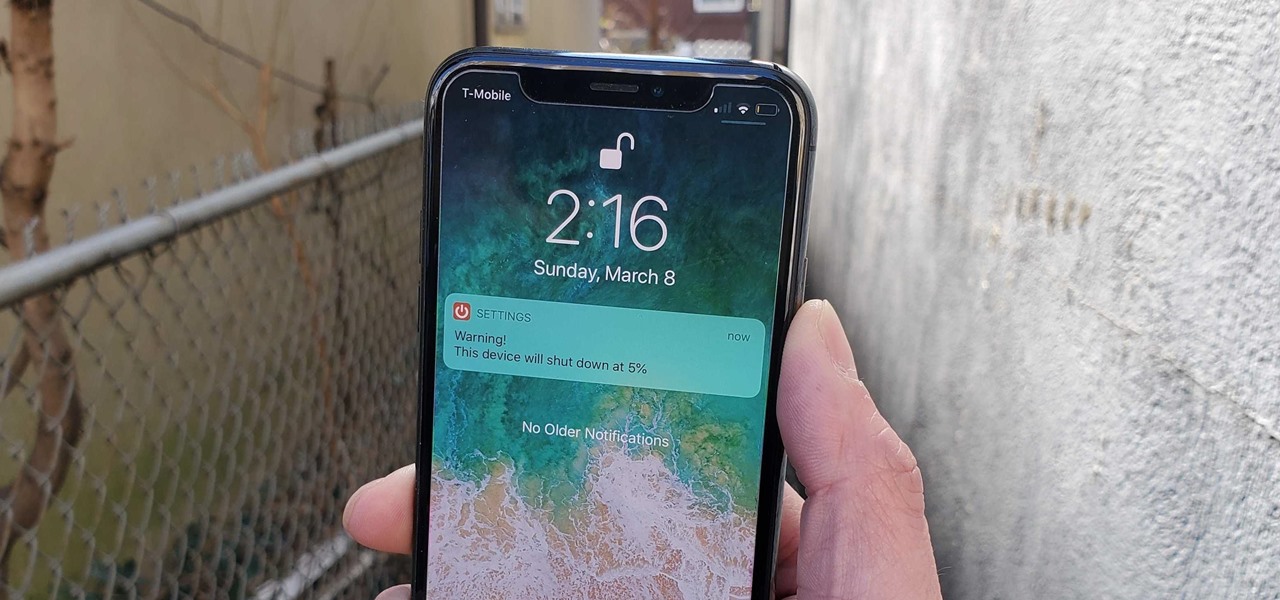
If running out of battery while out and about weren't bad enough, the experience is a lot more painful if your iPhone has a semi-untethered jailbreak. With that kind of jailbreak, when the iPhone dies, all of the mods will be disabled after the device powers back up. Fortunately, instead of restoring your jailbreak and tweaks manually after recovering from a critically low battery, you can avoid it altogether.

Staying inside during the coronavirus pandemic isn't easy for most of us. As important as it is to keep away from others, it can be challenging to keep to ourselves day after day. That's why mobile game developers are stepping in to help; many are making their games free for a limited time, to provide some much-needed fun during scary times.

MIT artificial intelligence researcher Lex Fridman recently asked SpaceX and Tesla founder Elon Musk possibly the best question he's ever been asked: What would he ask a hypothetical AGI system (an AI system with human-level intelligence and understanding) if he only had one question?

The top five apps of the 2010s were all social media apps of some kind, and the fact that's not surprising to you says a lot. We may use them for other reasons here and there, but our phones are social media machines at their cores. The thing is, some make better machines than others.

This week, the beginning of an epic legal battle was set to begin between augmented reality players Magic Leap and Nreal, the small China-based startup accused by the former of stealing trade secrets.

UPDATE: The OnePlus 8 Pro has been released! Check it out on the official OnePlus website or read through the rumored specs we've left below for posterity.

Although the Health app mostly focuses on fitness, Apple has slowly added features to help with other aspects of well-being, including hearing. In iOS 13, there's now a headphones volume tracker in Health that monitors audio levels and lets you know when your music, podcast, movie, or whatever else is too loud.

The year 2019 was filled with all the normal peaks and valleys of the tech business cycle, but this year was particularly important in a space as relatively young as the augmented reality industry.

Post-exploitation information gathering can be a long and drawn-out process, but it is an essential step when trying to pivot or establish advanced persistence. Every hacker should know how to enumerate a target manually, but sometimes it is worth it to automate the process. Metasploit contains post modules that can quickly gather valuable information about a target, saving both time and effort.

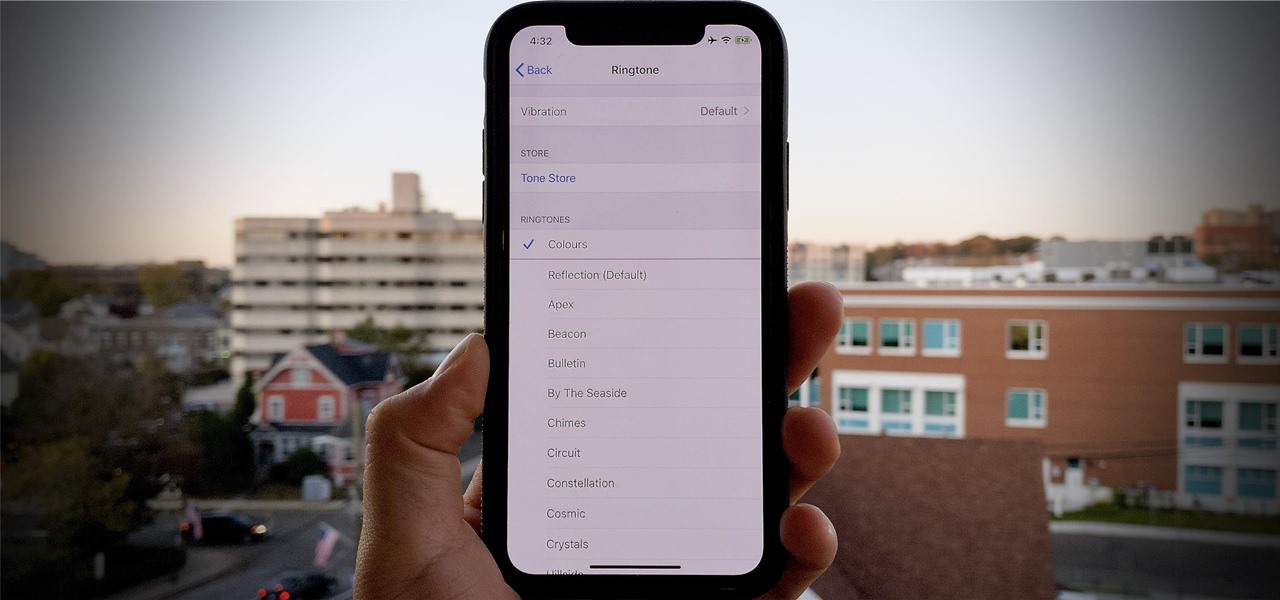
Have you ever heard someone else's iPhone ringing and thought it was yours? Of course you did. iPhone ringtones are iconic, but not varied. If you're using one of the more popular iOS sounds, you'll likely encounter it in the wild multiple times. Why bother, when you can create your own custom ringtones right on your Mac.

Advancements in technology have made it perfectly possible to make a short film or even an entire movie with your iPhone or Android — as long as you've got the right gear. Lenses, stabilizers, tripods, lighting, microphones, chargers, and cases can make the difference between a good movie and a great film, all of which can make a great gift for those aspiring (or current) filmmakers in your life.

If you had a phone in 2004, there's a pretty good chance it was a Motorola RAZR. The iconic phone is the tenth highest-selling of all time, and it marked the height of the flip phone era. Now that the technology has caught up, Lenovo (Motorola's parent company) is bringing it back in a big way.

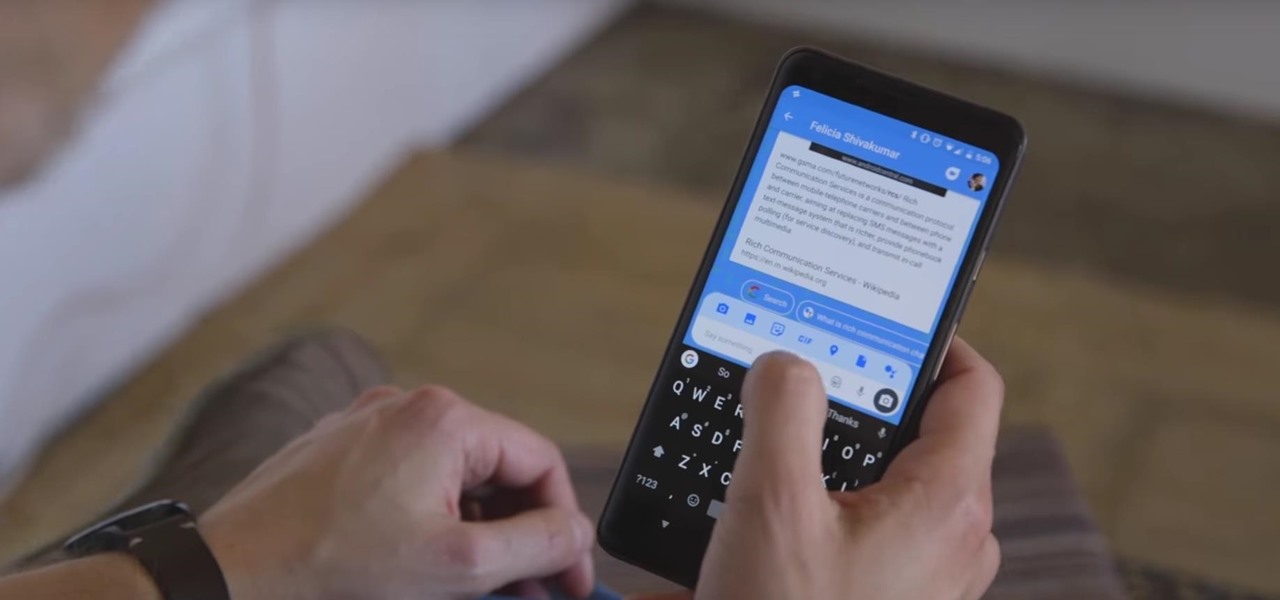
In November 2016, the RCS Universal Profile (Rich Communications Services) was introduced. The technology takes text messaging to the 21st century, emulating many of the features found in IM apps like WhatsApp and iMessage, but working through your phone number like regular SMS or MMS. The only thing is, your carrier needs to support RCS-UP to use the feature. Thankfully, the list is growing.

Google is an incredibly useful database of indexed websites, but querying Google doesn't search for what you type literally. The algorithms behind Google's searches can lead to a lot of irrelevant results. Still, with the right operators, we can be more exact while searching for information that's time-sensitive or difficult to find.

The landscape of the augmented reality space is broad, diverse, and constantly shifting, perhaps more so than any other vertical in technology. At the same time, major players are attempting to standardize various hardware designs and delivery methods, while still others are rushing to claim their piece of virtual property through AR clouds and application stores.

OnePlus, whose phones always challenge for the title of best spec-to-price ratio, releases two main devices every year. There's the primary flagship in late spring, then an iterative update with the "T" suffix in fall. Typically, there's not much difference between the two, but this year, OnePlus is mixing up the formula a bit.

One of the most common web application vulnerabilities is LFI, which allows unauthorized access to sensitive files on the server. Such a common weakness is often safeguarded against, and low-hanging fruit can be defended quite easily. But there are always creative ways to get around these defenses, and we'll be looking at two methods to beat the system and successfully pull off LFI.

When it comes to shooting games, battle royale titles like PUBG and Fortnite have come to dominate the scene, leaving other sub-genres like top-down and third-person shooters living in the shadows. They're far from irrelevant, though, as evidenced by all the great games released just in 2019 alone.

Since the Razer Phone's announcement in 2017, we've seen a new subgroup of phones emerge. Gaming phones are now a thing, leading to companies like ASUS creating phones that are thoroughly optimized for the mobile gaming experience. And with their second iteration, they perfected it.

When I first found out about Nreal, back in the spring of 2018, the most interesting thing about the company's story was the founder's background. Chi Xu, the CEO and founder of Nreal, previously worked at Magic Leap as a software engineer.

Phone numbers often contain clues to the owner's identity and can bring up a lot of data during an OSINT investigation. Starting with a phone number, we can search through a large number of online databases with only a few clicks to discover information about a phone number. It can include the carrier, the owner's name and address, and even connected online accounts.

Motorola is a shell of its former self. In 2010, it had just released the Motorola Droid, a phone so popular it led to all Android phones being called "Droids" by non-techies. But there have been some rough years between then and now, and Motorola's latest "flagship" doesn't look like it will help get them off this path.

While photography usually gets all the love, our phones have gotten really good at capturing video. Think about it — when was the last time you needed a camcorder for a vacation? With mobile cameras getting better each year, we're now at a point where smartphones can be used for pro-level videography.

The year in augmented reality 2019 started with the kind of doom and gloom that usually signals the end of something. Driven in large part by the story we broke in January about the fall of Meta, along with similar flameouts by ODG and Blippar, the virtual shrapnel of AR ventures that took a wrong turn has already marred the landscape of 2019.

When joining a new network, computers use the Address Resolution Protocol to discover the MAC address of other devices on the same network. A hacker can take advantage of ARP messages to silently discover the MAC and IP address of network devices or actively scan the network with spoofed ARP requests.

On Monday, Apple unveiled its Apple Card, the company's boldest move yet toward becoming a truly mainstream mobile payments company. And the product has vast implications for our augmented reality future, some of which may not be immediately obvious to many.

Microsoft Office files can be password-protected in order to prevent tampering and ensure data integrity. But password-protected documents from earlier versions of Office are susceptible to having their hashes extracted with a simple program called office2john. Those extracted hashes can then be cracked using John the Ripper and Hashcat.

Now that the dust has finally settled on Microsoft's big HoloLens 2 announcement, the company is circling back to offer more granular detail on some aspects of the device we still don't know about.

It's easy to forget just how cool face filters are. Augmented reality has come a long way, and apps like Instagram now offer a suite of impressive effects to play with, but some of the best ones aren't easily found. There is a treasure trove of exclusive, custom face filters that are unavailable to the general public, but not at all inaccessible — you just need to know the trick to getting them.

Your social security number, credit card information, and medical history can fall into the wrong hands if you're not careful about how and where you share your data online. If you really care about your data, there are tools and techniques you can utilize to protect yourself from cyberstalkers, advertisers, and hackers in a time when digital lives are a high commodity.

Apple CEO Tim Cook has said that augmented reality (or, AR for short) will "change everything." But what, exactly, is augmented reality?

Update: The LG G8 ThinQ has been announced. You can read all of the official specs at our full article on the new phone.

The ability to stay organized and be resourceful with data gathered from recon is one of the things that separates the true hackers from the script kiddies. Metasploit contains a built-in database that allows for efficient storage of information and the ability to utilize that information to better understand the target, which ultimately leads to more successful exploitation.

The year 2018 was a rough one for Snap, the company behind the Snapchat app and the Spectacles wearable camera device. From executive departures to reports of slowed user growth, the company that once spurned Facebook's multibillion-dollar advances is now facing a moment of truth as it stares down its uncertain future.

Huawei has been in a losing battle with the US government for around ten years, with the last year being the spike of Huawei's problems. Because of US pushback against some Chinese-based smartphone manufacturers due to security concerns, Huawei is hoping to limit its dependency on US-based companies, and recent rumors of Huawei's very own mobile operating system may be the first step.

One of the best ways to improve your skills as a hacker is to learn to combine different avenues of attack to achieve success. What if it were possible to get a victim to connect to our machine and execute a chosen payload on our behalf? This is indeed possible with the almighty Metasploit and the aid of a technique known as command injection.

By now, you've probably already seen Andy Serkis and his performance capture demo for Magic Leap. And sure, marrying motion capture acting and augmented reality sounds compelling, but how does it really work as an experience?

The battle between the Pixels and the iPhones has been heating up over the last few years, and this year's bout is the best one yet, with Google's Pixel 3 taking on Apple's iPhone XS.