Many people find Steampunk problematic for a whole host of reasons, not least of which is the glorification of an era of Western history that featured institutionalized slavery, racism, sexism, elitism, and many more -isms.
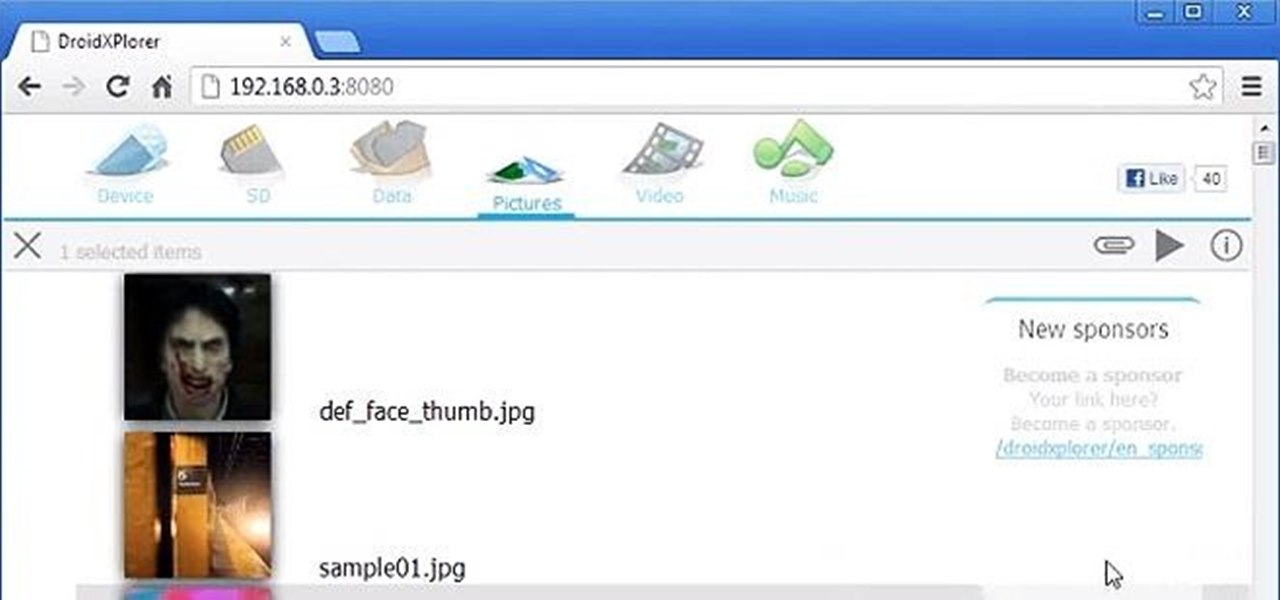
Want to search through your Samsung Galaxy S III or other Android smartphone using only a web browser? Thanks to XDA-Developers member Metal Droid, you can now access and download anything from your phone through any browser on your computer using DroidXPlorer.

I've tried my hand in the past at defining Steampunk, but as anyone else who has made a similar attempt will tell you, there's a significant backlash from the community against working to create a real definition of what Steampunk is. That may sound ridiculous to some, but it's a very serious matter to others. With the recent announcement that TeslaCon 4 will be called the Congress of Steam, I think it's appropriate to talk about why all of this stuff is worth it. In this article, I'm going t...

Here's a video on how to deal with pedestrian crossings in England. It's to help all of you taking driving lessons in Nottingham and the surrounding area, and can be used before or in-between your training.
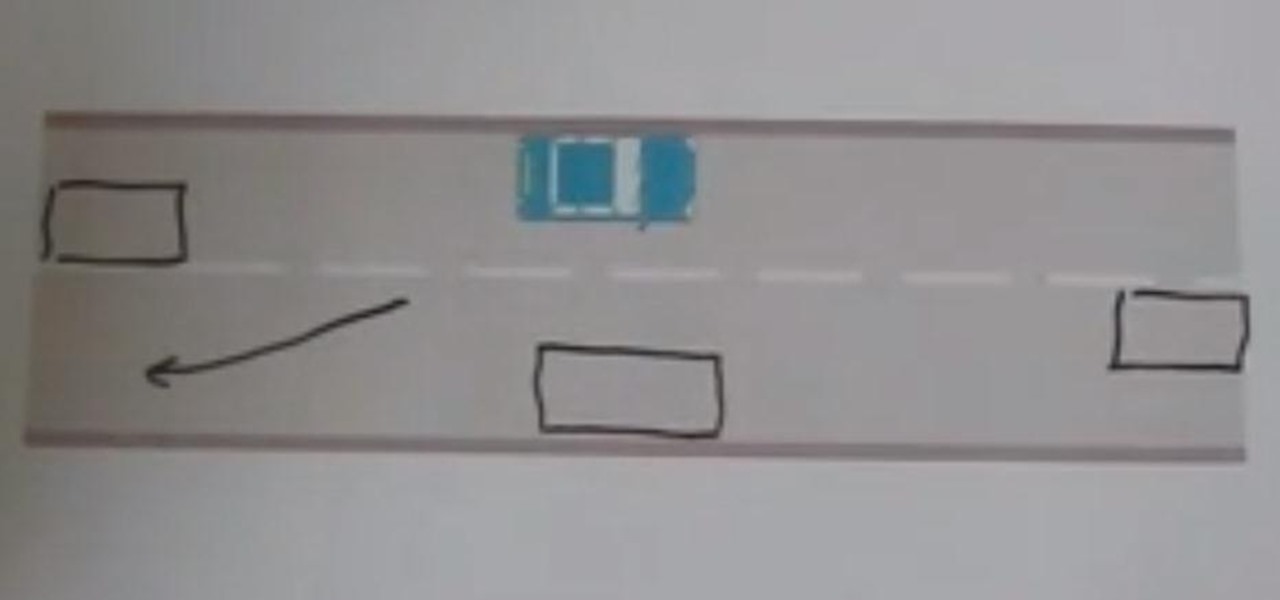
Here is a video all about meeting other vehicles when you're having lessons with driving instructors in Nottingham and the surrounding area. It happens when you are passing parked cars and someone is coming the other way.

Toasters can do so much more than toast bread. A toaster oven can make your Halloween jack-o'-lanterns look pretty creepy, and you can even mod one into a reflow oven. But what about a regular ol' toaster? Well, you can turn one into a working NES console—or you can keep its bread-toasting functionality by just making it look cooler, like Instructables user lemonie did with his VHS player toaster mod.

Want the convenience of a throwaway email address without all the hassle? How about anonymous text messaging so you can get to know someone before giving them your real information? Gliph has you covered. Gliph is a service that lets you create an identity around a set of three to five symbols called "artifacts" instead of your name, phone number, or email address. You choose how much information you reveal, and anytime you communicate with someone else who has Gliph, the data is protected us...

If you want to send someone secret messages you have come to the right place. This is a way in which you can send secret messages to anyone without even making them get a clue that you have sent a secret message.

A clever driver from Cairo, Egypt has revolutionized parallel parking with a fifth wheel built into his car. The extra wheel in the rear is perpendicular to the others and under the trunk (which looks like it's actually stored in the trunk compartment), and can be raised and lowered for easy parking in tight spots. You can even ditch that old, rusty tire jack and swap out a rear flat tire in record time.

Spammers are the bane of every email user. No matter what you do, junk mail always breaks through the spam filters. And some of the best ones seem to come from legit companies, and that's because they aren't legit companies— they're spammers masquerading as legit companies.

Is someone more interested in you than you are in them? Can't get them to go away or take the hint? Don't worry, this tutorial is here to help with tips and tricks for how to get that unwanted suitor out of your hair and avoid a remake of "Fatal Attraction".

No need to make a bad situation worse when running into an ex boyfriend or girlfriend. There is no need to be petty or spiteful when keeping to a nice yet vague conversation will ultimately leave you looking like a real class act.

Here's a low-key way to take advantage of someone's trust. Gain access to a friend or frenemy's iPhone and add curse words as separate new contacts to their contacts page. Sit back and wait for your friend to text someone. Enjoy.

This lesson teaches you how to ask someone to dance, to dinner or to go out with you in Mandarin Chinese. Impress that special person by asking them out in Mandarin Chinese. This lesson is great for a beginning Mandarin Chinese student or someone visiting China.

Who had Lil Nas X, blood-drop Nikes, and satan worship on your 2021 bingo card? In a story that's stranger than fiction, the "Old Town Road" rapper has ruffled some feathers with the video for his new single, "MONTERO (Call Me By Your Name)" filled with demonic imagery usually reserved for death metal bands.

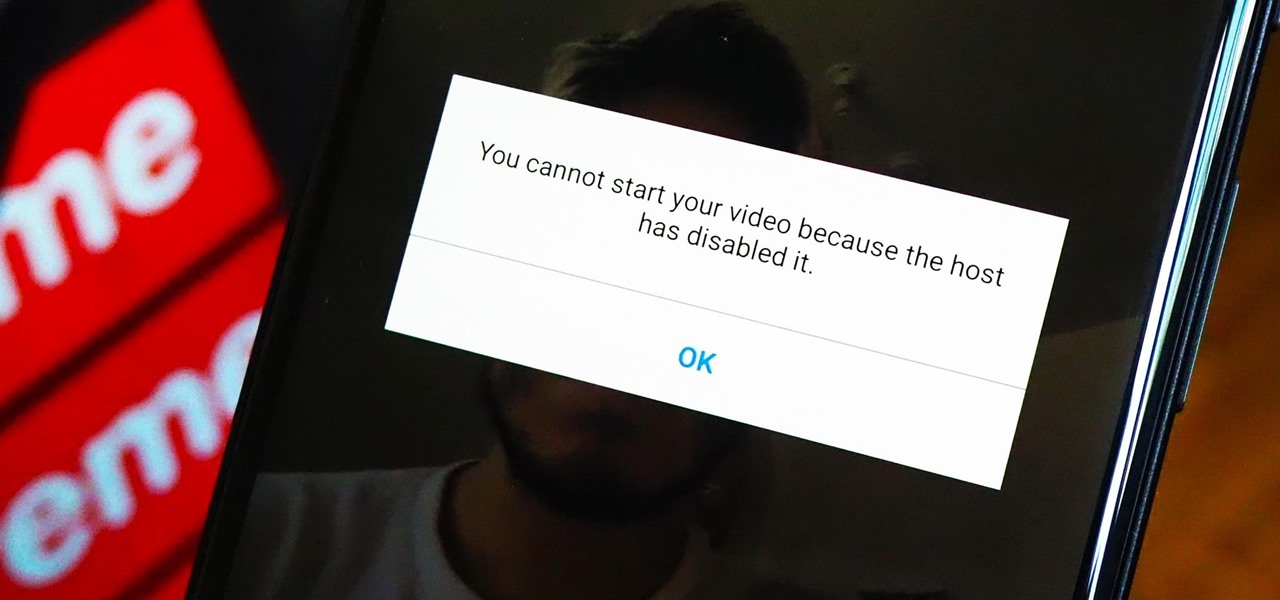
As a meeting host on Zoom, you can't control what a participant does during your live video call, but you do have the power to turn off their camera so that other people aren't subjected to distractions. So if you catch someone in your call purposely making obscene gestures or accidentally exposing themselves while using the bathroom, you can block their camera, as long as you know how.

When you're stuck working or learning from home, video meetings can help you stay connected to employers, coworkers, schools, students, and more. And Zoom is the hottest video conferencing service at the moment. While Zoom is easy to use, it does have a fair share of sketchy features you should know about, such as attendee attention tracking.

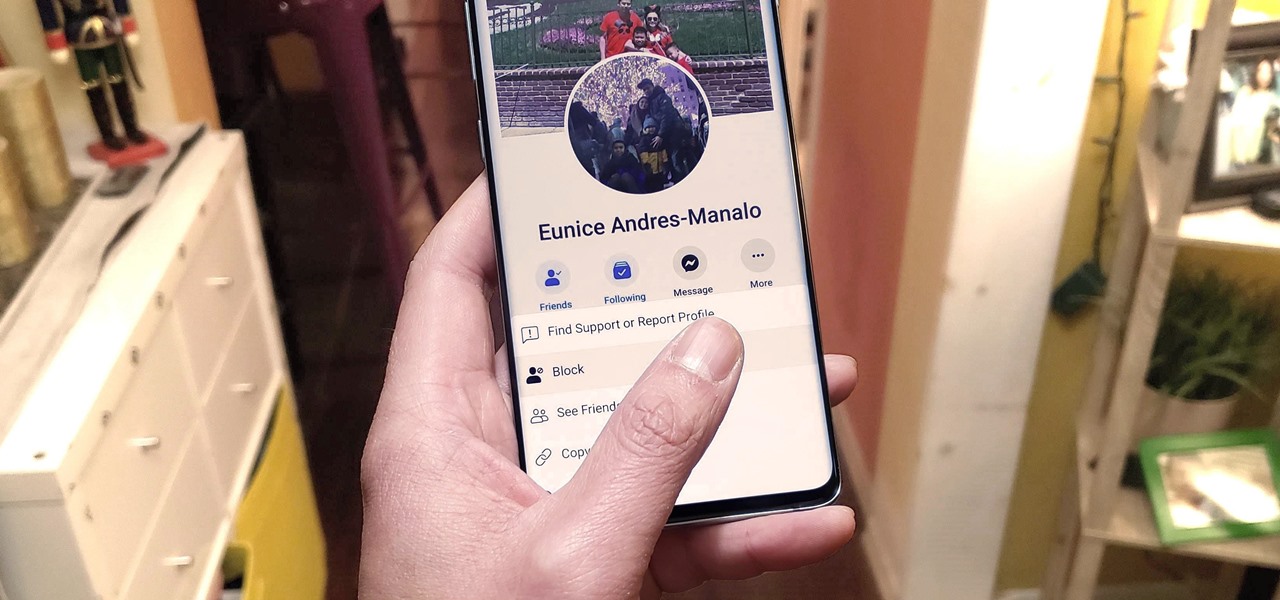
It's easy to block a person or a website from appearing in your Facebook feed, but it isn't as easy to undo that. Thankfully, there are still ways to unblock people directly from your phone.

If you're concerned about someone accessing your OneDrive files, you may want to upgrade your protection by enabling fingerprint or Face ID unlocking. Your sensitive information deserves to be protected, and now you can do so easily. Worry no longer — if you need to let someone else use your phone, with a password-protected OneDrive, sneaky file grabbers will be out of luck.

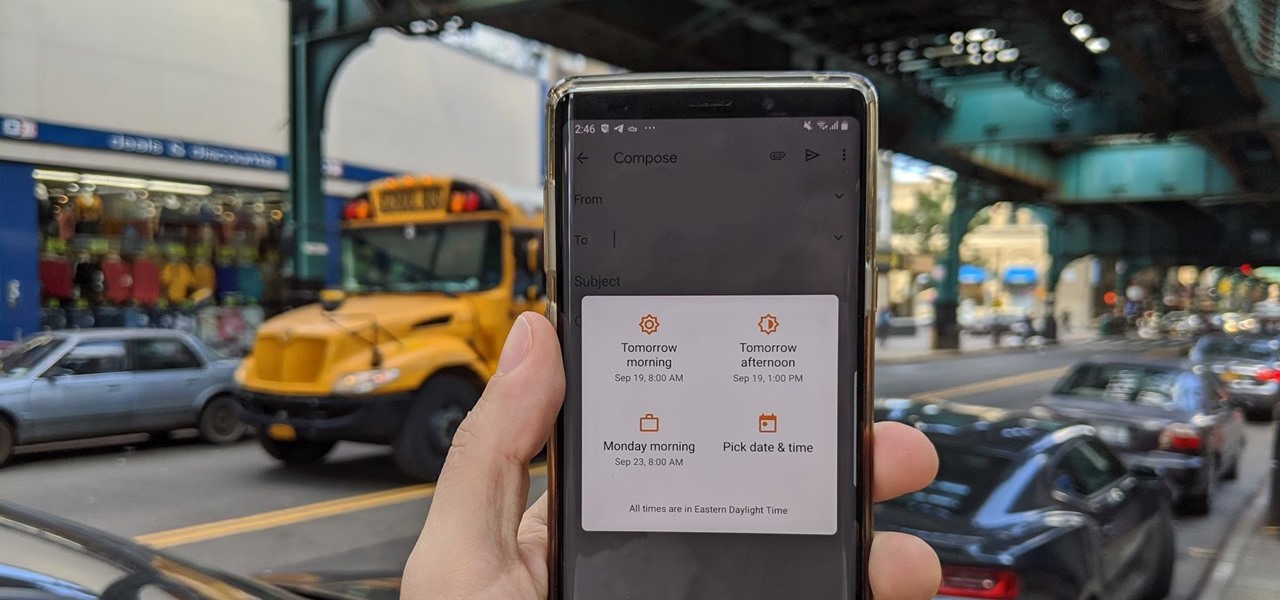
There is power in the detail. Sending an email at a specific time can give you an edge. Depending on what you are doing, it can help your email get read or it can put you at the top of someone's inbox. With the Gmail app for Android and iOS, you can now schedule your messages to maximize the efficiency of your email.

Featured on MTV's Catfish TV series, in season 7, episode 8, Grabify is a tracking link generator that makes it easy to catch an online catfish in a lie. With the ability to identify the IP address, location, make, and model of any device that opens on a cleverly disguised tracking link, Grabify can even identify information leaked from behind a VPN.

So, you accidentally sent a voice message to someone in an Instagram DM. Maybe it contains an unflattering conversation about the recipient. Maybe it's a record of something embarrassing you said. Whatever your message contains, it's out there, on someone else's smartphone. You might think you're out of luck, and that your life is over. If you act quick, however, it won't be.

When you've had enough of someone's annoying baby videos or cat photos on Instagram, you would have to either unfollow them or even block them outright. Now, you don't have to cut ties with them completely — you can just mute them instead, a feature that Instagram's parent company, Facebook, has allowed on its platform for some time.

We already know that the connection between virtual and augmented reality is pretty tight, with tools like Unity making porting some apps between the two platforms fairly frictionless. But there are some things currently going in VR that just don't need to come to the world of AR.

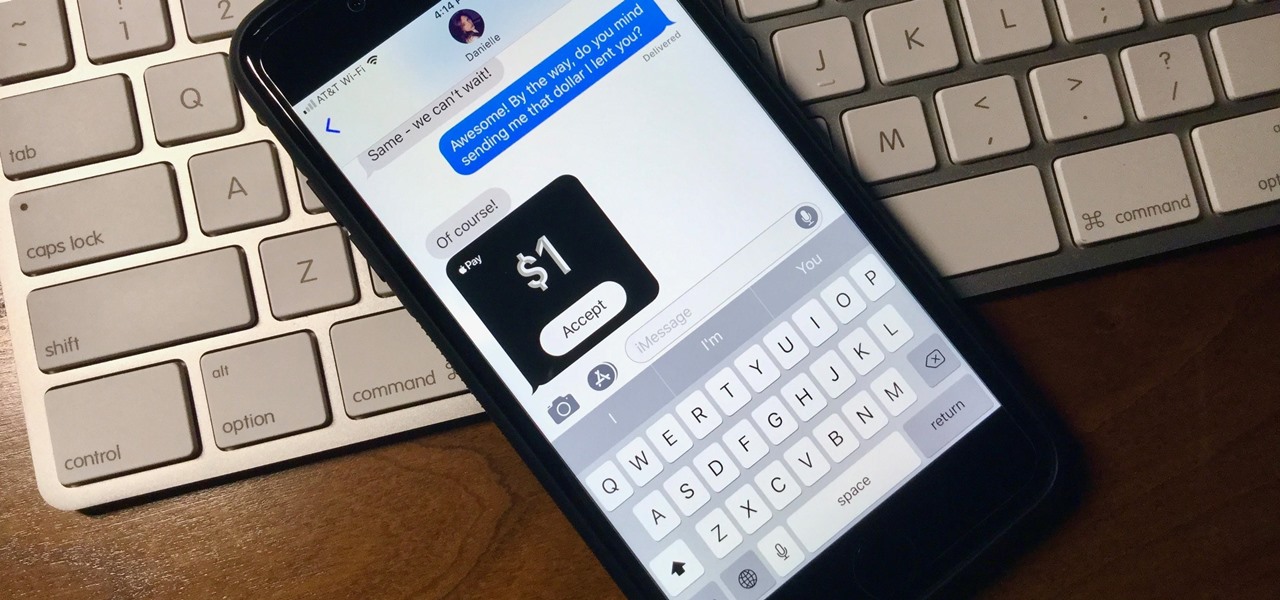
What happens when somebody sends you Apple Pay Cash inside of an iMessage? Do you have to add it to your Apple Pay Cash card on your iPhone manually or does it miraculously appear there automatically?

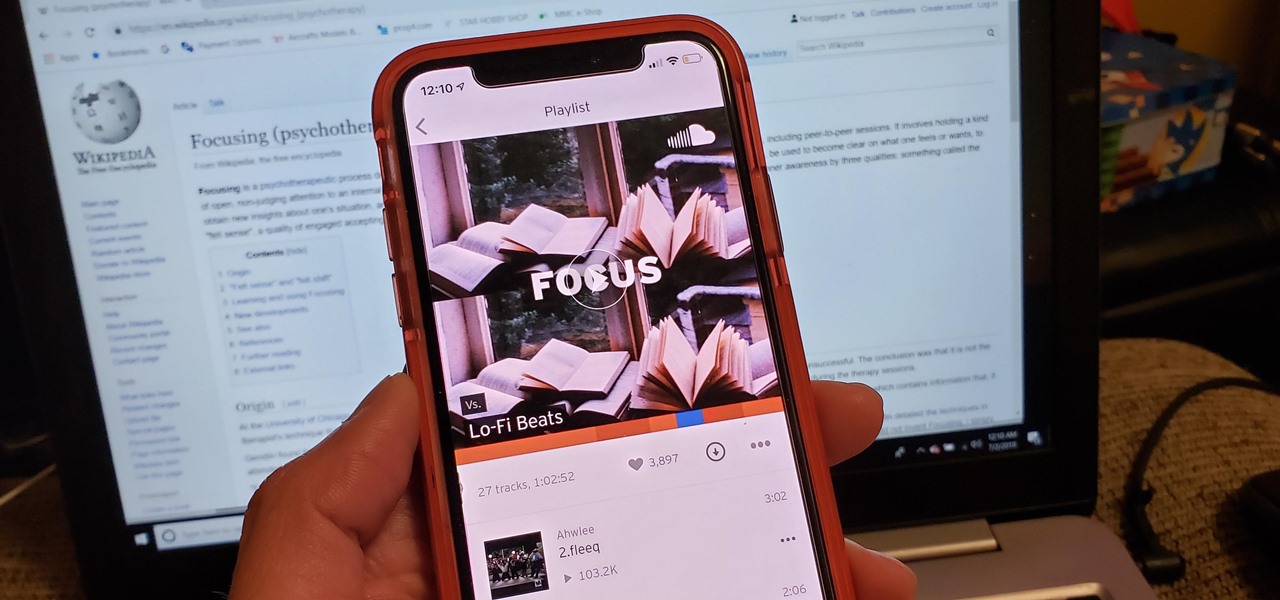
Within the last week, there have been at least three times when someone asked me to play a good playlist. This is always a tough call. What if I play something that nobody likes? I probably will.

M — Facebook's AI-powered assistant unveiled to the public in April — is now better than ever. The latest update to M now allows it to provide three more suggestions: a function to save content to view later, birthday wishes, and call initiation.

More details about Google's latest Taimen device have been revealed all thanks to Geekbench. We already know that Google has been working on a tablet-like third device next to its original Pixel 2 lineup. Though, Taimen is not confirmed to be part of the Pixel 2 lineup.

Paris, girl, you are awesome, but you did not invent the selfie. If you want to spread this #newmarketingterm to the media masses, then go right ahead. It's your brand, your career, and you got the opportunity. People will listen. No one really cares about who invented the silly thing anyway. Though I got to say, the original king of the selfie did seem like one pretty chill dude ...

We're all passionate about something. Maybe it's the environment. Stopping poverty. Finding the best taco joint ... Whatever your cause, the last thing we want is to support companies whose practices go against what we believe. After all, you can't trust someone who doesn't like tacos. So it can be difficult to know which companies to avoid; there are just too many doing too many shady things to keep track of. Until ...

Baidu Inc, the "Chinese Google" search engine and technology company, which has been actively pursuing self-driving cars, reported that a gang of hackers recently attempted to steal its driverless car technology.

We live in a marvelous age, a time where technology is driving us forward as a species at a rapid pace, and tech-driven miracles are becoming more and more commonplace. While the human race may not be focused on building the largest wonders of the world, as it once was in history, the current order of wonders are much smaller in scale—even internal.

Today, December 7, it was officially announced that Magic Leap has found their replacement for the recently departed Brian Wallace. Magic Leap CEO Rony Abovitz has tapped Brenda Freeman, former EVP and Chief Marketing Officer of National Geographic Channel, as their new Chief Marketing Officer.

Many new developers are diving right into the Microsoft HoloLens, but augmented and mixed reality are fairly big subjects in terms of learning. There's a lot to cover and, unfortunately, very few places for someone brand new to Windows Holographic to begin lessons.

If you follow tech, you're probably familiar with Siri, Apple's personal voice assistant, which has been integrated heavily into iOS ever since iOS 5. But you might not have known that Siri is capable of performing some tasks when the iPhone is in a locked state. The default state of iOS is to allow access to Siri from the lock screen, most likely for the convenience of hands-free access to the phone.

It's a given that if you're driving, you or someone you know has Waze as a go-to on their smartphone. The Google-owned crowdsourced navigation app is one of the best for avoiding traffic, roadblocks, and even cops.

In this video I'm going to teach you 5 pranks you can get away with at school or at home On April 1st.

Video: . The following are 5 Simple household pranks you can pull off on friends and family this upcoming April Fools' Day! All the material needed you already have at home so lets get started! Check out the video tutorial for further instruction.

This is not essentially the next part in the series, but an expansion of previous part about why should you not use cryptocurrencies.

In this how-to we will be sending an email with an image we get from a php script after running some fishy code. What you'll need