Sharks. The first thing that comes to mind is "Jaws", Steven Spielberg's horrifying shark film that scared generations of young adults from entering the ocean waters. But not all sharks are as violent (and hungry) as "Jaws", so jump in the water and know a few guidelines to stay safe. Escape a shark’s jaws of death with these lifesaving strategies.

Speeding tickets are one of the worst things a driver fears on the highway, aside from wrecking, of course. But you can get home safe without getting a ticket. You just need to keep your vehicle off the radar by following these stealthy driving techniques.

Neck pain can be the worst. Be aware of daily habits that may be causing your chronic neck pain and replace them with healthy choices. In this tutorial, learn how to soothe chronic neck pain.

Accidents are the worst. They're costly, time consuming and an all around pain in the butt. Rear-end collisions are among the most common types of accidents on the road. Take these simple precautions to avoid a rear-end collision.
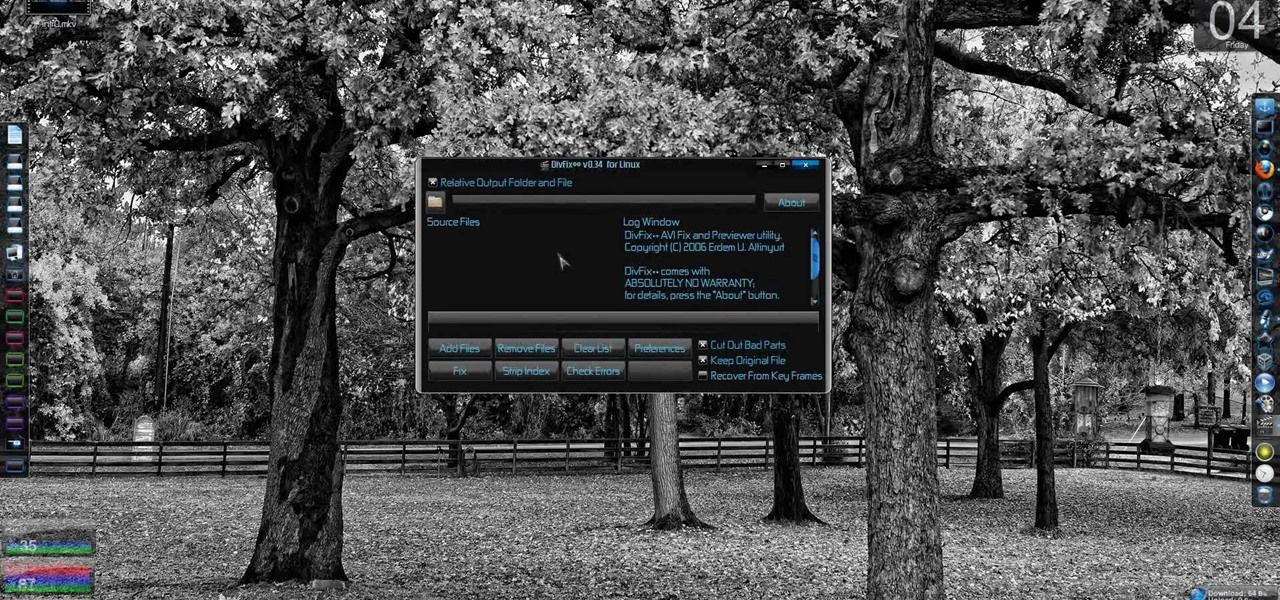
Broken AVI video files are your worst nightmare. Nobody wants to watch a video and find out it's corrupted and not working anymore. But there could be a solution on Linux. This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to fix broken AVI files with DivFix++ on Ubuntu Linux.

It's not too uncommon for your basement to become extraordinarily messy, as that is where unused items tend to migate.

Mononucleosis, an infection caused by the Epstein-Barr virus, can strike anyone, but those who experience the worst symptoms are teenagers. Follow these simple steps to avoid getting this virus.

You've drafted a promising team, and the season's under way. Now increase your chances of making the playoffs.

Feeling unprepared for the next earthquake? In this tutorial, learn what to do and what not to do to survive "the big one". You'll be surprised to learn that hiding in a doorway is a myth!

Are you a lawyer who's married to a computer programmer? Chances are you might not have even dated if you first met online.

Glue is one of the worst things that you can get on your clothes. It sticks to most things and fabric is no exception. Watch this video to learn how to get glue stains out of any type of clothing.

This is my first tutorial and it is about accessing deep web for total beginner,sorry in advance if I make any mistake plz forgive me.

Worried about a hard drive failure? Or a virus that destroys your operating system? Well, don't worry… Windows 7 lets you backup and restore your Windows 7 operating system and all of the files and folders you choose.

FoodWishes will show you how to make an apple swan with this short little video. This project is simple and quick.

This how to video is overview of the same mode played in different positions on the harmonica. As you can hear there are better positions for the tune "Help Me" than other positions. For example the C harp in 4th sounds the worst because of the unstable root. Even though this tune is traditionally played in 2nd position (cross harp) I prefer to play it on a G harp in 3rd position because I think it offers more sonic options due to it's naturally occurring Dorian mode.

Microsoft decided to give users a free upgrade to Windows 10 if they were previously running Windows 7 or 8—but it came with a catch. Their main motivation for knocking off over $100 from the normal going rate was to get more people using new Microsoft services like Cortana and the Windows Store. To bolster these services, Microsoft implemented a host of new tracking "features" in Windows 10.

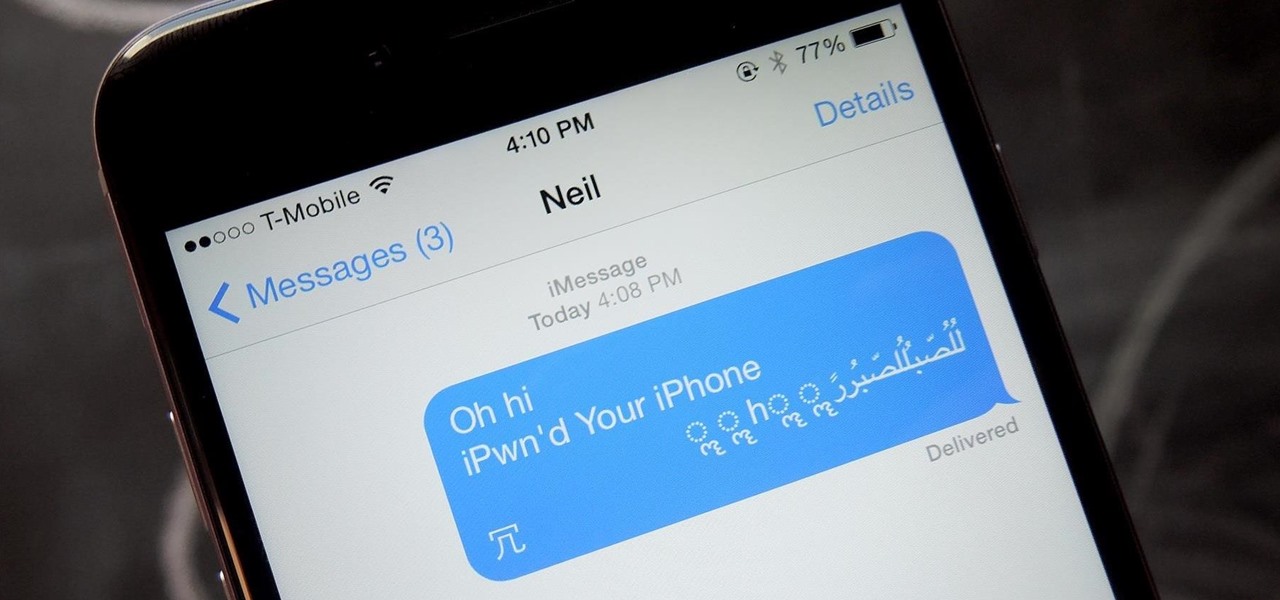
Thanks to a newly discovered iOS exploit, a text message can now ruin your day. It will literally cripple your iPhone, and the worst thing is that anyone with a phone that supports double-byte unicode can do it to you. While it initially sounded like bullshit, we tried it out several times here, and to our surprise, it worked perfectly each time.

The worst thing to clean up is a broken egg on the floor, it's not only smelly but gooey too. Here's a really fun booby trap you can pull off at home using an egg, it will require the use of 2 magnets and a paper cup like the ones you get a your local fast food joint.

One of the worst messes to clean up is raw eggs, well use that to annoy anyone you want by setting up this practical joke.

While AT&T and Verizon may not have had a chance to screw Note 2 owners with unrootbale devices—mainly because they've screwed us over by not issuing KitKat updates—it's safe to say that they can in the future. And while Sprint and T-Mobile subscribers have been able to root, the various methods can make the process somewhat confusing, especially for first-timers.

Watch this instructional video to learn how to do the hummingbird card trick. This is possibly the worst magic trick I have ever seen. It's easy to do as well as easy to figure out.

Electronics seem to fail on you at the worst moments, don't they? Luckily, if your iPod freezes, there is a quick and easy fix. Check out this video and learn how to reboot your iPod on the spot and solve many issues.

Shake to undo is now the worst way to take back what you just typed on your iPhone. Among the many changes in iOS 13, Apple has updated text gestures, including how you select a word, sentence, and paragraph, copy and paste text, and undo and redo what you type.

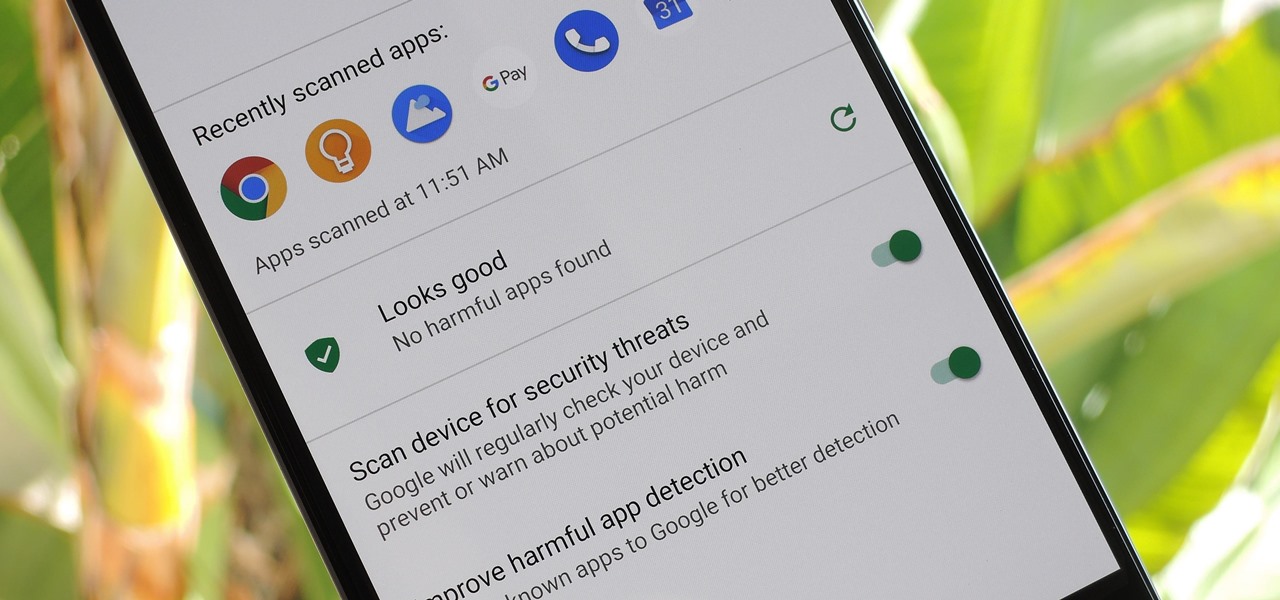
According to Google's new Android ecosystem transparency report, you're eleven times more likely to be infected by malware if you're running Android Lollipop (5.0) as opposed to Android Pie (9). The same report shows that if you sideload apps, you're almost seven times more likely to be infected than if you stick to Google Play as your app source. All of the data provided in the report is quite interesting, but there's a clear pattern among malware-infected users.

Assuming that you're not going to knit a sweater and celebrate New Year's Eve with Ryan Seacrest and Jenny McCarthy on ABC's “New Year's Rockin' Eve," it's a pretty safe bet to say that you're probably going to consume alcohol—a considerable amount of alcohol.

You know that sinking feeling you get when know you've just done the unthinkable? It's the worst. Sending that ridiculous text message to the wrong number or posting a shameful tweet during a weekend bender.

Greetings, fellow NBers! Welcome to my sixth iteration of my sorting series. Today, we'll be discussing a personal favorite: Quicksort, or Quick Sort.

Whether you have the original Nexus 7, or the 2013 Nexus 7 tablet, rooting it will give you access to tomorrow's features, today.

Bokeh (which translates to "blur" in Japanese) is a photography technique referring to the blurred areas of a photograph. Basic bokeh photographs often have one point of focus, while the background falls away into a dreamy, blurred haze.

In last week's guide, we covered the best places to purchase digital copies of computer games online. This week we'll cover another type of downloadable content: those available for video game consoles. Every major console out today either has or plans to have a DLC platform, but which one is the best? If you don't like leaving your house and want to play console video games, which console should you get? Below I will break down what the online marketplace offers so you can decide which conso...

Many online users worry about their accounts being breached by some master hacker, but the more likely scenario is falling victim to a bot written to use leaked passwords in data breaches from companies like LinkedIn, MySpace, and Tumblr. For instance, a tool called H8mail can search through over 1 billion leaked credentials to discover passwords that might still be in use today.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Just because you have a Mac doesn't mean you can't root your Nexus 7 tablet. In fact, rooting Android 4.4 KitKat on both the 2013 and original 2012 N7 models is easy, if not easier than rooting it using a Windows PC.

Will the predicted apocalyptic date—December 21st, 2012—really be the end of the world? In this ongoing five-part series, we examine what would happen if zombies, nuclear weapons, cyber wars, earthquakes, or aliens actually destroyed our planet—and how you might survive.

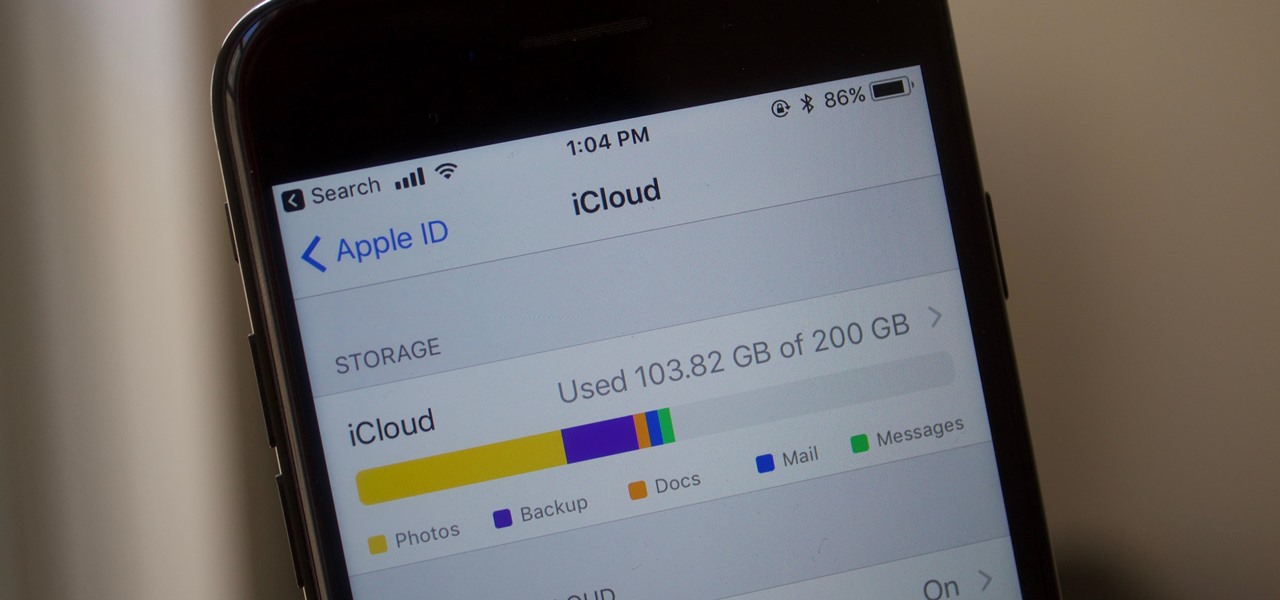
iCloud can occasionally be the worst part of being an Apple user. It's useful for backing up your information, however, sometimes the problems that stem from Apple's cloud service are so tremendously frustrating they almost seem intentional. Well, buckle in, because it's possible there may be a widespread login issue.

Ah, the Nokia Lumia series... what can be said about Microsoft's recently-deceased line of smartphones? They might not have been the best, but they certainly weren't the worst, and they did get the job done in terms of what you would expect from a smartphone.

Do I really need to tell you that it's a bad idea to play Pokémon GO while you're driving? I really hope it's not necessary, but just in case it is, here you go: It's a bad idea to play Pokémon GO while you're driving.

The Weather Channel, by virtue of its name, has always been tasked with the difficult problem of making the weather interesting. As Mashable notes, they've turned to augmented reality for a solution and can now render a 3D storm in their studio, as well as help us understand how bad a storm might be with 3D forecasts.

More proof is emerging that the iPhone 7 won't include a 3.5 mm headphone jack, and damn—it is not pretty. These third-party Lightning-to-3.5 mm dongles were spotted on Chinese site Tama, and they give us a glimpse into a horrifying future in which we have to attach one of these clunky monstrosities to an iPhone just to connect a set of standard headphones.