It's not the bacteria itself that takes lives and limbs during invasive flesh-eating bacteria infections. It's the toxins secreted by the group A Streptococcus bacteria invading the body that causes the most damage.

Bats are an important part of the US economy. They devour metric tons of bugs every night that would otherwise ravage crops and also be generally disgusting-looking and make you itchy. But they're in danger from a nasty fungal infection called white-nose syndrome, which has just popped up in Texas and has been spreading across the country.

A rose by any other name may smell as sweet, but one annoying invasive weed may hold the answer to treating the superbug MRSA. Researchers from Emory University have found that the red berries of the Brazilian peppertree contain a compound that turns off a gene vital to the drug-resistance process.

Every year, 100-200 people in the US contract leptospirosis, but usually 50% of the cases occur in Hawaii where outdoor adventurers are exposed to Leptospira bacteria found in freshwater ponds, waterfalls, streams, and mud. That's why it's so alarming that two people in the Bronx have been diagnosed with the disease and a 30-year-old man has died from it.

A recent pathogen outbreak in Illinois is just one of many outbreaks of an underappreciated, but serious, viral infection passed from rodents to humans. These hantaviruses have been cropping up more frequently in the last decade or so, giving us more reason to clean out our dusty attics, basements, and garages.
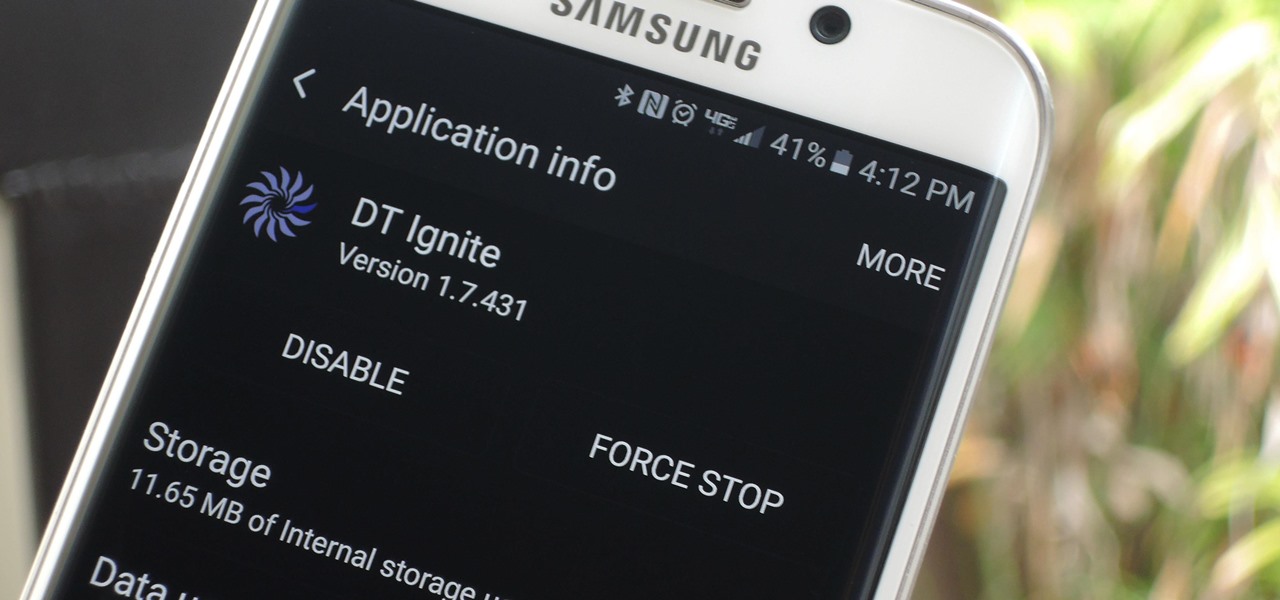
A few months ago, it was discovered that Verizon was installing an extremely shady app called "DT Ignite" on some of its smartphones—most notably, the Galaxy S7 and S7 Edge. The app, created by Digital Turbine, monitors your smartphone usage, then uses the data it collects to silently install "recommended" apps without notifying you.

When it comes to busted smartphones, liquid damage ranks right up there with shattered screens as one of the most common issues owners have to deal with—as well as the most embarrassing. Thankfully, though, with the rise of waterproof phones such as the Samsung Galaxy S7 and even the iPhone 7, this is becoming less and less of a worry. But not everyone has a waterproof device.

Pumpkin pie is a symbol of autumn, and it's the traditional dessert to whip up for your fam when Thanksgiving Day arrives. But year after year of the same old thing can be a total bore if you're not a strict traditionalist. So, we found 8 unique ways to make that pie a little less snooze-fest and a little more interesting.

To some people, Thanksgiving is merely quality time with family and friends that they can't get throughout the rest of the year. To others, it's that one time when it's okay to be a greedy hog and get hammered all weekend long.

When most people say, "Damn, look at that rock," regarding an engagement ring, they're usually not referencing an actual rock—let alone a space rock.

Since the dawn of time—well, that maybe a slight exaggeration, but let's roll with it—sly entrepreneurs have been swindling the general public with inferior products for the sake of saving a few cents. Nothing is sacred when it comes to saving money: caviar, cheese, or even baby formula. Hell, there's even an entire book dedicated to the history of food swindling.

Guys, this has got to stop. It's not funny anymore. I'll defer to one of my all-time favorite people when it comes to my feelings on this unsavory subject:

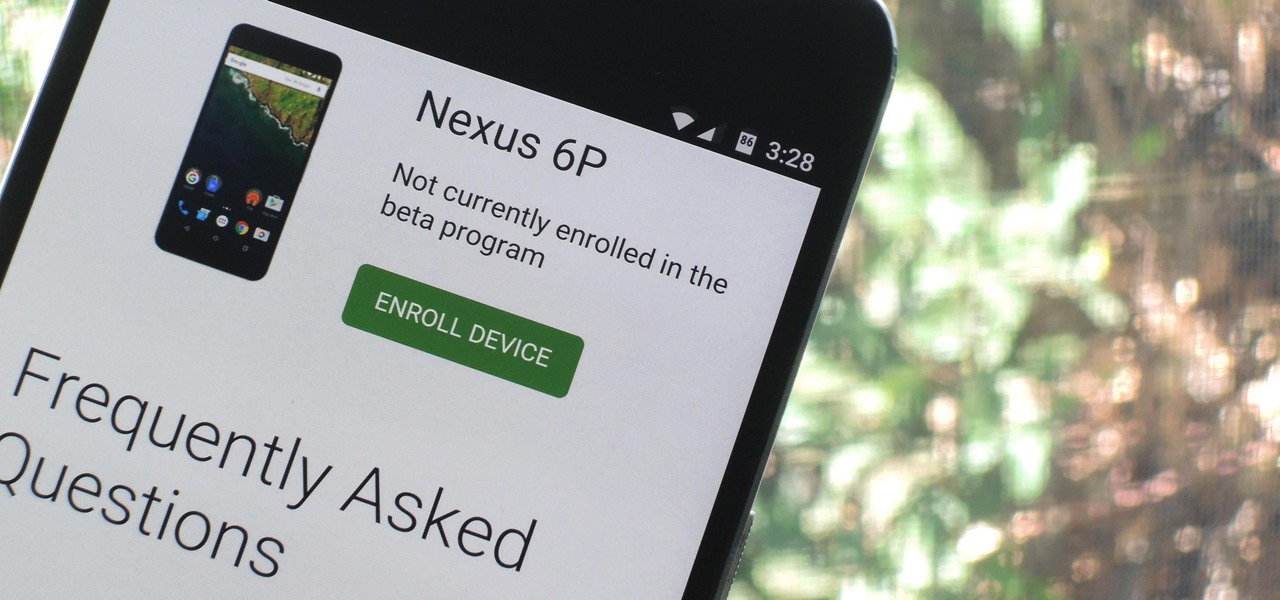
Google just released Android 7.0 Nougat, and as usual, they're doing a staged rollout. This means that most users won't actually get the update on their Nexus devices for a few weeks—that is, unless they take matters into their own hands.

You can easily take audio for granted in virtual reality, but realistic sound in VR isn't an afterthought. It not only involves creating surround sound within a pair of headphones, but figuring out where the sound ought to exist based on your position and line of sight.

During the summer, fresh strawberries are everywhere: at your neighborhood farmers market and in many desserts like strawberry shortcake and strawberry rhubarb pie, to name just a couple. Bringing home a few baskets of the ruby red fruit always seems like a good idea... until they begin to turn to mush or grow mold only a few days later.

It's very easy to get your hands on a good cake. These days, a store-bought cake or even one made from boxed cake mix will usually be pretty good. Heck, make the first simple recipe you find on the internet, and it's likely to taste fine.

Wait, don't dump that milk! It may have a slightly sour smell and be expiring tomorrow, but you can still put it to good use by making sour milk jam.

Hello people, I'm back for Part-3. In this part, as promised, we are going to create a client program and then we are going to test it with our server program made in Part-2.

When it comes to proper tomato storage, conventional kitchen wisdom (and Alton Brown) state that tomatoes are best stored at room temperature—not in the refrigerator. Supposedly, refrigerated tomatoes develop a mealy texture and lose their flavor if they are exposed to cooler temperatures over time.
In this Tutorial I will show you how you can use the frequency of letters to decrypt the famous Caesar cipher. I hope it is easy to understand and helpful for getting in touch with basic cryptanalysis. If you find any mistakes or have questions feel free to ask me. Finally I ask you to give me feedback which I will take into account for the next part.

Rich, creamy chocolate cups stuffed with smooth, salty-sweet peanut butter in a bite-sized package—yep, Reese's Peanut Butter Cups are an amazing fix for your sweet tooth at best, and a guilty pleasure at worst. It's easy enough to buy them on a whim at the local grocery store, but it's even easier than you might think to make them right at home.

Welcome back, NB community, to my series on sorting. I introduced in my last article the concept of complexity. When I say complexity, I'm talking about time complexity.
If your company has already released some popular and addictive game and you're thinking about creation a sequel, this article is just what you need. We gathered the main tips and advices that will be useful for the building a strategy and a sequel itself. Check out the following instructions and recommendations that can lend you a hand in making a sequel for your game.

For the past couple of years, random internet dwellers have embarked on an ambitious quest to see just how useless a box can be in hopes of earning sweet, sweet internet points. Welcome to the world of useless machines.

I mentioned in one of my earlier articles something about ghost hackers, and very shortly stated a thing or two of what they do.
Hello Strangers, This is my first article for null-byte and its about staying anonymous on the Internet. But the question is why would you want to stay anonymous online?

If you read my previous post, "How to Hack into a Mac Without the Password", you know that it is very easy to break into someone's Mac if you have physical access to the computer. Now the question that lies is, how do we protect ourselves from this happening to us? Well, here is a way that guarantees that no one will be able to change your password through OS X Recovery.

We've all been there before. Preheated the oven, popped in the cake, and then became distracted by this, that, or the other... until we either smelled burning or had the smoke detector pierce our eardrums.

I was bored when I found this piece of literature: ==Phrack Inc.==

With a slab-style touchscreen device, butt dialing is always going to be a problem. While you're moving about, your phone can unlock itself and give your most recent contact a ring, leading to an awkward one-sided conversation where the other person gets to eavesdrop on everything you're doing or saying at that moment.

Hello everybody Joe here. Today I will be demonstrating how you can find XSS vulnerabilities in a website and what you can do with them

Onions add essential flavor to almost any dish, whether it's a sauce, main dish, or salad. They are one of the humblest "superfoods," full of vitamins and nutrients but generally inexpensive, which is why they're also one of the most widely eaten ingredients in the world.

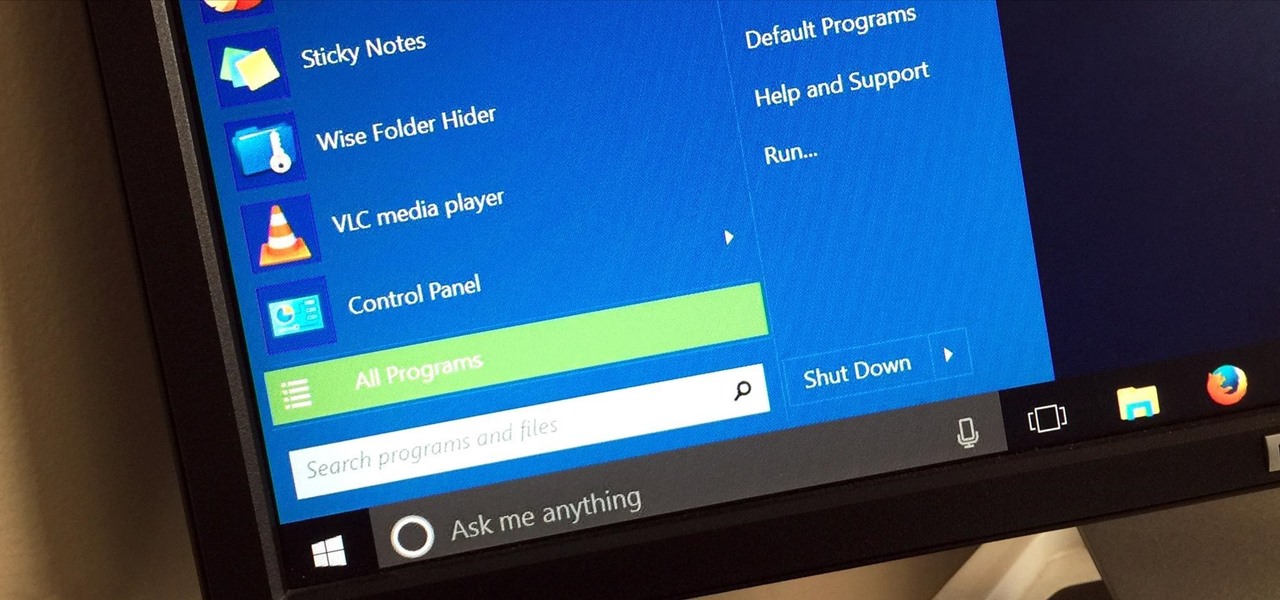
Windows 95, which introduced the Start menu to the world, recently celebrated its 20th birthday! The feature was an instant hit, becoming a core component of Windows operating systems. Well, it was removed in the mistake that was Windows 8, but you should know by now that the Start menu has been reincarnated for Windows 10.

Well hello dear readers of Null byte, let me start off stating english is not my first language and they will be some grammar mistakes. This also is my first tutorial so don't hesitate to give me feedback :)

Man-in-the-Middle attacks can prove to be very useful, they allow us to do many things, such as monitoring, injection, and recon.

For many of you, this is common knowledge. But I still regularly see comments posted here and elsewhere asking, "This <AV bypass> doesn't work, because when I upload my payload to VirusTotal...."

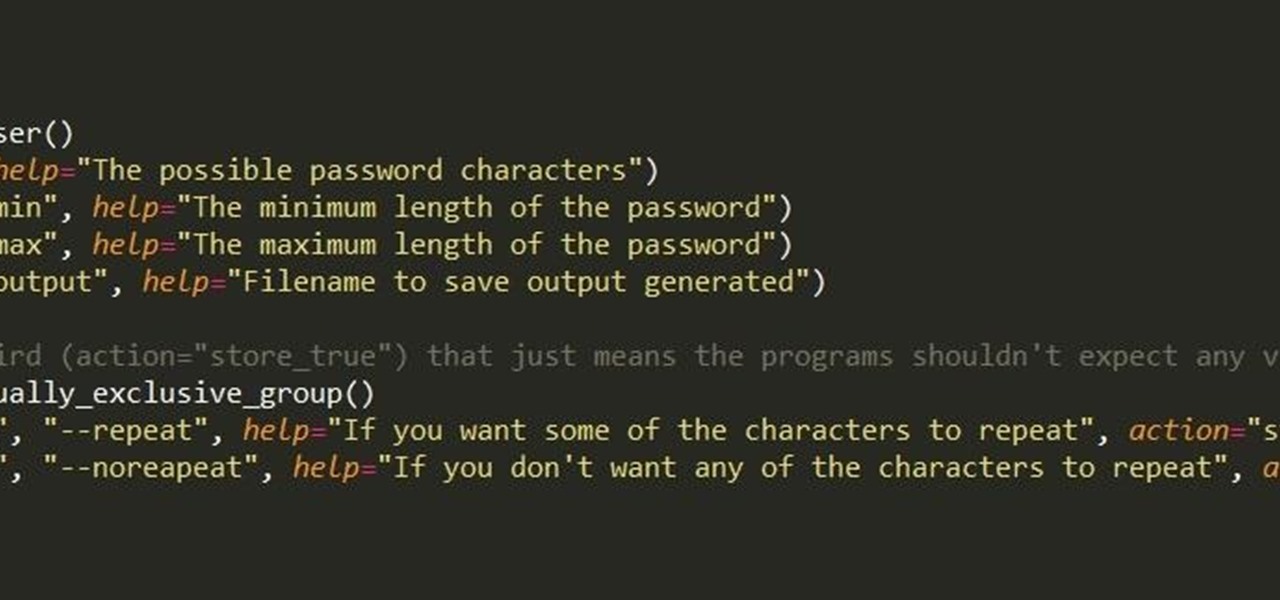
First of all, I hope the title makes sense. :D Well, this is basically creating a program that can help with dictionary attacks. Generate possible passwords. It pretty much lies in you knowing the person you want to hack.

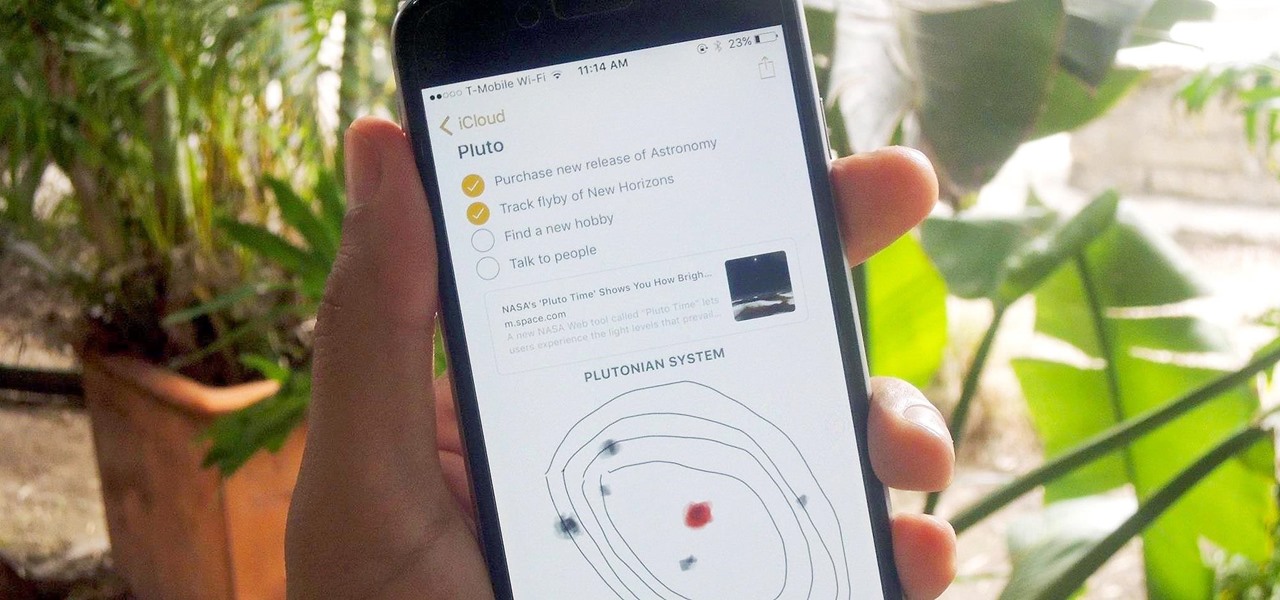
Notes on iOS has never been a particularly great app due to a lack of overall features compared to other note-taking apps like Evernote or Microsoft OneNote.

Sriracha has quickly become one of the country's most universally loved condiments. The addictive and affordable chili sauce seemingly goes on anything, and with anything, and never seems to get old. To wit: when I studied abroad, all of our food was boring, pre-packaged Sysco shipments; for three months, I smothered every breakfast, lunch, and dinner with Sriracha. And after all of that, I still eat it almost religiously.

One of the great joys of cooking is taking the most basic of foods and preparing them in new and exciting ways. About two years ago, my wife opened my eyes to a delicious staple of Indian and Moroccan cuisine that is made in a very elementary way, the preserved lemon.