While there are many advantages to working from home, properly managing your time can be a real issue. Working remotely requires a particular skill set, including an ability to focus, self-motivate, and communicate from a distance. Thankfully, all of these skills are teachable.

Snapchat popularized personalized stickers for social media and messaging with Bitmoji, followed by walled-garden versions from Apple with Memojis and Samsung with AR Emojis. Even Google has gotten into the game, integrating an emoji generator for Gboard.

You need a break from gloomy coronavirus updates. We all do. The unrelenting stream of doom and negative news is both helpful in terms of keeping ourselves and our families safe, but it also has the unfortunate effect of increasing our anxiety. When will this end? How bad will it get? Is there reason to be hopeful?

Password cracking is a specialty of some hackers, and it's often thought that raw computing power trumps everything else. That is true in some cases, but sometimes it's more about the wordlist. Making a custom, targeted wordlist can cut down cracking time considerably, and Wordlister can help with that.
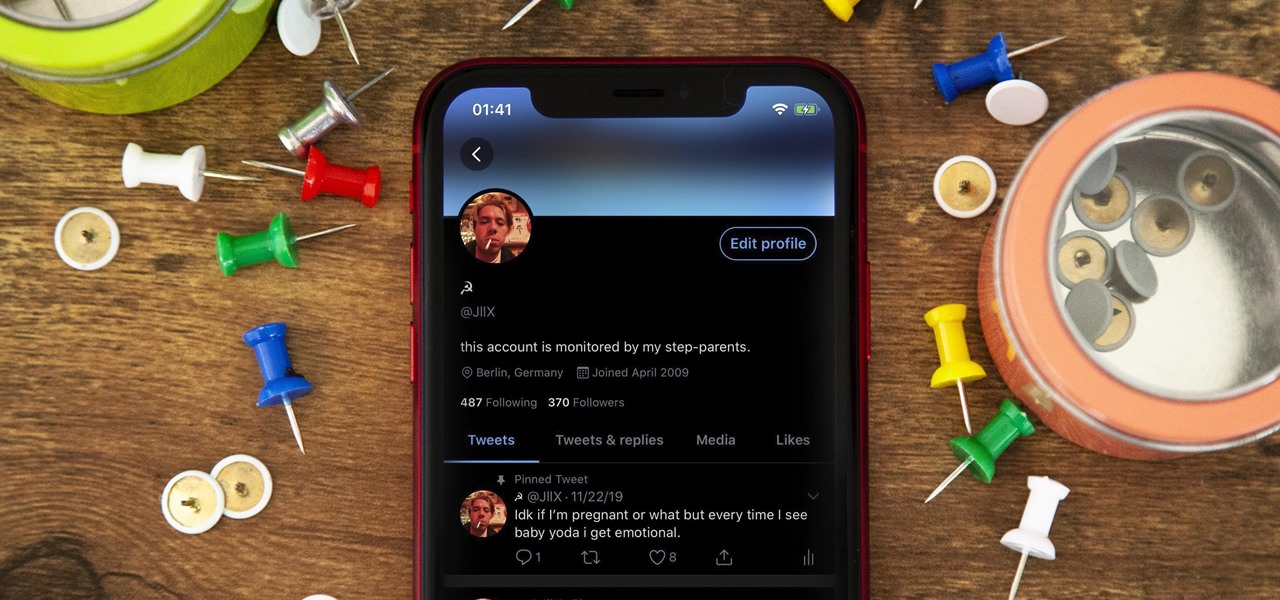
Pinning a tweet is a great way to get the point across because it's the first post people see when they visit your Twitter profile. When you pin a tweet, reply, or retweet, it sticks to the top of your profile, whether you create new tweets or not. It's the perfect spot to place one of your more popular tweets, a fantastic blog you wrote, or even just a joke that shows your personality.
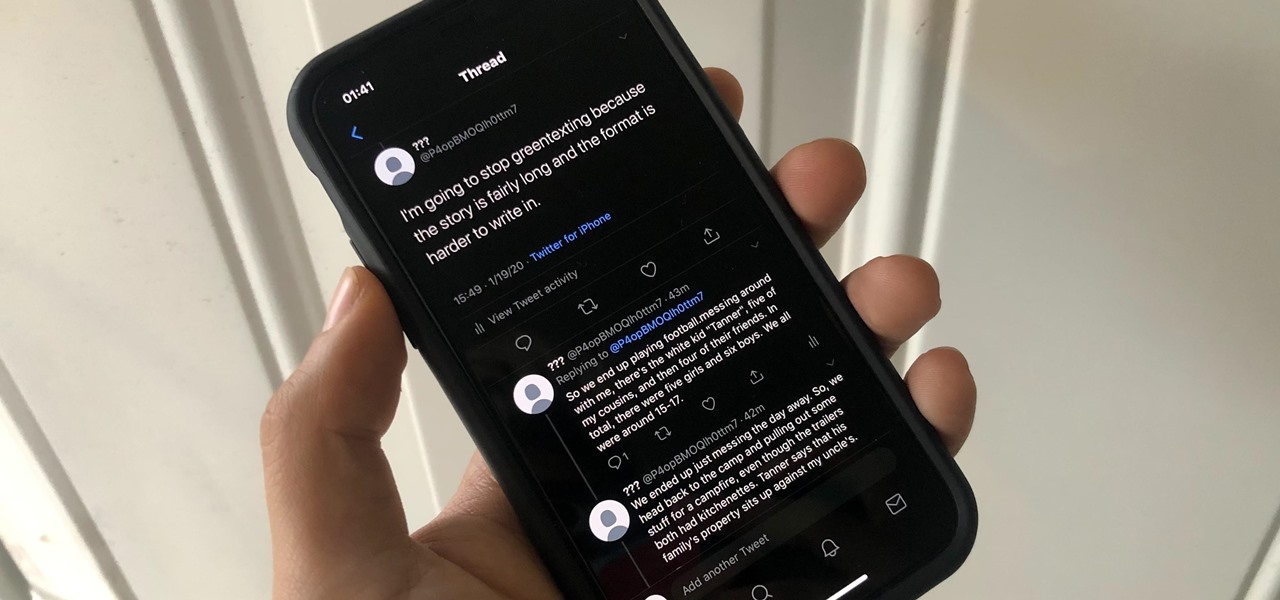
The 280-character limit for tweets on Twitter is double what it used to be back in the day, but it's still not enough to express in-depth thoughts, ideas, commentary, rants, blogs, stories, and the like. These tweetstorms, as they're called, are the reason why Twitter created its threads feature.

Facebook recently hit a snag in its quest to take augmented reality face effects to its millions of users.

Correctly identifying the underlying technologies that run on a website gives pentesters a considerable advantage when preparing an attack. Whether you're testing out the defenses of a large corporation or playing the latest CTF, figuring out what technologies a site uses is a crucial pen-tester skill.

Apple's iOS 13 has been available for beta testing since June, and the stable release pushed out to everyone on Thursday, Sept. 19. To help you make the most out of iOS 13 for iPhone, we've rounded up everything you'll want to know, whether a colossal feature, small settings change, interface update, or hidden improvement.

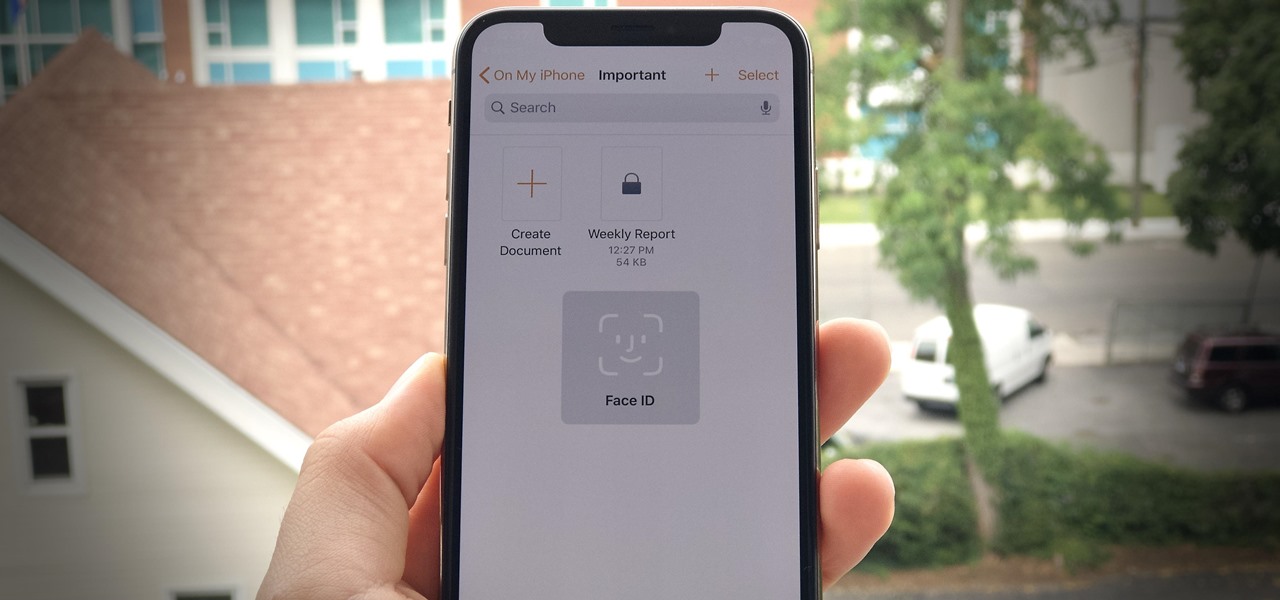
Your writing is just that — yours — so the work you do in Apple Pages should remain private until you choose to share it. Apple seems to share this sentiment. As another symbol of its dedication to user privacy and security, the company includes a feature in its word-processing app for iOS that allows you to lock documents behind a password, as well as with Face ID or Touch ID.

In a world of seemingly endless streaming services, podcasts continue to offer free, unlimited entertainment for all. When you find a podcast that's just too good to keep to yourself, sharing it with family and friends is inevitable, but how you share may determine whether or not they listen to it or not. Links alone aren't enough. Audio and video clips are how you get them sucked in.

So you forgot to send that super important email to your boss, teacher, or another important contact. We've all been there. Spark makes these panic moments a thing of the past. With "Send Later," you can schedule emails to send at any time you want, even when you're not by your phone or computer. You just need to remember to write the email in the first place.

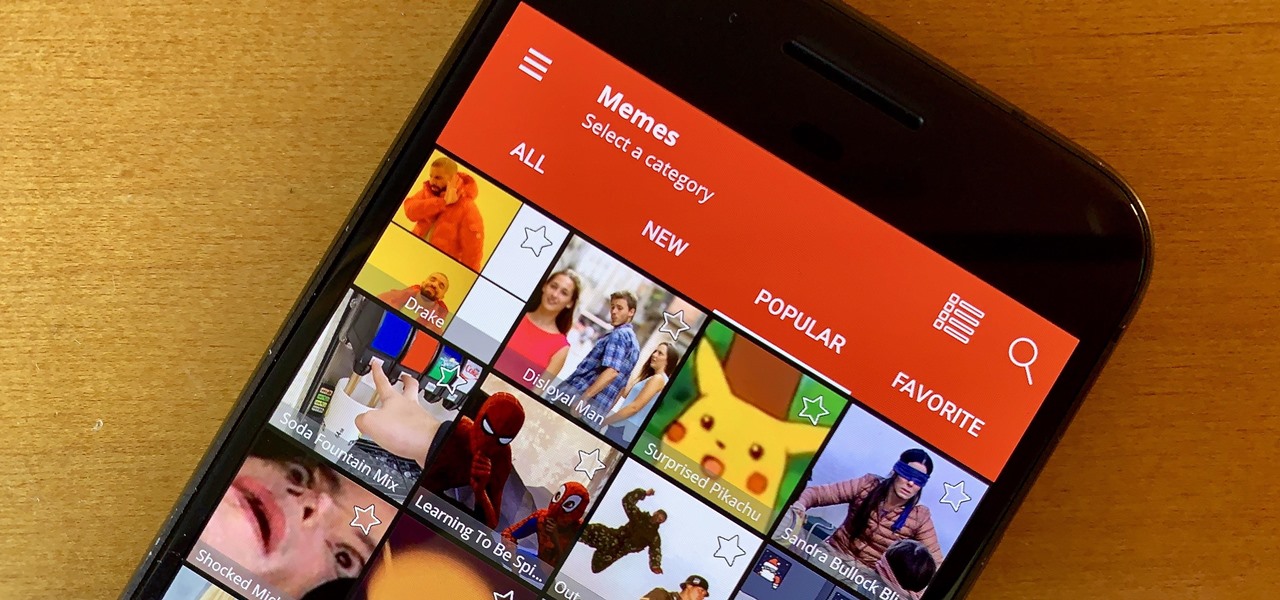
Internet memes are simply everywhere these days. While they've been popular since the '90s, memes, as we know them now, are much different these days. You used to need a computer to make viral images that spread from one random user to the next, but thanks to modern technology, you can quickly create a meme right on your Android phone — you just need the right app.

When Google finally gave us a dark theme for YouTube, it was a bit disappointing. They didn't use a pure black background, reducing some of the battery savings you'd get with an OLED panel. But with the help of another app, we can fix this, and not only get a real dark mode, but other colors as well.

If you ever looked at Apple's Peek and Pop feature on Safari and said "I want that," Google has kinda-sorta delivered. A new hidden Chrome feature brings similar functionality to Android despite the lack of 3D Touch, and while it's a bit redundant and nowhere near as polished, it does make navigating the web easier.

One of the things that sets a seasoned hacker apart from the script kiddies is the ability to effectively sneak past antivirus defenses when executing an attack. One way to do this is to use custom shellcode in an exploit. Not everyone is an expert at writing shellcode, but luckily there's an easy way to do this that is both quick and effective.

If you want the best two-factor authentication app out there, our pick is Authy. A close second is LastPass Authenticator. If neither of those is to your liking, try Duo Mobile or Microsoft Authenticator. But if you're fine with missing out on great features, then and only then should you look at using Google Authenticator.

After backdooring a MacBook not protected by FileVault or using a fake PDF to gain remote access, an attacker may wish to upgrade their Netcat shell to something more fully featured. While a root shell allows attackers to remotely modify most files on the MacBook, Empire features some useful post-exploitation modules which make hacking Macs very easy.

Ever since Google CEO Sundar Pichai took the helms of the world's most valuable brand, he has made it his mission to bring smartphones to lower-income communities. Born in India, Mr. Pichai has created several programs to address the needs of the Indian market, particularly the lower income families.

Most of us have probably used a GIF at least once or twice to respond to a message, and that's why a lot of messaging services and keyboards have GIF search tools readily available to use. Now, Google wants to take GIF responses to a more personal level, by allowing you to create your own selfies GIFs to instantly sent to family and friends.

Google Trends says that "unicorn" costumes are among the Top 5 searches for 2017, holding steady onto the no. 4 spot, trailing only Wonder Woman, Harley Quinn, and clowns. Seeing as how this year, unicorns made the full leap back into our lives, its popularity when it comes to Halloween costumes is not surprising.

One of the least important but most noticeable changes in any iOS update is the look of home screen icons. In the new iOS 11, there aren't any drastic icon differences compared to iOS 10, but there's definitely a few design modifications for some of the main stock apps, such as Maps and the App Store.

Casey Hudson, the one-time project director for games like Star Wars: The Knights of the Old Republic and the original Mass Effect trilogy, has announced his return to his former home, Bioware as the General Manager. Of course, that also means he is leaving his role at Microsoft Studios as Creative Director, where he was reportedly working on both Xbox One and HoloLens projects.

If you're someone who loves to read, you've probably read a book that made you want to hop into the story and live in the world that wasn't your own. Reading has a way of letting us escape into other worlds and experience things that we normally wouldn't be able to. Augmented reality is similar in that way. Which is why it makes sense that the two would be combined to create an incredible, immersive new way of reading.

Who would have thought that musical.ly would be the first social media app with a highly successful original show?

Maybe you thought sitting behind a Mac gives you special protection when it comes to getting hacked. Thanks to a a new report from Check Point, you can kiss that theory goodbye. The cyber security company just uncovered the latest strain of malware — OSX/Dok — infecting all versions of macOS (previously Mac OS X).

The modern age of techno-dating has made an interesting landscape for social interactions when there is some modicum of romance (or lust). For those of us born before the internet evolved into the prolific monster it has become, we first met our love interests face to face. Today, however, apps like Tinder have changed the introductory stage, for better or worse.

"Necessity, not novelty," is a phrase I use often when it comes to HoloLens development. It would be fair to call it my mantra, or mission statement, as I prototype and explore software creation on this new frontier of mixed reality.

Smartphones have been around for nearly a decade now, so we've had plenty of time to develop preconceptions and bias. People that have never owned an iPhone will tell you that Apple devices are restrictive and bland, while others might say that stock Android is boring compared to manufacturer skins like HTC's Sense, despite never having owned a Nexus or Pixel.

Avocados have been the darling of the food world for quite some time now—so you'd think that we might have already exhausted the ways in which to enjoy this amazing fruit.

Alright, NB community! Here we go... Bubble Sort. What Is Bubble Sort?

Welcome back, my rookie hackers! The Golden Fleece of hackers is to develop a zero-day exploit, an exploit that has not been seen by antivirus (AV) software or and intrusion detection system (IDS). A zero-day exploit is capable of skating right past these defenses as they do not contain a signature or another way of detecting them.

Welcome back! Sorry for the dry spell, but I've been rather busy setting up some side projects! If you remember back to a few training sessions ago, we covered basic file I/O. This is a very important step in making our scripts applicable in a real life scenario, and today we're going to further these concepts.

Welcome back! In our last training session we covered classes and how OOP can make programming/scripting easier. Today we'll be taking a breather and covering something fairly simple, bitwise operators.

Hello again, readers! In our previous crypter tutorial, we looked at how we could obfuscate our malware (or any program) by using a simple one-byte XOR key. In this quick tutorial, we will be looking at how a simple little tweak can create a better means of obfuscation. Let's get right into it!

After seeing the title of this post from me, you might be thinking, "Why did The Joker made another post on a topic on which we already have a nice sticky post?"

Welcome back! In the last training session, we covered logical and membership operators. We're going to switch gears and expand our knowledge of lists.

Welcome back, reader! In this tutorial, we will be covering our first program! So let's get to it. We all know the unspoken tradition of the first program when learning a language and of course, here we will respect and complete it. Fire up your favorite text editor (be it vim, emacs, gedit, it's all the same to me, no h8) and try to keep up.

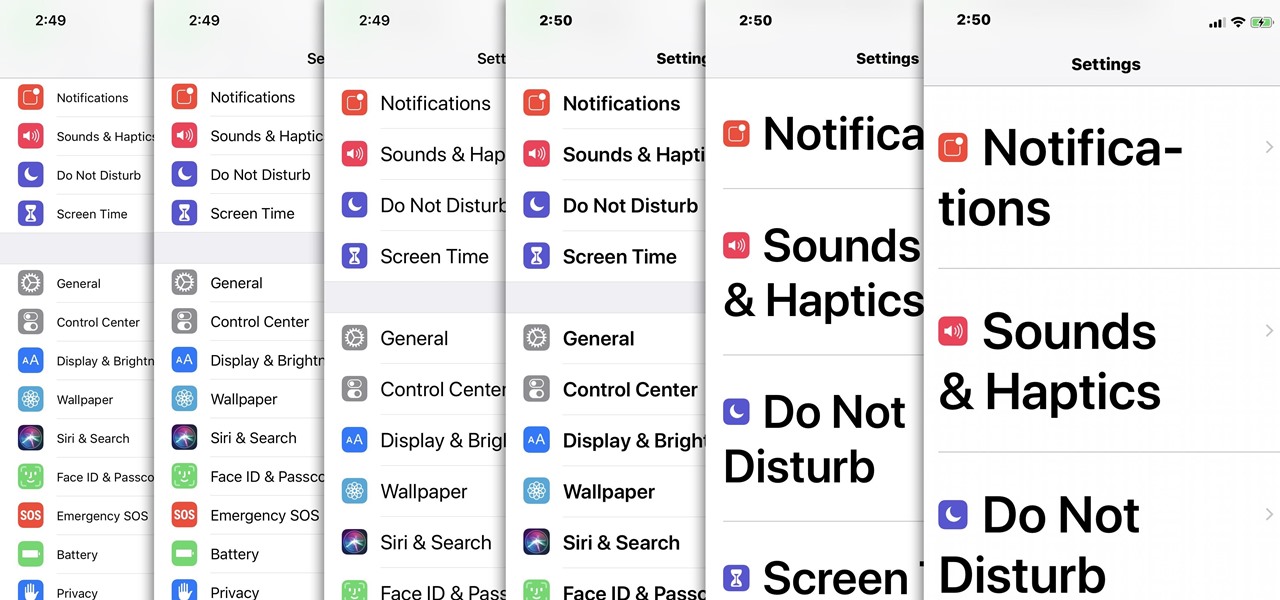
For most people, the font that Apple uses in iOS is just perfect, but some of you may think it's too big while others with poor vision may have a hard time reading it. Whether you're having a hard time seeing text on your iPhone or just want something different, there are actually three things you can do to adjust how text is viewed.

Welcome back! In the last iteration of how to train your python, we covered loops, today we'll be covering something that I wish I had learned about much earlier in my scripting career, errors. We all run into them, and they can be frustrating, but there is also a silver lining to them. Today, we'll be discussing why some errors are unavoidable, and what we can do when we run into them. Also, this article will be more of a concept and less of writing actual code, but the information is equall...