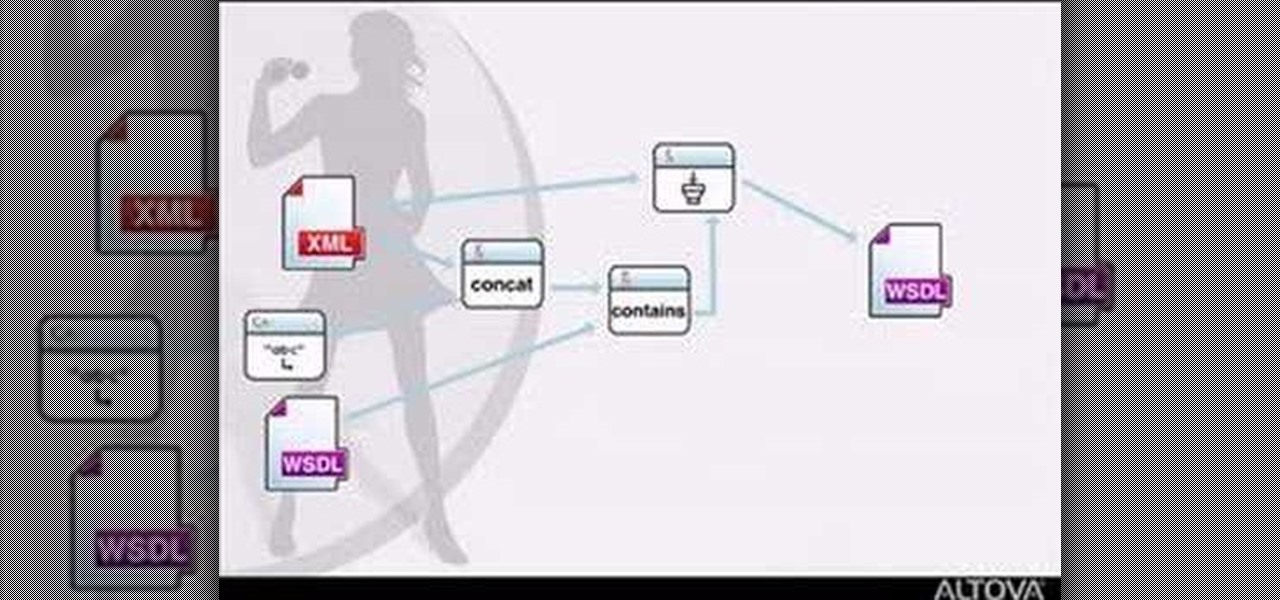
If you want to do some easy XML editing, then this markup language video is the one to watch, for XMLSpy. The graphical WSDL editor allows developers to design the interface for Web Services in an intuitive manner.
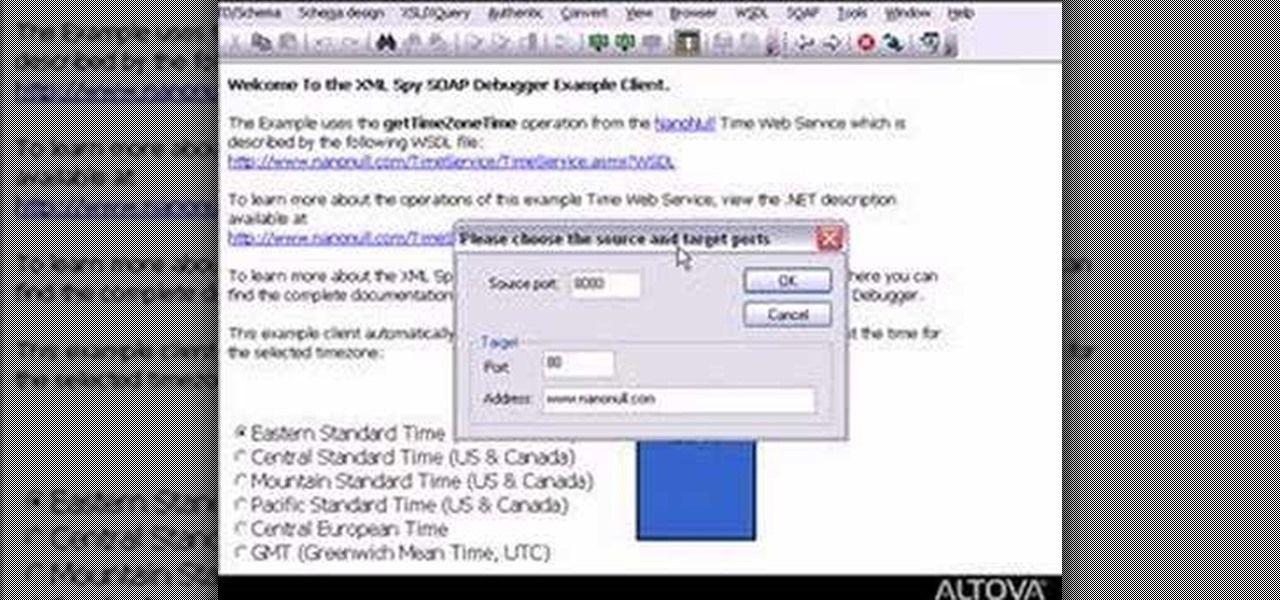
Need to debug some exisiting net services? Well, check this video out for how to do some basic XML editing in XMLSpy.

This guide will explain how to configure a USB Flash Drive / Memory Stick so that you can run a keylogger within just a few seconds of plugging it in any computer.
SoundHound's new virtual assistant application, Hound, is gaining a lot of buzz in the tech world—especially after a demo video showed just how awesome it works (it has amassed over 1.6 million views in under a week).
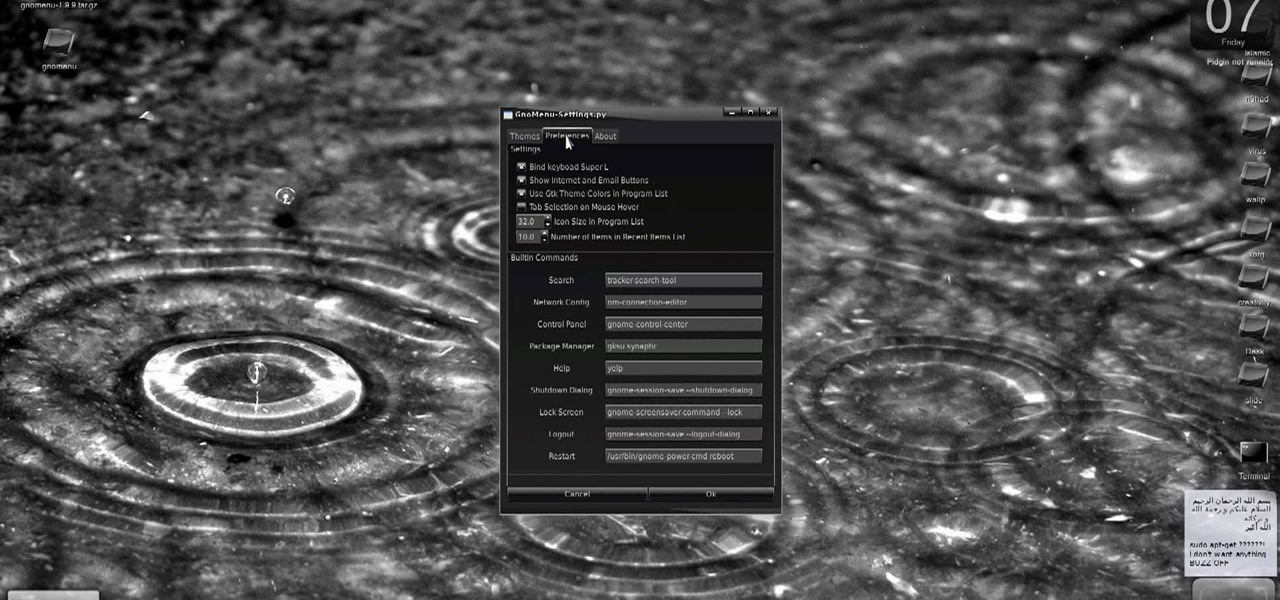
New to Ubuntu Linux? This computer operating system could be a bit tricky for beginners, but fret not, help is here. Check out this video tutorial on how to install GnoMenu on Ubuntu Linux.

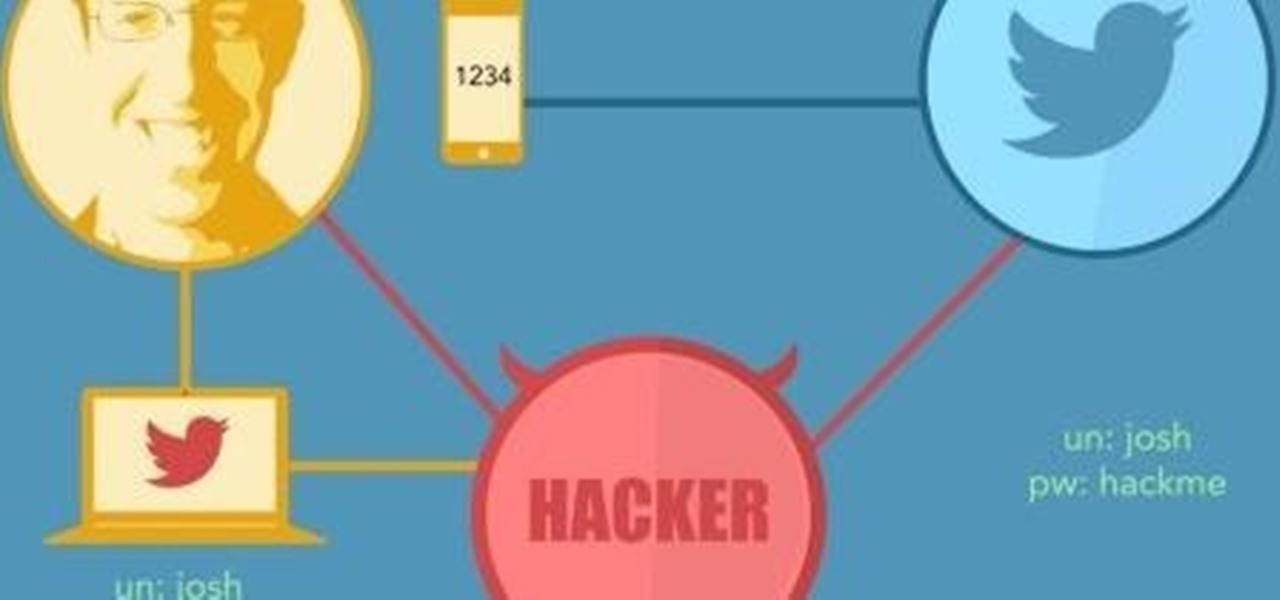
Single sign-on (SSO) lets users login across different sites without having to manage multiple accounts. I'm sure most of us appreciate the convenience of seeing "Sign in with …" buttons that let us login with a single username. Hackers, however, see a possible avenue for exploitation, and you'll soon learn how an attacker can exploit a SAML vulnerability to assume another user's identity.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - https://techkernel.org/2015/12/19/embed-metasploit-payload-in-apk-manually/

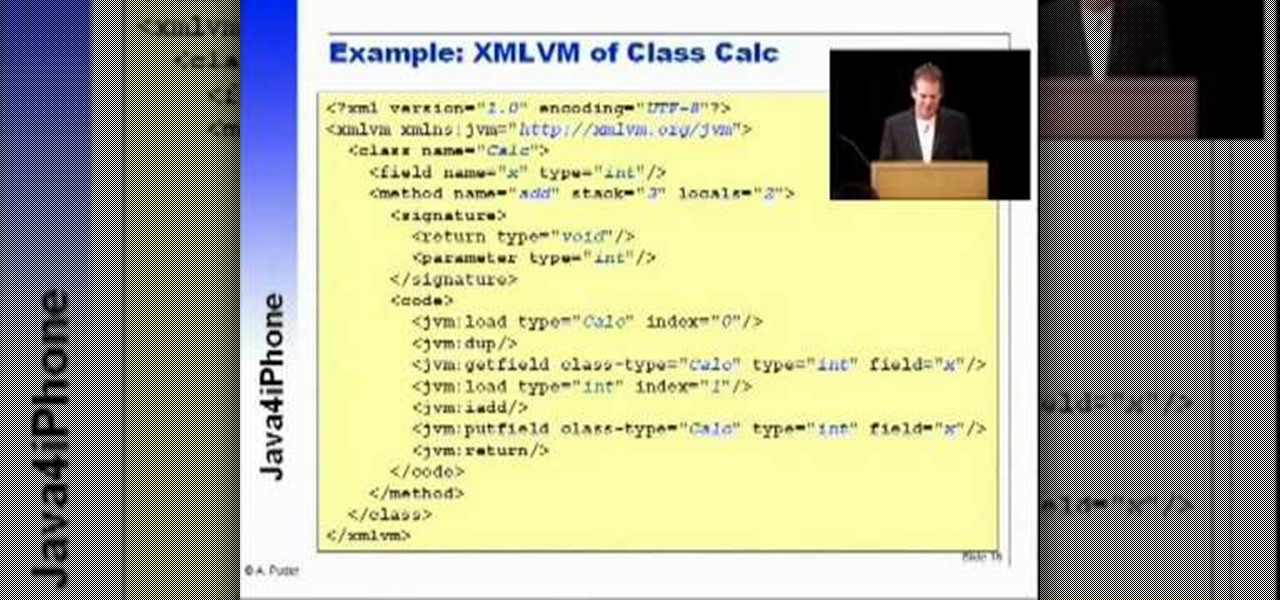
Arno Puder, a master of the XML coding field, gives a great rundown of Apple's new proprietary Java coding. This is especially helpful for Cocoa implementation

Regardless of what you're trying to accomplish with Tasker, there's a good chance that someone else has already walked through the same steps. If you're unfamiliar with creating tasks and working with profiles, simply importing someone else's work would be a great shortcut. After all, there are 2 billion Android devices out there, so someone must've created a setup that suits your needs, right?

Carriers like to distinguish their Android phones from the competition by making small changes to the interface here and there. This practice is so common that Android now has a built-in system for managing these small tweaks.

Podcasts have been around and popular for close to a decade now. For the uninitiated, podcasts are like radio shows that can be downloaded directly from the web and listened to on any device. Up until now, only paid apps allowed podcasts to be casted via Chromecast, but with the latest update to Xavier Guillemane's Podcast Addict, you can now do the same thing for free!

Early last month, Sony released PlayStation Mobile, bringing PlayStation games to the PS Vita and other certified phones and tablets. The list of certified phones isn't as extensive as it should have been, consisting of only Sony devices (a few tablets and Xperia) and a couple of HTC ones. For anyone with a supported device, you can head over to the PS Store for the download and installation instructions.

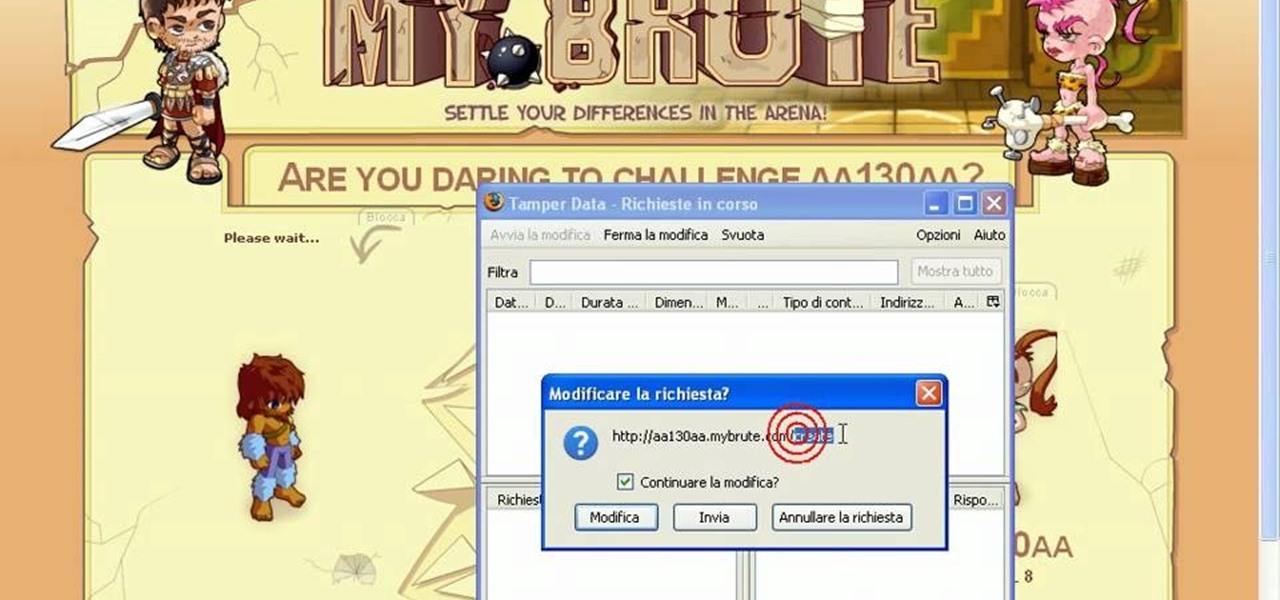
Hack mybrute with this mybrute cheat. MyBrute hacks, cheats, tricks. Watch this video tutorial to learn how to cheat MyBrute for a bear (05/08/09). This is the easiest way to get a bear!

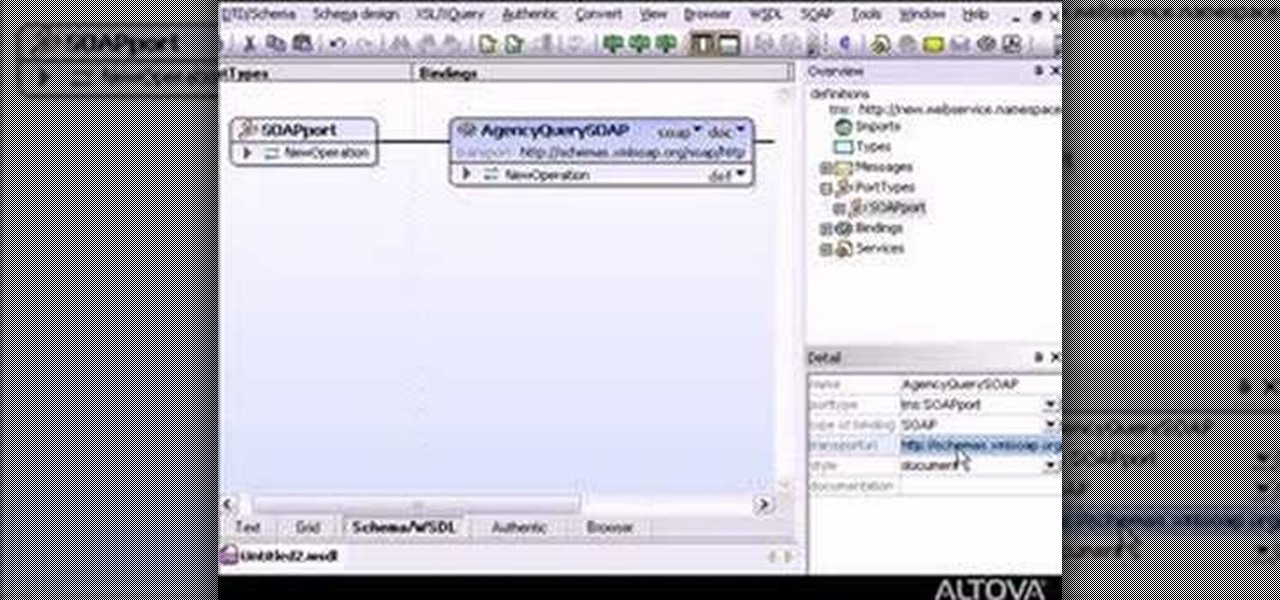
MapForce supports XML, databases, flat files, EDI and web services as the source and target of any mapping. In this tutorial, you'll take a look at how to use the different data sources available in MapForce.

Reconnaissance is one of the most important and often the most time consuming, part of planning an attack against a target.

Watch this video to learn how to edit the Windows Experience Index. While it may not be apparent from the video, but it is really quite simple. Browse to C:\Windows\Performance\WinSAT\DataStore

In my previous article, we learned how to generate a vulnerable virtual machine using SecGen to safely and legally practice hacking. In this tutorial, we will put it all together, and learn how to actually hack our practice VM. This will provide some insight into the methodology behind an actual attack and demonstrate the proper way to practice on a VM.

The triple camera system on the OnePlus 7 Pro is the best setup they've ever done so far, but it could always be better. The primary sensor packs a whopping 48 megapixels, but as history has taught us, megapixels don't equal better photos by default. In fact, with where we are in terms of hardware right now, it's the software that determines a phone's camera performance.

Samsung has stepped up its camera game with the Galaxy S10's dual- and triple-lens systems. But as impressive as the hardware is, the native Samsung Camera app still isn't as good with image processing and video stabilization as the Google Camera app for Pixel phones. Thankfully, you can get the best of both worlds.

Recently, Sprint announced a partnership with Harman Kardon to deliver exclusive sound FX technology to their variant of the HTC One M8. The joint effort between the two companies is both to entice customers to switch to Sprint as well as improve the overall audio quality coming from the already extraordinary BoomSound speakers. But while this is great for new and existing Sprint customers, it does leave the rest of us out in the cold.

It's nearly impossible not to be at least somewhat familiar with Microsoft Excel. While it's needed for many office jobs and data analysis fields, hackers could also benefit from improving their spreadsheet skills. Many white hats already know some of the essential Excel hacks, such as cracking password-protected spreadsheets, but there's so much more to know from an attack standpoint.

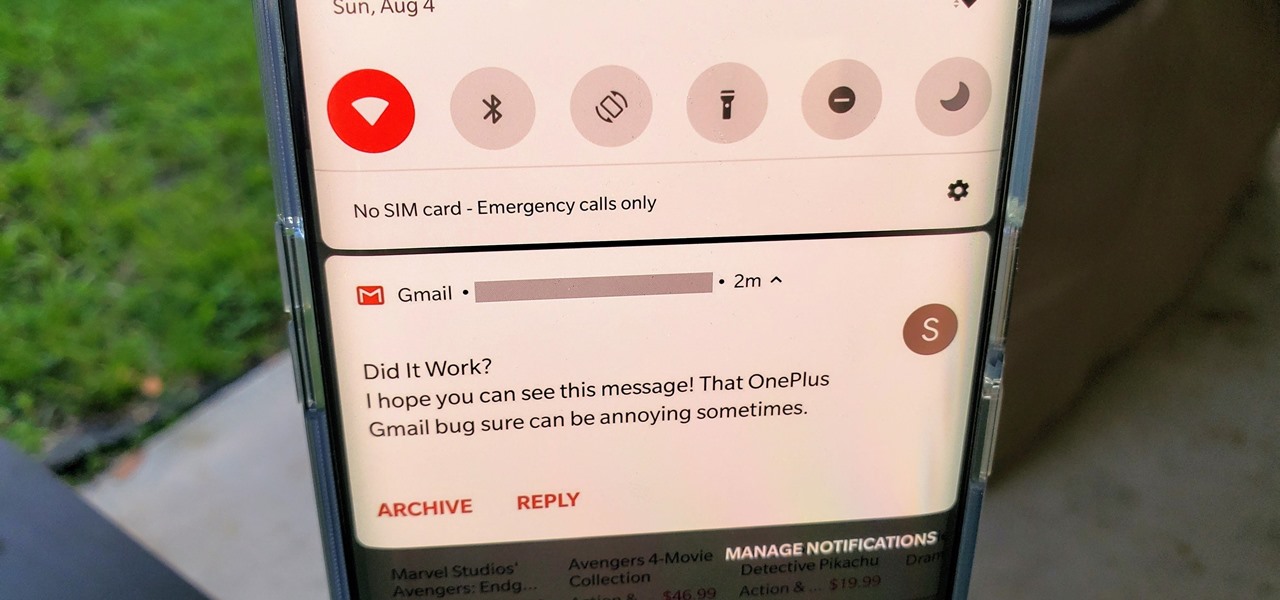
OxygenOS is often described as one of the best skins for Android on the market. It's fast, clean, and has a ton of useful features that appeal to just about everyone. However, it's also faced a significant issue for the longest time — overly aggressive battery optimizations that frequently kill background apps, including Gmail services.

Being in a band, I exposed myself to years of extremely high volumes, so I can't hear as well as I once did. I'm not concerned about going deaf or anything, but I tend to have the volume raised to the max, beyond the "high volume" warning, whenever listening to music on my OnePlus One with headphones.

Bluetooth has been a staple on every Android smartphone ever since they began taking over our lives. Despite the fact that every device seems to have the ability to share files with one another, there is a limit to the types of files that can be shared between them.

It always helps to be prepared for the worst. This applies to our phones now more than ever, as we depend on them to be our record keepers for text messages from friends, family, and coworkers. If you ever lose or severely damage your phone, having a backup of your precious texts gives you the peace of mind of knowing that you can always get them back.

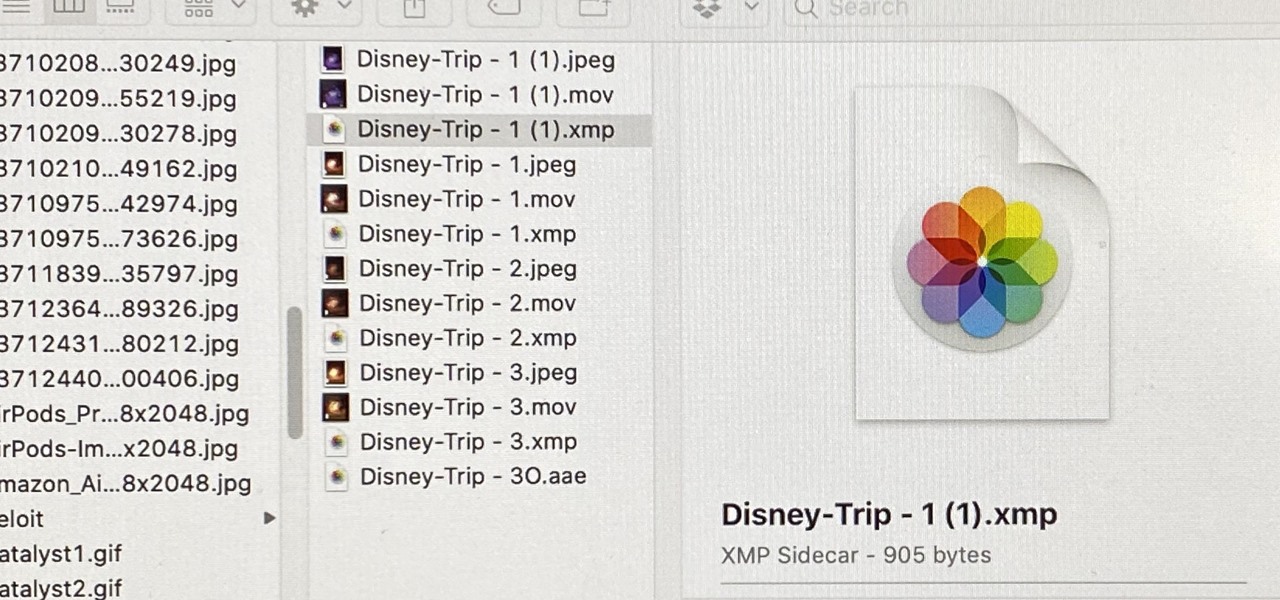
When you export an image from the Photos app in macOS, you may not be getting the whole deal. In the export menu, you need to select either JPEG, TIFF, or PNG, and if you don't make any adjustments to the quality settings, it'll likely be compressed. If you need the original full-resolution file or want to get the video that's attached to a Live Photo, there's a simple way to do it.

The first sneak peak of Android O is finally here. The developer preview promises more features, stabilization, and better performance, according to the Android Developers Blog. Furthermore, there's speculation that the latest operating system will be code-named "Android Oreo," so it definitely sounds like we're in for a treat.

Hi guys, this is going to be kinda like a follow up to my previous post on hacking facebook with the remote keylogger. If you haven't seen that post I suggest you do. So like you can click here. Anyway let's move on.

Slowly but surely, Microsoft seems to be steering Windows in the direction of Google's Android. First, they released Windows 10 as a free upgrade, mainly because they wanted to cash in on the revenue that they hoped would come when more users had access to the Windows Store. Then, they included tons of tracking "features" to help populate Bing with targeted ads, which has always been Google's primary method for monetizing Android.

Welcome back, my budding hackers! With this article, I am initiating a new series that so many of you have been asking for: Hacking Web Applications.

Today, I want to share a tutorial on one of the most useful but old methods which you could use to hack websites, that is using the Dot net nuke (DNN) vulnerability . I know some of you already know about this method.

A wave of shock and anger swept across the country after Edward Snowden released private documents recounting the U.S. government's secretive mass surveillance programs. Although some of the fear was unwarranted (they don't read your emails or listen to your calls), many scrambled to find privacy of new heights for protection from the all-watchful eye. While the government may not be tracking you down, there are a myriad of other candidates that fill that Big Brother role—and I'm not talking ...

The beauty of free apps is that, well, they're free. But as we all know, there is no such thing as a free lunch. Sometimes these "free" applications are only feature-limited mini versions, or they're so littered with ads that opting to pay for it is the only way to actually enjoy it.

With the number of web applications out there today, it comes as no surprise that there are just as many vulnerabilities waiting for hackers to discover. Finding those vulnerabilities can be a difficult task, but there are plenty of tools available to make the process easier. While it won't help find any zero-days, web scanners such as Uniscan will detect common vulnerabilities.

Not all websites are created equal, and that's why Safari doesn't apply Dark Mode to each webpage you visit during your iPhone's system-wide dark appearance. But in Safari's latest update, Apple gives its web browser more power to automatically apply Dark Mode to specific website content without having to use extensions like Noir.

The first few minutes after gaining access to a MacBook are critical — but where do we begin? Using tools built into macOS, we can develop an in-depth understanding of running background processes, detect antivirus software, locate sensitive files, and fingerprint other devices on the network. All of this can be done without installing additional software or modifying any files.

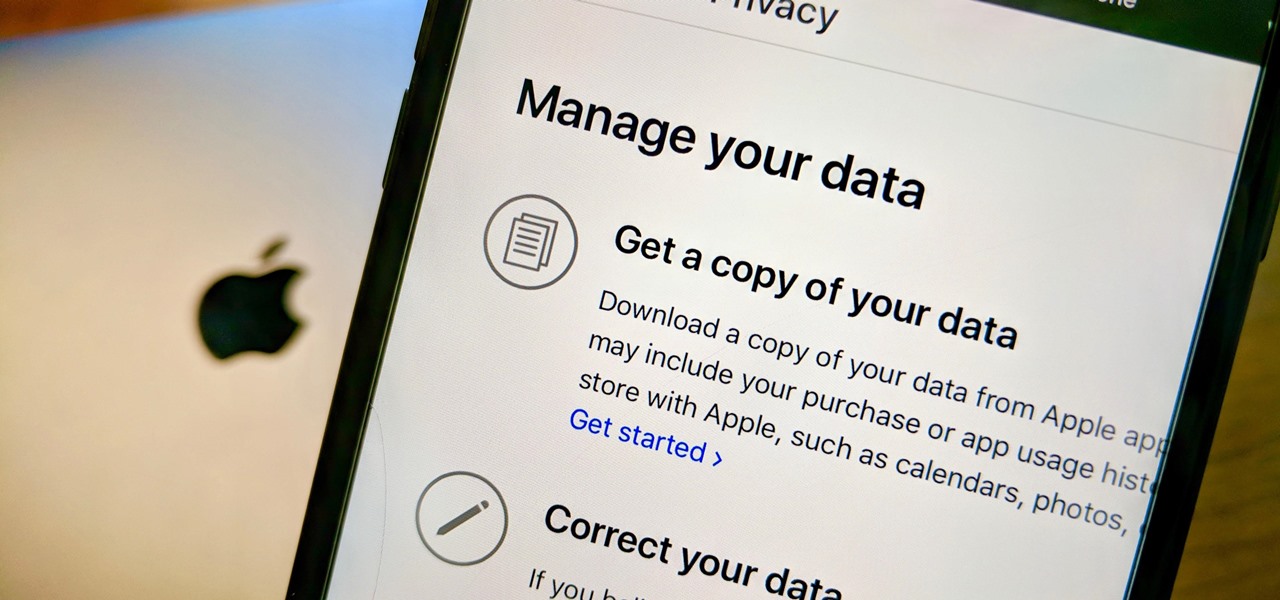
Personal data is a hot topic right now, and for good reason. Never before has the public been so on edge about how companies use their information. Services like Facebook and Google now allow you to download all of the data each has on file. Soon, you'll be able to see exactly the same for Apple as well.

Using Hydra, Ncrack, and other brute-forcing tools to crack passwords for the first time can be frustrating and confusing. To ease into the process, let's discuss automating and optimizing brute-force attacks for potentially vulnerable services such as SMTP, SSH, IMAP, and FTP discovered by Nmap, a popular network scanning utility.

In a previous article, we learned how to take advantage of a feature, Dynamic Data Exchange (DDE), to run malicious code when a Microsoft Word document is opened. The biggest challenge of this attack is that it requires getting the user to agree to a pop-up prompt. Fortunately, since I posted that article, many new obfuscation techniques have been discovered to make this easier. Today, we explore and combine some of them to make the ultimate hidden DDE attack.

Surely you've heard of the wildly-popular custom ROM CyanogenMod, right? As the longest-tenured third-party firmware for Android devices, CM has been able to maintain its popularity by supporting a wide array of devices and offering many customization options.