Google Reader is soon to be no more. Yesterday, the company announced that the service will be shutting down as of July 1, 2013, as part of Google's second "Spring Cleaning."

With an ordinary birthday card, we can introduce a physical device which contains malicious files into someone's home and deceive them into inserting the device into a computer.

Surveying a target's Wi-Fi infrastructure is the first step to understanding the wireless attack surface you have to work with.

UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found UPDATE: This post is outdated, the latest version with the correct links and updated instructions can be found at my blog, here - at my blog, here - https://techkernel.org/2015/12/11/embed-metasploit-payload-in-apk-easily/

Welcome back, my nascent hackers! In the conclusion of the Mr. Robot television series, Elliot and fsociety successfully completed their mission of encrypting all of Evil Corp's data with AES-128 encryption and destroying the key.

Welcome back, my rookie hackers! So many readers come to Null Byte to learn how to hack Wi-Fi networks (this is the most popular hacking area on Null Byte) that I thought I should write a "how-to" on selecting a good Wi-Fi hacking strategy.

Possibly the most popular feature in iOS 14, home screen widgets are here to stay. Apple created a ton for its own apps, and third-party developers keep building ones for their own apps. But home screen widgets go beyond that since you can make a widget for practically anything you want, from a custom news feed to an inspirational picture of the day — and this is how you do it.

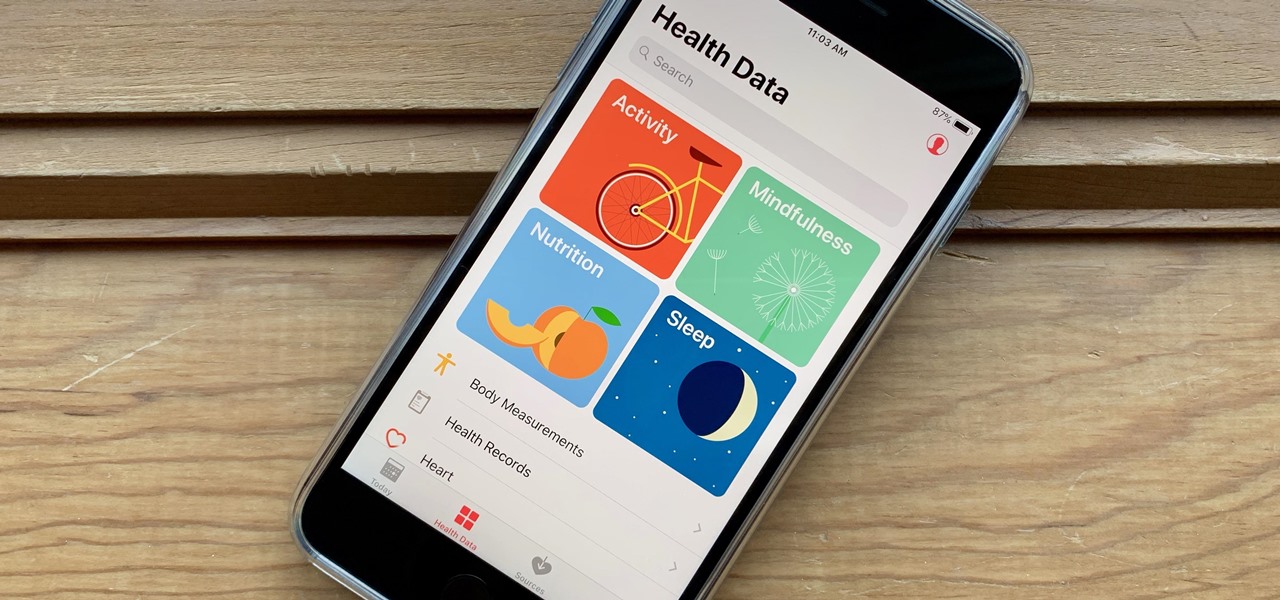
It's not easy staying fit and healthy these days with addicting phones, oversized portions, and long workdays, to name just a few things. To succeed, it takes work, commitment, and an understanding of your mind and body — and your iPhone can help you with some of that. While Apple pushed its Screen Time tool to help curb unhealthy smartphone habits, its "Health" app can help with everything else.

Complex shell scripts can be implanted into photo metadata and later used to exploit a MacBook. In addition to obfuscating the true nature of an attack, this technique can be used to evade network firewalls as well as vigilant sysadmins.

Auditing websites and discovering vulnerabilities can be a challenge. With RapidScan and UserLAnd combined, anyone with an unrooted Android phone can start hacking websites with a few simple commands.

The idea of a perfect phone is a myth. There are lots of pros when it comes to OnePlus devices, but there are also a few things that could be better. And even if there were a phone without flaw, there are still things that you might want to customize for personal preference. That's why we set out to find the very best tweaks for OnePlus phones, and to make it easier for you to apply them.

Web application vulnerabilities are one of the most crucial points of consideration in any penetration test or security evaluation. While some security areas require a home network or computer for testing, creating a test website to learn web app security requires a slightly different approach. For a safe environment to learn about web app hacking, the OWASP Juice Shop can help.

Open-source data scraping is an essential reconnaissance tool for government agencies and hackers alike, with big data turning our digital fingerprints into giant neon signs. The problem is no longer whether the right data exists, it's filtering it down to the exact answer you want. TheHarvester is a Python email scraper which does just that by searching open-source data for target email addresses.

Welcome back, my fledgling hackers! Over the years, we have examined multiple ways to own, exploit, or compromise a system. On the other hand, we have not spent a lot of time on denial-of-service (DoS) attacks.

Welcome back, my hacker apprentices! Metasploit framework is an incredible hacking and pentesting tool that every hacker worth their salt should be conversant and capable on.

The public leaks of NSA tools and information have led to the release of previously secret zero-day exploits such as EternalBlue, which was used in the notorious WannaCry ransomware attack. Despite multiple patches being released, many users have failed to update their systems, so many devices are still vulnerable to these now-public attacks.

It's easier than you might think to hack into Wi-Fi routers using just one unrooted Android phone. This method doesn't require brute-forcing the password, a Windows OS for converting PowerShell scripts into EXE format, a reliable VPS for intercepting hacked Wi-Fi passwords, or Metasploit for post-exploitation tricks.

Step 1: What Exploit Development Is and Why Should I Be Interested on About This Topic

Not all websites need a dedicated mobile app, which is why so many don't. Web apps are now designed to scale to different screen sizes, so mobile sites in your web browser are easy to navigate and utilize. Still, there's just something about an app on your iPhone's Home Screen that makes it feel more like an app from the App Store.

Withstanding an attack from a motivated hacker is one of the most important responsibilities a system administrator must undertake. This is especially true for websites that may contain sensitive customer information and a high volume of users. So it's important for a sysadmin to take proactive measures to find and fix vulnerabilities in their websites.

After Effects CS4 allows you to save any After Effects project in an editable text format known as XML. This tutorial will show you how to use the XML file format to modify and dynamically update an After Effects project without having to run the After Effects CS4 application. Using XML format After Effects files is a great way to save time and maintain flexibility by using a simple text editor to make changes. Use the XML project file format in After Effects CS4.

This video introduces you to XML (Extensible Mark-up Language) , and prepares you to work with Ajax. You will learn how quick and easy it is to create a new XML file in Dreamweaver CS3 and what the typical contents of an XML file are. Use XML in Dreamweaver CS3.

In this clip, you'll learn how to use XML within a C# app. Whether you're new to Microsoft's popular multi-paradigm programming language or are a seasoned developer merely looking to improve your chops, you're sure to find benefit in this free, official video tutorial. For more information, including detailed, step-by-step instructions, take a look. Use and work with XML documents in a C# application.

How to Create Scenery in FSX

An RSS feed is a dynamically generated XML summary of information or news published on a website. The Feed2JS tool provides an easy way to display RSS feeds on your website, all without knowing the least bit about XML. All you need to enter is the URL for the RSS source and decide how you'd like it to be formatted. For more on using the Feed2JS tool, watch this video tutorial. Display RSS feeds on your website with Feed2JS.

Tom Green shows how to easily take an effect created in After Effects and bring it over Flash using the XML format.
Check out this easy way to find your polling place for the Election tomorrow November 2nd.

This two part video goes over using XML Conform workflows and Digital Intermediates workflows in Smoke. The videos are a touch dry, but they cover the material in a well paced and thorough presentation. Understand and use advanced conform workflows in Smoke.

The modo camera and rendering system is incredibly powerful and flexible. This new film back preset options helps you to quickly harness that power for your specific target medium. Need to render out to 2k Academy 35mm film? No problem. Imax? Sure thing. Did we mention this is an XML driven preset system so you can add your own? See how to use the film back preset render options in this modo 301 tutorial. Use Film back presets when rendering from modo 301.

INTRODUCTION If you are a part-time blogger and owns a blog which is hosted on blogger, then the first thing which you could want to do is to convert your blog layout to a professional looking website. You can either edit the XML file yourself or you could choose to use a template designed by others. If you have no idea of XML editing and neither you want to use a template created by other, then hopefully there's a way to convert your blog into a website.

To create an elegant WordPress blog or website from scratch without being noticed that you're a complete beginner, you need that drive and pairs of eyes and ears. It may seem difficult at first but it can truly be fun and exciting.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

It's no secret. Professional video editors everywhere are irate at the newest edition to Apple's popular non-linear video editing software, Final Cut Pro X. As of right now, Final Cut Pro X has 503 five-star ratings in the Mac App Store. Not bad. But it also has 671 one-star ratings and 414 users who aren't sure what they think. It's such a bad update that it even earned itself a skit on Conan.

Recently, buyout talks between Google and Groupon ended with Groupon turning down Google's $6 million offer. But with Amazon backing LivingSocial, should they have? Your guess is as good as mine, but one thing's for sure— Groupon has a great voice, and they're sharing it with the world via their Public Groupon Editorial Manual.

Backing up your files is a requirement in today's world of tech. In an instant, your storage device can fail. This is an unacceptable situation that should never happen to anyone. Storage is cheap, and backups are easier than ever to perform. Most of the time, this can be completely automated, so you can just set it and forget it. Today, Null Byte will be covering how we can automatically, and efficiently back up our data across all OS platforms, while giving a few alternatives to the built-i...