INTRODUCTION In this Digital world now almost every one knows the a, b , c of computer. From a child of 5th grade to an old man, everyone knows how to operate computer and do simple work on it. Thats why you need to have something which makes you different from others.

Huzzah! My sentences have been recorded! This is normally the most exciting part of beginning a language with this method, because you actually had another person do something for you that is really of great value. I remember receiving my first recording in Japanese. I listened to that thing about 100 times. I shadowed it, repeated it to my family multiple times and still hear it in my head from time to time.

Nothin's better than freshly homemade popsicles in these hot summer months. Design Sponge has posted three delicious-sounding recipes by Ashley of Small Measure.

With the mass arrests of 25 anons in Europe and South America, and the rumors of an FBI sweep on the east coast of America floating around, times look dicey for hackers. Over the past few days, a lot of questions have been posed to me about removing sensitive data from hard drives. Ideas seem to range from magnets to microwaves and a lot of things in-between. So, I'd like to explain a little bit about data forensics, how it works, and the steps you can take to be safe.

In this article, I'll show you how to create a simple yet effective way of scaring off intruders. Of course, there are methods around this approach, but it's great for office pranks and general fun. The project requires a little background knowledge in electronics and circuitry, like reading schematics and using a soldering iron.

When your computer first connects to a nework, it sends out a request on the network to lease an IP from the router. The router then leases your computer an unused IP address, which is used as a unique routing address for sending traffic that is meant for you, to you. As everything tends to, this method has its flaws.

If you found the world renown Body Worlds exhibition gnarly and perverse, perhaps you'll find this latest parade of plastination a little less so—considering we don't share the same DNA as these specimens of jerky-in-the-name-of-science. The Koerperwelten der Tiere—or Animal Body Worlds–doesn't showcase preserved corporal matter, but rather 20 odd plastinated mammals, currently on display at the Cologne Zoo in Cologne, Germany.

Introduction PostgreSQL is a very popular Open-Source database management system. It competes heavily with many proprietary and commercial database management systems. More information on what it is and it's history can be found here and here.

Alas, today we continue on the journey to a more environmentally conscious way of being with part 2 of How to make your beauty routine more eco-friendly. Check out part 1 here.

If you've been reading, watching or listening to the news, you sure know about the Trayvon Martin case. If you visit this site often, you may also have noticed that I've not put up any news on this case. I have my reasons. And this post will describe why.

Injection is an attack vector that involves breaking out of a data context and switching into a programming context through the use of special characters. These characters are significant to the interpreter being used, but not needed for the general user input being asked for.

In the first part of this series, we learned about darknets, as well as how they came about. But these patches of forgotten Internet are not the oasis of free information you might think. Despite being hidden—or just harder to come across—these networks are no more safe then anywhere else on the 'clear' Internet. The nature of networking and routing means your location is always known in server logs. It only takes one phone call to your ISP with your IP address to obtain both your physical ad...

Some people are what is labeled a power user. I am one of these people. No matter how fast I get my system, or how quick of programs I have, it is never good enough. There is always at least one program that I could swap out for a more advanced, text-based counterpart that increases performance just a bit. Luckily, you don't have to use text-based programs without graphical user interfaces to get blazing fast speeds on Linux. There are tons of open source alternatives to the mainstream progra...

It may not be your number one spot for finding cool apps for your Android device, but the Amazon Appstore for Android is running a new promotion this week called "Geek Week," where eight of the most popular productivity and utility apps are now on sale for 48 percent off or more.

Do you do last minute cramming before you go to the dentist? No, I don't mean reading up on orthodontia in hopes of having an intellectual conversation about crowns with your dentist (how you can talk at all with all those tools in your mouth is beyond me, though dentists always ridiculously try).

You can blame your naggy mom, a crappy soap bar, and school or work stress for your acne. But ultimately, you should blame yourself. While it's true that your skin type (oily vs. dry vs. sensitive) and how your skin reacts to stress play a big part in blemishes, there is a nurture component to this argument.

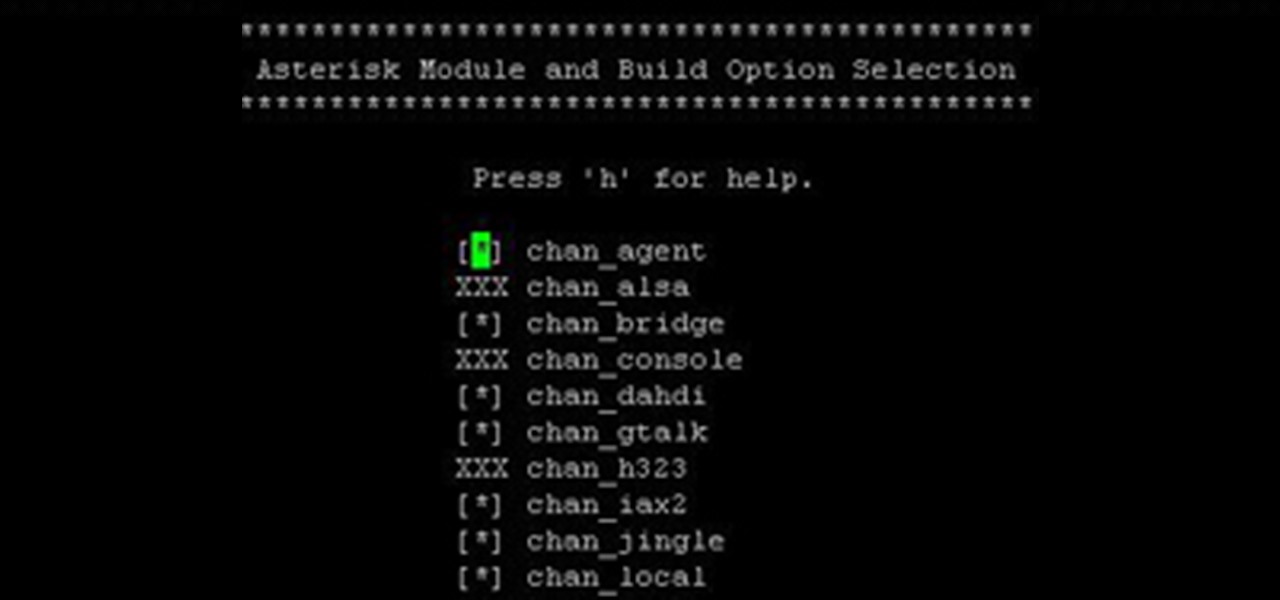
Over the years, I have enjoyed playing with Asterisk. I have found Asterisk to be extremely powerful and fun to play with. There are several books and many scattered how to articles out there, but most are outdated and the information required to build Asterisk from beginning to end can be a bit daunting. I wanted to combine all the steps into a single article and share my experience with everyone. If I have left out any steps please let me know.

Welcome to Minecraft World! Check out our tutorials, post to the community corkboard, and come play on our free server!

Have you ever forgotten your password and didn't know how to get back on your computer? Or ever had an annoying roommate you wanted to play a trick on to teach them a lesson? Or perhaps overly religious parents who think the internet is of the devil and won't let you read online articles about elliptic curve cryptography applications to C++? Well, then this article is for you!

Fire. It’s everywhere— always has been. From the Ordovician Period where the first fossil record of fire appears to the present day everyday uses of the Holocene. Today, we abundantly create flames (intentionally or unintentionally) in power plants, extractive metallurgy, incendiary bombs, combustion engines, controlled burns, wildfires, fireplaces, campfires, grills, candles, gas stoves and ovens, matches, cigarettes, and the list goes on... Yet with our societies' prodigal use of fire, t...