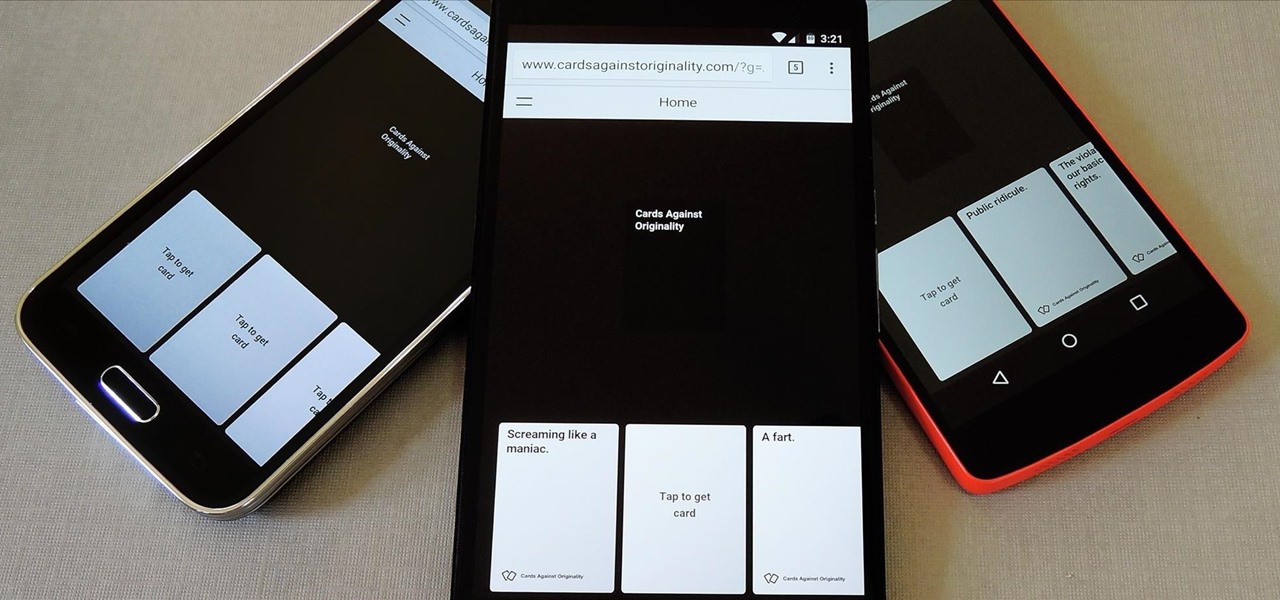
Cards Against Humanity is a popular party game with good old-fashioned raunchy adult themes that go quite well with a few alcoholic beverages. Up until now, though, you had to either print out a set of cards or order the official deck to play—unless, of course, all players happened to have devices that sported the same operating system.

While you may not have loads of secret files hiding on your computer, there might be one or two items that need a little extra security, like a file of website logins or a folder of risqué photos.
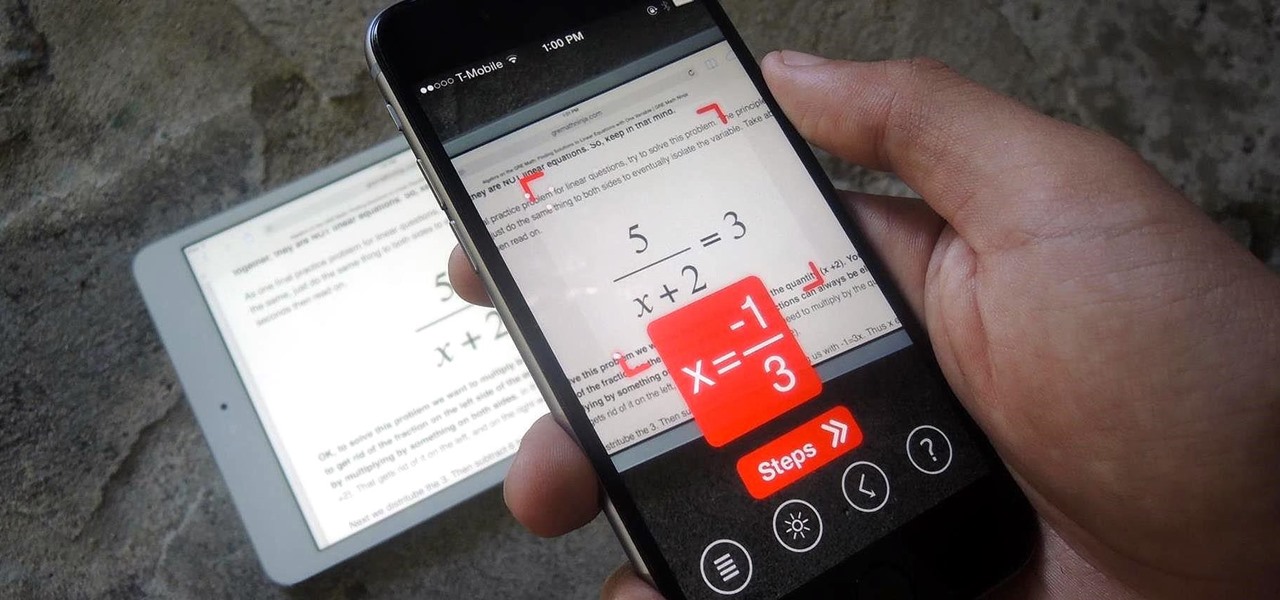
Math homework isn't the easiest thing to get through quickly, no matter how prepared you are. Knowing your stuff simply won't cut it. Going through dozens of equations in one sitting could take up hours of your time. Even when you finish, there's always going to be that one problem you couldn't solve, which could take hours itself to finally get right.

If you purchased your Nexus 5 from Google Play in the United States, we've got great news for you. In an unprecedented move, Google has started offering customers the chance to exchange their broken or water-damaged Nexus 5 for a new or refurbished unit—free of charge.

Everyone loves cupcakes. And it is so much fun to grab a cupcake bite when watching your favorite FIFA match. After all what is a match without some munchies? So this FIFA, cheer away with your team's cupcakes. They're great to win over a bet or just celebrate your team's win.
You may not always be connected to the internet, but if you're anything like me, your thirst for web content is insatiable. Whether you're on an airplane or stuck in an area with no reception, having some offline content stored on your Nexus can definitely save the day.

The recently released HTC One M8 and the upcoming Samsung Galaxy S5 are both boasting selective focus features for their camera apps, but with a 13 megapixel camera, the GS4 can take some pretty stellar pictures, too.

The in-fighting between the major US carriers just got a little more interesting. In July of last year, T-Mobile introduced their JUMP! plan, letting customers upgrade their devices after just six months, up to twice a year. Buy a device, split up the price into monthly payments, and pay an additional $10/month to enroll in the service.

How can you tell if the pair of Ray-Ban Wayfarer sunglasses that you are about to buy online are not a fake? Follow these 9 simple steps to verify the authenticity of your purchase. Always ask the seller to use the youVerify app prior to purchase. It's Smarter Selling & Safer Shopping.

With the explosion of food blogs in the last couple of years, there are more recipes available at the tip of your fingers than ever before. Craving chocolate chip cookies or Sriracha-flavored anything? You're guaranteed to have several thousand versions to choose from. So that's how they did it before the Internet...

It wasn't that long ago that we started seeing a variety of beers catering to the Steampunk crowd, so why not some wine?

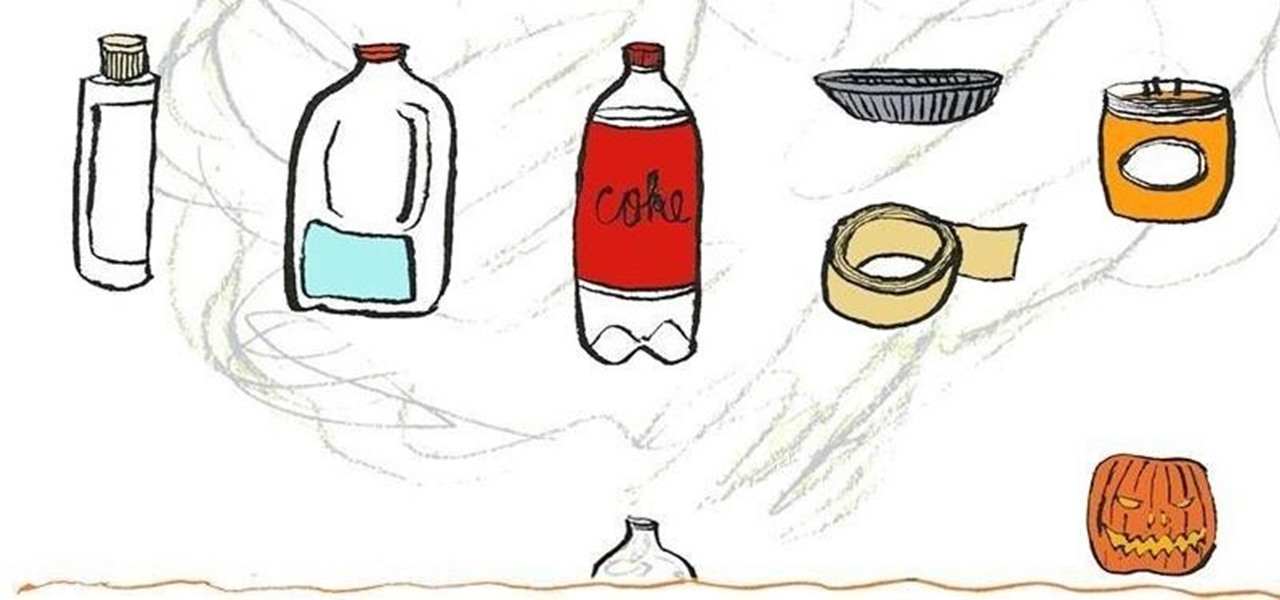
Need to add some spooky ambient fog to your super-scary Halloween party? Rather than shelling out money for a fog machine you'll probably only use once a year, make a trip to the nearest drug store and pick up a bottle of glycerin, a gallon of distilled water, a 2-liter bottle of cola, a disposable mini-pie tin, and a big candle in a jar.

When you're a kid, the best part about Halloween is the free candy, but if you're past your trick-or-treating years, there are still plenty of things you can do. With all the costumes, scary stories, and pranks, what's not to love? And now, you can even use your smartphone to celebrate.

You may remember string art from your elementary school days. If so, it probably makes you think of the 2D geometrical designs that took every ounce of patience you had as a kid. Or those laborious curve stitch drawings, which string art was actually birthed from. But thanks to some innovative modern artists, string art has gotten a lot more interesting. Here are some of the most creative applications so far.

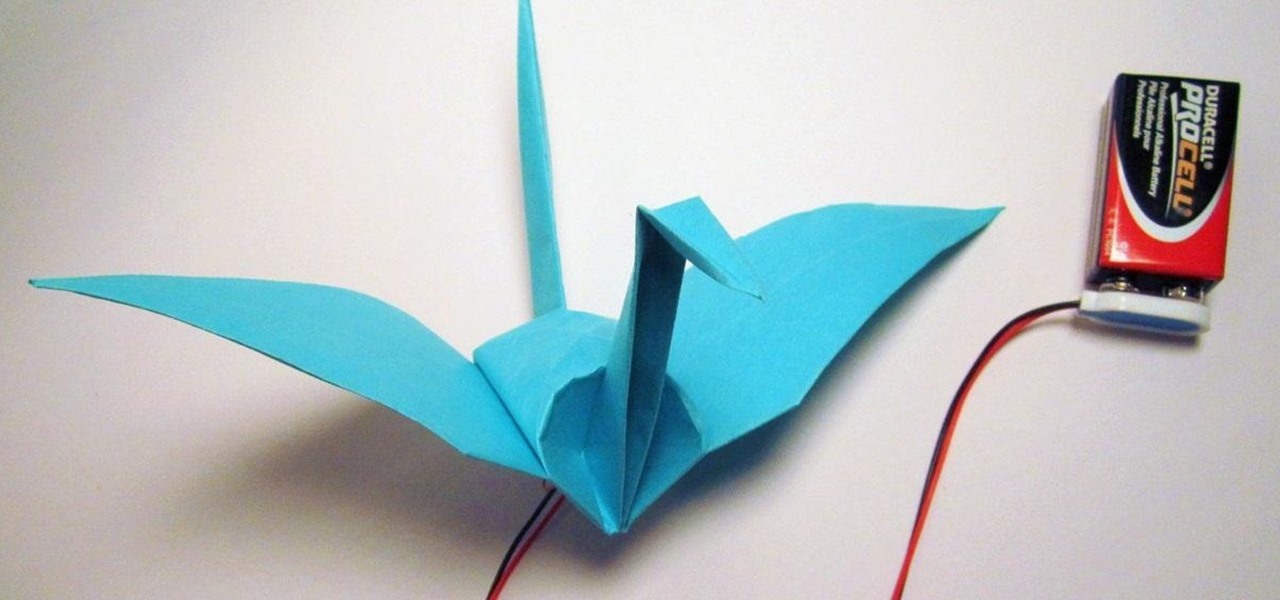
Want to spice up your origami cranes? MIT's High-Low Tech Group made two electronic origami cranes that flap their wings when you squeeze their tails.

Jake von Slatt of The Steampunk Workshop kept breaking the rear glass panel on his iPhone. So, he ended up making his own gorgeous replacement out of brass to replace the standard Apple logo ones who kept getting. The only problem was that it made his signal strength super weak, so he figured out how to transfer the etching onto a glass back. Here's the basic rundown of how he accomplished this feat...

In this video, we learn how to take a screen shot without using special tools. First, pull up the page you want to take a screen shot of. Once you have that page up, press the "Alt" and "Prnt Scrn" buttons on your computer keyboard. After you have done this, open up the "Paint" program on your computer and find the toolbar at the top. Find the button that says "edit" then hit "paste". After you do this, your page will show up in paint. You can crop it and edit it to the size you need, or leav...

This video takes you through the steps of making Coconut Milk Ice Cream. There is no narration in the video, just some bouncy music and the steps printed in text on the screen while you watch hands measuring and mixing the ingredients. Starting with coconut milk powder, you mix in milk, cook while stirring over low heat then add sugar. After those ingredients melt, you turn off the heat and add gelatin then cool. Then, you add fresh cream, mix and freeze. Simple ice cream that anyone can make!

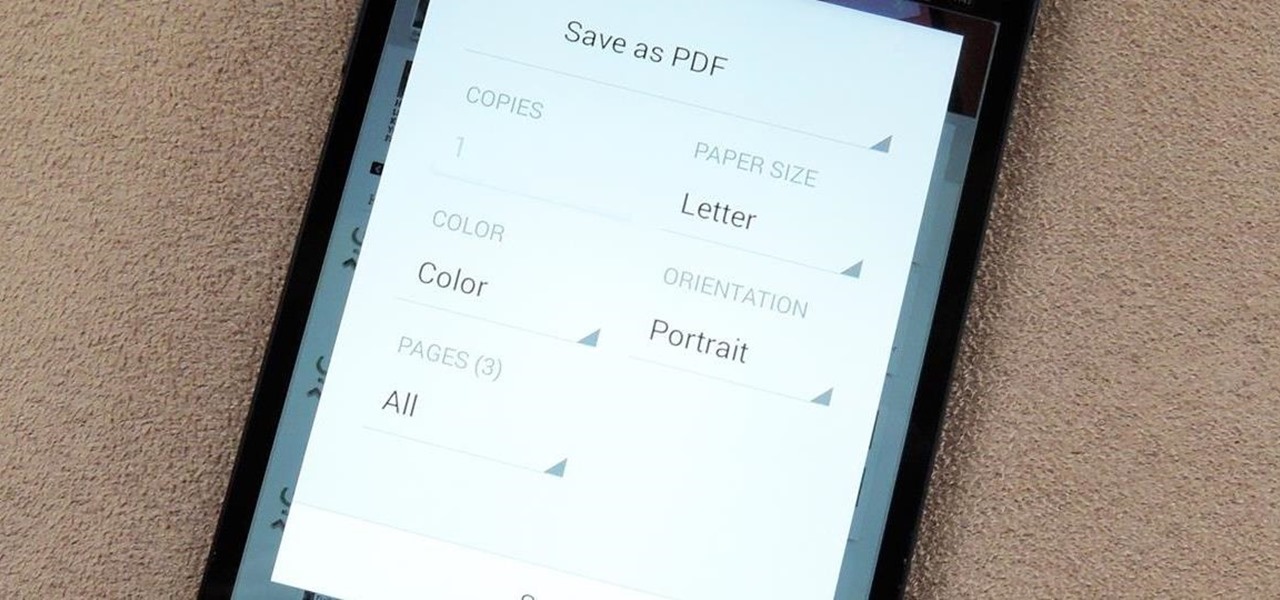
Wouldn't it be great to create a list of all of the songs on your Music Folder and then be able to print it? Wouldn't you love to have a list of files and folders burned on a CD?

Apple Card has generated quite the buzz since its March 2019 announcement. The iPhone maker's new credit card pairs with Apple Wallet on your device, is simple to sign up for, includes enhanced security over other cards, has zero fees, and provides daily rewards right to your Apple Cash account. And as good as that sounds, the fine print can complicate things real quick.

Here are a few tips and setting suggestions when getting started with your Canon PowerShot. This is a very portable and user friendly, point and shoot digital camera that has a few neat tricks up it’s sleeve so experiment and have fun.

Internet4Dummies shows how to take a screen-shot of your desktop screen using your keyboard and a photo-editing software like Microsoft-Paint, in this walk-through video first you have to navigate or arrange your screen as desired to be captured in the snapshot. Then using the print screen key the whole desktop screen can be captured. This image can be edited by any photo editing software for ease of use Microsoft Paint is used in this example. For this just open Paint and paste the screen-sh...

In this series of videos you'll learn how to connect and use a 2D scanner. Electronics & media expert Tony Ramirez shows you step by step how to load the drivers and software onto your computer, how to adjust the scanning settings, and how to save and print an image you've scanned.

Bash scripting is a convenient way to automate things on any Linux system, and we're going to use it here to automate certain tasks we use all the time.

The only thing better than programming MicroPython is programming MicroPython over Wi-Fi. So once you set up MicroPython on a microcontroller and have it on its own power source, you won't need to use a data cable to connect to it whenever you need to interact with it, program it, upload files, or grab data.

The USB Rubber Ducky and the Digispark board both suffer from the same issue when attacking macOS computers: a keyboard profiler pop-up which tries to identify any non-Apple USB keyboards. While it's an annoying setback, the solution is a simple modification that allows Mac computers to be targeted, which affects the ability to target Windows and Linux devices.

SMB (Server Message Block) is a protocol that allows resources on the same network to share files, browse the network, and print over the network. It was initially used on Windows, but Unix systems can use SMB through Samba. Today, we will be using a tool called Enum4linux to extract information from a target, as well as smbclient to connect to an SMB share and transfer files.

The $35 Raspberry Pi is an amazingly useful single-board computer (SBC) with a good balance of price, performance, and connectivity options. But for some projects, it just isn't enough. Whether you need more computing power, a smaller size, or better machine-learning capabilities, there are other options available.

When researching a person using open source intelligence, the goal is to find clues that tie information about a target into a bigger picture. Screen names are perfect for this because they are unique and link data together, as people often reuse them in accounts across the internet. With Sherlock, we can instantly hunt down social media accounts created with a unique screen name on many online platforms simultaneously.

With a simple social engineering trick, sudo passwords can be captured in seconds without the target's knowledge. The passwords can then be saved to a file or exfiltrated to another computer on the network.

With just one line of Ruby code embedded into a fake PDF, a hacker can remotely control any Mac computer from anywhere in the world. Creating the command is the easy part, but getting the target to open the code is where a hacker will need to get creative.

Back in July, Google rolled out a new design for the web version of Gmail. The rollout included new features alongside the visual changes, one of which being Confidential Mode. This new privacy-centric feature has now finally arrived on the mobile app version of the service, and here's what you need to know.

Most users don't realize how much valuable data is in their network traffic. With a few simple tools, an attacker can quickly pick out cookies, passwords, and DNS queries from a macOS device as it covertly streams the victim's network traffic to the attacker's system. Here, we will cover two methods for analyzing packets flowing from a Mac.

There are hundreds, if not thousands, of programming languages and variations of those languages that exist. Currently, in the augmented reality space, it seems the Microsoft-created C# has won out as the overall top language of choice. While there are other options like JavaScript and C++, to name a few, C# seems to be the most worthwhile place to invest one's time and effort.

Using Bitcoin (BTC) or Ethereum (ETH) to buy alt-coins like TRON (TRX), Stellar (XLM), or Ripple (XRP) can seem intimidating if you're new to cryptocurrency. Though you'll still need to do your research to avoid potential disasters, Binance takes the hassle out of trading digital currencies on your smartphone.

There's a good chance that an iPhone is on one of your Christmas shopping lists, but these things are uber-expensive now, making it hard to justify as a holiday gift — even for yourself. That's what Black Friday is for, though, which can help you save a little bit of cash on an iPhone purchase — or at least, give you something in return to help you get even more holiday presents.

You know Moana's a rock-solid pick for Halloween this year. The question is, how far will you go to become Moana? Are you going to just slap on a cream skirt and a red bandeau? Or do you want to go all out and end up with the finished product like YouTuber Gladzy Kei did?

Think of the coolest, most unique way to create art that you can. Got it? Now think about creating that art out of living things.

Gaining access to a system is always exciting, but where do you go from there? Root or bust. Sure, a compromised host is a great way to run a botnet, or do some other boring, nefarious thing—but as hackers, we want root. We also want to take the easiest path possible, search out low-hanging fruit, and exploit them. SUID programs are the lowest of the low-hanging fruit.